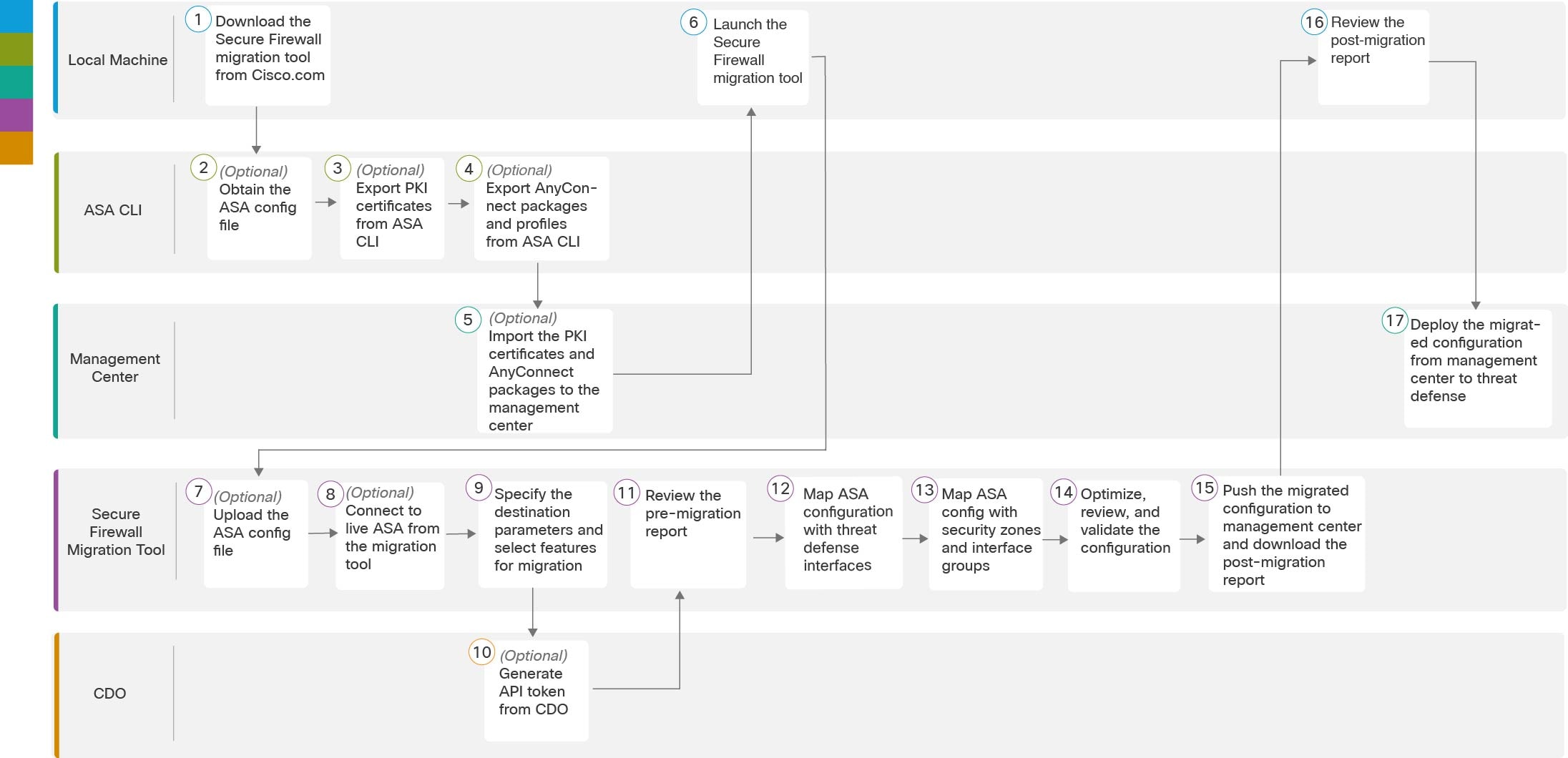
|
Step 1
|
(Optional) On the Optimize, Review and Validate Configuration screen, click Optimize ACL in to run the optimization code, and perform the following:
-
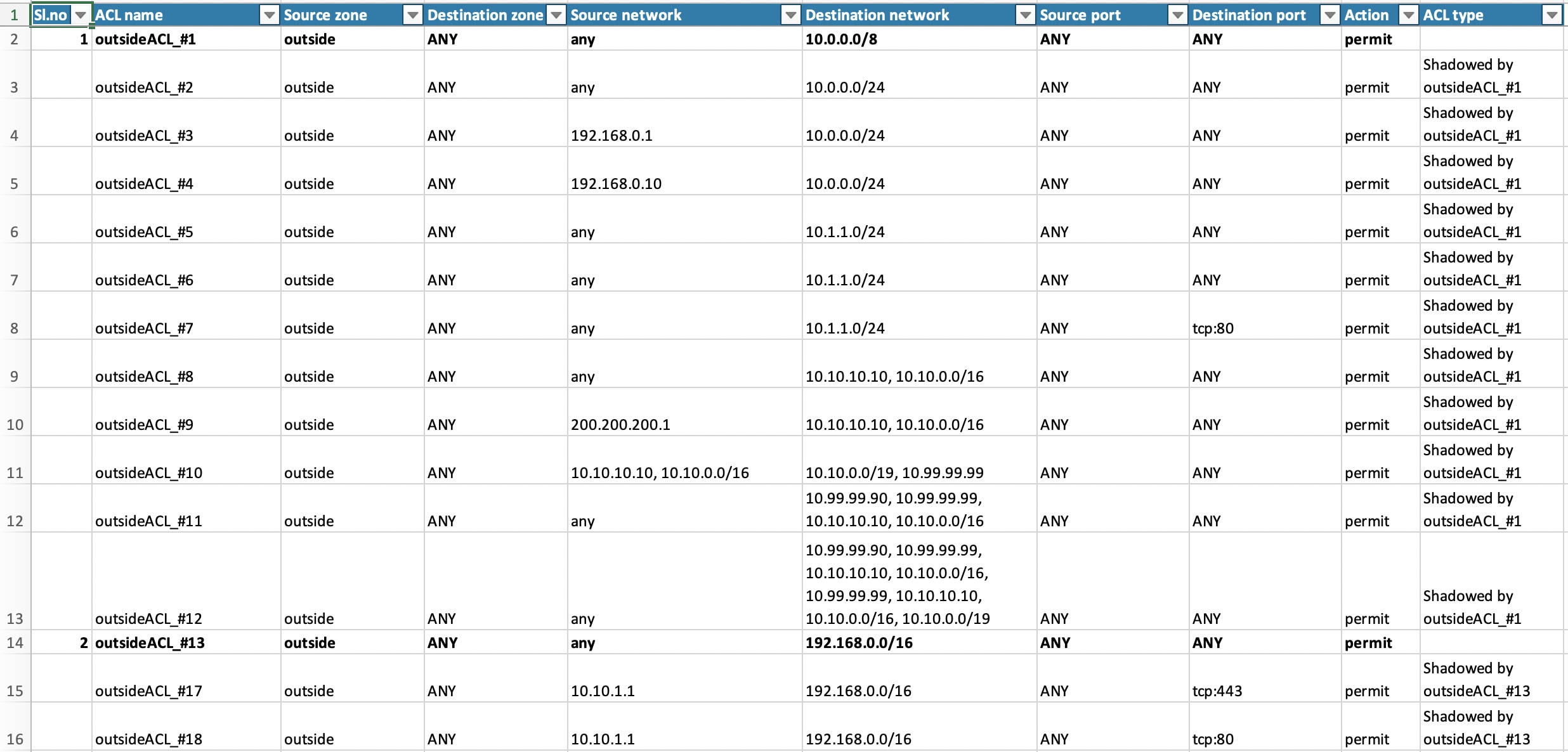
Click Proceed to proceed with the ACL optimization, where the identified Redundant ACLs and Shadow ACLs rules for migration are displayed.
The time taken for analyzing the ACL optimization depends on the source configuration file size. The estimation time is displayed.
A report with the summary of total ACL rules considered for optimization is displayed. For more information on optimization
report and its components, see Reporting for ACL Optimization.
The Redundant ACL and Shadow ACL tabs appears only if there is data in the ACL optimization report.
The ACLs are displayed in both Redundant and Shadow ACLs under different base rules.
|
Note
|
An ACL entry that is displayed under the Redundant or shadow ACL, the same is not considered as the base ACL.
|
-
To download the identified ACL optimization rules, click Download Report.
-
Select rules and choose or and apply one of the actions.
-
Click Save.
The migration operation changes from Do not migrate to disabled or vice-versa.
You can perform bulk selection of rules, using the following options
-
Migrate—To migrate with default state.
-
Do not Migrate—To ignore the migration of ACLs.
-
Migrate as disabled—To migrate ACLs with State field set to Disable.
-
Migrate as enabled—To migrate ACLs will with State field set to Enable.
|
|
Step 2
|
On the Optimize, Review and Validate Configuration screen, click Access Control Rules and do the following:
-
For each entry in the table, review the mappings and verify that they are correct.
A migrated Access Policy Rule uses the ACL name as prefix and appends the ACL rule number to it to make it easier to map back
to the ASA configuration file. For example, if an ASA ACL is named "inside_access," then the first rule (or ACE) line in the ACL will be named as "inside_access_#1." If a rule
must be expanded because of TCP or UDP combinations, an extended service object, or some other reason, the Secure Firewall
migration tool adds a numbered suffix to the name. For example, if the allow rule is expanded into two rules for migration,
they are named "inside_access _#1-1" and " inside_access_#1-2".
For any rule that includes an unsupported object, the Secure Firewall migration tool appends an "_UNSUPPORTED" suffix to the
name.
-
If you do not want to migrate one or more access control list policies, choose the rows by checking the box against the policy,
choose and then click Save.
All rules that you choose not to migrate are grayed out in the table.
-
If you want to apply a management center file policy to one or more access control policies, check the box for the appropriate rows, choose .
In the File Policy dialog, select the appropriate file policy and apply it to the selected access control policies and click Save.
-
If you want to apply a management center IPS policy to one or more access control policies, check the box for the appropriate rows, choose .
In the IPS Policy dialog, select the appropriate IPS policy and its corresponding variable set and apply it to the selected access control
policies and click Save.
-
If you want to change the logging options for an access control rule which has logging enabled, check the box for the appropriate
row and choose .
In the Log dialog, you can enable logging events either at the beginning or end of a connection or both. If you enable logging, you
must opt to send the connection events either to the Event Viewer or to the Syslog or both. When you opt to send connection events to a syslog server, you can choose the syslog policies that are already configured
on the management center from the Syslog drop-down menu.
-
If you want to change the actions for the migrated access control rules in the Access Control table, check the box for the
appropriate row and choose .
In the Rule Action dialog from the Actions drop-down, you can either choose ACP or Prefilter tabs:
-
ACP—Every access control rule has an action that determines how the system handles and logs matching traffic. You can either
perform an allow, trust, monitor, block, or block with reset action on an access control rule.
-
Prefilter—A rule's action determines how the system handles and logs matching traffic. You can either perform a fastpath and
block.
|
Tip
|
The IPS and file policies that are attached to an access control rule are automatically removed for all rule actions except
for the Allow option.
|
ACL Rule Category—The Secure Firewall migration tool preserves the Rule sections in the CSM managed ASA configuration and
migrates them as ACL categories on management center.
Policy capacity and limit warning—The Secure Firewall migration tool compares the total ACE count for the migrated rules with
the supported ACE limit on the target platform.
Based on the comparison result, the Secure Firewall migration tool displays a visible indicator and a warning message if the
total count of migrated ACE exceeds threshold or if it approaches the threshold of the supported limit of target device.
You can optimize or decide not to migrate if the rules exceed the ACE Count column. You can also complete the migration and
use this information to optimize the rules after a push on the management center before deployment.
|
Note
|
The Secure Firewall migration tool does not block any migration despite the warning.
|
You can filter the ACE counts in the ascending, descending, equal, greater than, and lesser than filtering order sequence.
To clear the existing filter criteria, and to load a new search, click Clear Filter.
|
Note
|
The order that you sort the ACL based on ACE is for viewing only. The ACLs are pushed based on the chronological order in
which they occur.
|
|
|
Step 3
|
Click the following tabs and review the configuration items:
-
Access Control
-
Objects (Access List Objects, Network Objects, Port Objects, VPN Objects, and Dynamic-Route Objects)
-
NAT
-
Interfaces
-
Routes
-
DHCP
-
SNMP
-
Site-to-Site VPN Tunnels
-
Remote Access VPN
-
WebVPN
|
Note
|
For site-to-site and remote access VPN configurations, VPN filter configurations and extended access list objects pertaining
to them are migrated and can be reviewed under the respective tabs.
|
Access List objects displays Standard and Extended ACL used in BGP, EIGRP, and RA VPN.
If you do not want to migrate one or more NAT rules or route interfaces, check the box for the appropriate rows, choose , and then click Save.
All rules that you choose not to migrate are grayed out in the table.
|
|
Step 4
|
(Optional) On the Network Objects and the Port Objects tabs, review all the network objects, network groups, port objects, port groups, and their values. To rename an object or
object group, select the object and choose .
-
Click Optimize Objects and Groups to optimize your list of objects before migrating them to the target management center. The migration tool identifies objects
and groups that have the same value and prompts you to choose which to retain.
-
Click  to move objects from Conflict Detected column to Objects/Groups Retained column and click to move objects from Conflict Detected column to Objects/Groups Retained column and click  to move them back. Note that the ones that are referenced in most configurations are displayed in bolded text. to move them back. Note that the ones that are referenced in most configurations are displayed in bolded text.
-
Click Auto Select to automatically select all the objects and groups with most number of referenes. However, you can still manually override
the autoselection and move objects between columns because manual selection takes higher priority.
-
Click Optimize. The migration tool performs the optimization and displays an optimization summary with optimization data including retained
and duplicate objects. For a detailed version of the optimization report, refer to the postmigration report.
-
Click Proceed and Validate.
|
Note
|
The objects and groups which are not chosen to be retained are not migrated and are replaced with the retained objects in
the configurations they were used, such as in ACL and NAT configurations. This ensures the list of objects being migrated
is fully optimized and there are no duplicate objects migrated.
|
|
|
Step 5
|
(Optional) While reviewing your configuration, you can rename one or more network, port, or VPN objects in the Network Objects tab or Port Objects tab, or the VPN Objects by choosing .
Access rules and NAT policies that reference the renamed objects are also updated with new object names.
|
|
Step 6
|
In the Dynamic-Route Objects section, all the supported objects that are migrated are displayed:
-
Policy-List
-
Prefix-List
-
Route-Map
-
Community List
-
AS-Path
-
Access-List
|
|
Step 7
|
In the Routes section, the following routes are displayed:
-
Static—Displays all IPv4 and IPv6 static routes.
-
BGP—Displays all the BGP routes.
-
EIGRP—Displays all the EIGRP routes.
For EIGRP, authentication keys are obtained if the more system:running configuration is uploaded and the keys are unencrypted. If the key is encrypted in the source configuration, you can manually
provide the key under the interface section in EIGRP. You can select the authentication type (encrypted, unencrypted, auth,
or none) and provide the key accordingly.
-
ECMP—Displays all the ECMP zones and associated VRFs.
|
Note
|
The only action which can be performed in this section is renaming the ECMP zones.
|
-
PBR—Displays all the PBR routes.
|
|
Step 8
|
Under the DHCP tab, you can review and validate the following tabs:
-
DHCP Server: Review all the IP address pools and the corresponding interfaces.
-
DHCP Relay: Review the DHCP Relay server IP addresses, interfaces to which the DHCP server is associated with, and the Relay-enabled
interfaces.
-
DDNS: Under DDNS Update Methods tab, review the DDNS method names, types, the DDNS update intervals, and which records are configured to be updated by the
DHCP Server (A or PTR records).
|
Note
|
In the Select Features page, you can select either DHCP Server only or Relay and DDNS together. Therefore, if you see configurations in the DHCP Server tab in the Optimize, Review and Validate Configuration page, the DHCP Relay and DDNS tabs are empty.
|
|
|
Step 9
|
Under the SNMP tab, you can review, validate, and work with the following tabs:
Based on whether you have SNMPV1/V2 or SNMPV3 configurations on your ASA device, the configurations gets displayed in SNMPV1/V2 tab or SNMPV3 tab.
SNMPV1/V2:
-
Host Server Name: The hostname of the SNMP host
-
IP Address: The IP address of the SNMP host
-
Community String: The SNMP community string that must be provided manually. Select the host and navigate to provide the community string. This must be the same as the community or username that is configured for the SNMP service.
-
Validation State: The host server's validation state that will be created in the target management center
SNMPV3:
-
User Name: The username for SNMP host
-
Authentication Password: Click Actions to provide the authentication password for the user
-
Encryption Password: Click Actions to provide the privacy password for the user
-
Validation State: The user's validation state that will be created in the target management center
|
|
Step 10
|
In the Site-to-Site VPN Tunnels section, all the supported VPN tunnels that are migrated from ASA to management center are displayed, and includes the following lists.
-
Both crypto map and route-based (VTI) based VPN tunnels.
-
VPN tunnels of authentication type preshared key and certificate-based authentication.
You must enter the values for preshared key and the PKI object for each VPN topology for validation for all the rows. Failure
to update will be marked as incomplete and the Secure Firewall migration tool will not allow to proceed to validation.
|
Note
|
For a live connect ASA, the preshared keys are retrieved automatically by the migration tool; for a manually uploaded configuration,
use the more system: running-config to retrieve the hidden keys and provide them manually in the preshared Key column.
|
|
Note
|
Trustpoint or PKI object migration from ASA to management center is part of the pre-migration activity and is required for successful migration of certificate-based VPN migration.
|
|
|
Step 11
|
(Optional) Click Add Hub & Spoke Topology to configure a hub and spoke VPN topology using the target threat defense as the hub node and selecting one or more ASA peer
interfaces as the spoke nodes.
|
Note
|
You can select spoke nodes of the same IKE versions only. For instance, you cannot choose one spoke node of IKEv1 and another
spoke node of IKEv2 IKE version.
|
Based on the IKE version of the selected spoke nodes, configure or verify the following:
-
IKE Version—Verify that the IKE version of the selected nodes is checked.
-
Endpoints—Verify that the target threat defense device is by default selected as the hub node, the spoke nodes you selected from the
list, and their VPN interfaces and protected source and remote networks.
-
IKE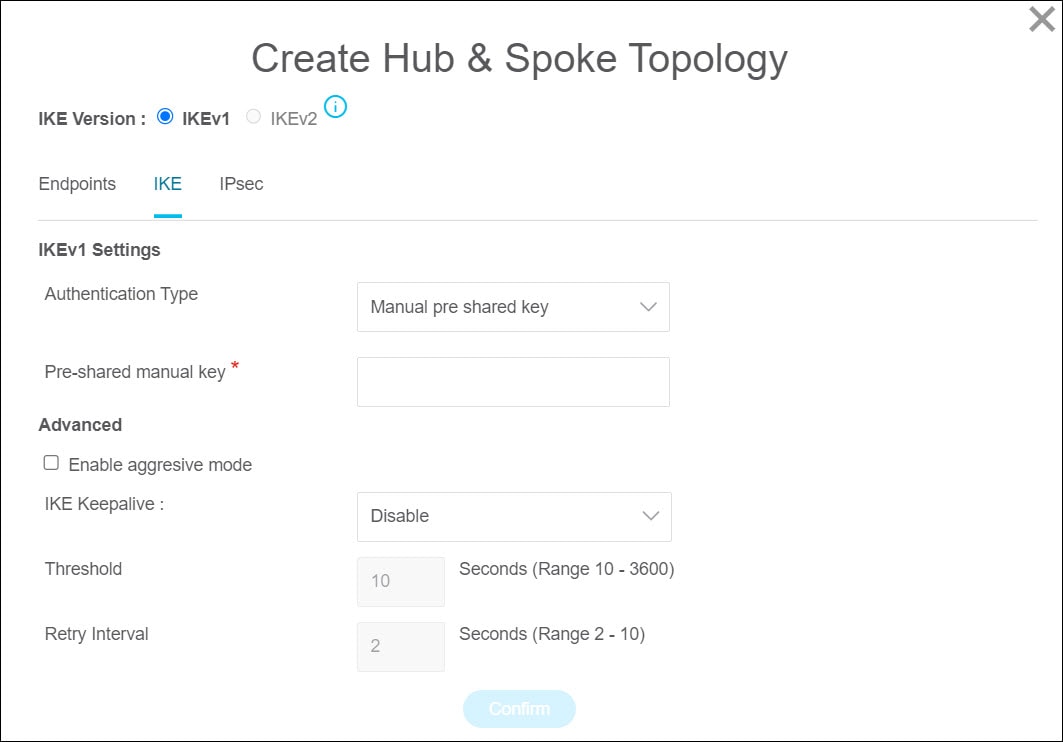
-
IPsec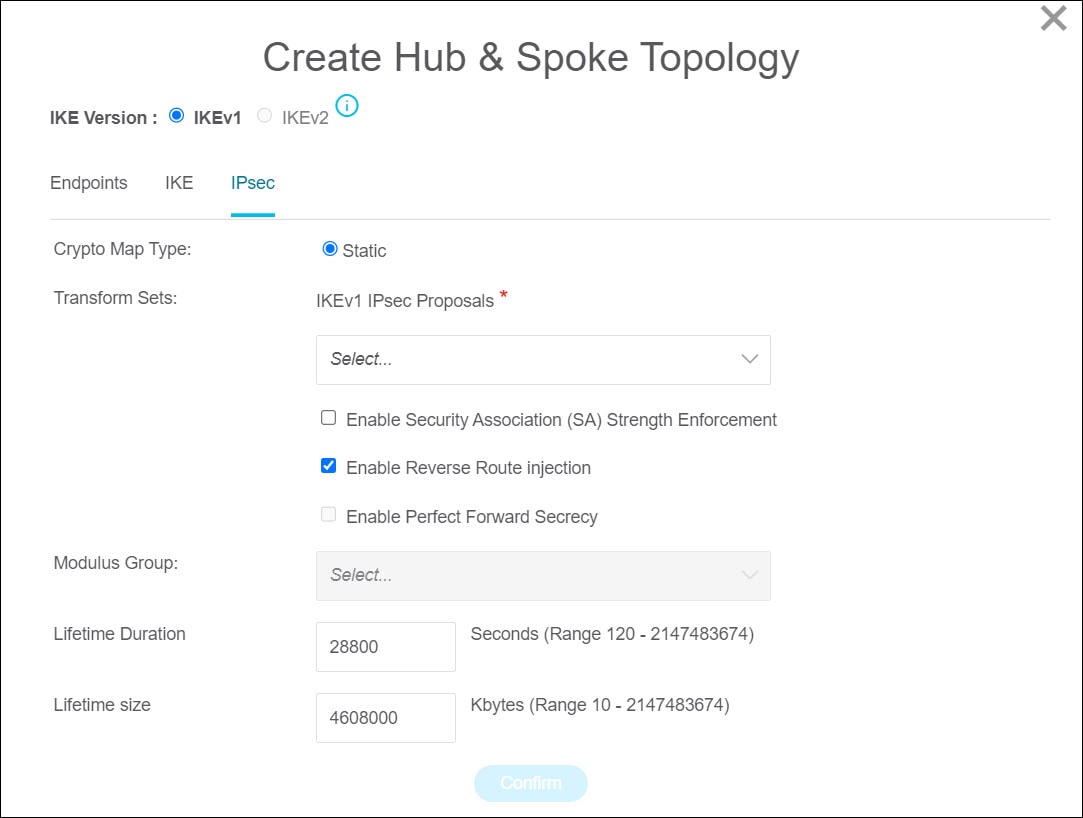
-
Crypto Map Type—A crypto map combines all the components required to set up IPsec security associations (SA). When two peers try to establish
an SA, they must each have at least one compatible crypto map entry. The IPsec security negotiation uses the proposals defined
in the crypto map entry to protect the data flows specified by that crypto map’s IPsec rules. Choose static or dynamic for
this deployment's crypto map.
-
Transform Sets—Select the IPsec proposal that you want to use for the IKE version nodes you selected.
-
Enable Security Association (SA) Strength Enforcement—Check this checkbox to ensure that the encryption algorithm used by the child IPsec SA is not stronger (in terms of the number
of bits in the key) than the parent IKE SA.
-
Enable Reverse Route Injection—Check this checkbox to enable reverse route injection which automatically inserts static routes into routing for networks
and hosts, which are protected by a remote tunnel group list.
-
Enable Perfect Forward Secrecy—Check this checkbox to generate and use a unique session key for each encrypted exchange. The unique session key protects
the exchange from subsequent decryption, even if the entire exchange was recorded and the attacker has obtained the preshared
or private keys used by the endpoint devices.
-
Modulus Group—Choose the Diffie-Hellman group to use for deriving a shared secret between the two IPsec peers without transmitting it to
each other. A larger modulus provides higher security but requires more processing time. The two peers must have a matching
modulus group. See Deciding Which Diffie-Hellman Modulus Group to Use in the Cisco Secure Firewall Management Center Device Configuration Guide for more information.
-
Lifetime Duration—The number of seconds you want a security association to exist before expiring. The default is 28,800 seconds.
-
Lifetime Size—The volume of traffic (in kilobytes) that can pass between IPsec peers using a given security association before it expires.
The default is 4,608,000 kilobytes. Infinite data is not allowed.
If you have an existing site-to-site hub and spoke VPN configuration on one of the devices in the management center, you can
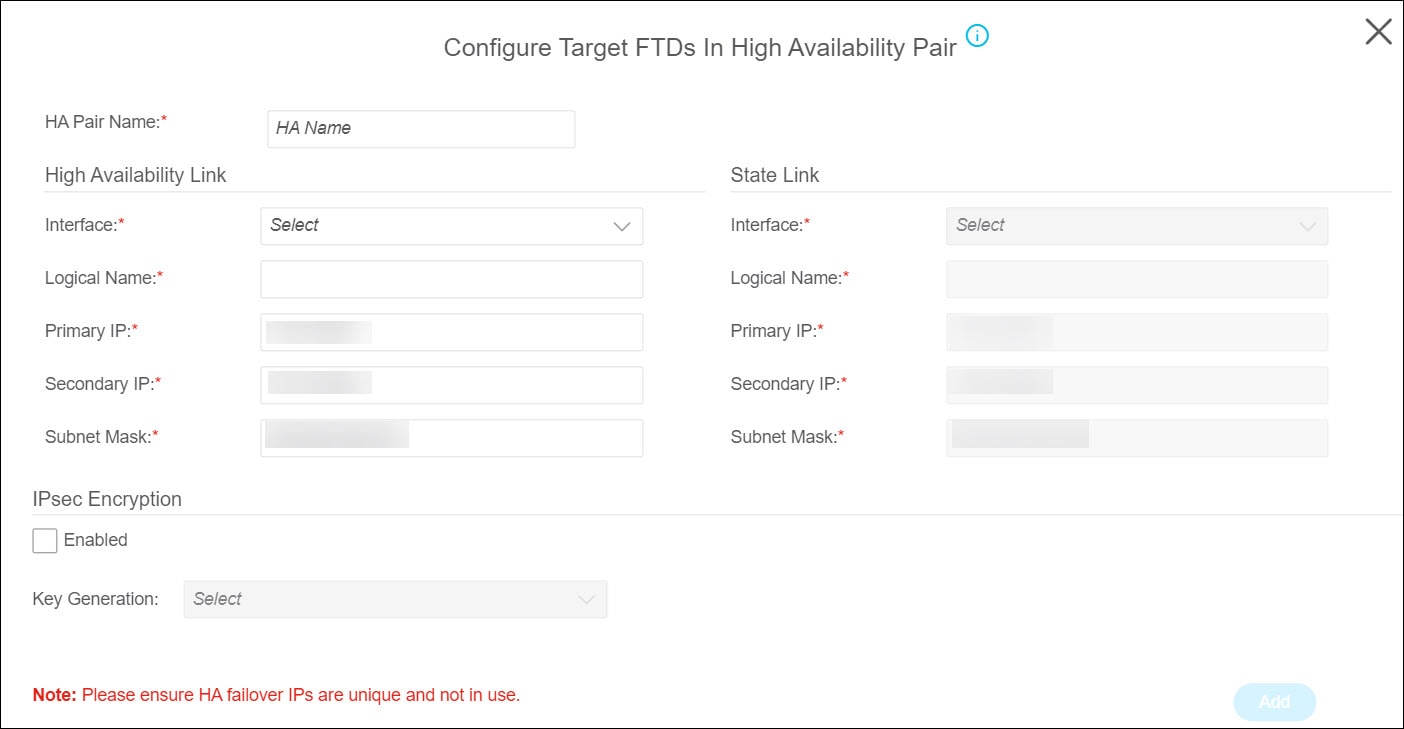
choose to add your target threat defense device as one of the spokes to it. Choose Add to existing Hub & Spoke Topology, select the topology to which you want to add your device, and select Interface and Protected Networks.
|
|
Step 12
|
For configurations containing several site-to-site VPN tunnel configurations, to update the preshared keys for multiple entries
at once, follow the steps below:
-
Select the site-to-site VPN configuration entries for which you want to update the preshared keys.
-
Click download ( ) to export the table to an editable Excel sheet. ) to export the table to an editable Excel sheet.
-
Enter the preshared keys in the respective columns against each VPN configuration and save the file. For VPN configurations
containing both IKEv1 and IKEv2 versions of IKE, ensure you enter two values in the column separated by a comma.
-
Click upload ( ). The migration tool reads the entries in the Excel and automatically adds them to the corresponding preshared key columns
of the VPN configurations. ). The migration tool reads the entries in the Excel and automatically adds them to the corresponding preshared key columns
of the VPN configurations.
|
Note
|
To update a preshared key that was missed to be updated as part of the bulk update, use the default method of selecting the
entry and choosing or export the Excel, update the key, and import it.
|
If the target threat defense device already has a site-to-site VPN topology configured, the migration tool detects it and
prompts you to choose if you want to delete it. If you choose to delete it, the migration tool deletes it for you, without
you having to log in to the management center to manually delete it. If you choose No, you need to manually delete any existing VPN configurations on the target threat defense device to continue the migration.
|
|
Step 13
|
In the Remote Access VPN section, all objects corresponding to remote access VPN are migrated from ASA to the management center, and are displayed:
-
Anyconnect Packages: Retreive the AnyConnect packages, Hostscan Files (Dap.xml, Data.xml, Hostscan Package), External Browser package, and AnyConnect profiles should be retrieved from the source ASA device for migration.
As part of the premigration activity, upload all the AnyConnect packages to the management center. You can upload AnyConnect
profiles either directly to the management center or from the Secure Firewall migration tool.
Select pre-existing AnyConnect, Hostscan, or external browser packages retrieved from the management center. You must select atleast one AnyConnect package. You must also select the Hostscan, dap.xml, data.xml, or external browser, if they are available in the source configuration.
AnyConnect profiles are optional.
Ensure that the correct Dap.xml file is retrieved from the source firewall. Validations are performed on the dap.xml file
that are available in the configuration file. You must select all the files that are required for validation and upload them.
Failure to update marks as incomplete and the Secure Firewall migration tool does not proceed with validation.
-
AAA—Authentication servers of Radius, LDAP, AD, LDAP, SAML, and Local Realm type are displayed. Update the keys for all AAA servers.
From Secure Firewall migration tool 3.0, the preshared keys are retrieved automatically for a Live Connect ASA. You can also
upload the source configuration with the hidden keys using more system: running-config file. To retrieve the AAA authentication key in clear text format, follow the below steps:
|
Note
|
These steps should be performed outside the Secure Firewall migration tool.
|
-
Connect to the ASA through the SSH console.
-
Enter the more system:running-config command.
-
Go to the aaa-server and local user section to find all the AAA config and the respective key values in clear text format.
ciscoASA#more system:running-config
!
aaa-server Test-RADIUS (inside) host 2.2.2.2
key <key in clear text> <-----The radius key is now displayed in clear text format.
aaa-server Test-LDAP (inside) host 3.3.3.3
ldap-login-password <Password in clear text> <-----TheLDAP/AD/LDAPS password is now displayed in clear text format.
username Test_User password <Password in clear text> <-----The Local user
password is shown in clear text.
|
Note
|
If the password for the local user is encrypted, you can internally check for the password or configure a new one on the Secure
Firewall migration tool.
|
-
LDAPS requires domain on management center. You must update domain for encryption type LDAPS.
-
Unique AD Primary Domain is required on management center for an AD server. If a unique domain is identified, it will be displayed on the Secure Firewall migration tool. If conflict
is found, you must enter a unique AD primary domain to push the objects successfully.
For AAA server with encryption set to LDAPS, ASA supports IP and hostname or domain but the management center supports only
hostname or domain. If ASA config contains hostname or domain, it is retrieved and displayed. If ASA config contains the IP
address for LDAPS, enter a domain in the AAA section under Remote Access VPN. You must enter the domain that can be resolved to the IP address of the AAA server.
For AAA server with type AD (server-type is Microsoft in ASA config), AD Primary Domain is a mandatory field to be configured on a management center. This field is not configured separately on ASA and extracted
from the LDAP-base-dn config on ASA.
If the ldap-base-dn is: ou=Test-Ou,dc=gcevpn,dc=comThe AD Primary Domain is the field starting with dc, with dc=gcevpn, and dc=com that forms the primary domain. The AD primary domain would be gcevpn.com.
LDAP-base-dn example file:
cn=asa,OU=ServiceAccounts,OU=abc,dc=abc,dc=com:Here, dc=abc, and dc=com will be combined as abc.com to form the AD Primary Domain. cn=admin, cn=users, dc=fwsecurity, dc=cisco, dc=com:AD Primary Domain is fwsecurity.cisco.com.
AD Primary Domain is retrieved automatically and displayed on the Secure Firewall migration tool.
|
Note
|
AD Primary Domain value needs to be unique for each Realm object. In case a conflict is detected or if the Firewall Migration
Tool is unable to find the value in the ASA config, you are requested to enter an AD Primary Domain for the specific server.
Enter the AD Primary Domain to validate the configuration.
|
-
Address Pool—Review all the IPv4 and IPv6 pools that are displayed here.
-
Group-Policy—Select or remove the user profile, management profile, and client module profile from this area, which displays group policies
with client profiles, management profiles, client modules, and group policies without profiles. If a profile was added in
the AnyConnect file area, it is displayed as preselected. You can select or remove the user profile, management profile, and
client module profile.
The custom attribute related to the specific group-policy is displayed in the AnyConnect Custom Attribute tab. You can select the custom attribute and validate it.
-
Connection Profile—Review all connection profiles/tunnel groups that are displayed here.
-
Trustpoints—Trustpoint or PKI object migration from the ASA to the management center is part of the premigration activity and is required for successful migration of remote access VPN.
Map the trustpoint for Global SSL, IKEv2, and interfaces in the Remote Access Interface section to proceed with the migration. Global SSL and IKEv2 Trustpoint are mandatory if the LDAPS protocol is enabled.
If a Security Assertion Markup Language (SAML) object exists, the trustpoint for the SAML IDP and SP can be mapped in the
SAML section. SP certificate upload is optional. Trustpoints can be overridden for a specific tunnel group. If the overriden
SAML trustpoint configuration is available in the source ASA, it can be selected under Override SAML.
For information on exporting PKI certificates from ASA, see Export PKI Certificate from ASA
and Import into Management Center.
-
Certificate Maps—Certificate maps are displayed here.
-
VPN Load Balancing—VPN load balancing Configurations are displayed here.
For VPN load balancing, the Secure Firewall migration tool will fetch the encryption key if more system: running-config configuration is uploaded. You can manually update the encryption key using .
-
Under the WebVPN tab, the migration tool lists all the WebVPN policies that it detected in the source ASA device. WebVPN policies include
any ASA group policy with SSL clientless VPN tunnel protocol configurations and tunnel groups that are referenced to policies
using SAML authentication. Ensure you review the tabs associated with your WebVPN configurations before proceeding:
-
Zero Trust Application Policy: Provide a different value by selecting the policy and navigating
-
Policy Name: The policy's name that will get migrated.
-
Domain Name: User-defined domain name that must be manually provided. This domain name resolves to the threat defense interface from
where the private applications are accessed. The domain name is used to generate the ACS URL for all private applications
in an Application Group.
-
Identity Certificate: The identity certificate that you imported into the target management center before migration. This must be done as part
of the premigration tasks.
-
Security Zones: The corresponding security zones associated with the policy.
-
Global Port Pool: The port range for the policy. A unique port from this pool is assigned to each application.
-
Application Group
-
Application Group: Review the Application Group Settings including application group name, re-authentication interval, and security zones.
Under the SAML IdP Metadata tab, you can choose to manually configure application group name, entity ID for the service provider, single sign-on URL
for the SAML identity provider (IdP), and IdP certificate or choose Configure Later
The Applications tab lets you review or configure application-specific settings such as application name, external URL, application URL, application
certificate, and application group.
-
Standalone Applications: Review or configure Application Settings for standalone applications, including application name, external URL, application URL, application certificate, re-authentication
interval, and security zones. The SAML IdP Metadata tab lets you manually configure IdP metadata settings for standalone applications or configure later. The tabs include application
group name, entity ID, single sign-on URL, and IdP certificate.
To update the fields, click Actions and choose to update the various fields.
After the migration is successful, ensure you do a thorough review of the configurations that you migrated to the management
center and when ready, deploy it to your threat defense device.
|
|
Step 14
|
(Optional) To download the details for each configuration item in the grid, click Download.
|
|
Step 15
|
After you have completed your review, click Validate. Note that the mandatory fields that need your attention keeps flickering until you enter values in them. The Validate button gets enabled only after all the mandatory fields are filled.
During validation, the Secure Firewall migration tool connects to management center, reviews the existing objects, and compares those objects to the list of objects to be migrated. If an object already exists
in management center, the Secure Firewall migration tool does the following:
-
If the object has the same name and configuration, the Secure Firewall migration tool reuses the existing object and does
not create a new object in management center.
-
If the object has the same name but a different configuration, the Secure Firewall migration tool reports an object conflict.
You can view the validation progress in the console.
|
|
Step 16
|
When the validation is complete, if the Validation Status dialog box shows one or more object conflicts, do the following:
-
Click Resolve Conflicts.
The Secure Firewall migration tool displays a warning icon on either or both of the Network Objects or Port Objects tab, depending upon where the object conflicts were reported.
-
Click the tab and review the objects.
-
Check the entry for each object that has a conflict and choose .
-
In the Resolve Conflicts window, complete the recommended action.
For example, you might be prompted to add a suffix to the object name to avoid a conflict with the existing management center object. You can accept the default suffix or replace it with one of your own.
-
Click Resolve.
-
When you have resolved all object conflicts on a tab, click Save.
-
Click Validate to revalidate the configuration and confirm that you have resolved all object conflicts.
|
|
Step 17
|
When the validation is complete and the Validation Status dialog box displays the message Successfully Validated, continue with Push the Migrated Configuration to Management Center.
|





 to move objects from
to move objects from  to move them back. Note that the ones that are referenced in most configurations are displayed in bolded text.
to move them back. Note that the ones that are referenced in most configurations are displayed in bolded text.


 ) to export the table to an editable Excel sheet.
) to export the table to an editable Excel sheet.
 ). The migration tool reads the entries in the Excel and automatically adds them to the corresponding preshared key columns
of the VPN configurations.
). The migration tool reads the entries in the Excel and automatically adds them to the corresponding preshared key columns
of the VPN configurations.

 Feedback
Feedback