Restrictions for Loop Detection Guard
Loop detection guard can be configured only on Layer 2 physical interfaces. Layer 3 ports and virtual interfaces, such as port channels, switch virtual interfaces (SVIs), and tunnels, are not supported.
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Loop detection guard can be configured only on Layer 2 physical interfaces. Layer 3 ports and virtual interfaces, such as port channels, switch virtual interfaces (SVIs), and tunnels, are not supported.
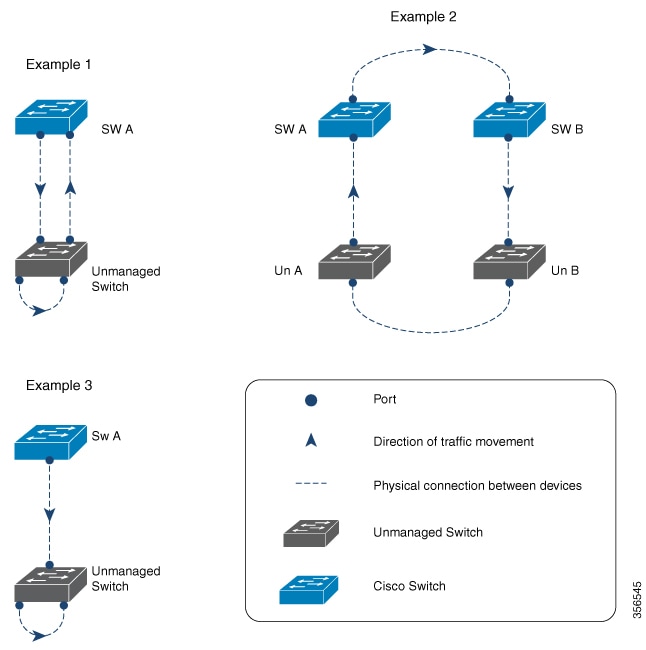
A computer network can experience a network loop where there is more than one Layer 2 path between two endpoints. This is possible when there are multiple connections between two switches in a network or two ports on the same switch are connected to each other. The following figure shows a few examples of a network loop:
Example 1: Switch SW A, which is within the network, is sending traffic to an unmanaged switch on one port and receiving traffic from the same unmanaged switch, on another port. On the unmanaged switch, the port receiving traffic is connected to the port sending traffic back to the SW A in the network, resulting in a network loop.
Example 2: This example shows a network loop involving four switches, two within the network (SW A and SW B) and two unmanaged switches (Un A and Un B). Traffic is moving in the following direction SW A to SW B to Un B to Un A and back to SW A, resulting in a network loop.
Example 3: Two ports on the unmanaged switch are connected to each other, resulting in a network loop.
While Spanning Tree Protocol (STP) is normally the protocol that is configured for this purpose (to prevent network loops), loop detection guard is suited to situations where there may be unmanaged switches in a network that do not understand STP, or where STP is not configured on the network.
Loop detection guard is enabled at the interface level. To detect loops, the system sends loop-detect frames from the interface, at preconfigured intervals. When a loop is detected, the configured action is taken.
Loop detection guard is disabled by default. When you enable the feature, you can configure one of these actions:
Error-disable the port sending traffic.
Error-disable the port receiving traffic (default).
Display an error message and not disable any port.
When a port is error-disabled, no traffic is sent or received on that port.
When both loop detection guard and STP are enabled on a device, STP takes over monitoring the network for loops. In this case loop-detect packets are neither received nor processed in the network.
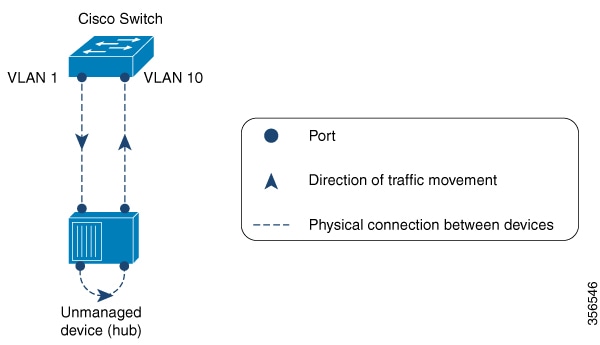
We do not recommend configuring this feature on a switch that is connected to a hub for these reasons: The hub floods traffic to all of its interfaces. If the switch in your network is receiving traffic from the same hub, but on a port in a different VLAN, you may be inadvertently error-disabling those destination ports. The figure below illustrates such a situation. The port in VLAN 1 is sending traffic to the hub. The switch is also receiving traffic from the same hub, but on a port in a different VLAN, that is, VLAN 10. If you configure loop detection guard (and you have configured the default action of error-disabling the destination port), then the port in VLAN 10 is blocked. Configuring the option to display a message (instead of error-disabling a port) is not recommended either, because the system displays as many messages as the number of interfaces configured in the hub, resulting in a CPU overload.
The feature is disabled by default. Complete the following steps to enable loop detection guard and configure the action that you want the system to take when a loop is detected:
| Command or Action | Purpose | |||
|---|---|---|---|---|
|
Step 1 |
enable Example: |
Enables privileged EXEC mode. Enter your password if prompted. |
||
|
Step 2 |
configure terminal Example: |
Enters global configuration mode. |
||
|
Step 3 |
interface { interface-id| subinterface-id| vlan-id} Example: |
Enters interface configuration mode. Specify only a physical interface to configure loop detection guard on the device. Layer 3 ports and virtual interfaces like PortChannels, switch virtual interfaces (SVIs), and tunnels are not supported. |
||
|
Step 4 |
[ no] loopdetect Example: |
Enables loop detection guard on the device. Loopdetect frames are sent from the configured interface. Use the loopdetect command without any keyword to enable loop detection guard. Use the no form of this command to disable this feature.
|
||
|
Step 5 |
[ no] loopdetect{ time| action syslog| source-port} Example: |
Specifies the frequency at which loop-detect frames are sent and the action the system takes when a loop is detected. If you do not specify an action, the destination port is error-disabled by default. You can configure the following:
In the example configuration on the left ( |
||
|
Step 6 |
end Example: |
Returns to privileged EXEC mode. |
||
|
Step 7 |
show loopdetect Example: |
Displays all the interfaces where loop detection guard is enabled, the frequency at which loop-detect packets are sent, and the status of the physical interface. |
| Related Topic | Document Title |
|---|---|
|
For complete syntax and usage information for the commands used in this chapter. |
See the Layer 2/3 Commands section of the Command Reference (Catalyst 9600 Series Switches) |
This table provides release and related information for features explained in this module.
These features are available on all releases subsequent to the one they were introduced in, unless noted otherwise.
|
Release |
Feature |
Feature Information |
|---|---|---|
|
Cisco IOS XE Amsterdam 17.2.1 |
Loop Detection Guard |
Loop detection guard prevents network loops in either networks that are not configured with STP or unmanaged devices in networks that are configured with STP. |
Use Cisco Feature Navigator to find information about platform and software image support. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn.