Contents
- Configuring Accounting
- Finding Feature Information
- Prerequisites for Configuring Accounting
- Restrictions for Configuring Accounting
- Information About Configuring Accounting
- Named Method Lists for Accounting
- Method Lists and Server Groups
- AAA Accounting Methods
- Accounting Record Types
- Accounting Methods
- AAA Accounting Types
- Network Accounting
- EXEC Accounting
- Command Accounting
- Connection Accounting
- System Accounting
- Resource Accounting
- AAA Resource Failure Stop Accounting
- AAA Resource Accounting for Start-Stop Records
- VRRS Accounting
- VRRS Accounting Plug-in
- AAA Accounting Enhancements
- AAA Broadcast Accounting
- AAA Session MIB
- Accounting Attribute-Value Pairs
- How to Configure AAA Accounting
- Configuring AAA Accounting Using Named Method Lists
- Configuring RADIUS System Accounting
- Suppressing Generation of Accounting Records for Null Username Sessions
- Generating Interim Accounting Records
- Generating Accounting Records for Failed Login or Session
- Specifying Accounting NETWORK-Stop Records Before EXEC-Stop Records
- Configuring AAA Resource Failure Stop Accounting
- Configuring AAA Resource Accounting for Start-Stop Records
- Configuring AAA Broadcast Accounting
- Configuring Per-DNIS AAA Broadcast Accounting
- Configuring AAA Session MIB
- Configuring VRRS Accounting
- Establishing a Session with a Router if the AAA Server is Unreachable
- Monitoring Accounting
- Troubleshooting Accounting
- Configuration Examples for AAA Accounting
- Example Configuring Named Method List
- Example Configuring AAA Resource Accounting
- Example Configuring AAA Broadcast Accounting
- Example Configuring Per-DNIS AAA Broadcast Accounting
- Example AAA Session MIB
- Example Configuring VRRS Accounting
- Additional References
- Feature Information for Configuring Accounting
Configuring Accounting
The AAA Accounting feature allows the services that users are accessing and the amount of network resources that users are consuming to be tracked. When AAA Accounting is enabled, the network access server reports user activity to the TACACS+ or RADIUS security server (depending on which security method is implemented) in the form of accounting records. Each accounting record contains accounting attribute-value (AV) pairs and is stored on the security server. This data can then be analyzed for network management, client billing, and auditing.
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest feature information and caveats, see the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the Feature Information Table at the end of this document.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
Prerequisites for Configuring Accounting
The following tasks must be performed before configuring accounting using named method lists:
- Enable AAA on the network access server by using the aaa new-modelcommand in global configuration mode.
- Define the characteristics of the RADIUS or TACACS+ security server if RADIUS or TACACS+ authorization is issued. For more information about configuring the Cisco network access server to communicate with the RADIUS security server, see the Configuring RADIUS module. For more information about configuring the Cisco network access server to communicate with the TACACS+ security server, see the Configuring TACACS+ module.
Restrictions for Configuring Accounting
- Accounting information can be sent simultaneously to a maximum of only four AAA servers.
- For Service Selection Gateway (SSG) systems, the aaa accounting network broadcast command broadcasts only start-stop accounting records. If interim accounting records are configured using the ssg accounting interval command, the interim accounting records are sent only to the configured default RADIUS server.
Information About Configuring Accounting
- Named Method Lists for Accounting
- AAA Accounting Types
- AAA Accounting Enhancements
- Accounting Attribute-Value Pairs
Named Method Lists for Accounting
Similar to authentication and authorization method lists, method lists for accounting define the way accounting is performed and the sequence in which these methods are performed.
Named accounting method lists allow particular security protocol to be designated and used on specific lines or interfaces for accounting services. The only exception is the default method list (which is named âdefaultâ). The default method list is automatically applied to all interfaces except those that have a named method list explicitly defined. A defined method list overrides the default method list.
A method list is simply a named list describing the accounting methods to be queried (such as RADIUS or TACACS+), in sequence. Method lists allow one or more security protocols to be designated and used for accounting, thus ensuring a backup system for accounting in case the initial method fails. Cisco IOS software uses the first method listed to support accounting; if that method fails to respond, the Cisco IOS software selects the next accounting method listed in the method list. This process continues until there is successful communication with a listed accounting method, or all methods defined are exhausted.
Accounting method lists are specific to the type of accounting being requested. AAA supports seven different types of accounting:
- Network --Provides information for all PPP, SLIP, or ARAP sessions, including packet and byte counts.
- EXEC --Provides information about user EXEC terminal sessions of the network access server.
- Commands --Provides information about the EXEC mode commands that a user issues. Command accounting generates accounting records for all EXEC mode commands, including global configuration commands, associated with a specific privilege level.
- Connection --Provides information about all outbound connections made from the network access server, such as Telnet, local-area transport (LAT), TN3270, packet assembler/disassembler (PAD), and rlogin.
- System --Provides information about system-level events.
- Resource --Provides âstartâ and âstopâ records for calls that have passed user authentication, and provides âstopâ records for calls that fail to authenticate.
- VRRS --Provides information about Virtual Router Redundancy Service (VRRS).
 Note | System accounting does not use named accounting lists; only the default list for system accounting can be defined. |
Once again, when a named method list is created, a particular list of accounting methods for the indicated accounting type are defined.
Accounting method lists must be applied to specific lines or interfaces before any of the defined methods are performed. The only exception is the default method list (which is named âdefaultâ). If the aaa accounting command for a particular accounting type is issued without specifying a named method list, the default method list is automatically applied to all interfaces or lines except those that have a named method list explicitly defined (A defined method list overrides the default method list). If no default method list is defined, then no accounting takes place.
This section includes the following subsections:
Method Lists and Server Groups
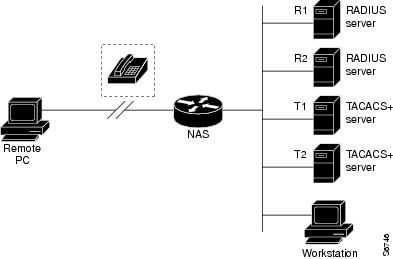
A server group is a way to group existing RADIUS or TACACS+ server hosts for use in method lists. The figure below shows a typical AAA network configuration that includes four security servers: R1 and R2 are RADIUS servers, and T1 and T2 are TACACS+ servers. R1 and R2 comprise the group of RADIUS servers. T1 and T2 comprise the group of TACACS+ servers.
Cisco IOS software, RADIUS and TACACS+ server configurations are global. A subset of the configured server hosts can be specified using server groups. These server groups can be used for a particular service. For example, server groups allow R1 and R2 to be defined as separate server groups (SG1 and SG2), and T1 and T2 as separate server groups (SG3 and SG4). This means either R1 and T1 (SG1 and SG3) or R2 and T2 (SG2 and SG4) can be specified in the method list, which provides more flexibility in the way that RADIUS and TACACS+ resources are assigned.
Server groups also can include multiple host entries for the same server, as long as each entry has a unique identifier. The combination of an IP address and a UDP port number creates a unique identifier, allowing different ports to be individually defined as RADIUS hosts providing a specific AAA service. In other words, this unique identifier enables RADIUS requests to be sent to different UDP ports on a server from the same IP address. If two different host entries on the same RADIUS server are configured for the same service--for example, accounting--the second host entry configured acts as failover backup to the first one. Using this example, if the first host entry fails to provide accounting services, the network access server tries the second host entry configured on the same device for accounting services (The RADIUS host entries are tried in the order in which they are configured).
For more information about configuring server groups and about configuring server groups based on Dialed Number Identification Service (DNIS) numbers, see the âConfiguring RADIUSâ or âConfiguring TACACS+â module in the Cisco IOS Security Configuration Guide: Securing User Services .
AAA Accounting Methods
The Cisco IOS software supports the following two methods for accounting:
- TACACS+--The network access server reports user activity to the TACACS+ security server in the form of accounting records. Each accounting record contains accounting AV pairs and is stored on the security server.
- RADIUS--The network access server reports user activity to the RADIUS security server in the form of accounting records. Each accounting record contains accounting AV pairs and is stored on the security server.
Accounting Record Types
For minimal accounting, use the stop-only keyword, which instructs the specified method (RADIUS or TACACS+) to send a stop record accounting notice at the end of the requested user process. For more accounting information, use the start-stop keyword to send a start accounting notice at the beginning of the requested event and a stop accounting notice at the end of the event. To stop all accounting activities on this line or interface, use the none keyword.
Accounting Methods
The table below lists the supported accounting methods.
|
Keyword |
Description |
|---|---|
|
group radius |
Uses the list of all RADIUS servers for accounting. |
|
group tacacs+ |
Uses the list of all TACACS+ servers for accounting. |
|
group group-name |
Uses a subset of RADIUS or TACACS+ servers for accounting as defined by the server group group-name. |
The method argument refers to the actual method the authentication algorithm tries. Additional methods of authentication are used only if the previous method returns an error, not if it fails. To specify that the authentication should succeed even if all other methods return an error, specify additional methods in the command. For example, to create a method list named acct_tac1 that specifies RADIUS as the backup method of authentication in the event that TACACS+ authentication returns an error, enter the following command:
aaa accounting network acct_tac1 stop-only group tacacs+ group radius
To create a default list that is used when a named list is not specified in the aaa accountingcommand, use the default keyword followed by the methods that are wanted to be used in default situations. The default method list is automatically applied to all interfaces.
For example, to specify RADIUS as the default method for user authentication during login, enter the following command:
aaa accounting network default stop-only group radius
AAA Accounting supports the following methods:
- group tacacs --To have the network access server send accounting information to a TACACS+ security server, use the group tacacs+ method keyword.
- group radius --To have the network access server send accounting information to a RADIUS security server, use the group radius method keyword.
- group group-name --To specify a subset of RADIUS or TACACS+ servers to use as the accounting method, use the aaa accountingcommand with the group group-name method. To specify and define the group name and the members of the group, use the aaa group server command. For example, use the aaa group server command to first define the members of group loginrad:
aaa group server radius loginrad server 172.16.2.3 server 172.16.2 17 server 172.16.2.32
This command specifies RADIUS servers 172.16.2.3, 172.16.2.17, and 172.16.2.32 as members of the group loginrad.
To specify group loginrad as the method of network accounting when no other method list has been defined, enter the following command:
aaa accounting network default start-stop group loginrad
Before a group name can be used as the accounting method, communication with the RADIUS or TACACS+ security server must be enabled.
AAA Accounting Types
- Network Accounting
- EXEC Accounting
- Command Accounting
- Connection Accounting
- System Accounting
- Resource Accounting
- VRRS Accounting
Network Accounting
Network accounting provides information for all PPP, SLIP, or ARAP sessions, including packet and byte counts.
The following example shows the information contained in a RADIUS network accounting record for a PPP user who comes in through an EXEC session:
Wed Jun 27 04:44:45 2001
NAS-IP-Address = â172.16.25.15â
NAS-Port = 5
User-Name = âusername1â
Client-Port-DNIS = â4327528â
Caller-ID = â562â
Acct-Status-Type = Start
Acct-Authentic = RADIUS
Service-Type = Exec-User
Acct-Session-Id = â0000000Dâ
Acct-Delay-Time = 0
User-Id = âusername1â
NAS-Identifier = â172.16.25.15â
Wed Jun 27 04:45:00 2001
NAS-IP-Address = â172.16.25.15â
NAS-Port = 5
User-Name = âusername1â
Client-Port-DNIS = â4327528â
Caller-ID = â562â
Acct-Status-Type = Start
Acct-Authentic = RADIUS
Service-Type = Framed
Acct-Session-Id = â0000000Eâ
Framed-IP-Address = â10.1.1.2â
Framed-Protocol = PPP
Acct-Delay-Time = 0
User-Id = âusername1â
NAS-Identifier = â172.16.25.15â
Wed Jun 27 04:47:46 2001
NAS-IP-Address = â172.16.25.15â
NAS-Port = 5
User-Name = âusername1â
Client-Port-DNIS = â4327528â
Caller-ID = â562â
Acct-Status-Type = Stop
Acct-Authentic = RADIUS
Service-Type = Framed
Acct-Session-Id = â0000000Eâ
Framed-IP-Address = â10.1.1.2â
Framed-Protocol = PPP
Acct-Input-Octets = 3075
Acct-Output-Octets = 167
Acct-Input-Packets = 39
Acct-Output-Packets = 9
Acct-Session-Time = 171
Acct-Delay-Time = 0
User-Id = âusername1â
NAS-Identifier = â172.16.25.15â
Wed Jun 27 04:48:45 2001
NAS-IP-Address = â172.16.25.15â
NAS-Port = 5
User-Name = âusername1â
Client-Port-DNIS = â4327528â
Caller-ID = â408â
Acct-Status-Type = Stop
Acct-Authentic = RADIUS
Service-Type = Exec-User
Acct-Session-Id = â0000000Dâ
Acct-Delay-Time = 0
User-Id = âusername1â
NAS-Identifier = â172.16.25.15â
The following example shows the information contained in a TACACS+ network accounting record for a PPP user who first started an EXEC session:
Wed Jun 27 04:00:35 2001 172.16.25.15 username1 tty4 562/4327528 starttask_id=28 service=shell Wed Jun 27 04:00:46 2001 172.16.25.15 username1 tty4 562/4327528 starttask_id=30 addr=10.1.1.1 service=ppp Wed Jun 27 04:00:49 2001 172.16.25.15 username1 tty4 408/4327528 update task_id=30 addr=10.1.1.1 service=ppp protocol=ip addr=10.1.1.1 Wed Jun 27 04:01:31 2001 172.16.25.15 username1 tty4 562/4327528 stoptask_id=30 addr=10.1.1.1 service=ppp protocol=ip addr=10.1.1.1 bytes_in=2844 bytes_out=1682 paks_in=36 paks_out=24 elapsed_time=51 Wed Jun 27 04:01:32 2001 172.16.25.15 username1 tty4 562/4327528 stoptask_id=28 service=shell elapsed_time=57
 Note | The precise format of accounting packets records may vary depending on the security server daemon. |
The following example shows the information contained in a RADIUS network accounting record for a PPP user who comes in through autoselect:
Wed Jun 27 04:30:52 2001
NAS-IP-Address = â172.16.25.15â
NAS-Port = 3
User-Name = âusername1â
Client-Port-DNIS = â4327528â
Caller-ID = â562â
Acct-Status-Type = Start
Acct-Authentic = RADIUS
Service-Type = Framed
Acct-Session-Id = â0000000Bâ
Framed-Protocol = PPP
Acct-Delay-Time = 0
User-Id = âusername1â
NAS-Identifier = â172.16.25.15â
Wed Jun 27 04:36:49 2001
NAS-IP-Address = â172.16.25.15â
NAS-Port = 3
User-Name = âusername1â
Client-Port-DNIS = â4327528â
Caller-ID = â562â
Acct-Status-Type = Stop
Acct-Authentic = RADIUS
Service-Type = Framed
Acct-Session-Id = â0000000Bâ
Framed-Protocol = PPP
Framed-IP-Address = â10.1.1.1â
Acct-Input-Octets = 8630
Acct-Output-Octets = 5722
Acct-Input-Packets = 94
Acct-Output-Packets = 64
Acct-Session-Time = 357
Acct-Delay-Time = 0
User-Id = âusername1â
NAS-Identifier = â172.16.25.15â
The following example shows the information contained in a TACACS+ network accounting record for a PPP user who comes in through autoselect:
Wed Jun 27 04:02:19 2001 172.16.25.15 username1 Async5 562/4327528 starttask_id=35 service=ppp Wed Jun 27 04:02:25 2001 172.16.25.15 username1 Async5 562/4327528 update task_id=35 service=ppp protocol=ip addr=10.1.1.2 Wed Jun 27 04:05:03 2001 172.16.25.15 username1 Async5 562/4327528 stoptask_id=35 service=ppp protocol=ip addr=10.1.1.2 bytes_in=3366 bytes_out=2149 paks_in=42 paks_out=28 elapsed_time=164
EXEC Accounting
EXEC accounting provides information about user EXEC terminal sessions (user shells) on the network access server, including username, date, start and stop times, the access server IP address, and (for dial-in users) the telephone number the call originated from.
The following example shows the information contained in a RADIUS EXEC accounting record for a dial-in user:
Wed Jun 27 04:26:23 2001
NAS-IP-Address = â172.16.25.15â
NAS-Port = 1
User-Name = âusername1â
Client-Port-DNIS = â4327528â
Caller-ID = â5622329483â
Acct-Status-Type = Start
Acct-Authentic = RADIUS
Service-Type = Exec-User
Acct-Session-Id = â00000006â
Acct-Delay-Time = 0
User-Id = âusername1â
NAS-Identifier = â172.16.25.15â
Wed Jun 27 04:27:25 2001
NAS-IP-Address = â172.16.25.15â
NAS-Port = 1
User-Name = âusername1â
Client-Port-DNIS = â4327528â
Caller-ID = â5622329483â
Acct-Status-Type = Stop
Acct-Authentic = RADIUS
Service-Type = Exec-User
Acct-Session-Id = â00000006â
Acct-Session-Time = 62
Acct-Delay-Time = 0
User-Id = âusername1â
NAS-Identifier = â172.16.25.15â
The following example shows the information contained in a TACACS+ EXEC accounting record for a dial-in user:
Wed Jun 27 03:46:21 2001 172.16.25.15 username1 tty3 5622329430/4327528 start task_id=2 service=shell Wed Jun 27 04:08:55 2001 172.16.25.15 username1 tty3 5622329430/4327528 stop task_id=2 service=shell elapsed_time=1354
The following example shows the information contained in a RADIUS EXEC accounting record for a Telnet user:
Wed Jun 27 04:48:32 2001
NAS-IP-Address = â172.16.25.15â
NAS-Port = 26
User-Name = âusername1â
Caller-ID = â10.68.202.158â
Acct-Status-Type = Start
Acct-Authentic = RADIUS
Service-Type = Exec-User
Acct-Session-Id = â00000010â
Acct-Delay-Time = 0
User-Id = âusername1â
NAS-Identifier = â172.16.25.15â
Wed Jun 27 04:48:46 2001
NAS-IP-Address = â172.16.25.15â
NAS-Port = 26
User-Name = âusername1â
Caller-ID = â10.68.202.158â
Acct-Status-Type = Stop
Acct-Authentic = RADIUS
Service-Type = Exec-User
Acct-Session-Id = â00000010â
Acct-Session-Time = 14
Acct-Delay-Time = 0
User-Id = âusername1â
NAS-Identifier = â172.16.25.15â
The following example shows the information contained in a TACACS+ EXEC accounting record for a Telnet user:
Wed Jun 27 04:06:53 2001 172.16.25.15 username1 tty26 10.68.202.158 starttask_id=41 service=shell Wed Jun 27 04:07:02 2001 172.16.25.15 username1 tty26 10.68.202.158 stoptask_id=41 service=shell elapsed_time=9
Command Accounting
Command accounting provides information about the EXEC shell commands for a specified privilege level that are being executed on a network access server. Each command accounting record includes a list of the commands executed for that privilege level, as well as the date and time each command was executed, and the user who executed it.
The following example shows the information contained in a TACACS+ command accounting record for privilege level 1:
Wed Jun 27 03:46:47 2001 172.16.25.15 username1 tty3 5622329430/4327528 stop task_id=3 service=shell priv-lvl=1 cmd=show version <cr> Wed Jun 27 03:46:58 2001 172.16.25.15 username1 tty3 5622329430/4327528 stop task_id=4 service=shell priv-lvl=1 cmd=show interfaces Ethernet 0 <cr> Wed Jun 27 03:47:03 2001 172.16.25.15 username1 tty3 5622329430/4327528 stop task_id=5 service=shell priv-lvl=1 cmd=show ip route <cr>
The following example shows the information contained in a TACACS+ command accounting record for privilege level 15:
Wed Jun 27 03:47:17 2001 172.16.25.15 username1 tty3 5622329430/4327528 stop task_id=6 service=shell priv-lvl=15 cmd=configure terminal <cr> Wed Jun 27 03:47:21 2001 172.16.25.15 username1 tty3 5622329430/4327528 stop task_id=7 service=shell priv-lvl=15 cmd=interface Serial 0 <cr> Wed Jun 27 03:47:29 2001 172.16.25.15 username1 tty3 5622329430/4327528 stop task_id=8 service=shell priv-lvl=15 cmd=ip address 10.1.1.1 255.255.255.0 <cr>
 Note | The Cisco implementation of RADIUS does not support command accounting. |
Connection Accounting
Connection accounting provides information about all outbound connections made from the network access server such as Telnet, LAT, TN3270, PAD, and rlogin.
The following example shows the information contained in a RADIUS connection accounting record for an outbound Telnet connection:
Wed Jun 27 04:28:00 2001
NAS-IP-Address = â172.16.25.15â
NAS-Port = 2
User-Name = âusername1â
Client-Port-DNIS = â4327528â
Caller-ID = â5622329477â
Acct-Status-Type = Start
Acct-Authentic = RADIUS
Service-Type = Login
Acct-Session-Id = â00000008â
Login-Service = Telnet
Login-IP-Host = â10.68.202.158â
Acct-Delay-Time = 0
User-Id = âusername1â
NAS-Identifier = â172.16.25.15â
Wed Jun 27 04:28:39 2001
NAS-IP-Address = â172.16.25.15â
NAS-Port = 2
User-Name = âusername1â
Client-Port-DNIS = â4327528â
Caller-ID = â5622329477â
Acct-Status-Type = Stop
Acct-Authentic = RADIUS
Service-Type = Login
Acct-Session-Id = â00000008â
Login-Service = Telnet
Login-IP-Host = â10.68.202.158â
Acct-Input-Octets = 10774
Acct-Output-Octets = 112
Acct-Input-Packets = 91
Acct-Output-Packets = 99
Acct-Session-Time = 39
Acct-Delay-Time = 0
User-Id = âusername1â
NAS-Identifier = â172.16.25.15â
The following example shows the information contained in a TACACS+ connection accounting record for an outbound Telnet connection:
Wed Jun 27 03:47:43 2001 172.16.25.15 username1 tty3 5622329430/4327528 start task_id=10 service=connection protocol=telnet addr=10.68.202.158 cmd=telnet username1-sun Wed Jun 27 03:48:38 2001 172.16.25.15 username1 tty3 5622329430/4327528 stop task_id=10 service=connection protocol=telnet addr=10.68.202.158 cmd=telnet username1-sun bytes_in=4467 bytes_out=96 paks_in=61 paks_out=72 elapsed_time=55
The following example shows the information contained in a RADIUS connection accounting record for an outbound rlogin connection:
Wed Jun 27 04:29:48 2001
NAS-IP-Address = â172.16.25.15â
NAS-Port = 2
User-Name = âusername1â
Client-Port-DNIS = â4327528â
Caller-ID = â5622329477â
Acct-Status-Type = Start
Acct-Authentic = RADIUS
Service-Type = Login
Acct-Session-Id = â0000000Aâ
Login-Service = Rlogin
Login-IP-Host = â10.68.202.158â
Acct-Delay-Time = 0
User-Id = âusername1â
NAS-Identifier = â172.16.25.15â
Wed Jun 27 04:30:09 2001
NAS-IP-Address = â172.16.25.15â
NAS-Port = 2
User-Name = âusername1â
Client-Port-DNIS = â4327528â
Caller-ID = â5622329477â
Acct-Status-Type = Stop
Acct-Authentic = RADIUS
Service-Type = Login
Acct-Session-Id = â0000000Aâ
Login-Service = Rlogin
Login-IP-Host = â10.68.202.158â
Acct-Input-Octets = 18686
Acct-Output-Octets = 86
Acct-Input-Packets = 90
Acct-Output-Packets = 68
Acct-Session-Time = 22
Acct-Delay-Time = 0
User-Id = âusername1â
NAS-Identifier = â172.16.25.15â
The following example shows the information contained in a TACACS+ connection accounting record for an outbound rlogin connection:
Wed Jun 27 03:48:46 2001 172.16.25.15 username1 tty3 5622329430/4327528 start task_id=12 service=connection protocol=rlogin addr=10.68.202.158 cmd=rlogin username1-sun /user username1 Wed Jun 27 03:51:37 2001 172.16.25.15 username1 tty3 5622329430/4327528 stop task_id=12 service=connection protocol=rlogin addr=10.68.202.158 cmd=rlogin username1-sun /user username1 bytes_in=659926 bytes_out=138 paks_in=2378 paks_ out=1251 elapsed_time=171
The following example shows the information contained in a TACACS+ connection accounting record for an outbound LAT connection:
Wed Jun 27 03:53:06 2001 172.16.25.15 username1 tty3 5622329430/4327528 start task_id=18 service=connection protocol=lat addr=VAX cmd=lat VAX Wed Jun 27 03:54:15 2001 172.16.25.15 username1 tty3 5622329430/4327528 stop task_id=18 service=connection protocol=lat addr=VAX cmd=lat VAX bytes_in=0 bytes_out=0 paks_in=0 paks_out=0 elapsed_time=6
System Accounting
System accounting provides information about all system-level events (for example, when the system reboots or when accounting is turned on or off).
The following accounting record shows a typical TACACS+ system accounting record server indicating that AAA Accounting has been turned off:
Wed Jun 27 03:55:32 2001 172.16.25.15 unknown unknown unknown start task_id=25 service=system event=sys_acct reason=reconfigure
 Note | The precise format of accounting packets records may vary depending on the TACACS+ daemon. |
The following accounting record shows a TACACS+ system accounting record indicating that AAA Accounting has been turned on:
Wed Jun 27 03:55:22 2001 172.16.25.15 unknown unknown unknown stop task_id=23 service=system event=sys_acct reason=reconfigure
Additional tasks for measuring system resources are covered in the Cisco IOS software configuration guides. For example, IP accounting tasks are described in the Configuring IP Services chapter in the CiscoIOS Application Services Configuration Guide .
Resource Accounting
The Cisco implementation of AAA accounting provides âstartâ and âstopâ record support for calls that have passed user authentication. The additional feature of generating âstopâ records for calls that fail to authenticate as part of user authentication is also supported. Such records are necessary for users employing accounting records to manage and monitor their networks.
This section includes the following subsections:
AAA Resource Failure Stop Accounting
Before AAA resource failure stop accounting, there was no method of providing accounting records for calls that failed to reach the user authentication stage of a call setup sequence. Such records are necessary for users employing accounting records to manage and monitor their networks and their wholesale customers.
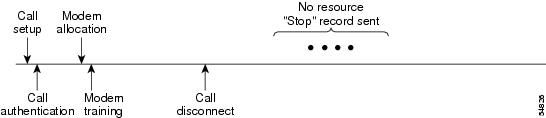
This functionality generates a âstopâ accounting record for any calls that do not reach user authentication; âstopâ records are generated from the moment of call setup. All calls that pass user authentication behave as they did before; that is, no additional accounting records are seen.
The figure below illustrates a call setup sequence with normal call flow (no disconnect) and without AAA resource failure stop accounting enabled.
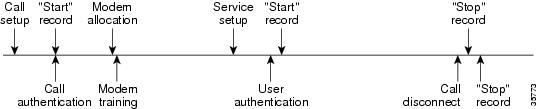
The figure below illustrates a call setup sequence with normal call flow (no disconnect) and with AAA resource failure stop accounting enabled.
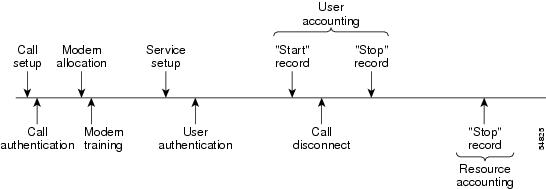
The figure below illustrates a call setup sequence with call disconnect occurring before user authentication and with AAA resource failure stop accounting enabled.

The figure below illustrates a call setup sequence with call disconnect occurring before user authentication and without AAA resource failure stop accounting enabled.
AAA Resource Accounting for Start-Stop Records
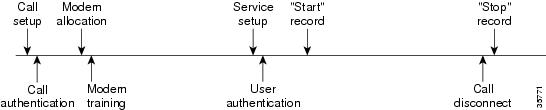
AAA resource accounting for start-stop records supports the ability to send a âstartâ record at each call setup, followed by a corresponding âstopâ record at the call disconnect. This functionality can be used to manage and monitor wholesale customers from one source of data reporting, such as accounting records.
With this feature, a call setup and call disconnect âstart-stopâ accounting record tracks the progress of the resource connection to the device. A separate user authentication âstart-stopâ accounting record tracks the user management progress. These two sets of accounting records are interlinked by using a unique session ID for the call.
The figure below illustrates a call setup sequence with AAA resource start-stop accounting enabled.
VRRS Accounting
Virtual Router Redundancy Service (VRRS) provides a multiclient information abstraction and management service between a First Hop Redundancy Protocol (FHRP) and a registered client. The VRRS multiclient service provides a consistent interface with FHRP protocols by abstracting over several FHRPs and providing an idealized view of their state. VRRS manages data updates, allowing interested clients to register in one place and receive updates for named FHRP groups or all registered FHRP groups.
Virtual Router Redundancy Protocol (VRRP) is an FHRP that acts as a server that pushes FHRP status information out to all registered VRRS clients. Clients obtain status on essential information provided by the FHRP, including current and previous redundancy states, active and inactive L3 and L2 addresses, and, in some cases, information about other redundant gateways in the network. Clients can use this information to provide stateless and stateful redundancy information to clients and protocols.
VRRS Accounting Plug-in
The VRRS Accounting plug-in provides a configurable AAA method list mechanism that provides updates to a RADIUS server when a VRRS group transitions its state. The VRRS accounting plug-in is an extension of existing AAA system accounting messages. The VRRS Accounting plug-in provides accounting-on and accounting-off messages and an additional Vendor-Specific Attribute (VSA) that sends the configured VRRS name in RADIUS accounting messages. The VRRS name is configured using the vrrp name command in interface configuration mode.
The VRRS Accounting plug-in provides a configurable AAA method list mechanism that provides updates to a RADIUS server when a VRRS group transitions its state.
The VRRS accounting plug-in is an extension of existing AAA system accounting messages. The VRRS Accounting plug-in provides accounting-on and accounting-off messages and an additional Vendor-Specific Attribute (VSA) that sends the configured VRRS name in RADIUS accounting messages. The VRRS name is configured using the vrrp name command in interface configuration mode. The VRRS Accounting plug-in sends an accounting-on message to RADIUS when a VRRS group transitions to the master state, and it sends an accounting-off message when a VRRS group transitions from the master state.
The following RADIUS attributes are included in VRRS accounting messages by default:
- Attribute 4, NAS-IP-Address
- Attribute 26, Cisco VSA Type 1, VRRS Name
- Attribute 40, Acct-Status-Type
- Attribute 41, Acct-Delay-Time
- Attribute 44, Acct-Session-Id
Accounting messages for a VRRS transitioning out of master state are sent after all PPPoE accounting stop messages for sessions that are part of that VRRS.
AAA Accounting Enhancements
AAA Broadcast Accounting
AAA broadcast accounting allows accounting information to be sent to multiple AAA servers at the same time; that is, accounting information can be broadcast to one or more AAA servers simultaneously. This functionality allows service providers to send accounting information to their own private AAA servers and to the AAA servers of their end customers. It also provides redundant billing information for voice applications.
Broadcasting is allowed among groups of RADIUS or TACACS+ servers, and each server group can define its backup servers for failover independently of other groups.
Thus, service providers and their end customers can use different protocols (RADIUS or TACACS+) for the accounting server. Service providers and their end customers can also specify their backup servers independently. As for voice applications, redundant accounting information can be managed independently through a separate group with its own failover sequence.
AAA Session MIB
The AAA session MIB feature allows customers to monitor and terminate their authenticated client connections using Simple Network Management Protocol (SNMP). The data of the client is presented so that it correlates directly to the AAA Accounting information reported by either the RADIUS or the TACACS+ server. AAA session MIB provides the following information:
- Statistics for each AAA function (when used in conjunction with the show radius statistics command)
- Status of servers providing AAA functions
- Identities of external AAA servers
- Real-time information (such as idle times), providing additional criteria for use by SNMP networks for assessing whether or not to terminate an active call
 Note | This command is supported only on Cisco AS5300 and Cisco AS5800 universal access server platforms. |
The table below shows the SNMP user-end data objects that can be used to monitor and terminate authenticated client connections with the AAA session MIB feature.
|
SessionId |
The session identification used by the AAA Accounting protocol (same value as reported by RADIUS attribute 44 (Acct-Session-ID)). |
|
UserId |
The user login ID or zero-length string if a login is unavailable. |
|
IpAddr |
The IP address of the session or 0.0.0.0 if an IP address is not applicable or unavailable. |
|
IdleTime |
The elapsed time in seconds that the session has been idle. |
|
Disconnect |
The session termination object used to disconnect the given client. |
|
CallId |
The entry index corresponding to this accounting session that the Call Tracker record stored. |
The table below describes the AAA summary information provided by the AAA session MIB feature using SNMP on a per-system basis.
|
ActiveTableEntries |
Number of sessions currently active. |
|
ActiveTableHighWaterMark |
Maximum number of sessions present at once since last system reinstallation. |
|
TotalSessions |
Total number of sessions since last system reinstallation. |
|
DisconnectedSessions |
Total number of sessions that have been disconnected using since last system reinstallation. |
How to Configure AAA Accounting
- Configuring AAA Accounting Using Named Method Lists
- Suppressing Generation of Accounting Records for Null Username Sessions
- Generating Interim Accounting Records
- Generating Accounting Records for Failed Login or Session
- Specifying Accounting NETWORK-Stop Records Before EXEC-Stop Records
- Configuring AAA Resource Failure Stop Accounting
- Configuring AAA Resource Accounting for Start-Stop Records
- Configuring AAA Broadcast Accounting
- Configuring Per-DNIS AAA Broadcast Accounting
- Configuring AAA Session MIB
- Configuring VRRS Accounting
- Establishing a Session with a Router if the AAA Server is Unreachable
- Monitoring Accounting
- Troubleshooting Accounting
Configuring AAA Accounting Using Named Method Lists
To configure AAA Accounting using named method lists, perform the following steps:
 Note | System accounting does not use named method lists. For system accounting, define only the default method list. |
- Router(config)# line [aux | console | tty | vty] line-number [ending-line-number]
- Router(config)# interface interface-type interface-number
- Router(config-line)# accounting {arap | commands level | connection | exec} {default | list-name}
- Router(config-if)# ppp accounting{default | list-name}
DETAILED STEPS
This section includes the following subsection:
Configuring RADIUS System Accounting
DETAILED STEPS
Suppressing Generation of Accounting Records for Null Username Sessions
When AAA Accounting is activated, the Cisco IOS software issues accounting records for all users on the system, including users whose username string, because of protocol translation, is NULL. An example of this is users who come in on lines where the aaa authentication login method-list none command is applied. To prevent accounting records from being generated for sessions that do not have usernames associated with them, use the following command in global configuration mode:
Generating Interim Accounting Records
To enable periodic interim accounting records to be sent to the accounting server, use the following command in global configuration mode:
|
Command |
Purpose |
|---|---|
Router(config)# aaa accounting update [newinfo] [periodic] number |
Enables periodic interim accounting records to be sent to the accounting server. |
When the aaa accounting updatecommandis activated, the Cisco IOS software issues interim accounting records for all users on the system. If the keyword newinfo is used, interim accounting records are sent to the accounting server every time there is new accounting information to report. An example of this would be when IPCP completes IP address negotiation with the remote peer. The interim accounting record includes the negotiated IP address used by the remote peer.
When used with the keyword periodic, interim accounting records are sent periodically as defined by the number argument. The interim accounting record contains all of the accounting information recorded for that user up to the time the interim accounting record is sent.
 Caution | Using the aaa accounting update periodic command can cause heavy congestion when many users are logged in to the network. |
Generating Accounting Records for Failed Login or Session
When AAA Accounting is activated, the Cisco IOS software does not generate accounting records for system users who fail login authentication, or who succeed in login authentication but fail PPP negotiation for some reason.
To specify that accounting stop records be generated for users who fail to authenticate at login or during session negotiation, use the following command in global configuration mode:
|
Command |
Purpose |
|---|---|
Router(config)# aaa accounting send stop-record authentication failure
|
Generates âstopâ records for users who fail to authenticate at login or during session negotiation using PPP. |
Router(config)#
aaa accounting send stop-record always
|
Sends authentication, authorization, and accounting (AAA) stop records regardless of whether a start record was sent earlier. |
Specifying Accounting NETWORK-Stop Records Before EXEC-Stop Records
For PPP users who start EXEC terminal sessions, you can specify the NETWORK records to be generated before EXEC-stop records. In cases such as billing customers for specific services, it can be desirable to keep network start and stop records together, essentially ânestingâ them within the framework of the EXEC start and stop messages. For example, a user dialing in using PPP can create the following records: EXEC-start, NETWORK-start, EXEC-stop, NETWORK-stop. By nesting the accounting records, NETWORK-stop records follow NETWORK-start messages: EXEC-start, NETWORK-start, NETWORK-stop, EXEC-stop.
To nest accounting records for user sessions, use the following command in global configuration mode:
Configuring AAA Resource Failure Stop Accounting
To enable resource failure stop accounting, use the following command in global configuration mode:
|
Command |
Purpose |
||
|---|---|---|---|
Router(config)# aaa accounting resource method-list stop-failure group server-group |
Generates a âstopâ record for any calls that do not reach user authentication.
|
Configuring AAA Resource Accounting for Start-Stop Records
To enable full resource accounting for start-stop records, use the following command in global configuration mode:
|
Command |
Purpose |
||||
|---|---|---|---|---|---|
Router(config)# aaa accounting resource method-list start-stop group server-group |
Supports the ability to send a âstartâ record at each call setup. followed with a corresponding âstopâ record at the call disconnect.
|
Configuring AAA Broadcast Accounting
To configure AAA broadcast accounting, use the aaa accounting command in global configuration mode:
|
Command |
Purpose |
|---|---|
Router(config)# aaa accounting {system | network | exec | connection | commands level} {default | list-name} {start-stop | stop-only | none} [broadcast] method1 [method2...] |
Enables sending accounting records to multiple AAA servers. Simultaneously sends accounting records to the first server in each group. If the first server is unavailable, failover occurs using the backup servers defined within that group. |
Configuring Per-DNIS AAA Broadcast Accounting
To configure AAA broadcast accounting per DNIS, use the aaa dnis map accounting networkcommand in global configuration mode:
|
Command |
Purpose |
|---|---|
Router(config)# aaa dnis map dnis-number accounting network [start-stop | stop-only | none] [broadcast] method1 [method2...] |
Allows per-DNIS accounting configuration. This command has precedence over the global aaa accounting command. Enables sending accounting records to multiple AAA servers. Simultaneously sends accounting records to the first server in each group. If the first server is unavailable, failover occurs using the backup servers defined within that group. |
Configuring AAA Session MIB
The following tasks must be performed before configuring the AAA session MIB feature:
- Configure SNMP. For information on SNMP, see the chapter Configuring SNMP Support in the Cisco IOS Network Management Configuration Guide.
- Configure AAA.
- Define the RADIUS or TACACS+ server characteristics.
 Note | Overusing SNMP can affect the overall system performance; therefore, normal network management performance must be considered when this feature is used. |
To configure AAA session MIB, use the following command in global configuration mode
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | Router(config)# aaa session-mib disconnect |
Monitors and terminates authenticated client connections using SNMP. To terminate the call, the disconnect keyword must be used. |
Configuring VRRS Accounting
Perform the following task to configure Virtual Router Redundancy Service (VRRS) to send AAA Accounting messages to the AAA server:
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example: Router> enable |
Enables privileged EXEC mode.
|
| Step 2 |
configure
terminal
Example: Router# configure terminal |
Enters global configuration mode. |
| Step 3 |
aaa
accounting
vrrs
{default | list-name} start-stop method1 [method2...] Example: Router(config)# aaa accounting vrrs default start-stop |
Enables AAA accounting for VRRS. |
| Step 4 |
aaa
attribute
list
list-name
Example: Router(config)# aaa attribute list list1 |
Defines a AAA attribute list locally on a router, and enters attribute list configuration mode. |
| Step 5 |
attribute
type
name
value
[service service] [protocol protocol][mandatory][tag tag-value] Example: Router(config-attr-list)# attribute type example 1 |
Defines an attribute type that is to be added to an attribute list locally on a router. |
| Step 6 |
exit
Example: Router(config-attr-list)# exit |
Exits attribute list configuration mode and returns to global configuration mode. |
| Step 7 |
vrrs
vrrs-group-name
Example: Router(config)# vrrs vrrs1 |
(Optional) Defines a VRRP group and configures parameters for the VRRS group, and enters VRRS configuration mode. |
| Step 8 |
accounting
delay
seconds
Example: Router(config-vrrs)# accounting delay 10 |
(Optional) Specifies the delay time for sending accounting-off messages to the VRRS. |
| Step 9 |
accounting
method
{default | accounting-method-list} Example: Router(config-vrrs)# accounting method default |
(Optional) Enables VRRS accounting for a VRRP group. |
| Step 10 |
exit
Example: Router(config-vrrs)# exit |
Exits VRRS configuration mode. |
Establishing a Session with a Router if the AAA Server is Unreachable
To establish a console or telnet session with a router if the AAA server is unreachable, use the following command in global configuration mode:
|
Command |
Purpose |
|---|---|
Router(config)# no aaa accounting system guarantee-first
|
The aaa accounting system guarantee-first command guarantees system accounting as the first record, which is the default condition. In some situations, users may be prevented from starting a session on the console or terminal connection until after the system reloads, which can take more than three minutes. To resolve this problem, the no aaa accounting system guarantee-first command can be used. |
 Note | Entering the no aaa accounting system guarantee-first command is not the only condition by which the console or telnet session can be started. For example, if the privileged EXEC session is being authenticated by TACACS and the TACACS server is not reachable, then the session cannot start. |
Configuration Examples for AAA Accounting
- Example Configuring Named Method List
- Example Configuring AAA Resource Accounting
- Example Configuring AAA Broadcast Accounting
- Example Configuring Per-DNIS AAA Broadcast Accounting
- Example AAA Session MIB
- Example Configuring VRRS Accounting
Example Configuring Named Method List
The following example shows how to configure a Cisco AS5200 (enabled for AAA and communication with a RADIUS security server) in order for AAA services to be provided by the RADIUS server. If the RADIUS server fails to respond, then the local database is queried for authentication and authorization information, and accounting services are handled by a TACACS+ server.
aaa new-model aaa authentication login admins local aaa authentication ppp dialins group radius local aaa authorization network blue1 group radius local aaa accounting network red1 start-stop group radius group tacacs+ username root password ALongPassword tacacs-server host 172.31.255.0 tacacs-server key goaway radius-server host 172.16.2.7 radius-server key myRaDiUSpassWoRd interface group-async 1 group-range 1 16 encapsulation ppp ppp authentication chap dialins ppp authorization blue1 ppp accounting red1 line 1 16 autoselect ppp autoselect during-login login authentication admins modem dialin
The lines in this sample RADIUS AAA configuration are defined as follows:
- The aaa new-model command enables AAA network security services.
- The aaa authentication login admins local command defines a method list âadminsâ, for login authentication.
- The aaa authentication ppp dialins group radius local command defines the authentication method list âdialinsâ, which specifies that first RADIUS authentication and then (if the RADIUS server does not respond) local authentication is used on serial lines using PPP.
- The aaa authorization network blue1 group radius local command defines the network authorization method list named âblue1â, which specifies that RADIUS authorization is used on serial lines using PPP. If the RADIUS server fails to respond, then local network authorization is performed.
- The aaa accounting network red1 start-stop group radius group tacacs+command defines the network accounting method list named red1, which specifies that RADIUS accounting services (in this case, start and stop records for specific events) are used on serial lines using PPP. If the RADIUS server fails to respond, accounting services are handled by a TACACS+ server.
- The username command defines the username and password to be used for the PPP Password Authentication Protocol (PAP) caller identification.
- The tacacs-server host command defines the name of the TACACS+ server host.
- The tacacs-server key command defines the shared secret text string between the network access server and the TACACS+ server host.
- The radius-server host command defines the name of the RADIUS server host.
- The radius-server key command defines the shared secret text string between the network access server and the RADIUS server host.
- The interface group-async command selects and defines an asynchronous interface group.
- The group-range command defines the member asynchronous interfaces in the interface group.
- The encapsulation ppp command sets PPP as the encapsulation method used on the specified interfaces.
- The ppp authentication chap dialinscommand selects Challenge Handshake Authentication Protocol (CHAP) as the method of PPP authentication and applies the âdialinsâ method list to the specified interfaces.
- The ppp authorization blue1command applies the blue1 network authorization method list to the specified interfaces.
- The ppp accounting red1command applies the red1 network accounting method list to the specified interfaces.
- The line command switches the configuration mode from global configuration to line configuration and identifies the specific lines being configured.
- The autoselect ppp command configures the Cisco IOS software to allow a PPP session to start up automatically on these selected lines.
- The autoselect during-login command is used to display the username and password prompt without pressing the Return key. After the user logs in, the autoselect function (in this case, PPP) begins.
- The login authentication admins command applies the admins method list for login authentication.
- The modem dialin command configures modems attached to the selected lines to only accept incoming calls.
The show accountingcommand yields the following output for the preceding configuration:
Active Accounted actions on tty1, User username2 Priv 1 Task ID 5, Network Accounting record, 00:00:52 Elapsed task_id=5 service=ppp protocol=ip address=10.0.0.98
The table below describes the fields contained in the preceding output.
|
Field |
Description |
|---|---|
|
Active Accounted actions on |
Terminal line or interface name user with which the user logged in. |
|
User |
Userâs ID. |
|
Priv |
Userâs privilege level. |
|
Task ID |
Unique identifier for each accounting session. |
|
Accounting record |
Type of accounting session. |
|
Elapsed |
Length of time (hh:mm:ss) for this session type. |
|
attribute=value |
AV pairs associated with this accounting session. |
Example Configuring AAA Resource Accounting
The following example shows how to configure the resource failure stop accounting and resource accounting for start-stop records functions:
!Enable AAA on your network access server. aaa new-model !Enable authentication at login and list the AOL string name to use for login authentication. aaa authentication login AOL group radius local !Enable authentication for ppp and list the default method to use for PPP authentication. aaa authentication ppp default group radius local !Enable authorization for all exec sessions and list the AOL string name to use for authorization. aaa authorization exec AOL group radius if-authenticated !Enable authorization for all network-related service requests and list the default method to use for all network-related authorizations. aaa authorization network default group radius if-authenticated !Enable accounting for all exec sessions and list the default method to use for all start-stop accounting services. aaa accounting exec default start-stop group radius !Enable accounting for all network-related service requests and list the default method to use for all start-stop accounting services. aaa accounting network default start-stop group radius !Enable failure stop accounting. aaa accounting resource default stop-failure group radius !Enable resource accounting for start-stop records. aaa accounting resource default start-stop group radius
Example Configuring AAA Broadcast Accounting
The following example shows how to turn on broadcast accounting using the global aaa accounting command:
aaa group server radius isp server 10.0.0.1 server 10.0.0.2 aaa group server tacacs+ isp_customer server 172.0.0.1 aaa accounting network default start-stop broadcast group isp group isp_customer radius-server host 10.0.0.1 radius-server host 10.0.0.2 radius-server key key1 tacacs-server host 172.0.0.1 key key2
The broadcast keyword causes âstartâ and âstopâ accounting records for network connections to be sent simultaneously to server 10.0.0.1 in the group isp and to server 172.0.0.1 in the group isp_customer. If server 10.0.0.1 is unavailable, failover to server 10.0.0.2 occurs. If server 172.0.0.1 is unavailable, no failover occurs because backup servers are not configured for the group isp_customer.
Example Configuring Per-DNIS AAA Broadcast Accounting
The following example shows how to turn on per DNIS broadcast accounting using the global aaa dnis map accounting networkcommand:
aaa group server radius isp server 10.0.0.1 server 10.0.0.2 aaa group server tacacs+ isp_customer server 172.0.0.1 aaa dnis map enable aaa dnis map 7777 accounting network start-stop broadcast group isp group isp_customer radius-server host 10.0.0.1 radius-server host 10.0.0.2 radius-server key key_1 tacacs-server host 172.0.0.1 key key_2
The broadcast keyword causes âstartâ and âstopâ accounting records for network connection calls having DNIS number 7777 to be sent simultaneously to server 10.0.0.1 in the group isp and to server 172.0.0.1 in the group isp_customer. If server 10.0.0.1 is unavailable, failover to server 10.0.0.2 occurs. If server 172.0.0.1 is unavailable, no failover occurs because backup servers are not configured for the group isp_customer.
Example AAA Session MIB
The following example shows how to set up the AAA session MIB feature to disconnect authenticated client connections for PPP users:
aaa new-model aaa authentication ppp default group radius aaa authorization network default group radius aaa accounting network default start-stop group radius aaa session-mib disconnect
Example Configuring VRRS Accounting
The following example shows how to configure VRRS to send AAA Accounting messages to the AAA server:
Router# configure terminal Router(config)# aaa accounting vrrs vrrp-mlist-1 start-stop group radius Router(config)# aaa attribute list vrrp-1-attr Router(config-attr-list)# attribute type account-delay 10 Router(config-attr-list)# exit Router(config)# vrrs vrrp-group-1 Router(config-vrrs)# accounting delay 10 Router(config-vrrs)# accounting method vrrp-mlist-1 Router(config-vrrs)# exit
Additional References
MIBs
Technical Assistance
|
Description |
Link |
|---|---|
|
The Cisco Support and Documentation website provides online resources to download documentation, software, and tools. Use these resources to install and configure the software and to troubleshoot and resolve technical issues with Cisco products and technologies. Access to most tools on the Cisco Support and Documentation website requires a Cisco.com user ID and password. |
Feature Information for Configuring Accounting
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
|
Feature Name |
Releases |
Feature Information |
|---|---|---|
|
AAA Broadcast Accounting |
12.2 12.2S 12.2SB 12.2SX 12.4T |
AAA broadcast accounting allows accounting information to be sent to multiple AAA servers at the same time; that is, accounting information can be broadcast to one or more AAA servers simultaneously. |
|
AAA Resource Accounting for Start-Stop Records |
12.2 12.4T 12.2S 12.2SB 12.2SX |
AAA resource accounting for start-stop records supports the ability to send a âstartâ record at each call setup, followed by a corresponding âstopâ record at the call disconnect. This functionality can be used to manage and monitor wholesale customers from one source of data reporting, such as accounting records. |
|
AAA Session MIB |
12.2 12.4T 12.2S 12.2SB 12.2SX |
The AAA session MIB feature allows customers to monitor and terminate their authenticated client connections using SNMP. The data of the client is presented so that it correlates directly to the AAA Accounting information reported by either the RADIUS or the TACACS+ server. |
|
AAA: IPv6 Accounting Delay Enhancements |
15.1(1)S |
VRRS provides a multiclient information abstraction and management service between a First Hop Redundancy Protocol (FHRP) and a registered client. |
Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco's trademarks can be found at www.cisco.com/go/trademarks. Third party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1005R)
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.

 Feedback
Feedback