Cisco Secure Equipment Access Integration with Cisco Catalyst SD-WAN
|
Feature Name |
Release Information |
Feature Description |
|---|---|---|
|
Cisco Secure Equipment Access Integration |
Cisco IOS XE Catalyst SD-WAN Release 17.16.1a Cisco Catalyst SD-WAN Manager Release 20.16.1 |
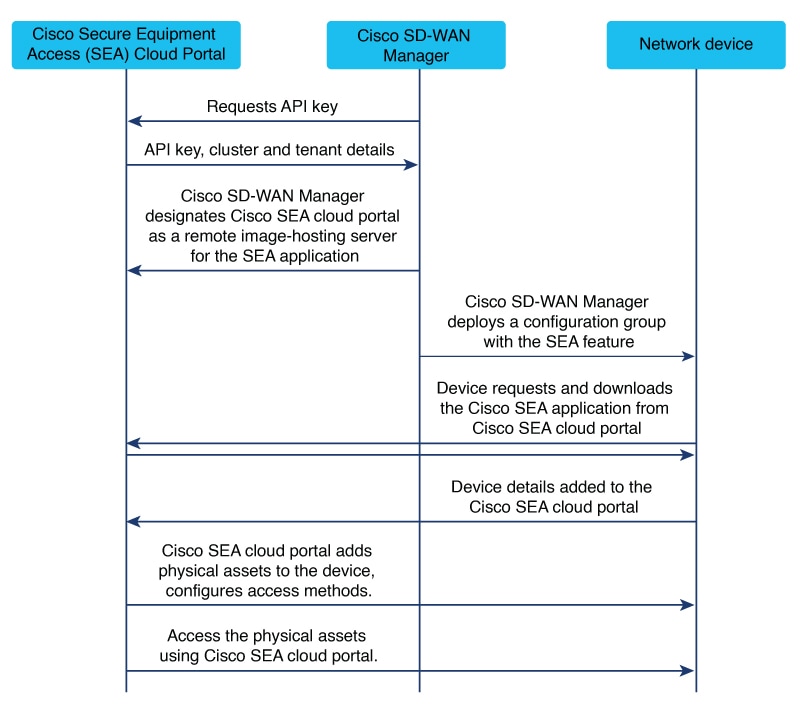
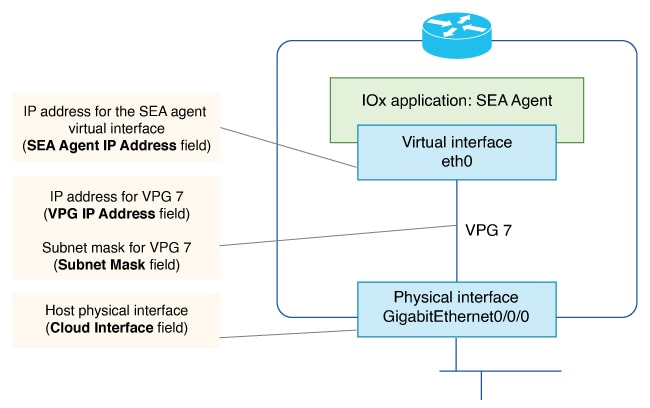
Cisco Secure Equipment Access (SEA) is a solution that provides remote access to network-connected assets. Assets can include anything reachable by IP address, such as servers, industrial internet of things (IIoT) devices, and so on. Integration with Cisco Catalyst SD-WAN enables you to use Cisco SD-WAN Manager to deploy the Cisco SEA solution within a Cisco Catalyst SD-WAN network. |

 Feedback
Feedback