- About This Guide
- Index
- Glossary
-
- Configuring IPSec and ISAKMP
- Configuring L2TP over IPSec
- Setting General VPN Parameters
- Configuring Tunnel Groups, Group Policies, and Users
- Configuring IP Addresses for VPN
- Configuring Remote Access VPNs
- Configuring Network Admission Control
- Configuring Easy VPN on the ASA 5505
- Configuring the PPPoE Client
- Configuring LAN-to-LAN VPNs
- Configuring Clientless SSL VPN
- Configuring AnyConnect VPN Client Connections
- Configuring AnyConnect Host Scan
- Understanding Policy Enforcement of Permissions and Attributes
- Configuring an External LDAP Server
Configuring an External Server for Authorization and Authentication
This appendix describes how to configure an external LDAP, RADIUS, or TACACS+ server to support AAA on the ASA. Before you configure the ASA to use an external server, you must configure the server with the correct ASA authorization attributes and, from a subset of these attributes, assign specific permissions to individual users.
Understanding Policy Enforcement of Permissions and Attributes
The ASA supports several methods of applying user authorization attributes (also called user entitlements or permissions) to VPN connections. You can configure the ASA to obtain user attributes from a Dynamic Access Policy (DAP) on the ASA, from an external authentication and/or authorization AAA server (RADIUS or LDAP), from a group policy on the ASA, or from all three.
If the ASA receives attributes from all sources, the attributes are evaluated, merged, and applied to the user policy. If there are conflicts between attributes coming from the DAP, the AAA server, or the group policy, those attributes obtained from the DAP always take precedence.
The ASA applies attributes in the following order (see Figure C-1).
1.![]() DAP attributes on the ASA—Introduced in Version 8.0(2), these attributes take precedence over all others. If you set a bookmark or URL list in DAP, it overrides a bookmark or URL list set in the group policy.
DAP attributes on the ASA—Introduced in Version 8.0(2), these attributes take precedence over all others. If you set a bookmark or URL list in DAP, it overrides a bookmark or URL list set in the group policy.
2.![]() User attributes on the AAA server—The server returns these attributes after successful user authentication and/or authorization. Do not confuse these with attributes that are set for individual users in the local AAA database on the ASA (User Accounts in ASDM).
User attributes on the AAA server—The server returns these attributes after successful user authentication and/or authorization. Do not confuse these with attributes that are set for individual users in the local AAA database on the ASA (User Accounts in ASDM).
3.![]() Group policy configured on the ASA—If a RADIUS server returns the value of the RADIUS CLASS attribute IETF-Class-25 (OU= group-policy) for the user, the ASA places the user in the group policy of the same name and enforces any attributes in the group policy that are not returned by the server.
Group policy configured on the ASA—If a RADIUS server returns the value of the RADIUS CLASS attribute IETF-Class-25 (OU= group-policy) for the user, the ASA places the user in the group policy of the same name and enforces any attributes in the group policy that are not returned by the server.
For LDAP servers, any attribute name can be used to set the group policy for the session. The LDAP attribute map that you configure on the ASA maps the LDAP attribute to the Cisco attribute IETF-Radius-Class.
4.![]() Group policy assigned by the Connection Profile (called tunnel-group in the CLI)—The Connection Profile has the preliminary settings for the connection, and includes a default group policy applied to the user before authentication. All users connecting to the ASA initially belong to this group, which provides any attributes that are missing from the DAP, user attributes returned by the server, or the group policy assigned to the user.
Group policy assigned by the Connection Profile (called tunnel-group in the CLI)—The Connection Profile has the preliminary settings for the connection, and includes a default group policy applied to the user before authentication. All users connecting to the ASA initially belong to this group, which provides any attributes that are missing from the DAP, user attributes returned by the server, or the group policy assigned to the user.
5.![]() Default group policy assigned by the ASA (DfltGrpPolicy)—System default attributes provide any values that are missing from the DAP, user attributes, group policy, or connection profile.
Default group policy assigned by the ASA (DfltGrpPolicy)—System default attributes provide any values that are missing from the DAP, user attributes, group policy, or connection profile.
Figure C-1 Policy Enforcement Flow

Configuring an External LDAP Server
The VPN 3000 concentrator and the ASA/PIX 7.0 software required a Cisco LDAP schema for authorization operations. Beginning with Version 7.1.x, the ASA performs authentication and authorization using the native LDAP schema, and the Cisco schema is no longer needed.
You configure authorization (permission policy) using an LDAP attribute map. For examples, see the “Active Directory/LDAP VPN Remote Access Authorization Examples” section.
This section describes the structure, schema, and attributes of an LDAP server and includes the following topics:
- Organizing the ASA for LDAP Operations
- Defining the ASA LDAP Configuration
- Active Directory/LDAP VPN Remote Access Authorization Examples
The specific steps of these processes vary, depending on which type of LDAP server that you are using.

Note![]() For more information about the LDAP protocol, see RFCs 1777, 2251, and 2849.
For more information about the LDAP protocol, see RFCs 1777, 2251, and 2849.
Organizing the ASA for LDAP Operations
This section describes how to search within the LDAP hierarchy and perform authenticated binding to the LDAP server on the ASA and includes the following topics:
Your LDAP configuration should reflect the logical hierarchy of your organization. For example, suppose an employee at your company, Example Corporation, is named Employee1. Employee1 works in the Engineering group. Your LDAP hierarchy could have one or many levels. You might decide to set up a single-level hierarchy in which Employee1 is considered a member of Example Corporation. Or you could set up a multi-level hierarchy in which Employee1 is considered to be a member of the department Engineering, which is a member of an organizational unit called People, which is itself a member of Example Corporation. See Figure C-2 for an example of a multi-level hierarchy.
A multi-level hierarchy has more detail, but searches return results more quickly in a single-level hierarchy.
Figure C-2 A Multi-Level LDAP Hierarchy
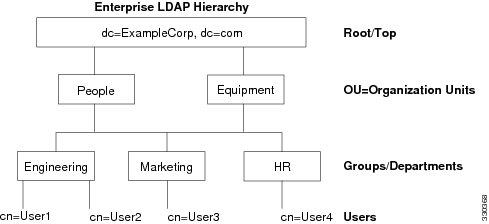
Searching the LDAP Hierarchy
The ASA lets you tailor the search within the LDAP hierarchy. You configure the following three fields on the ASA to define where in the LDAP hierarchy that your search begins, the extent, and the type of information it is looking for. Together these fields allow you to limit the search of the hierarchy to only the part that includes the user permissions.
- LDAP Base DN defines where in the LDAP hierarchy that the server should begin searching for user information when it receives an authorization request from the ASA.
- Search Scope defines the extent of the search in the LDAP hierarchy. The search proceeds this many levels in the hierarchy below the LDAP Base DN. You can choose to have the server search only the level immediately below it, or it can search the entire subtree. A single level search is quicker, but a subtree search is more extensive.
- Naming Attribute(s) defines the RDN that uniquely identifies an entry in the LDAP server. Common naming attributes can include cn (Common Name), sAMAccountName, and userPrincipalName.
Figure C-2 shows a sample LDAP hierarchy for Example Corporation. Given this hierarchy, you could define your search in different ways. Table C-1 shows two sample search configurations.
In the first example configuration, when Employee1 establishes the IPsec tunnel with LDAP authorization required, the ASA sends a search request to the LDAP server, indicating it should search for Employee1 in the Engineering group. This search is quick.
In the second example configuration, the ASA sends a search request indicating that the server should search for Employee1 within Example Corporation. This search takes longer.
|
|
|
|
|
|
|---|---|---|---|---|
Binding the ASA to the LDAP Server
Some LDAP servers (including the Microsoft Active Directory server) require the ASA to establish a handshake via authenticated binding before they accept requests for any other LDAP operations. The ASA uses the Login Distinguished Name (DN) and Login Password to establish a trust relationship (bind) with an LDAP server before a user can search. The Login DN represents a user record in the LDAP server that the administrator uses for binding.
When binding, the ASA authenticates to the server using the Login DN and the Login Password. When performing a Microsoft Active Directory read-only operation (such as for authentication, authorization, or group search), the ASA can bind with a Login DN with fewer privileges. For example, the Login DN can be a user whose AD “Member Of” designation is part of Domain Users. For VPN password management write operations, the Login DN needs elevated privileges and must be part of the Account Operators AD group. Microsoft Active Directory group search (also called “MemberOf retrieval”) was added in ASA Version 8.0.4.
An example of a Login DN includes the following entries:
cn=Binduser1,ou=Admins,ou=Users,dc=company_A,dc=com
See your LDAP Administrator guide for specific Login DN requirements for read and write operations.
The ASA supports the following features:
- Simple LDAP authentication with an unencrypted password using the default port 389. You can also use other ports instead of the default port.
- Secure LDAP (LDAP-S) using the default port 636. You can also use other ports instead of the default port.
- Simple Authentication and Security Layer (SASL) MD5
- SASL Kerberos
The ASA does not support anonymous authentication.

Note![]() As an LDAP client, the ASA does not support the transmission of anonymous binds or requests.
As an LDAP client, the ASA does not support the transmission of anonymous binds or requests.
Defining the ASA LDAP Configuration
This section describes how to define the LDAP AV-pair attribute syntax and includes the following topics:
- Supported Cisco Attributes for LDAP Authorization
- Cisco AV Pair Attribute Syntax
- Cisco AV Pairs ACL Examples

Note![]() The ASA enforces the LDAP attributes based on attribute name, not numeric ID. RADIUS attributes, on the other hand, are enforced by numeric ID, not by name.
The ASA enforces the LDAP attributes based on attribute name, not numeric ID. RADIUS attributes, on the other hand, are enforced by numeric ID, not by name.
Authorization refers to the process of enforcing permissions or attributes. An LDAP server defined as an authentication or authorization server enforces permissions or attributes if they are configured.
For software Version 7.0, LDAP attributes include the cVPN3000 prefix. For software Versions 7.1 and later, this prefix was removed.
Supported Cisco Attributes for LDAP Authorization
This section provides a complete list of attributes (see Table C-2 ) for the ASA 5500, VPN 3000 concentrator, and PIX 500 series ASAs. The table includes attribute support information for the VPN 3000 concentrator and PIX 500 series ASAs to assist you in configuring networks with a combination of these devices.
|
|
|
|
|
|
|
|
|---|---|---|---|---|---|---|
Banner string for clientless and client SSL VPN, and IPsec clients. |
||||||
Banner string for clientless and client SSL VPN, and IPsec clients. |
||||||
An octet string in the following format: [Prefix] [Action] [Protocol] [Source] [Source Wildcard Mask] [Destination] [Destination Wildcard Mask] [Established] [Log] [Operator] [Port] For more information, see the “Cisco AV Pair Attribute Syntax” section.” |
||||||
Possible values: UID, OU, O, CN, L, SP, C, EA, T, N, GN, SN, I, GENQ, DNQ, SER, and use-entire-name. |
||||||
Sets the group policy for the remote access VPN session. For version 8.2 and later, use this attribute instead of IETF-Radius-Class. You can use one of the three following formats: |
||||||
A list of DNS domains. Entries must be separated by the new line character sequence (\n). |
||||||
1 = Do not modify proxy settings |
||||||
Sets the group policy for the remote access VPN session. For versions 8.2 and later, we recommend that you use the Group-Policy attribute. You can use one of the three following formats: |
||||||
Access list name that is defined on the ASA. The setting applies to VPN remote access IPsec and SSL VPN clients. |
||||||
An IP address. The setting applies to VPN remote access IPsec and SSL VPN clients. |
||||||
An IP address mask. The setting applies to VPN remote access IPsec and SSL VPN clients. |
||||||
1 = Login |
||||||
|
|
|
|
|
1 = RADIUS 2 = LDAP (authorization only) 3 = NT Domain 4 = SDI (RSA) 5 = Internal 6 = RADIUS with Expiry 7 = Kerberos or Active Directory |
||
1 = Use client-configured list |
||||||
Specifies the name of the filter to be pushed to the client as firewall policy. |
||||||
Specifies the single default domain name to send to the client (1 - 255 characters). |
||||||
1 = Required |
||||||
0 = None |
||||||
|
|
|
|
|
|
||
Specifies the list of secondary domain names to send to the client (1 - 255 characters). |
||||||
0 = Tunnel everything |
||||||
Specifies the name of the network or access list that describes the split tunnel inclusion list. |
||||||
| 1 = Encryption required |
||||||
| 1 = Encryption required |
||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
1 = Cisco Systems (with Cisco Integrated Client) |
||||||
| 1 = Cisco Intrusion Prevention Security Agent or Cisco Integrated Client (CIC) 1 = Zone Alarm 1 = Personal Firewall |
||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
1 = PPTP |
||||
| With Versions 8.0 and later, this attribute is not required. |
||||||
See the SSL VPN Deployment Guide for examples at the following URL: http://supportwiki.cisco.com/ViewWiki/index.php/Cisco_ASA_5500_SSL_VPN_Deployment_Guide%2C_Version_8.x |
||||||
See the SSL VPN Deployment Guide for examples at the following URL: http://supportwiki.cisco.com/ViewWiki/index.php/Cisco_ASA_5500_SSL_VPN_Deployment_Guide%2C_Version_8.x |
||||||
0 = Disabled |
||||||
0 = Disabled |
||||||
Cisco AV Pair Attribute Syntax
The Cisco Attribute Value (AV) pair (ID Number 26/9/1) can be used to enforce access lists from a RADIUS server (like Cisco ACS), or from an LDAP server via an LDAP attribute map.
The syntax of each Cisco-AV-Pair rule is as follows:
[Prefix] [Action] [Protocol] [Source] [Source Wildcard Mask] [Destination] [Destination Wildcard Mask] [Established] [Log] [Operator] [Port]
Table C-3 describes the syntax rules.
Cisco AV Pairs ACL Examples
Table C-4 shows examples of Cisco AV pairs and describes the permit or deny actions that result.

Note![]() Each ACL # in inacl# must be unique. However, they do not need to be sequential (for example, 1, 2, 3, 4). That is, they could be 5, 45, 135.
Each ACL # in inacl# must be unique. However, they do not need to be sequential (for example, 1, 2, 3, 4). That is, they could be 5, 45, 135.
URL Types Supported in ACLs
The URL may be a partial URL, contain wildcards for the server, or include a port.
The following URL types are supported.

Note![]() The URLs listed in this table appear in CLI or ASDM menus based on whether or not the associated plug-in is enabled.
The URLs listed in this table appear in CLI or ASDM menus based on whether or not the associated plug-in is enabled.
Guidelines for Using Cisco-AV Pairs (ACLs)
- Use Cisco-AV pair entries with the ip:inacl# prefix to enforce access lists for remote IPsec and SSL VPN Client (SVC) tunnels.
- Use Cisco-AV pair entries with the webvpn:inacl# prefix to enforce access lists for SSL VPN clientless (browser-mode) tunnels.
- For webtype ACLs, you do not specify the source because the ASA is the source.
Table C-5 lists the tokens for the Cisco-AV-pair attribute:
Active Directory/LDAP VPN Remote Access Authorization Examples
This section presents example procedures for configuring authentication and authorization on the ASA using the Microsoft Active Directory server. It includes the following topics:
- User-Based Attributes Policy Enforcement
- Placing LDAP Users in a Specific Group Policy
- Enforcing Static IP Address Assignment for AnyConnect Tunnels
- Enforcing Dial-in Allow or Deny Access
- Enforcing Logon Hours and Time-of-Day Rules
Other configuration examples available on Cisco.com include the following TechNotes.
- ASA/PIX: Mapping VPN Clients to VPN Group Policies Through LDAP Configuration Example at the following URL:
http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a008089149d.shtml
http://www.cisco.com/en/US/partner/products/ps6120/products_configuration_example09186a00808d1a7c.shtml
User-Based Attributes Policy Enforcement
You can map any standard LDAP attribute to a well-known Vendor-Specific Attribute (VSA) as well as map one or more LDAP attribute(s) to one or more Cisco LDAP attributes.
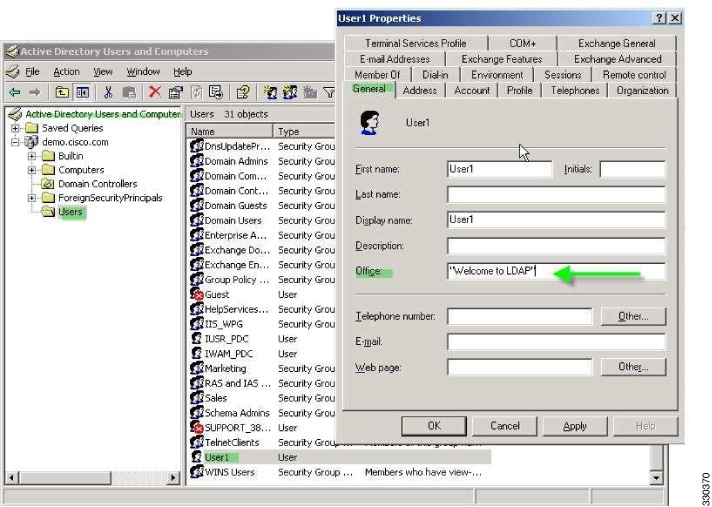
The following example shows how to configure the ASA to enforce a simple banner for a user configured on an AD LDAP server. On the server, use the Office field in the General tab to enter the banner text. This field uses the attribute named physicalDeliveryOfficeName. On the ASA, create an attribute map that maps physicalDeliveryOfficeName to the Cisco attribute Banner1. During authentication, the ASA retrieves the value of physicalDeliveryOfficeName from the server, maps the value to the Cisco attribute Banner1, and displays the banner to the user.
This example applies to any connection type, including the IPsec VPN client, AnyConnect SSL VPN client, or clientless SSL VPN. In the example, User1 connects through a clientless SSL VPN connection.
To configure the attributes for a user on the AD or LDAP Server, perform the following steps:
The Properties dialog box appears (see Figure C-3).
Step 2![]() Click the General tab and enter banner text in the Office field, which uses the AD/LDAP attribute physicalDeliveryOfficeName.
Click the General tab and enter banner text in the Office field, which uses the AD/LDAP attribute physicalDeliveryOfficeName.
Figure C-3 LDAP User Configuration
Step 3![]() Create an LDAP attribute map on the ASA.
Create an LDAP attribute map on the ASA.
The following example creates the map Banner and maps the AD/LDAP attribute physicalDeliveryOfficeName to the Cisco attribute Banner1:
Step 4![]() Associate the LDAP attribute map to the AAA server.
Associate the LDAP attribute map to the AAA server.
The following example enters the aaa server host configuration mode for the host 10.1.1.2 in the AAA server group MS_LDAP, and associates the attribute map Banner that you created in Step 3:
Step 5![]() Test the banner enforcement.
Test the banner enforcement.
The following example shows a clientless SSL connection and the banner enforced through the attribute map after the user authenticates (see Figure C-4).

Placing LDAP Users in a Specific Group Policy
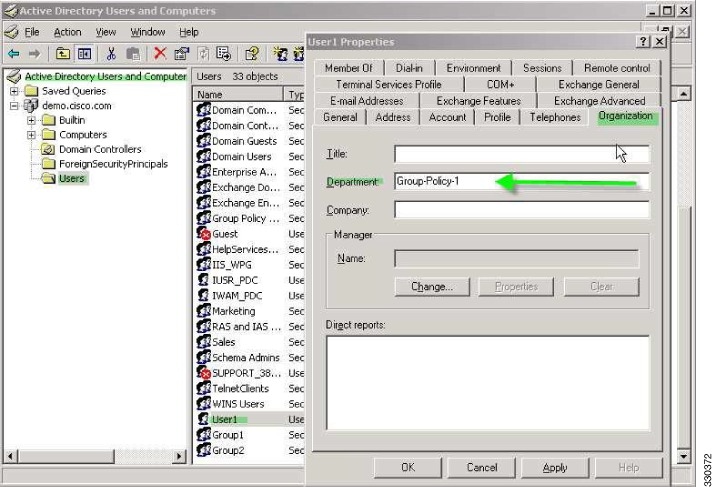
The following example shows how to authenticate User1 on the AD LDAP server to a specific group policy on the ASA. On the server, use the Department field of the Organization tab to enter the name of the group policy. Then create an attribute map and map Department to the Cisco attribute IETF-Radius-Class. During authentication, the ASA retrieves the value of Department from the server, maps the value to the IETF-Radius-Class, and places User1 in the group policy.
This example applies to any connection type, including the IPsec VPN client, AnyConnect SSL VPN client, or clientless SSL VPN. In this example, User1 is connecting through a clientless SSL VPN connection.
To configure the attributes for the user on the AD LDAP server, perform the following steps:
The Properties dialog box appears (see Figure C-5).
Step 2![]() Click the Organization tab and enter Group-Policy-1 in the Department field.
Click the Organization tab and enter Group-Policy-1 in the Department field.
Figure C-5 AD/LDAP Department Attribute
Step 3![]() Define an attribute map for the LDAP configuration shown in Step 1.
Define an attribute map for the LDAP configuration shown in Step 1.
The following example shows how to map the AD attribute Department to the Cisco attribute IETF-Radius-Class.
Step 4![]() Associate the LDAP attribute map to the AAA server.
Associate the LDAP attribute map to the AAA server.
The following example enters the aaa server host configuration mode for the host 10.1.1.2 in the AAA server group MS_LDAP, and associates the attribute map group_policy that you created in Step 3:
Step 5![]() Add the new group-policy on the ASA and configure the required policy attributes that will be assigned to the user. The following example creates Group-policy-1, the name entered in the Department field on the server:
Add the new group-policy on the ASA and configure the required policy attributes that will be assigned to the user. The following example creates Group-policy-1, the name entered in the Department field on the server:
Step 6![]() Establish the VPN connection as the user would, and verify that the session inherits the attributes from Group-Policy1 (and any other applicable attributes from the default group-policy).
Establish the VPN connection as the user would, and verify that the session inherits the attributes from Group-Policy1 (and any other applicable attributes from the default group-policy).
Step 7![]() Monitor the communication between the ASA and the server by enabling the debug ldap 255 command from privileged EXEC mode. The following is sample output from this command, which has been edited to provide the key messages:
Monitor the communication between the ASA and the server by enabling the debug ldap 255 command from privileged EXEC mode. The following is sample output from this command, which has been edited to provide the key messages:
Enforcing Static IP Address Assignment for AnyConnect Tunnels
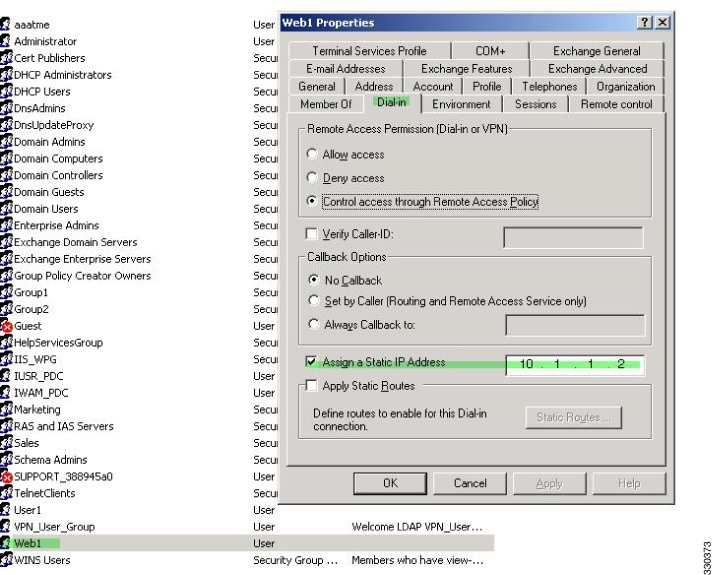
In this example, configure the AnyConnect client user Web1 to receive a static IP address. then enter the address in the Assign Static IP Address field of the Dialin tab on the AD LDAP server. This field uses the msRADIUSFramedIPAddress attribute. Create an attribute map that maps this attribute to the Cisco attribute IETF-Radius-Framed-IP-Address.
During authentication, the ASA retrieves the value of msRADIUSFramedIPAddress from the server, maps the value to the Cisco attribute IETF-Radius-Framed-IP-Address, and provides the static address to User1.
The following example applies to full-tunnel clients, including the IPsec client and the SSL VPN clients (AnyConnect client 2.x and the SSL VPN client).
To configure the user attributes on the AD/LDAP server, perform the following steps:
Step 1![]() Right-click the username.
Right-click the username.
The Properties dialog box appears (see Figure C-6).
Step 2![]() Click the Dialin tab, check the Assign Static IP Address check box, and enter an IP address of 10.1.1.2.
Click the Dialin tab, check the Assign Static IP Address check box, and enter an IP address of 10.1.1.2.
Figure C-6 Assign Static IP Address
Step 3![]() Create an attribute map for the LDAP configuration shown in Step 1.
Create an attribute map for the LDAP configuration shown in Step 1.
The following example shows how to map the AD attribute msRADIUSFramedIPAddress used by the Static Address field to the Cisco attribute IETF-Radius-Framed-IP-Address:
Step 4![]() Associate the LDAP attribute map to the AAA server.
Associate the LDAP attribute map to the AAA server.
The following example enters the aaa server host configuration mode for the host 10.1.1.2, in the AAA server group MS_LDAP, and associates the attribute map static_address that you created in Step 3:
Step 5![]() Verify that the vpn-address-assignment command is configured to specify AAA by viewing this part of the configuration with the show run all vpn-addr-assign command:
Verify that the vpn-address-assignment command is configured to specify AAA by viewing this part of the configuration with the show run all vpn-addr-assign command:
Step 6![]() Establish a connection to the ASA with the AnyConnect client. Observe the following:
Establish a connection to the ASA with the AnyConnect client. Observe the following:
- The banner is received in the same sequence as a clientless connection (see Figure C-7).
- The user receives the IP address configured on the server and mapped to the ASA (see Figure C-8).
Figure C-7 Verify the Banner for the AnyConnect Session

Figure C-8 AnyConnect Session Established

Step 7![]() Use the show vpn-sessiondb svc command to view the session details and verify the address assigned:
Use the show vpn-sessiondb svc command to view the session details and verify the address assigned:
Enforcing Dial-in Allow or Deny Access
The following example creates an LDAP attribute map that specifies the tunneling protocols allowed by the user. You map the allow access and deny access settings on the Dialin tab to the Cisco attribute Tunneling-Protocol, which supports the bitmap values shown in Table C-6 :
|
|
|
|---|---|
41 |
|
82 |
|
|
1.IPsec and L2TP over IPsec are not supported simultaneously. Therefore, the values 4 and 8 are mutually exclusive. |
Use this attribute to create an Allow Access (TRUE) or a Deny Access (FALSE) condition for the protocols and enforce the method for which the user is allowed access.
For this simplified example, by mapping the tunnel protocol IPsec/IKEv1 (4), you can create an allow (true) condition for the Cisco VPN client. You also map WebVPN (16) and SVC/AC (32), which are mapped as a value of 48 (16+32) and create a deny (false) condition. This allows the user to connect to the ASA using IPsec, but any attempt to connect using clientless SSL or the AnyConnect client is denied.
Another example of enforcing dial-in allow access or deny access is available in the Tech Note ASA/PIX: Mapping VPN Clients to VPN Group Policies Through LDAP Configuration Example at the following URL:
http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a008089149d.shtml
To configure the user attributes on the AD/LDAP server, perform the following steps:
The Properties dialog box appears.
Step 2![]() Click the Dial-in tab, then click the Allow Access radio button (Figure C-9).
Click the Dial-in tab, then click the Allow Access radio button (Figure C-9).
Figure C-9 AD/LDAP User1 - Allow Access


Note![]() If you select the Control access through the Remote Access Policy option, then a value is not returned from the server, and the permissions that are enforced are based on the internal group policy settings of the ASA.
If you select the Control access through the Remote Access Policy option, then a value is not returned from the server, and the permissions that are enforced are based on the internal group policy settings of the ASA.
Step 3![]() Create an attribute map to allow both an IPsec and AnyConnect connection, but deny a clientless SSL connection.
Create an attribute map to allow both an IPsec and AnyConnect connection, but deny a clientless SSL connection.
The following example shows how to create the map tunneling_protocols, and map the AD attribute msNPAllowDialin used by the Allow Access setting to the Cisco attribute Tunneling-Protocols using the map-name command, and add map values with the map-value command:
Step 4![]() Associate the LDAP attribute map to the AAA server.
Associate the LDAP attribute map to the AAA server.
The following example enters the aaa server host configuration mode for the host 10.1.1.2, in the AAA server group MS_LDAP, and associates the attribute map tunneling_protocols that you created in Step 2:
Step 5![]() Verify that the attribute map works as configured.
Verify that the attribute map works as configured.
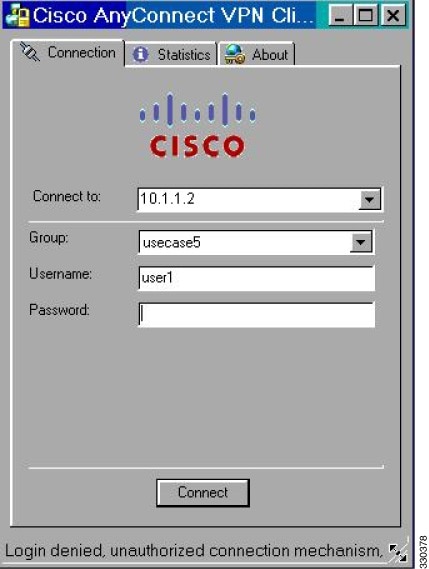
Step 6![]() Try connections using clientless SSL, the AnyConnect client, and the IPsec client. The clientless and AnyConnect connections should fail, and the user should be informed that an unauthorized connection mechanism was the reason for the failed connection. The IPsec client should connect because IPsec is an allowed tunneling protocol according to the attribute map (see Figure C-10 and Figure C-11).
Try connections using clientless SSL, the AnyConnect client, and the IPsec client. The clientless and AnyConnect connections should fail, and the user should be informed that an unauthorized connection mechanism was the reason for the failed connection. The IPsec client should connect because IPsec is an allowed tunneling protocol according to the attribute map (see Figure C-10 and Figure C-11).
Figure C-10 Login Denied Message for Clientless User
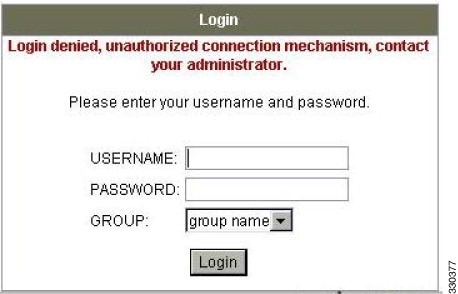
Figure C-11 Login Denied Message for AnyConnect Client User
Enforcing Logon Hours and Time-of-Day Rules
The following example shows how to configure and enforce the hours that a clientless SSL user (such as a business partner) is allowed to access the network.
On the AD server, use the Office field to enter the name of the partner, which uses the physicalDeliveryOfficeName attribute. Then we create an attribute map on the ASA to map that attribute to the Cisco attribute Access-Hours. During authentication, the ASA retrieves the value of physicalDeliveryOfficeName and maps it to Access-Hours.
To configure the user attributes on the AD /LDAP server, perform the following steps:
Step 1![]() Select the user, and right-click Properties.
Select the user, and right-click Properties.
The Properties dialog box appears (see Figure C-12).
Figure C-12 Active Directory Properties Dialog Box

Step 3![]() Create an attribute map.
Create an attribute map.
The following example shows how to create the attribute map access_hours and map the AD attribute physicalDeliveryOfficeName used by the Office field to the Cisco attribute Access-Hours.
Step 4![]() Associate the LDAP attribute map to the AAA server.
Associate the LDAP attribute map to the AAA server.
The following example enters the aaa server host configuration mode for the host 10.1.1.2, in the AAA server group MS_LDAP, and associates the attribute map access_hours that you created in Step 3:
Step 5![]() Configure time ranges for each value allowed on the server.
Configure time ranges for each value allowed on the server.
The following example configures Partner access hours from 9am to 5pm Monday through Friday:
Configuring an External RADIUS Server
This section presents an overview of the RADIUS configuration procedure and defines the Cisco RADIUS attributes. It includes the following topics:
- Reviewing the RADIUS Configuration Procedure
- ASA RADIUS Authorization Attributes
- ASA IETF RADIUS Authorization Attributes
- RADIUS Accounting Disconnect Reason Codes
Reviewing the RADIUS Configuration Procedure
This section describes the RADIUS configuration steps required to support authentication and authorization of ASA users.
To set up the RADIUS server to interoperate with the ASA, preform the following steps:
Step 1![]() Load the ASA attributes into the RADIUS server. The method you use to load the attributes depends on which type of RADIUS server you are using:
Load the ASA attributes into the RADIUS server. The method you use to load the attributes depends on which type of RADIUS server you are using:
- If you are using Cisco ACS: the server already has these attributes integrated. You can skip this step.
- For RADIUS servers from other vendors (for example, Microsoft Internet Authentication Service): you must manually define each ASA attribute. To define an attribute, use the attribute name or number, type, value, and vendor code (3076). For a list of ASA RADIUS authorization attributes and values, see Table C-7.
Step 2![]() Set up the users or groups with the permissions and attributes to send during IPsec or SSL tunnel establishment.
Set up the users or groups with the permissions and attributes to send during IPsec or SSL tunnel establishment.
ASA RADIUS Authorization Attributes
Authorization refers to the process of enforcing permissions or attributes. A RADIUS server defined as an authentication server enforces permissions or attributes if they are configured. These attributes have vendor ID 3076.
Table C-7 lists the ASA supported RADIUS attributes that can be used for user authorization.

Note![]() RADIUS attribute names do not contain the cVPN3000 prefix. Cisco Secure ACS 4.x supports this new nomenclature, but attribute names in pre-4.0 ACS releases still include the cVPN3000 prefix. The ASAs enforce the RADIUS attributes based on attribute numeric ID, not attribute name. LDAP attributes are enforced by their name, not by the ID.
RADIUS attribute names do not contain the cVPN3000 prefix. Cisco Secure ACS 4.x supports this new nomenclature, but attribute names in pre-4.0 ACS releases still include the cVPN3000 prefix. The ASAs enforce the RADIUS attributes based on attribute numeric ID, not attribute name. LDAP attributes are enforced by their name, not by the ID.
All attributes listed in Table C-7 are downstream attributes that are sent from the RADIUS server to the ASA except for the following attribute numbers: 146, 150, 151, and 152. These attribute numbers are upstream attributes that are sent from the ASA to the RADIUS server. RADIUS attributes 146 and 150 are sent from the ASA to the RADIUS server for authentication and authorization requests. All four previously listed attributes are sent from the ASA to the RADIUS server for accounting start, interim-update, and stop requests. Upstream RADIUS attributes 146, 150, 151, and 152 were introduced in ASA Version 8.4.3.
|
|
|
|
|
|
|
Valued |
|
|---|---|---|---|---|---|---|---|
1 = PPTP |
|||||||
0 = None |
|||||||
Banner string to display for Cisco VPN remote access sessions: IPsec IKEv1, AnyConnect SSL-TLS/DTLS/IKEv2, and Clientless SSL |
|||||||
Bitmap: |
|||||||
Bitmap: |
|||||||
Sets the group policy for the remote access VPN session. For versions 8.2 and later, use this attribute instead of IETF-Radius-Class. You can use one of the three following formats: |
|||||||
Specifies the name of the network/access list that describes the split tunnel inclusion list. |
|||||||
Specifies the single default domain name to send to the client (1-255 characters). |
|||||||
Specifies the list of secondary domain names to send to the client (1-255 characters). |
|||||||
Banner string to display for Cisco VPN remote access sessions: IPsec IKEv1, AnyConnect SSL-TLS/DTLS/IKEv2, and Clientless SSL. The Banner2 string is concatenated to the Banner1 string, if configured. |
|||||||
1 = Required |
|||||||
1 = Cisco Systems (with Cisco Integrated Client) |
|||||||
| 1 = Cisco Intrusion Prevention Security Agent or Cisco Integrated Client (CIC) Zone Labs Products: NetworkICE Product: Sygate Products: |
|||||||
0 = No split tunneling |
|||||||
0 = None |
|||||||
Specifies the name of the filter to be pushed to the client as firewall policy |
|||||||
1 = Use Client-Configured list |
|||||||
Possible values: UID, OU, O, CN, L, SP, C, EA, T, N, GN, SN, I, GENQ, DNQ, SER, use-entire-name |
|||||||
1 = Java ActiveX |
|||||||
String name (example, “Corporate-Apps”). This text replaces the default string, “Application Access,” on the clientless portal home page. |
|||||||
1 = No Modify |
|||||||
0 = Disabled |
|||||||
Name of a Smart Tunnel Auto Signon list appended by the domain name |
|||||||
Comma-delimited string, for example: Engineering, Sales
An administrative attribute that can be used in dynamic access policies. It does not set a group policy. |
|||||||
1 = Cisco VPN Client (IKEv1) |
|||||||
0 = None |
|||||||
0 = None Session Subtype applies only when the Session Type (151) attribute has the following values: 1, 2, 3, and 4. |
|||||||
Unbounded. For examples, see the SSL VPN Deployment Guide at the following URL: http://supportwiki.cisco.com/ViewWiki/index.php/Cisco_ASA_5500_SSL_VPN_Deployment_Guide%2C_Version_8.x |
|||||||
Unbounded. For examples, see the SSL VPN Deployment Guide at the following URL: http://supportwiki.cisco.com/ViewWiki/index.php/Cisco_ASA_5500_SSL_VPN_Deployment_Guide%2C_Version_8.x |
ASA IETF RADIUS Authorization Attributes
Table C-8 lists the supported IETF RADIUS attributes.
|
|
|
|
|
|
|
Valued |
|
For Versions 8.2.x and later, we recommend that you use the Group-Policy attribute (VSA 3076, #25) as described in Table C-7 : |
|||||||
Access list name that is defined on the ASA, which applies only to full tunnel IPsec and SSL VPN clients |
|||||||
Seconds. Possible Service Type values: |
|||||||
RADIUS Accounting Disconnect Reason Codes
These codes are returned if the ASA encounters a disconnect when sending packets:
|
|
|---|
Configuring an External TACACS+ Server
The ASA provides support for TACACS+ attributes. TACACS+ separates the functions of authentication, authorization, and accounting. The protocol supports two types of attributes: mandatory and optional. Both the server and client must understand a mandatory attribute, and the mandatory attribute must be applied to the user. An optional attribute may or may not be understood or used.

Note![]() To use TACACS+ attributes, make sure that you have enabled AAA services on the NAS.
To use TACACS+ attributes, make sure that you have enabled AAA services on the NAS.
Table C-9 lists supported TACACS+ authorization response attributes for cut-through-proxy connections. Table C-10 lists supported TACACS+ accounting attributes.
 Feedback
Feedback