Additional References
The following link contains additional resources that you can use when working with Cisco ISE: https://www.cisco.com/c/en/us/td/docs/security/ise/end-user-documentation/Cisco_ISE_End_User_Documentation.html
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
The following link contains additional resources that you can use when working with Cisco ISE: https://www.cisco.com/c/en/us/td/docs/security/ise/end-user-documentation/Cisco_ISE_End_User_Documentation.html
To receive timely, relevant information from Cisco, sign up at Cisco Profile Manager.
To get the business impact you’re looking for with the technologies that matter, visit Cisco Services.
To submit a service request, visit Cisco Support.
To discover and browse secure, validated enterprise-class apps, products, solutions, and services, visit Cisco DevNet.
To obtain general networking, training, and certification titles, visit Cisco Press.
To find warranty information for a specific product or product family, access Cisco Warranty Finder.
Cisco Bug Search Tool (BST) is a gateway to the Cisco bug-tracking system, which maintains a comprehensive list of defects and vulnerabilities in Cisco products and software. The BST provides you with detailed defect information about your products and software.
To provide feedback about Cisco technical documentation, use the feedback form available in the right pane of every online document.
Cisco ISE architecture includes the following components:
Nodes and persona types
Cisco ISE node—A Cisco ISE node can assume any or all of the following personas: Administration, Policy Service, Monitoring, or pxGrid
Network resources
Endpoints
The policy information point represents the point at which external information is communicated to the Policy Service persona. For example, external information could be a Lightweight Directory Access Protocol (LDAP) attribute.
This guide uses the following terms when discussing Cisco ISE deployment scenarios:
|
Term |
Definition |
|---|---|
|
Service |
A specific feature that a persona provides such as network access, profiling, posture, security group access, monitoring, and troubleshooting. |
|
Node |
An individual physical or virtual Cisco ISE appliance. |
|
Node Type |
The Cisco ISE node can assume any of the following personas: Administration, Policy Service, Monitoring |
|
Persona |
Determines the services provided by a node. A Cisco ISE node can assume any or all of the following personas: The menu options that are available through the administrative user interface depend on the role and personas that a node assumes. |
|
Role |
Determines if a node is a standalone, primary, or secondary node and applies only to Administration and Monitoring nodes. |
A Cisco ISE node can provide various services based on the persona that it assumes. Each node in a deployment can assume the Administration, Policy Service, pxGrid, and Monitoring personas. In a distributed deployment, you can have the following combination of nodes on your network:
Primary and secondary Administration nodes for high availability
A pair of Monitoring nodes for automatic failover
One or more Policy Service nodes for session failover
One or more pxGrid nodes for pxGrid services
A Cisco ISE node with the Administration persona allows you to perform all administrative operations on Cisco ISE. It handles all system-related configurations that are related to functionality such as authentication, authorization, and accounting. In a distributed deployment, you can have a maximum of two nodes running the Administration persona. The Administration persona can take on the standalone, primary, or secondary role.
A Cisco ISE node with the Policy Service persona provides network access, posture, guest access, client provisioning, and profiling services. This persona evaluates the policies and makes all the decisions. You can have more than one node assume this persona. Typically, there would be more than one Policy Service node in a distributed deployment. All Policy Service nodes that reside in the same high-speed Local Area Network (LAN) or behind a load balancer can be grouped together to form a node group. If one of the nodes in a node group fails, the other nodes detect the failure and reset any URL-redirected sessions.
At least one node in your distributed setup should assume the Policy Service persona.
A Cisco ISE node with the Monitoring persona functions as the log collector and stores log messages from all the Administration and Policy Service nodes in a network. This persona provides advanced monitoring and troubleshooting tools that you can use to effectively manage a network and resources. A node with this persona aggregates and correlates the data that it collects, and provides you with meaningful reports. Cisco ISE allows you to have a maximum of two nodes with this persona, and they can take on primary or secondary roles for high availability. Both the primary and secondary Monitoring nodes collect log messages. In case the primary Monitoring node goes down, the secondary Monitoring node automatically becomes the primary Monitoring node.
At least one node in your distributed setup should assume the Monitoring persona. We recommend that you do not have the Monitoring and Policy Service personas enabled on the same Cisco ISE node. We recommend that the Monitoring node be dedicated solely to monitoring for optimum performance.
You can use Cisco pxGrid to share the context-sensitive information from Cisco ISE session directory with other network systems such as ISE Eco system partner systems and other Cisco platforms. The pxGrid framework can also be used to exchange policy and configuration data between nodes like sharing tags and policy objects between Cisco ISE and third party vendors, and for other information exchanges. Cisco pxGrid also allows third party systems to invoke adaptive network control actions (EPS) to quarantine users/devices in response to a network or security event. The TrustSec information like tag definition, value, and description can be passed from Cisco ISE via TrustSec topic to other networks. The endpoint profiles with Fully Qualified Names (FQNs) can be passed from Cisco ISE to other networks through a endpoint profile meta topic. Cisco pxGrid also supports bulk download of tags and endpoint profiles.
You can publish and subscribe to SXP bindings (IP-SGT mappings) through pxGrid. For more information about SXP bindings, see Security Group Tag Exchange Protocol section in Cisco Identity Services Engine Administrator Guide.
In a high-availability configuration, Cisco pxGrid servers replicate information between the nodes through the PAN. When the PAN goes down, pxGrid server stops handling the client registration and subscription. You need to manually promote the PAN for the pxGrid server to become active.
A deployment that has a single Cisco ISE node is called a standalone deployment. This node runs the Administration, Policy Service, and Monitoring personas.
A deployment that has more than one Cisco ISE node is called a distributed deployment. To support failover and to improve performance, you can set up a deployment with multiple Cisco ISE nodes in a distributed fashion. In a Cisco ISE distributed deployment, administration and monitoring activities are centralized, and processing is distributed across the Policy Service nodes. Depending on your performance needs, you can scale your deployment. A Cisco ISE node can assume any of the following personas: Administration, Policy Service, and Monitoring.
Small Network Deployments
Medium-Sized Network Deployments
Large Network Deployments
The smallest Cisco ISE deployment consists of two Cisco ISE nodes with one Cisco ISE node functioning as the primary appliance in a small network.
The primary node provides all the configuration, authentication, and policy capabilities that are required for this network model, and the secondary Cisco ISE node functions in a backup role. The secondary node supports the primary node and maintains a functioning network whenever connectivity is lost between the primary node and network appliances, network resources, or RADIUS.
Centralized authentication, authorization, and accounting (AAA) operations between clients and the primary Cisco ISE node are performed using the RADIUS protocol. Cisco ISE synchronizes or replicates all of the content that resides on the primary Cisco ISE node with the secondary Cisco ISE node. Thus, your secondary node is current with the state of your primary node. In a small network deployment, this type of configuration model allows you to configure both your primary and secondary nodes on all RADIUS clients by using this type of deployment or a similar approach.
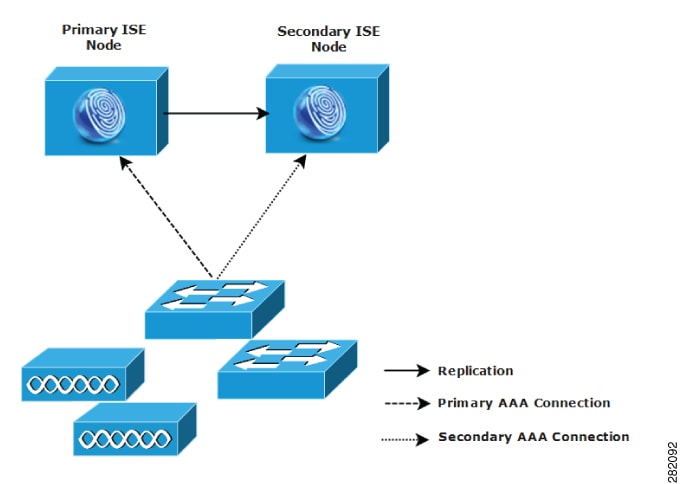
As the number of devices, network resources, users, and AAA clients increases in your network environment, you should change your deployment configuration from the basic small model and use more of a split or distributed deployment model.
In split Cisco ISE deployments, you continue to maintain primary and secondary nodes as described in a small Cisco ISE deployment. However, the AAA load is split between the two Cisco ISE nodes to optimize the AAA workflow. Each Cisco ISE appliance (primary or secondary) needs to be able to handle the full workload if there are any problems with AAA connectivity. Neither the primary node nor the secondary nodes handles all AAA requests during normal network operations because this workload is distributed between the two nodes.
The ability to split the load in this way directly reduces the stress on each Cisco ISE node in the system. In addition, splitting the load provides better loading while the functional status of the secondary node is maintained during the course of normal network operations.
In split Cisco ISE deployments, each node can perform its own specific operations, such as network admission or device administration, and still perform all the AAA functions in the event of a failure. If you have two Cisco ISE nodes that process authentication requests and collect accounting data from AAA clients, we recommend that you set up one of the Cisco ISE nodes to act as a log collector.
In addition, the split Cisco ISE deployment design provides an advantage because it allows for growth.
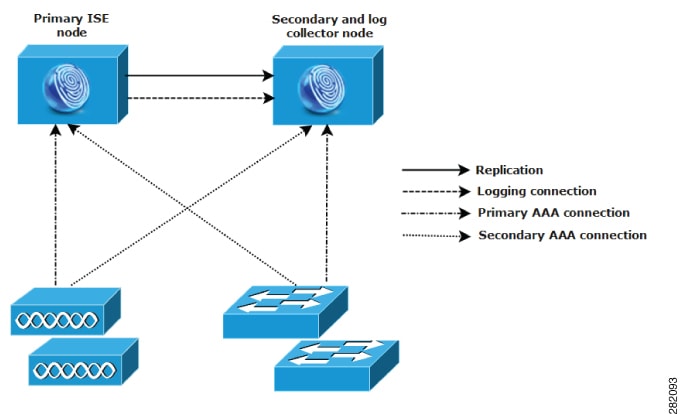
As small networks grow, you can keep pace and manage network growth by adding Cisco ISE nodes to create a medium-sized network. In medium-sized network deployments, you can dedicate the new nodes for all AAA functions, and use the original nodes for configuration and logging functions.
 Note |
In a medium-sized network deployment, you cannot enable the Policy Service persona on a node that runs the Administration persona, Monitoring persona, or both. You need dedicated policy service node(s). |
As the amount of log traffic increases in a network, you can choose to dedicate one or two of the secondary Cisco ISE nodes for log collection in your network.
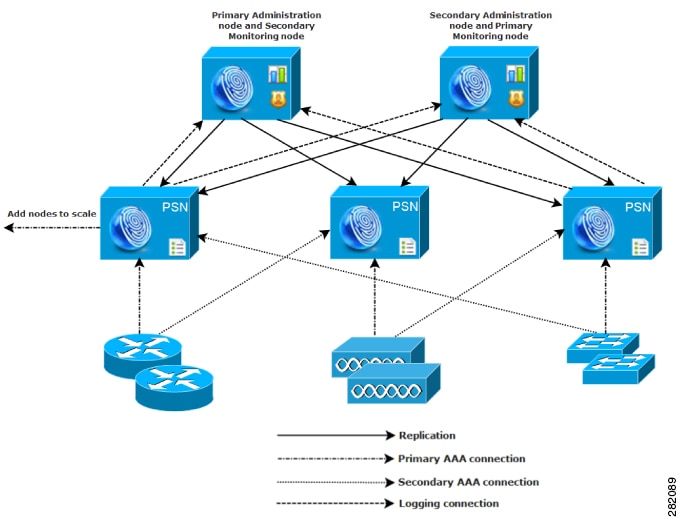
We recommend that you use centralized logging for large Cisco ISE networks. To use centralized logging, you must first set up a dedicated logging server that serves as a Monitoring persona (for monitoring and logging) to handle the potentially high syslog traffic that a large, busy network can generate.
Because syslog messages are generated for outbound log traffic, any RFC 3164-compliant syslog appliance can serve as the collector for outbound logging traffic. A dedicated logging server enables you to use the reports and alert features that are available in Cisco ISE to support all the Cisco ISE nodes.
You can also consider having the appliances send logs to both a Monitoring persona on the Cisco ISE node and a generic syslog server. Adding a generic syslog server provides a redundant backup if the Monitoring persona on the Cisco ISE node goes down.
In large centralized networks, you should use a load balancer, which simplifies the deployment of AAA clients. Using a load balancer requires only a single entry for the AAA servers, and the load balancer optimizes the routing of AAA requests to the available servers.
However, having only a single load balancer introduces the potential for having a single point of failure. To avoid this potential issue, deploy two load balancers to ensure a measure of redundancy and failover. This configuration requires you to set up two AAA server entries in each AAA client, and this configuration remains consistent throughout the network.
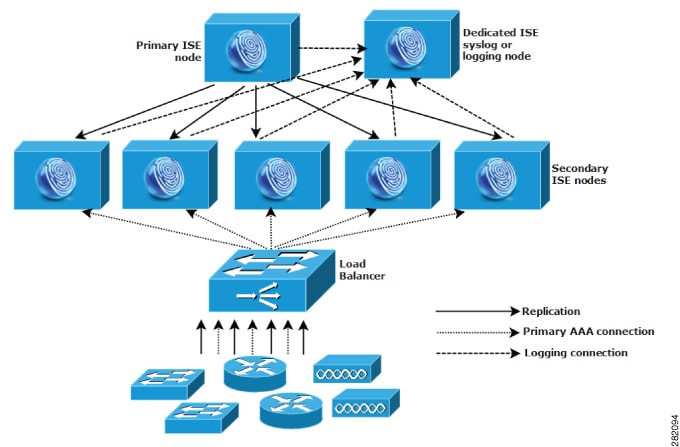
Dispersed Cisco ISE network deployments are most useful for organizations that have a main campus with regional, national, or satellite locations elsewhere. The main campus is where the primary network resides, is connected to additional LANs, ranges in size from small to large, and supports appliances and users in different geographical regions and locations.
Large remote sites can have their own AAA infrastructure for optimal AAA performance. A centralized management model helps maintain a consistent, synchronized AAA policy. A centralized configuration model uses a primary Cisco ISE node with secondary Cisco ISE nodes. We still recommend that you use a separate Monitoring persona on the Cisco ISE node, but each remote location should retain its own unique network requirements.
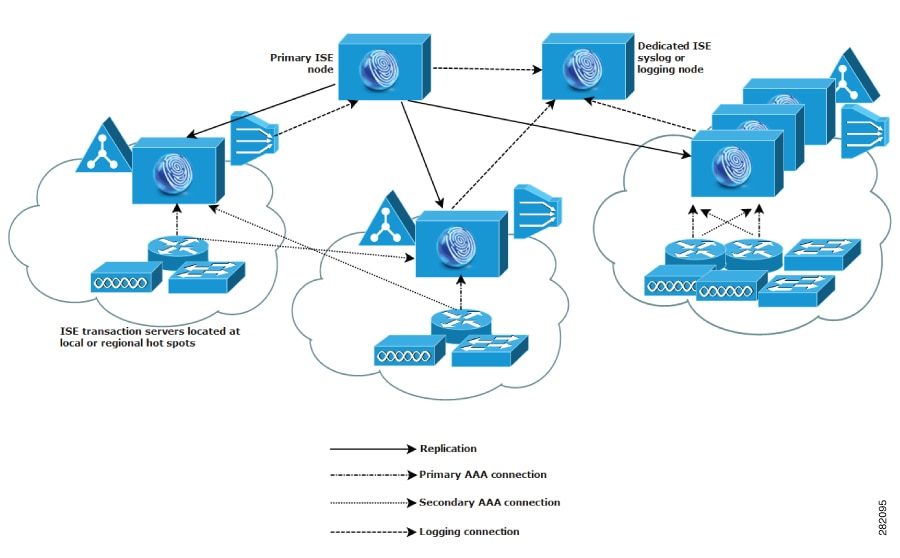
Verify if a central or external database is used, such as Microsoft Active Directory or Lightweight Directory Access Protocol (LDAP). Each remote site should have a synchronized instance of the external database that is available for Cisco ISE to access for optimizing AAA performance.
The location of AAA clients is important. You should locate the Cisco ISE nodes as close as possible to the AAA clients to reduce network latency effects and the potential for loss of access that is caused by WAN failures.
Cisco ISE has console access for some functions such as backup. Consider using a terminal at each site, which allows for direct, secure console access that bypasses network access to each node.
If small, remote sites are in close proximity and have reliable WAN connectivity to other sites, consider using a Cisco ISE node as a backup for the local site to provide redundancy.
Domain Name System (DNS) should be properly configured on all Cisco ISE nodes to ensure access to the external databases.
For information about the deployment sizing guidelines and the scale limits for different types of Cisco ISE deployment, see Performance and Scalability Guide for Cisco Identity Services Engine.
|
Deployment Model |
Platform |
Max Number of Dedicated PSNs |
Max RADIUS Sessions Per Deployment |
Max Passive Identity Sessions Per Deployment |
Max Merged and Easy Connect Sessions (Shared PSNs) |
Max Merged and Easy Connect Sessions (Dedicated PSNs) |
|---|---|---|---|---|---|---|
|
Standalone |
3515 |
0 |
7500 |
100,000 |
1,000 |
N/A |
|
3595 |
0 |
20,000 |
300,000 |
2,000 |
N/A |
|
|
PAN and MnT on same node and Dedicated PSNs |
3515 as PAN and MnT |
5 |
7,500 |
100,000 |
1,000 |
5,000 |
|
3595 as PAN and MnT |
5 |
20,000 |
300,000 |
2,000 |
10,000 |
|
|
Dedicated (PAN, MnT, PXG, and PSN Nodes) |
3595 as PAN and MnT |
50 |
500,000 |
300,000 |
N/A |
50,000 |
|
Dedicated (PAN, MnT, PXG, and PSN Nodes) |
Virtual Large SNS-3595 as PAN and MnT |
50 |
500,000 |
300,000 |
N/A |
50,000 |
|
pxGrid Scaling Per Deployment |
Platform |
Max PSNs |
Max PXGs |
Max pxGrid Subscribers (Shared PSN+PXG) |
Max pxGrid Subscribers (Dedicated PSN/PXG) |
|---|---|---|---|---|---|
|
Standalone - All personas on same node (2 nodes redundant) |
3515 |
0 |
0 |
2 |
N/A |
|
3595 |
0 |
0 |
2 |
N/A |
|
|
3515 as PAN + MnT/PXG |
5* |
2* |
5 |
15 |
|
3595 as PAN and MnT/PXG |
5* |
2* |
5 |
15 |
|
|
Dedicated - All personas on dedicated nodes (Minimum 6 nodes redundant) |
3595 as PAN and MnT |
50 |
2 |
N/A |
25 |
|
Scalability with pxGrid per PXG Node |
Platform |
Max Subscribers per PXG Node |
|||
|
Dedicated pxGrid nodes (Max Publish Rate Gated by Total Deployment Size) |
3515 |
15 |
|||
|
3595 |
25 |
||||
|
Deployment Type |
Platform |
Max PSNs |
Max PXGs |
Max pxGrid Subscribers: Shared PAN+MNT+PXG |
Max pxGrid Subscribers: Dedicated PSN/PXG |
|---|---|---|---|---|---|
|
Standalone All personas on same node 2 nodes redundant |
3515 |
0 |
0 |
20 |
N/A |
| 3595 | 0 | 0 | 30 | N/A | |
|
Medium PAN+MnT+PXG on same node and dedicated PSNs -OR- PAN+MnT and dedicated PSN & PXG Minimum 4 nodes redundant |
3515 as PAN+MNT/PXG |
5* |
2* |
140 |
400 |
| 3595 as PAN+MNT/PXG | 5* | 2* | 160 | 400 | |
| 3595 as PAN+MNT/PXG | 5* | 3* | 160 | 600 | |
|
Dedicated All personas on dedicated nodes Minimum 6 nodes redundant |
3595 as PAN and MNT |
50 |
4 |
N/A |
800 |
| 3595 as PAN and MNT | 50 | 4 | N/A | 800 |
 Note |
Cisco ISE 2.3 and above releases support pxGrid v2, but require v2 Subscribers/Publishers. Each pxGrid v2 node can be Active. |
|
Platform |
Max Subscribers per pxGrid node |
|---|---|
|
3515 |
200 |
|
3595 |
200 |
Maximum publish rate is gated by the total deployment size.
To ensure that Cisco ISE can interoperate with network switches and that functions from Cisco ISE are successful across the network segment, you must configure your network switches with certain required Network Time Protocol (NTP), RADIUS/AAA, IEEE 802.1X, MAC Authentication Bypass (MAB), and other settings.
|
For information about setting up Cisco ISE with WLC, see Cisco ISE with WLC Setup Video. |