VPN Model
VPN Objects
|
Object |
Description |
Examples |
|---|---|---|
|
VPNs |
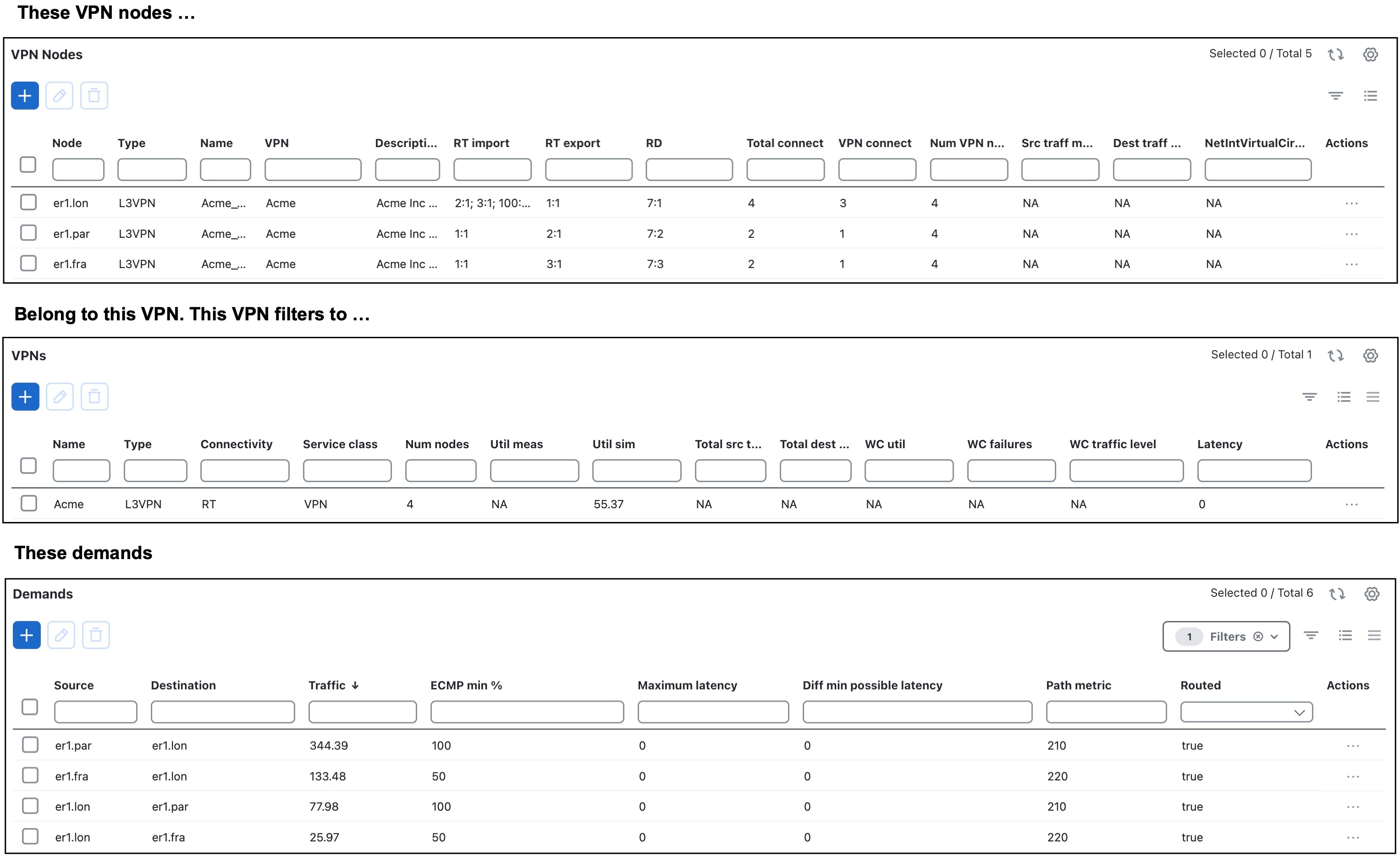
A set of VPN nodes that can exchange data with each other. |
|
|
VPN nodes |
Connection points in a VPN. They exist on standard nodes, and each node can contain multiple VPN nodes. A VPN node can be in only one VPN. |
|
VPN Topology and Connectivity
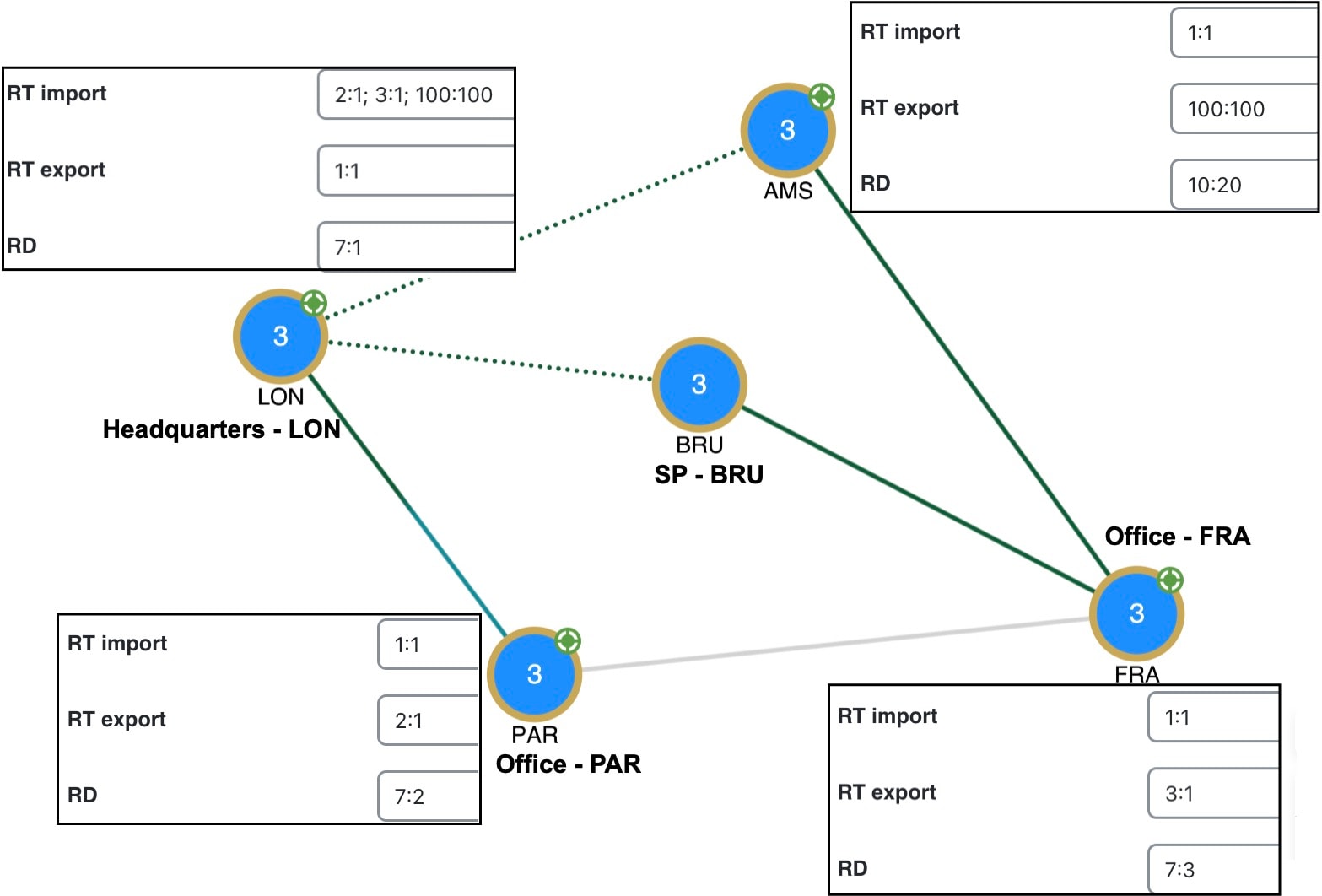
Cisco Crosswork Planning VPN topology route connections are established through Route Targets (RTs) or through a full mesh of VPN nodes. The Connectivity property is set in the Add/Edit VPN window.
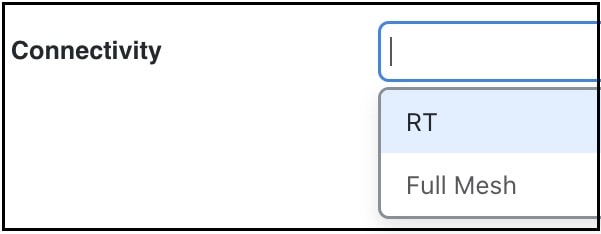
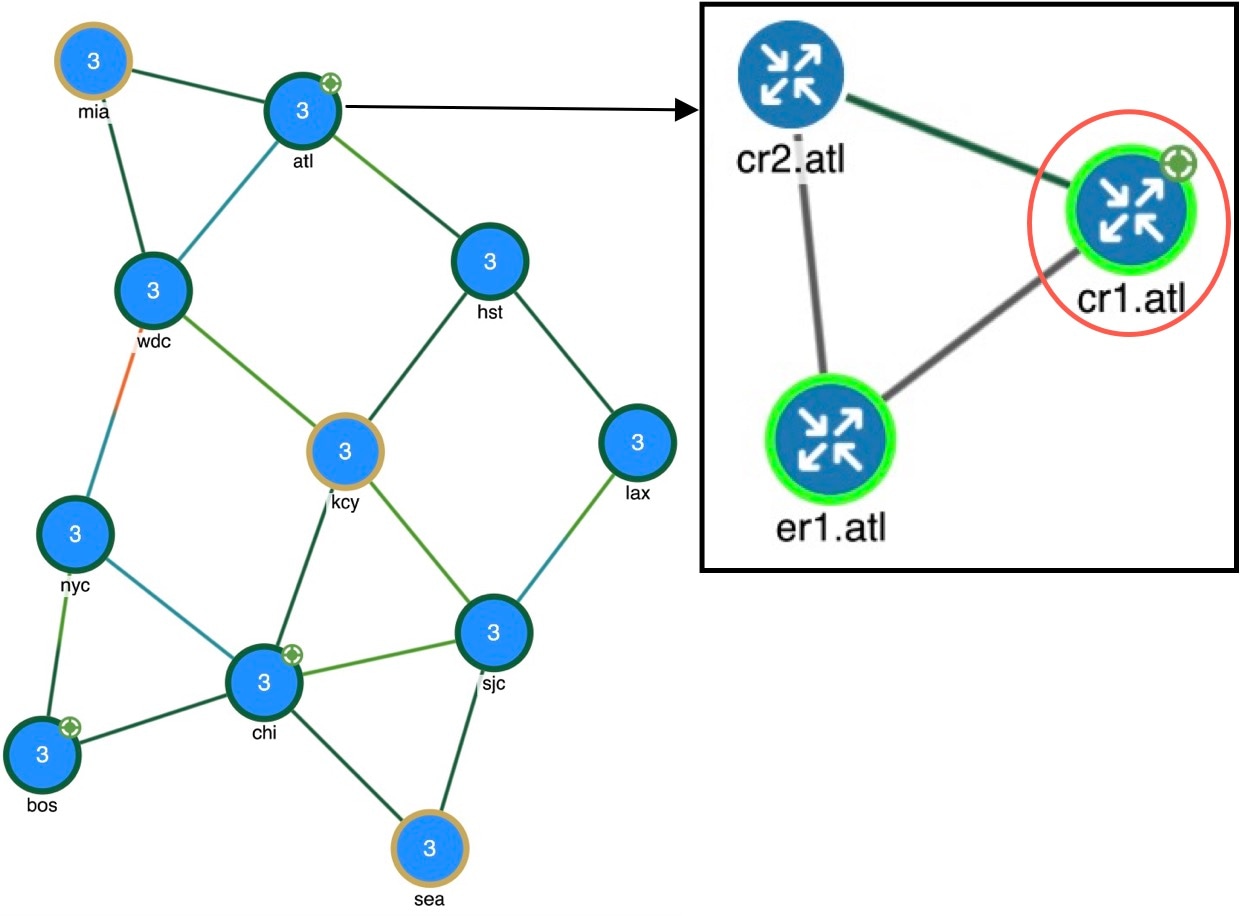
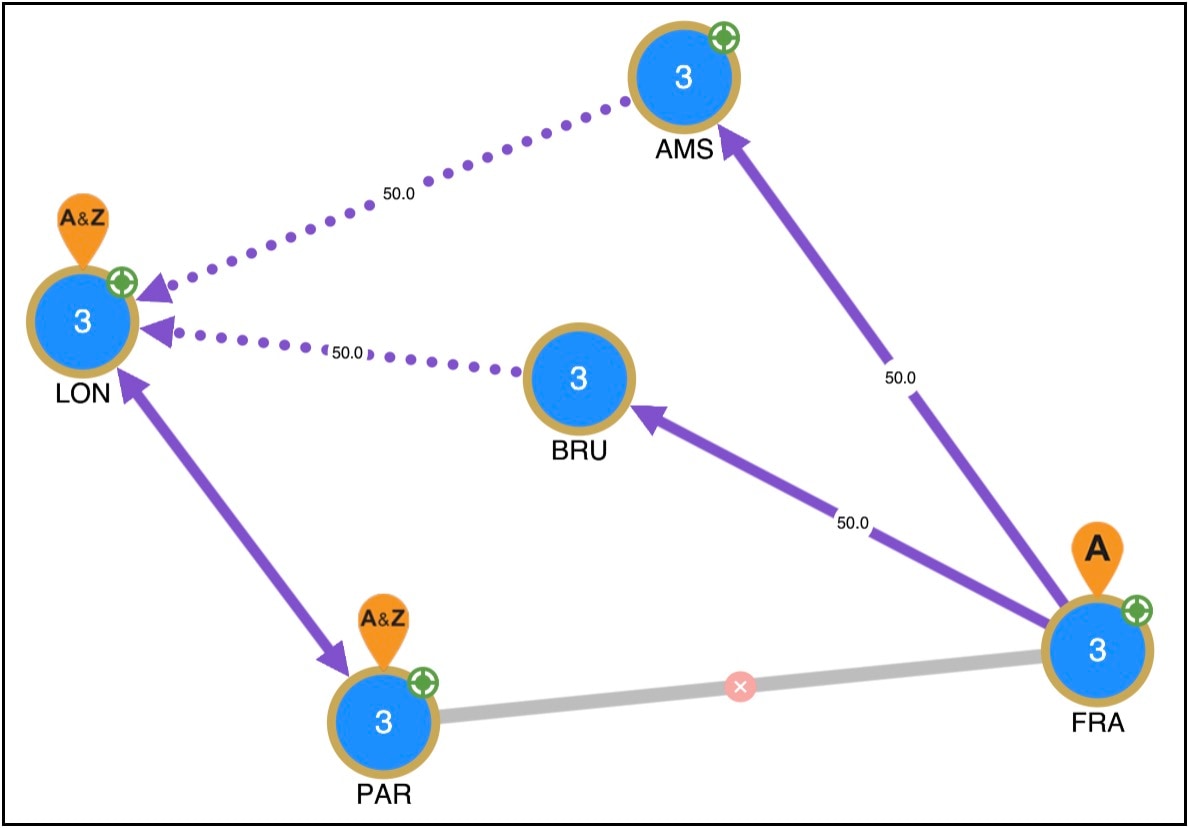
Knowing a VPN’s topology and connectivity lets Cisco Crosswork Planning calculate which demands between VPN nodes carry traffic for a particular VPN, and thus which interfaces carry traffic for that VPN. In turn, Cisco Crosswork Planning can calculate the vulnerability of a VPN to certain failure and congestion scenarios.
A demand is associated with a VPN, meaning it carries traffic for that VPN, if the following is true:
-
The two VPN nodes are in the same VPN.
-
The demand is in the same service class as the VPN.
-
Only for VPNs with RT connectivity, the RT export property of one VPN node must match the RT import property of another VPN node.
Once demands are associated with the VPN, this configuration simulates the associated access circuits exchanging traffic as if they were on the same LAN.
Note that a demand associated with a VPN can additionally contain other traffic that is for that VPN.
|
Connectivity |
Description |
|---|---|
|
Full Mesh |
Full-mesh connectivity is a complete mesh of connections between VPN nodes in a VPN so they can all communicate with each other. This connectivity is typical in a VPLS, where all VSIs identify one another based on a common AGI. |
|
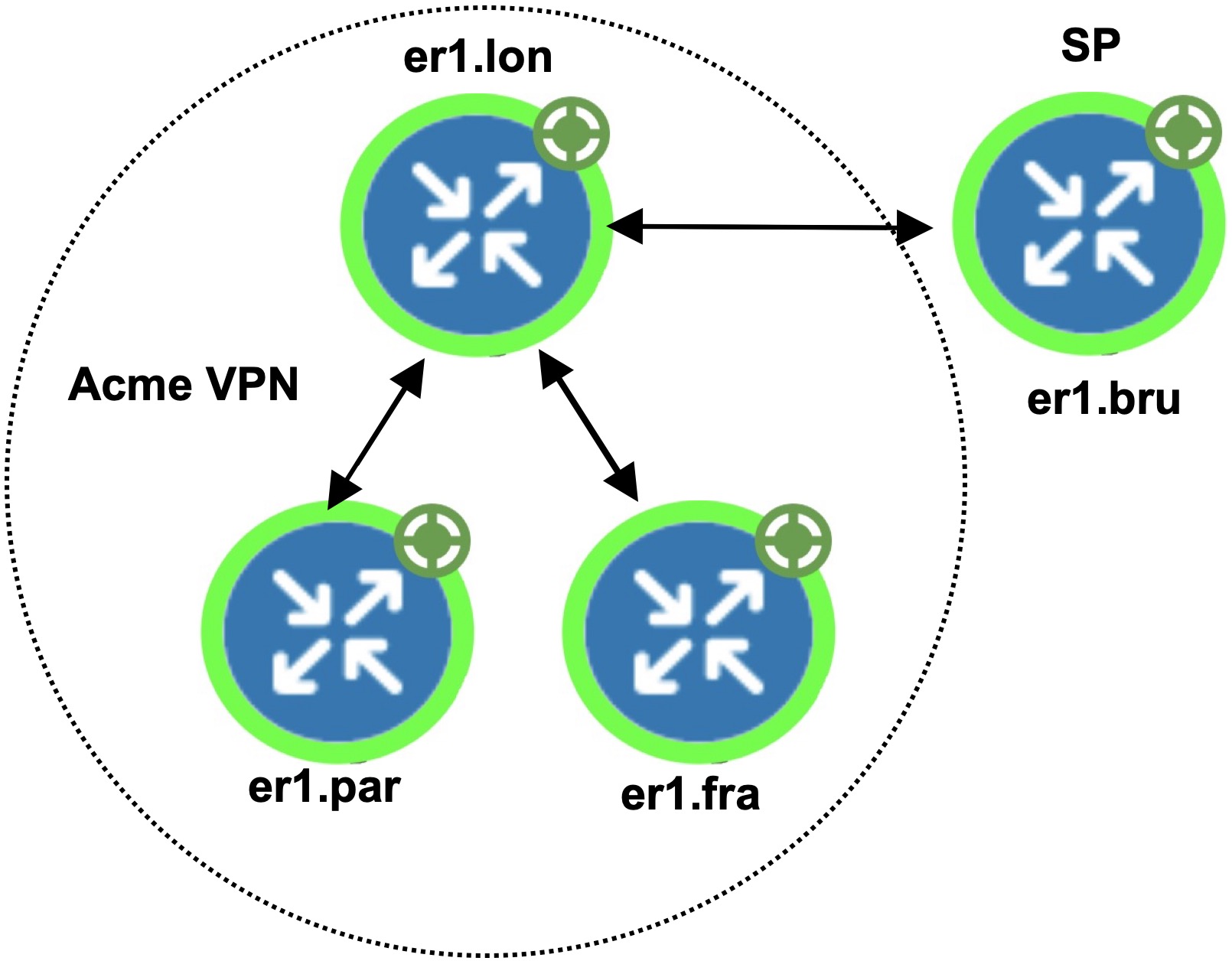
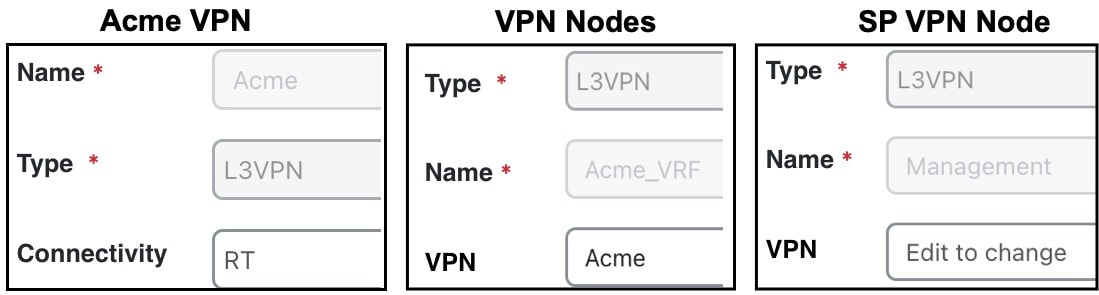
Route Targets (RT) |
Route targets model the more complex connectivity used in Layer 3 VPNs, such as hub-and-spoke networks. Here, the VRFs exchange data with one another based on the matching of RT export and RT import properties set for each VPN node. Having an import/export pair does not create bidirectional communication. Rather, traffic flows in the opposite direction of the routed advertisements. For example, if node A’s RT import matches node B’s RT export, traffic can flow from node A to B. For traffic to flow from node B back to node A, node B must have an RT import that matches an RT export of node A. This combination of matching imported and exported RTs defines which VPN nodes can exchange data. The VPN name identifies the VPN itself. |

 Feedback
Feedback