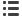
33
Cybersecurity in ASEAN: An Urgent Call to Action
“Regulators need to acknowledge that industries have
different business needs and organizational constraints,
and thus it would be difficult to mandate cybersecurity
metrics in a one-size-fit-all approach.”
—land transportation authority, ASEANcountry
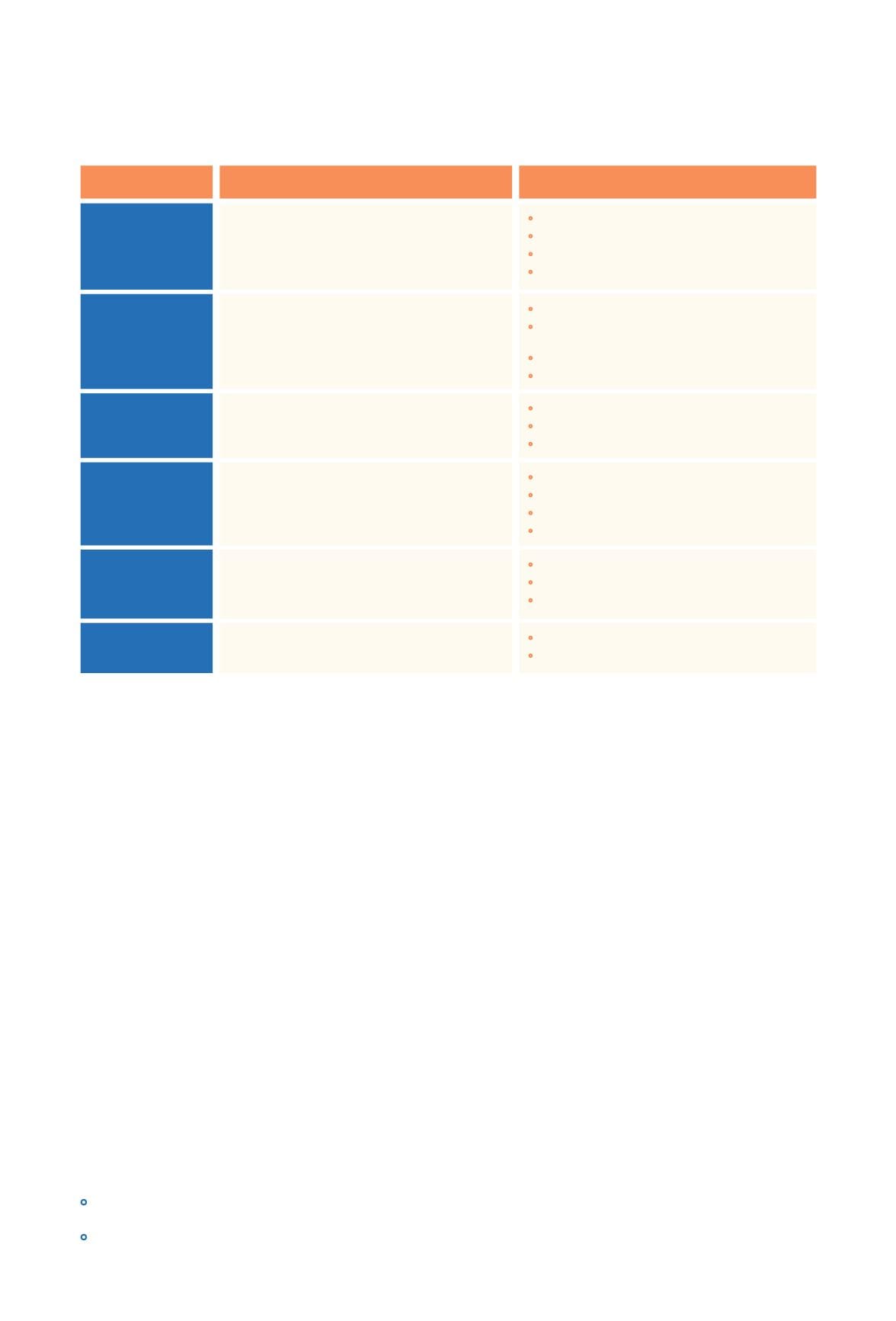
A cyber-hygiene dashboard should be an integral part of the corporate performance monitoring
system, tracking internal readiness on strategy, culture, technology, processes, and organization
(see figure 23 on page 34).
3.3 Fortify the ecosystem
The active defense mindset needs to be extended across the ecosystem in each country by not
only implementing best practice guidelines in the corporate sector, but also raising cyber
awareness across business partners. Four moves can help fortify the ecosystem:
•
Foster a risk-centric mindset around cybersecurity for the corporate sector.
•
Instill a culture of transparency in sharing threat intelligence.
Sources: Centre for Internet Security; A.T. Kearney analysis
Figure
Focus the cybersecurity agenda on relevant metrics
Incident
management
Function
Management perspective
Metrics
•
Mean time to incident discovery
•
Number of incidents
•
Mean time between security incidents
•
Mean time to incident recovery
How well do we detect, accurately identify,
handle, and recover from security incidents?
Vulnerability
management
•
Vulnerability scanning coverage
•
Percent of systems with no known
severe vulnerabilities
•
Mean time to mitigate vulnerabilities
•
Number of known vulnerabilities
How well do we manage the organization’s
exposure to vulnerabilities by identifying and
mitigating known vulnerabilities?
Patch
management
•
Patch policy compliance
•
Patch management coverage
•
Mean time to patch
How well are we able to maintain the patch
state of our systems?
Application
security
•
Number of applications
•
Percent of critical applications
•
Risk assessment coverage
•
Security testing coverage
Can we rely on the security model of
business applications to operate as intended?
Con iguration
management
•
Mean time to complete changes
•
Percent of changes with security reviews
•
Percent of changes with security exceptions
How do changes to system conigurations
aect the security of the organization?
Corporate
spending
•
IT security spending as percent of IT budget
•
IT security budget allocation
What is the level and purpose of spending
on information security?