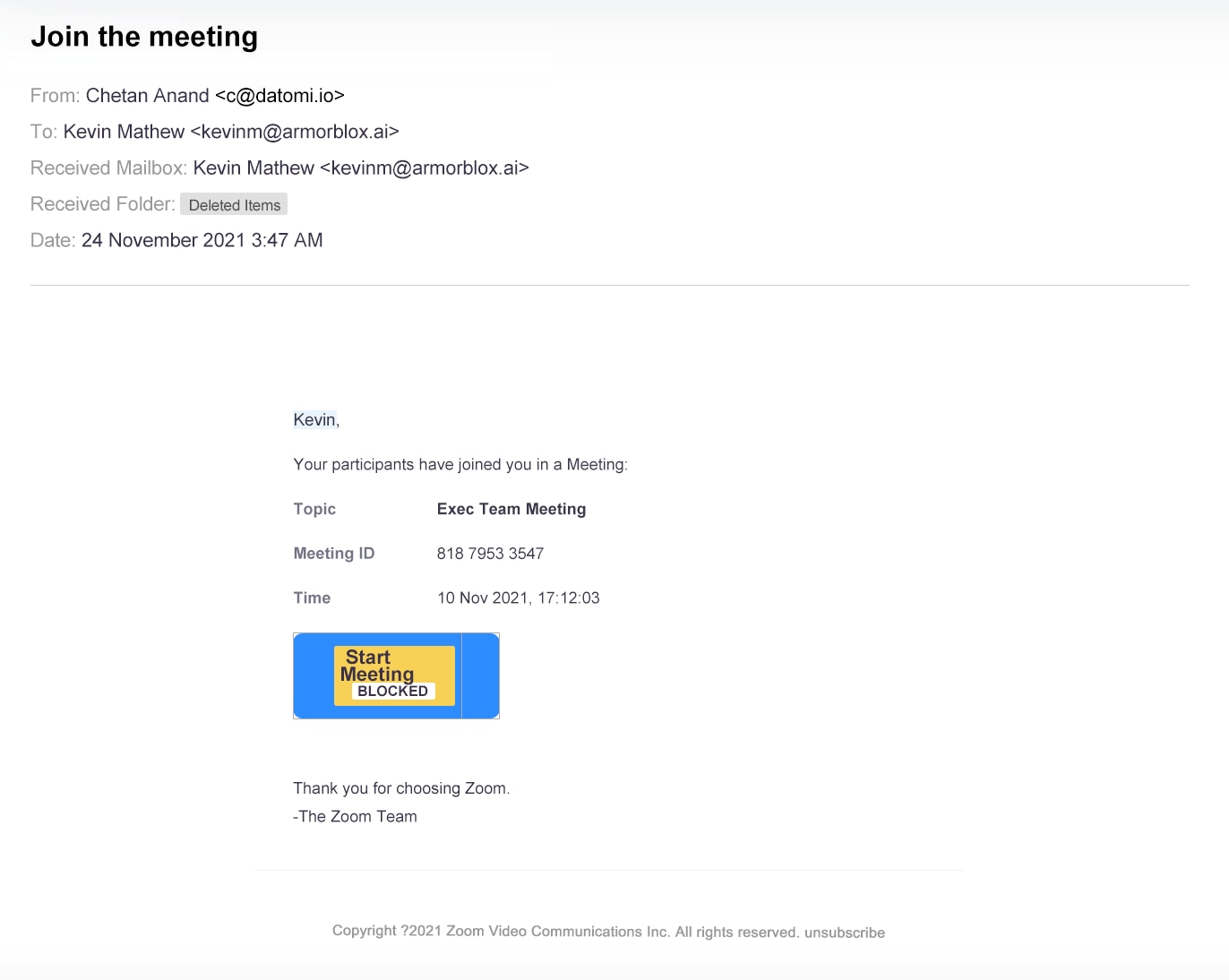
Adopt multi-factor authentication (MFA)
Implement multi-factor authentication (MFA) across your environment to significantly reduce the impact of spear phishing attacks. MFA protects your applications by requiring two or more sources of validation before granting access to users, decreasing the likelihood of spear phishing success. Even if a password is compromised in a spear phishing attack, it's useless without additional authentication steps.
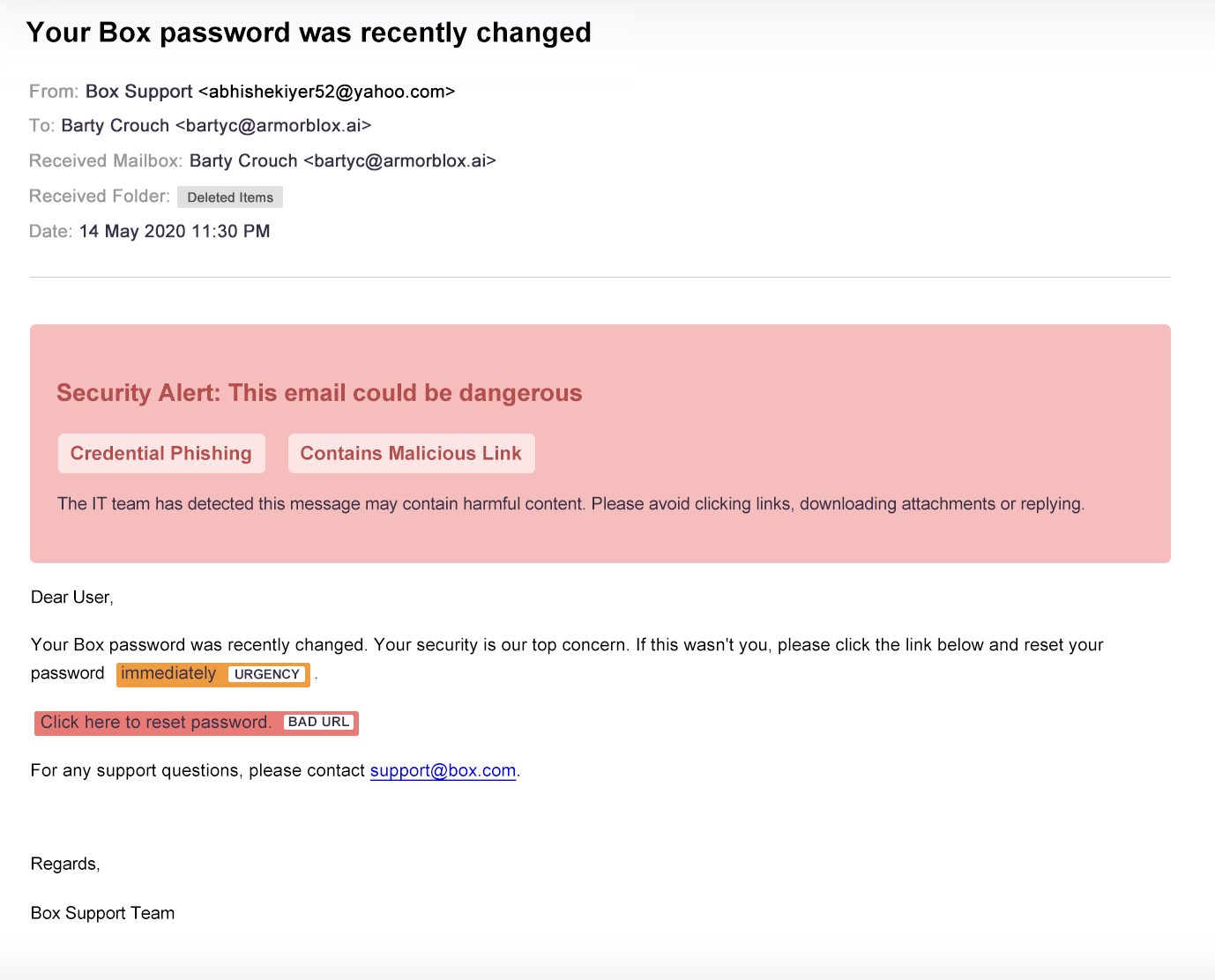
Implement strict password-management policies
Nearly 50% of all data breaches involve stolen credentials. By enforcing strict password policies and educating employees on best practices, organisations can significantly lower their risk of unauthorised access and security breaches.
Here are some best practices to consider for strong password security:
- Create long, complex passwords at least 10 characters in length
- Require MFA to verify user identities at login
- Require security challenge questions that ask for correct responses known to the user
- Store passwords in a secure password management solution
- Use biometric passwords, such as fingerprints, faces or voices
- Change your passwords frequently
Maintain regular backups and security patches
Consistently conducting backups and applying security patches is crucial in fortifying defences against spear phishing attacks. Regular backups serve as your safety net, ensuring data recovery and minimising potential losses should a breach occur.
Equally important is diligent patch management. These updates fortify your software defences by remediating vulnerabilities that attackers could exploit through spear phishing schemes.
Install advanced email security software
As spear phishing tactics become increasingly advanced and prevalent, it's imperative to adopt proactive anti-phishing measures to safeguard your organisation and its employees against data breaches, identity theft and corporate espionage. One of the most effective defences is to invest in a reputable email security solution.
Sophisticated email security solutions like Cisco Secure Email Threat Defense offer robust phishing protection, employing advanced algorithms that scrutinise thousands of signals across identity, behaviour and language. This system not only detects typical attack indicators transmitted by email, but it also neutralises threats before they can inflict damage, fortifying your organisation's critical communications.
Employ Advanced Malware Protection (AMP)
Because no security solution can prevent all spear phishing attacks, it's essential to layer your defences. Advanced Malware Protection software prevents, detects and removes software viruses that may have been installed in a successful phishing attack, such as ransomware, worms, spyware, adware or Trojans.
By employing AMP, organisations can significantly reduce the impact of potential breaches, ensuring that even if an attack penetrates initial defences, its effects are contained and minimised.
Prioritise security awareness training
Empowering employees with knowledge is only effective when applied consistently. Security awareness shouldn't be a one-time initiative. Given the evolving nature of spear phishing attacks and other dangerous threats, continuous employee training is essential. Integrate anti-phishing education into both the onboarding process for new recruits and as regular, updated training for existing staff. Continuous education helps employees stay ahead of spear phishing attempts, safeguarding your organisation's sensitive data and systems.