- RADIUS Attributes Overview and RADIUS IETF Attributes
- RADIUS Vendor-Proprietary Attributes
- RADIUS Vendor-Specific Attributes and RADIUS Disconnect-Cause Attribute Values
- RADIUS Attribute 8 Framed-IP-Address in Access Requests
- RADIUS Tunnel Attribute Extensions
- RADIUS Attribute Screening
- RADIUS NAS-IP-Address Attribute Configurability
RADIUS Vendor-Specific Attributes and RADIUS Disconnect-Cause Attribute Values
The Internet Engineering Task Force (IETF) draft standard specifies a method for communicating vendor-specific information between the network access server and the RADIUS server by using the vendor-specific attribute (attribute 26). Attribute 26 encapsulates vendor specific attributes (VSA), thereby, allowing vendors to support their own extended attributes otherwise not suitable for general use.
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table at the end of this module.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
Information About RADIUS Vendor-Specific Attributes and RADIUS Disconnect-Cause Attribute Values
The Cisco RADIUS implementation supports one vendor-specific option using the format recommended in the specification. Cisco's vendor-ID is 9, and the supported option has vendor-type 1, which is named "cisco-avpair." The value is a string of the following format:
protocol : attribute sep value *
"Protocol" is a value of the Cisco "protocol" attribute for a particular type of authorization; protocols that can be used include IP, IPX, VPDN, VOIP, SHELL, RSVP, SIP, AIRNET, OUTBOUND. "Attribute" and "value" are an appropriate attribute-value (AV) pair defined in the Cisco TACACS+ specification, and "sep" is "=" for mandatory attributes and "*" for optional attributes. This allows the full set of features available for TACACS+ authorization to also be used for RADIUS.
For example, the following AV pair causes Cisco's "multiple named ip address pools" feature to be activated during IP authorization (during PPP's IPCP address assignment):
cisco-avpair= "ip:addr-pool=first"
If you insert an "*", the AV pair "ip:addr-pool=first" becomes optional. Note that any AV pair can be made optional.
cisco-avpair= "ip:addr-pool*first"
The following example shows how to cause a user logging in from a network access server to have immediate access to EXEC commands:
cisco-avpair= "shell:priv-lvl=15"
Attribute 26 contains the following three elements:
The figure below shows the packet format for a VSA encapsulated "behind" attribute 26.
| Figure 1 | VSA Encapsulated Behind Attribute 26 |
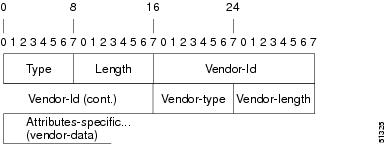
 Note |
It is up to the vendor to specify the format of their VSA. The Attribute-Specific field (also known as Vendor-Data) is dependent on the vendor's definition of that attribute. |
The table below describes significant fields listed in the Vendor-Specific RADIUS IETF Attributes table (second table below), which lists supported vendor-specific RADIUS attributes (IETF attribute 26).
| Table 1 | Vendor-Specific Attributes Table Field Descriptions |
| Field |
Description |
|---|---|
| Number |
All attributes listed in the following table are extensions of IETF attribute 26. |
| Vendor-Specific Command Codes |
A defined code used to identify a particular vendor. Code 9 defines Cisco VSAs, 311 defines Microsoft VSAs, and 529 defines Ascend VSAs. |
| Sub-Type Number |
The attribute ID number. This number is much like the ID numbers of IETF attributes, except it is a "second layer" ID number encapsulated behind attribute 26. |
| Attribute |
The ASCII string name of the attribute. |
| Description |
Description of the attribute. |
| Table 2 | Vendor-Specific RADIUS IETF Attributes |
| Number |
Vendor-Specific Company Code |
Sub-Type Number |
Attribute |
Description |
||
|---|---|---|---|---|---|---|
| MS-CHAP Attributes |
||||||
| 26 |
311 |
1 |
MSCHAP-Response |
Contains the response value provided by a PPP MS-CHAP user in response to the challenge. It is only used in Access-Request packets. This attribute is identical to the PPP CHAP Identifier. ( RFC 2548 |
||
| 26 |
311 |
11 |
MSCHAP-Challenge |
Contains the challenge sent by a network access server to an MS-CHAP user. It can be used in both Access-Request and Access-Challenge packets. ( RFC 2548 ) |
||
| VPDN Attributes |
||||||
| 26 |
9 |
1 |
l2tp-cm-local-window-size |
Specifies the maximum receive window size for L2TP control messages. This value is advertised to the peer during tunnel establishment. |
||
| 26 |
9 |
1 |
l2tp-drop-out-of-order |
Respects sequence numbers on data packets by dropping those that are received out of order. This does not ensure that sequence numbers will be sent on data packets, just how to handle them if they are received. |
||
| 26 |
9 |
1 |
l2tp-hello-interval |
Specifies the number of seconds for the hello keepalive interval. Hello packets are sent when no data has been sent on a tunnel for the number of seconds configured here. |
||
| 26 |
9 |
1 |
l2tp-hidden-avp |
When enabled, sensitive AVPs in L2TP control messages are scrambled or hidden. |
||
| 26 |
9 |
1 |
l2tp-nosession-timeout |
Specifies the number of seconds that a tunnel will stay active with no sessions before timing out and shutting down. |
||
| 26 |
9 |
1 |
tunnel-tos-reflect |
Copies the IP ToS field from the IP header of each payload packet to the IP header of the tunnel packet for packets entering the tunnel at the LNS. |
||
| 26 |
9 |
1 |
l2tp-tunnel-authen |
If this attribute is set, it performs L2TP tunnel authentication. |
||
| 26 |
9 |
1 |
l2tp-tunnel-password |
Shared secret used for L2TP tunnel authentication and AVP hiding. |
||
| 26 |
9 |
1 |
l2tp-udp-checksum |
This is an authorization attribute and defines whether L2TP should perform UDP checksums for data packets. Valid values are "yes" and "no." The default is no. |
||
| Store and Forward Fax Attributes |
||||||
| 26 |
9 |
3 |
Fax-Account-Id-Origin |
Indicates the account ID origin as defined by system administrator for the mmoip aaa receive-id or the mmoip aaa send-id commands. |
||
| 26 |
9 |
4 |
Fax-Msg-Id= |
Indicates a unique fax message identification number assigned by Store and Forward Fax. |
||
| 26 |
9 |
5 |
Fax-Pages |
Indicates the number of pages transmitted or received during this fax session. This page count includes cover pages. |
||
| 26 |
9 |
6 |
Fax-Coverpage-Flag |
Indicates whether or not a cover page was generated by the off-ramp gateway for this fax session. True indicates that a cover page was generated; false means that a cover page was not generated. |
||
| 26 |
9 |
7 |
Fax-Modem-Time |
Indicates the amount of time in seconds the modem sent fax data (x) and the amount of time in seconds of the total fax session (y), which includes both fax-mail and PSTN time, in the form x/y. For example, 10/15 means that the transfer time took 10 seconds, and the total fax session took 15 seconds. |
||
| 26 |
9 |
8 |
Fax-Connect-Speed |
Indicates the modem speed at which this fax-mail was initially transmitted or received. Possible values are 1200, 4800, 9600, and 14400. |
||
| 26 |
9 |
9 |
Fax-Recipient-Count |
Indicates the number of recipients for this fax transmission. Until e-mail servers support Session mode, the number should be 1. |
||
| 26 |
9 |
10 |
Fax-Process-Abort-Flag |
Indicates that the fax session was aborted or successful. True means that the session was aborted; false means that the session was successful. |
||
| 26 |
9 |
11 |
Fax-Dsn-Address |
Indicates the address to which DSNs will be sent. |
||
| 26 |
9 |
12 |
Fax-Dsn-Flag |
Indicates whether or not DSN has been enabled. True indicates that DSN has been enabled; false means that DSN has not been enabled. |
||
| 26 |
9 |
13 |
Fax-Mdn-Address |
Indicates the address to which MDNs will be sent. |
||
| 26 |
9 |
14 |
Fax-Mdn-Flag |
Indicates whether or not message delivery notification (MDN) has been enabled. True indicates that MDN had been enabled; false means that MDN had not been enabled. |
||
| 26 |
9 |
15 |
Fax-Auth-Status |
Indicates whether or not authentication for this fax session was successful. Possible values for this field are success, failed, bypassed, or unknown. |
||
| 26 |
9 |
16 |
Email-Server-Address |
Indicates the IP address of the e-mail server handling the on-ramp fax-mail message. |
||
| 26 |
9 |
17 |
Email-Server-Ack-Flag |
Indicates that the on-ramp gateway has received a positive acknowledgment from the e-mail server accepting the fax-mail message. |
||
| 26 |
9 |
18 |
Gateway-Id |
Indicates the name of the gateway that processed the fax session. The name appears in the following format: hostname.domain-name. |
||
| 26 |
9 |
19 |
Call-Type |
Describes the type of fax activity: fax receive or fax send. |
||
| 26 |
9 |
20 |
Port-Used |
Indicates the slot/port number of the Cisco AS5300 used to either transmit or receive this fax-mail. |
||
| 26 |
9 |
21 |
Abort-Cause |
If the fax session aborts, indicates the system component that signaled the abort. Examples of system components that could trigger an abort are FAP (Fax Application Process), TIFF (the TIFF reader or the TIFF writer), fax-mail client, fax-mail server, ESMTP client, or ESMTP server. |
||
| H323 Attributes |
||||||
| 26 |
9 |
23 |
Remote-Gateway-ID (h323-remote-address) |
Indicates the IP address of the remote gateway. |
||
| 26 |
9 |
24 |
Connection-ID (h323-conf-id) |
Identifies the conference ID. |
||
| 26 |
9 |
25 |
Setup-Time (h323-setup-time) |
Indicates the setup time for this connection in Coordinated Universal Time (UTC) formerly known as Greenwich Mean Time (GMT) and Zulu time. |
||
| 26 |
9 |
26 |
Call-Origin (h323-call-origin) |
Indicates the origin of the call relative to the gateway. Possible values are originating and terminating (answer). |
||
| 26 |
9 |
27 |
Call-Type (h323-call-type) |
Indicates call leg type. Possible values are telephony and VoIP. |
||
| 26 |
9 |
28 |
Connect-Time (h323-connect-time) |
Indicates the connection time for this call leg in UTC. |
||
| 26 |
9 |
29 |
Disconnect-Time (h323-disconnect-time) |
Indicates the time this call leg was disconnected in UTC. |
||
| 26 |
9 |
30 |
Disconnect-Cause (h323-disconnect-cause) |
Specifies the reason a connection was taken offline per Q.931 specification. |
||
| 26 |
9 |
31 |
Voice-Quality (h323-voice-quality) |
Specifies the impairment factor (ICPIF) affecting voice quality for a call. |
||
| 26 |
9 |
33 |
Gateway-ID (h323-gw-id) |
Indicates the name of the underlying gateway. |
||
| Large Scale Dialout Attributes |
||||||
| 26 |
9 |
1 |
callback-dialstring |
Defines a dialing string to be used for callback. |
||
| 26 |
9 |
1 |
data-service |
No description available. |
||
| 26 |
9 |
1 |
dial-number |
Defines the number to dial. |
||
| 26 |
9 |
1 |
force-56 |
Determines whether the network access server uses only the 56 K portion of a channel, even when all 64 K appear to be available. |
||
| 26 |
9 |
1 |
map-class |
Allows the user profile to reference information configured in a map class of the same name on the network access server that dials out. |
||
| 26 |
9 |
1 |
send-auth |
Defines the protocol to use (PAP or CHAP) for username-password authentication following CLID authentication. |
||
| 26 |
9 |
1 |
send-name |
PPP name authentication. To apply for PAP, do not configure the ppp pap sent-name password command on the interface. For PAP, "preauth:send-name" and "preauth:send-secret" will be used as the PAP username and PAP password for outbound authentication. For CHAP, "preauth:send-name" will be used not only for outbound authentication, but also for inbound authentication. For a CHAP inbound case, the NAS will use the name defined in "preauth:send-name" in the challenge packet to the caller box.
|
||
| 26 |
9 |
1 |
send-secret |
PPP password authentication. The vendor-specific attributes (VSAs) "preauth:send-name" and "preauth:send-secret" will be used as the PAP username and PAP password for outbound authentication. For a CHAP outbound case, both "preauth:send-name" and "preauth:send-secret" will be used in the response packet. |
||
| 26 |
9 |
1 |
remote-name |
Provides the name of the remote host for use in large-scale dial-out. Dialer checks that the large-scale dial-out remote name matches the authenticated name, to protect against accidental user RADIUS misconfiguration. (For example, dialing a valid phone number but connecting to the wrong router.) |
||
| Miscellaneous Attributes |
||||||
| 26 |
9 |
2 |
Cisco-NAS-Port |
Specifies additional vendor specific attribute (VSA) information for NAS-Port accounting. To specify additional NAS-Port information in the form an Attribute-Value Pair (AVPair) string, use the radius-server vsa send global configuration command.
|
||
| 26 |
9 |
1 |
min-links |
Sets the minimum number of links for MLP. |
||
| 26 |
9 |
1 |
proxyacl#<n> |
Allows users to configure the downloadable user profiles (dynamic ACLs) by using the authentication proxy feature so that users can have the configured authorization to permit traffic going through the configured interfaces. |
||
| 26 |
9 |
1 |
spi |
Carries the authentication information needed by the home agent to authenticate a mobile node during registration. The information is in the same syntax as the ip mobile secure host <addr> configuration command. Basically it contains the rest of the configuration command that follows that string, verbatim. It provides the Security Parameter Index (SPI), key, authentication algorithm, authentication mode, and replay protection timestamp range. |
For more information on configuring your NAS to recognize and use VSAs, refer to the "Configuring Router to Use Vendor-Specific RADIUS Attributes" section of th e " Configuring RADIUS " module.
RADIUS Disconnect-Cause Attribute Values
Disconnect-cause attribute values specify the reason a connection was taken offline. The attribute values are sent in Accounting request packets. These values are sent at the end of a session, even if the session fails to be authenticated. If the session is not authenticated, the attribute can cause stop records to be generated without first generating start records.
The table below lists the cause codes, values, and descriptions for the Disconnect-Cause (195) attribute.
 Note |
The Disconnect-Cause is incremented by 1000 when it is used in RADIUS AVPairs; for example, disc-cause 4 becomes 1004. |
| Table 3 | Disconnect-Cause Attribute Values |
For Q.850 cause codes and descriptions, see the Cisco IOS Voice Troubleshooting and Monitoring Guide , Release 12.4T.
Additional References
The following sections provide references related to RADIUS Vendor-Specific Attributes (VSA) and RADIUS Disconnect-Cause Attribute Values.
Related Documents
| Related Topic |
Document Title |
|---|---|
| Security Features |
Cisco IOS Security Configuration Guide: Securing User Services , Release 15.0. |
| Security Server Protocols |
|
| RADIUS Configuration |
" Configuring RADIUS " module. |
Standards
| Standard |
Title |
|---|---|
| Internet Engineering Task Force (IETF) Internet Draft: Network Access Servers Requirements |
Network Access Servers Requirements: Extended RADIUS Practices |
MIBs
| MIB |
MIBs Link |
|---|---|
| No new or modified MIBs are supported by this feature, and support for existing MIBs has not been modified by this feature. |
To locate and download MIBs for selected platforms, Cisco IOS releases, and feature sets, use Cisco MIB Locator found at the following URL: |
RFCs
| RFC |
Title |
|---|---|
| RFC 2865 |
Technical Assistance
| Description |
Link |
|---|---|
| The Cisco Support website provides extensive online resources, including documentation and tools for troubleshooting and resolving technical issues with Cisco products and technologies. To receive security and technical information about your products, you can subscribe to various services, such as the Product Alert Tool (accessed from Field Notices), the Cisco Technical Services Newsletter, and Really Simple Syndication (RSS) Feeds. Access to most tools on the Cisco Support website requires a Cisco.com user ID and password. |
Feature Information for RADIUS Vendor-Specific Attributes and RADIUS Disconnect-Cause Attribute Values
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
| Table 4 | Feature Information for RADIUS Vendor-Specific Attributes (VSA) and RADIUS Disconnect-Cause Attribute Values |
| Feature Name |
Releases |
Feature Information |
|---|---|---|
| RADIUS Vendor-Specific Attributes (VSA) and RADIUS Disconnect-Cause Attribute Values |
12.0(30)S3s 12.3(11)YS1 12.2(33)SRC |
This document discusses the Internet Engineering Task Force (IETF) draft standard, which specifies a method for communicating vendor-specific information between the network access server and the RADIUS server by using the vendor-specific attribute (attribute 26). Attribute 26 encapsulates vendor specific attributes, thereby, allowing vendors to support their own extended attributes otherwise not suitable for general use. This feature was introduced into Cisco IOS Release 12.0(30)S3s. This feature was integrated into Cisco IOS Release 12.3(11)YS1. This feature was integrated into Cisco IOS Release 12.2(33)SRC. |
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.
 Feedback
Feedback