目錄
簡介
本文檔可幫助配置思科統一通訊管理器(CUCM)和思科統一邊界元素(CUBE)之間的SIP傳輸層安全(TLS)
必要條件
思科建議瞭解以下主題
需求
- 端點的日期和時間必須匹配(建議使用相同的NTP源)。
- CUCM必須處於混合模式。
- 需要TCP連線(任何傳輸防火牆上的開放埠5061)。
- CUBE必須安裝安全許可證和UCK9許可證。
採用元件
設定
網路圖表
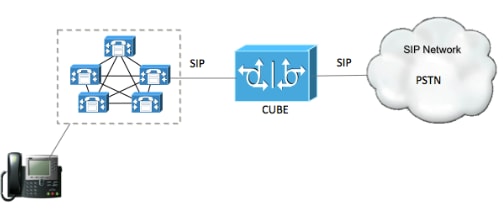
配置步驟
步驟1. 建立信任點以儲存CUBE的自簽名證書
crypto pki trustpoint CUBEtest(this can be any name)
enrollment selfsigned
serial-number none
fqdn none
ip-address none
subject-name cn= ISR4451-B.cisco.lab !(this has to match the router’s host name)
revocation-check none
rsakeypair ISR4451-B.cisco.lab !(this has to match the router's host name)
步驟2.建立信任點後,請運行Crypto pki enroll CUBEtest命令以獲取自簽名證書
crypto pki enroll CUBEtest
% The fully-qualified domain name will not be included in the certificate
Generate Self Signed Router Certificate? [yes/no]: yes
如果註冊正確,您必須看到此輸出
Router Self Signed Certificate successfully created
步驟3.取得憑證後,需要匯出憑證
crypto pki export CUBEtest pem terminal
上面的命令必須生成下面的證書
% Self-signed CA certificate:
-----BEGIN CERTIFICATE-----
MIIBgDCCASqgAwIBAgIBATANBgkqhkiG9w0BAQUFADAeMRwwGgYDVQQDExNJU1I0
NDUxLUIuY2lzY28ubGFiMB4XDTE1MTIxNTAxNTAxNVoXDTIwMDEwMTAwMDAwMFow
HjEcMBoGA1UEAxMTSVNSNDQ1MS1CLmNpc2NvLmxhYjBcMA0GCSqGSIb3DQEBAQUA
A0sAMEgCQQDGtZ974Tfv+pngs1+cCeLZ/e0b2zq6CrIj4T1t+NSlG5sjMJ919/ix
7Fa6DG33LmEYUM1NntkLaz+8UNDAyBZrAgMBAAGjUzBRMA8GA1UdEwEB/wQFMAMB
Af8wHwYDVR0jBBgwFoAU+Yy1UqKdb+rrINc7tZcrdIRMKPowHQYDVR0OBBYEFPmM
tVKinW/q6yDXO7WXK3SETCj6MA0GCSqGSIb3DQEBBQUAA0EADQXG2FYZ/MSewjSH
T88SHXq0EVqcLrgGpScwcpbR1mKFPpIhDVaJfH/FC6jnkGW7JFWcekA5Kp0tzYx4
LDQaxQ==
-----END CERTIFICATE-----
% General Purpose Certificate:
-----BEGIN CERTIFICATE-----
MIIBgDCCASqgAwIBAgIBATANBgkqhkiG9w0BAQUFADAeMRwwGgYDVQQDExNJU1I0
NDUxLUIuY2lzY28ubGFiMB4XDTE1MTIxNTAxNTAxNVoXDTIwMDEwMTAwMDAwMFow
HjEcMBoGA1UEAxMTSVNSNDQ1MS1CLmNpc2NvLmxhYjBcMA0GCSqGSIb3DQEBAQUA
A0sAMEgCQQDGtZ974Tfv+pngs1+cCeLZ/e0b2zq6CrIj4T1t+NSlG5sjMJ919/ix
7Fa6DG33LmEYUM1NntkLaz+8UNDAyBZrAgMBAAGjUzBRMA8GA1UdEwEB/wQFMAMB
Af8wHwYDVR0jBBgwFoAU+Yy1UqKdb+rrINc7tZcrdIRMKPowHQYDVR0OBBYEFPmM
tVKinW/q6yDXO7WXK3SETCj6MA0GCSqGSIb3DQEBBQUAA0EADQXG2FYZ/MSewjSH
T88SHXq0EVqcLrgGpScwcpbR1mKFPpIhDVaJfH/FC6jnkGW7JFWcekA5Kp0tzYx4
LDQaxQ==
-----END CERTIFICATE-----
複製上述生成的自簽名證書,並將其貼上到副檔名為.pem的文本檔案
以下示例命名為ISR4451-B.ciscolab.pem
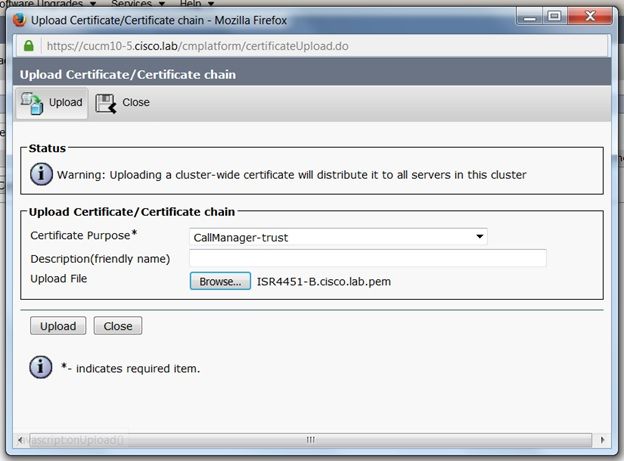
步驟4.將CUBE證書上傳到CUCM
- CUCM OS Admin > Security > Certificate Management > Upload Certificate/Certificate chain
- 證書用途= CallManager-Trust
- 上傳。pem檔案
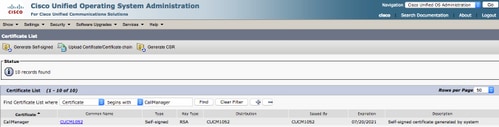
步驟5.下載Call manager自簽名證書
- 查詢表示Callmanager的證書
- 按一下主機名
- 點選下載PEM檔案
- 將其儲存到電腦
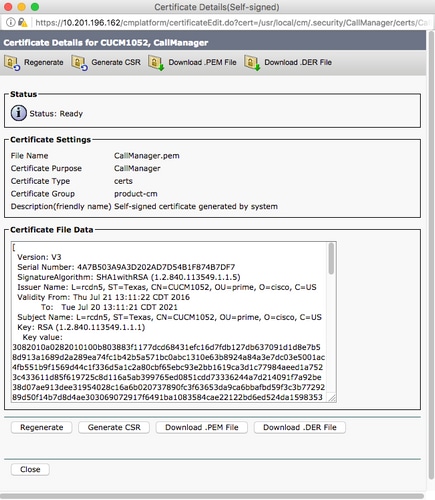
步驟6.將Callmanager.pem證書上傳到CUBE
- 使用文本檔案編輯器開啟Callmanager.pem
- 複製檔案的全部內容
- 對CUBE運行以下命令
crypto pki trustpoint CUCMHOSTNAME
enrollment terminal
revocation-check none
crypto pku authenticate CUCMHOSTNAME
(PASTE THE CUCM CERT HERE AND THEN PRESS ENTER TWICE)
You will then see the following:
Certificate has the following attributes:
Fingerprint MD5: B9CABE35 24B11EE3 C58C9A9F 02DB16BC
Fingerprint SHA1: EC164F6C 96CDC1C9 E7CA0933 8C7518D4 443E0E84
% Do you accept this certificate? [yes/no]: yes
If everything was correct, you should see the following:
Trustpoint CA certificate accepted.
% Certificate successfully imported
步驟7.配置SIP以使用CUBE的自簽名證書信任點
sip-ua
crypto signaling default trustpoint CUBEtest
步驟8.使用TLS配置撥號對等體
dial-peer voice 9999 voip
answer-address 35..
destination-pattern 9999
session protocol sipv2
session target dns:cucm10-5
session transport tcp tls
voice-class sip options-keepalive
srtp
步驟9.配置CUCM SIP中繼安全配置檔案
- CUCM Admin page > System > Security > SIP Trunk Security Profile
- 配置配置檔案,如下所示
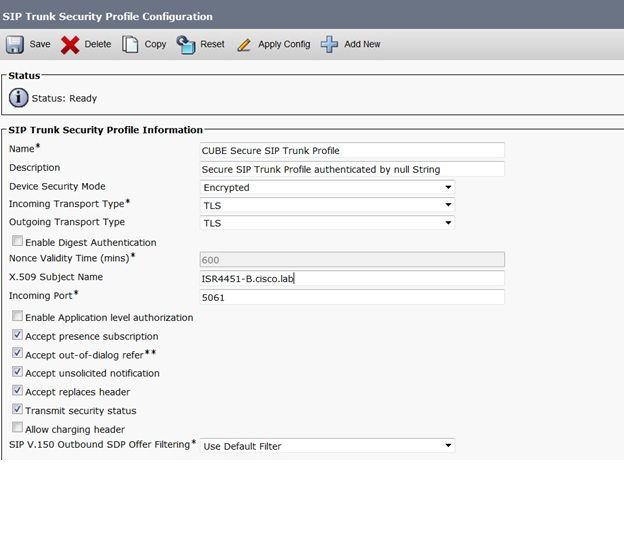
附註: 生成自簽名證書時,X.509欄位與先前配置的CN名稱匹配非常重要
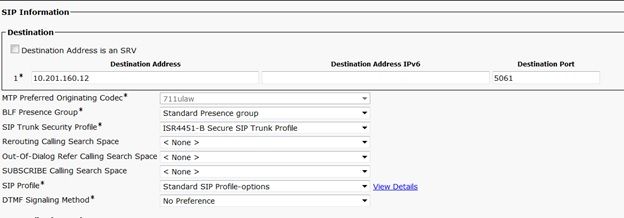
步驟10.在CUCM上配置SIP中繼
- 確保選中SRTP allowed覈取方塊
- 配置正確的目的地址並確保用埠5061替換埠5060
- 確保選擇正確的Sip中繼安全配置檔案(已在步驟9中建立)
驗證
由於您已在CUCM上啟用選項PING,因此SIP中繼必須處於完全服務狀態

SIP中繼狀態顯示完全服務。
撥號對等體狀態顯示如下:
show dial-peer voice summary
TAG TYPE MIN OPER PREFIX DEST-PATTERN FER THRU SESS-TARGET STAT PORT KEEPALIVE
9999 voip up up 9999 0 syst dns:cucm10-5 active
疑難排解
啟用並收集這些調試的輸出
debug crypto pki api
debug crypto pki callbacks
debug crypto pki messages
debug crypto pki transactions
debug ssl openssl errors
debug ssl openssl msg
debug ssl openssl states
debug ip tcp transactions
debug ccsip verbose
Webex Recording連結:
https://goo.gl/QOS1iT