Creating External VRFs
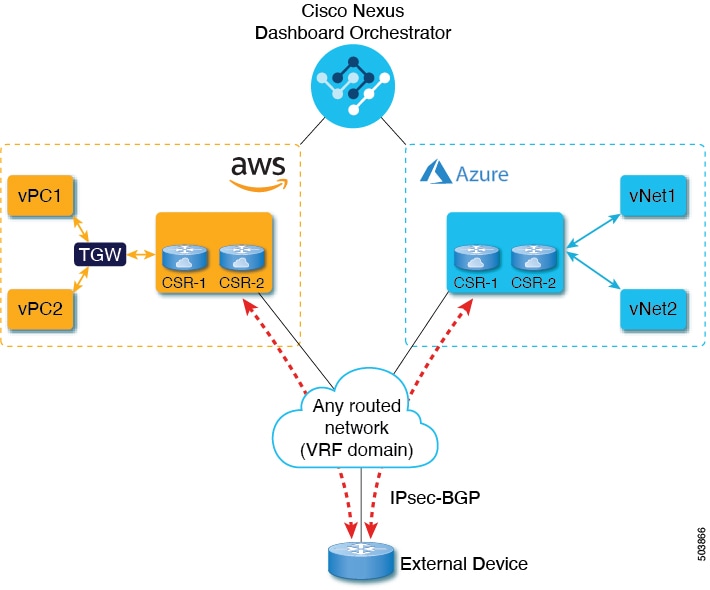
This section describes how to create an external VRF which will be used to establish connectivity to an external devices' subnets. You can follow the provided steps to provision an external VRF to multiple cloud sites.
Procedure
| Step 1 |
Log in to the Cisco Nexus Dashboard Orchestrator GUI. |
||
| Step 2 |
In the Main menu, select . |
||
| Step 3 |
Create a new schema and templates or select an existing schema where you will deploy the templates associated to the Infra tenant containing the external VRFs definition. You can create a separate schema specifically for this use case, where you will define all templates associated to the Infra tenant and containing the external VRFs providing the connectivity to the external devices. When creating the external VRF templates:
|
||
| Step 4 |
In the main pane, select . |
||
| Step 5 |
Provide the Display Name for the VRF. You can leave all other options at default values.
|
||
| Step 6 |
Assign the template that contains your external VRF to one or more cloud sites from which you will establish external connectivity. Remember that you must assign the template only to one type of cloud sites (AWS or Azure), but you can assign the same template to multiple cloud sites of the same type. |
||
| Step 7 |
Deploy the templates to create the external VRF in the cloud sites. |



 Feedback
Feedback