Cisco Intrusion Detection System Network Modules
Available Languages
Table Of Contents
Connecting Cisco Intrusion Detection System Network Modules to the Network
Connecting Cisco IDS Network Modules to the Network
Online Insertion and Removal with a Cisco IDS Network Module
Obtaining Documentation, Obtaining Support, and Security Guidelines
Connecting Cisco Intrusion Detection System Network Modules to the Network
Revised: May 1, 2008, OL-12826-01
This guide describes how to connect Cisco Intrusion Detection System (IDS) network modules to your network. It contains the following sections:
•
Cisco IDS Network Module LEDs
•
Online Insertion and Removal with a Cisco IDS Network Module
•
Obtaining Documentation, Obtaining Support, and Security Guidelines
Cisco IDS Network Modules
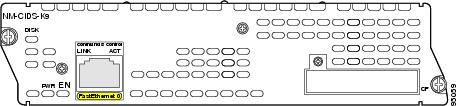
This section provides information on the Cisco IDS network module (NM-CIDS-K9) (see Figure 1)

CautionTo comply with the Telcordia GR-1089 NEBS standard for electromagnetic compatibility and safety, connect the Cisco IDS network module (NM-CIDS-K9) only to intrabuilding or nonexposed wiring or cabling. The intrabuilding cable must be shielded and the shield must be grounded at both ends.
Figure 1 Faceplate for the NM-CIDS-K9 Network Module
Connecting Cisco IDS Network Modules to the Network
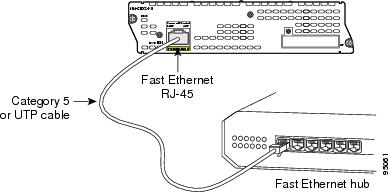
To connect a Cisco IDS network module to the network, use a straight-through two-pair Category 5 unshielded twisted-pair (UTP) cable to connect the RJ-45 port on the Cisco IDS network module to a switch, hub, repeater, server, or other network device. (See Figure 2.)

Note
RJ-45 cables are not available from Cisco Systems. These cables are widely available and must be Category 5 cables.

CautionTo comply with the Telcordia GR-1089 NEBS standard for electromagnetic compatibility and safety, connect the Cisco IDS network module (NM-CIDS-K9) only to intrabuilding or nonexposed wiring or cabling. The intrabuilding cable must be shielded and the shield must be grounded at both ends.
Figure 2 Connecting a Cisco IDS Network Module to a Fast Ethernet Hub
Cisco IDS Network Module LEDs
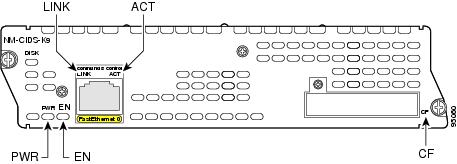
All network modules have an enable (EN) LED. This LED indicates that the module has passed its self-tests and is available to the router.
All Cisco IDS network modules display an additional power (PWR) LED and a CompactFlash (CF) LED on the faceplate, and two additional LEDs for the Fast Ethernet port (see Figure 3).
Figure 3 Cisco IDS Network Module LEDs
Online Insertion and Removal with a Cisco IDS Network Module
Some Cisco modular access routers allow you to replace network modules without switching off the router or affecting the operation of other interfaces. This feature is called online insertion and removal (OIR). OIR of network modules provides uninterrupted operation to network users, maintains routing information, and ensures session preservation.

CautionUnlike other network modules, Cisco IDS network modules use hard disks. Online removal of disks without proper shutdown can result in file system corruption and might render the disk unusable. The operating system on the Cisco IDS network module must be shut down in an orderly fashion before the network module is removed.

CautionCisco routers support OIR with similar modules only. If you remove a network module, install another module exactly like it in its place. If you remove a two-slot network module (along with any installed WAN or voice interface cards), install another module and card combination exactly like it.
For a description of informational and error messages that may appear on the console during this procedure, see the hardware installation guide for your type of router.
To perform online removal of a Cisco IDS network module and insertion of a replacement, follow these steps with the router in privileged EXEC mode:
Step 1
Perform a graceful halt of the Cisco IDS network module by using the following command:
Router# service-module IDS-Sensor slot/0 shutdownTrying 10.10.10.1, 2129 ... OpenWait for the following status message (it may take a minute or two):
%SERVICEMODULE-5-SHUTDOWN2:Service module IDS-Sensor1/0 shutdown completeStep 2
Unplug the network interface cable from the Cisco IDS network module.
Step 3
Loosen the two captive screws holding the Cisco IDS network module in the chassis slot.
Step 4
Slide the Cisco IDS network module out of the slot.
Step 5
Align the replacement Cisco IDS network module with the guides in the chassis slot, and slide it gently into the slot.

Note
If the router is not fully configured with network modules, make sure that blank panels fill the unoccupied chassis slots to provide proper airflow.
Step 6
Push the module into place until you feel its edge connector mate securely with the connector on the backplane.
Step 7
Reconnect the network interface cable previously removed in Step 2.
Step 8
Tighten the two captive screws on the faceplate.
Step 9
Reset the Cisco IDS network module using the reset command.
Router#service-module IDS-Sensor slot/0 resetUse reset only to recover from shutdown or failed stateWarning: May lose date on the hard disc!Do you want to reset?[confirm]Step 10
Press Enter to confirm the request. The Cisco IDS network module resets itself.
Step 11
Check that the network module LEDs are on and that the power and enable LEDs on the front panel also are on. This inspection ensures that connections are secure and that the new unit is operational.
Related Documents
For additional information, see the following documents and resources.
Cisco IDS software documentation
Cisco Intrusion Detection System (IDS) Hardware and Software Documentation Guide
http://www.cisco.com/univercd/cc/td/doc/product/iaabu/csids/csids10/15593_01.htmRegulatory compliance and safety information
Cisco Network Modules and Interface Cards Regulatory Compliance and Safety Information
http://www.cisco.com/en/US/docs/routers/access/interfaces/rcsi/IOHrcsi.htmlCisco IOS software website and reference documentation
Cisco IOS Software http://www.cisco.com/web/psa/products/index.html?c=268438303
Obtaining Documentation, Obtaining Support, and Security Guidelines
For information on obtaining documentation, obtaining support, providing documentation feedback, security guidelines, and also recommended aliases and general Cisco documents, see the monthly What's New in Cisco Product Documentation, which also lists all new and revised Cisco technical documentation, at:
http://www.cisco.com/en/US/docs/general/whatsnew/whatsnew.html
CCDE, CCENT, Cisco Eos, Cisco Lumin, Cisco StadiumVision, the Cisco logo, DCE, and Welcome to the Human Network are trademarks; Changing the Way We Work, Live, Play, and Learn is a service mark; and Access Registrar, Aironet, AsyncOS, Bringing the Meeting To You, Catalyst, CCDA, CCDP, CCIE, CCIP, CCNA, CCNP, CCSP, CCVP, Cisco, the Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unity, Collaboration Without Limitation, EtherFast, EtherSwitch, Event Center, Fast Step, Follow Me Browsing, FormShare, GigaDrive, HomeLink, Internet Quotient, IOS, iPhone, iQ Expertise, the iQ logo, iQ Net Readiness Scorecard, iQuick Study, IronPort, the IronPort logo, LightStream, Linksys, MediaTone, MeetingPlace, MGX, Networkers, Networking Academy, Network Registrar, PCNow, PIX, PowerPanels, ProConnect, ScriptShare, SenderBase, SMARTnet, Spectrum Expert, StackWise, The Fastest Way to Increase Your Internet Quotient, TransPath, WebEx, and the WebEx logo are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the United States and certain other countries.
All other trademarks mentioned in this document or Website are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (0804R)
Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and coincidental.
© 2008 Cisco Systems, Inc. All rights reserved.
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback