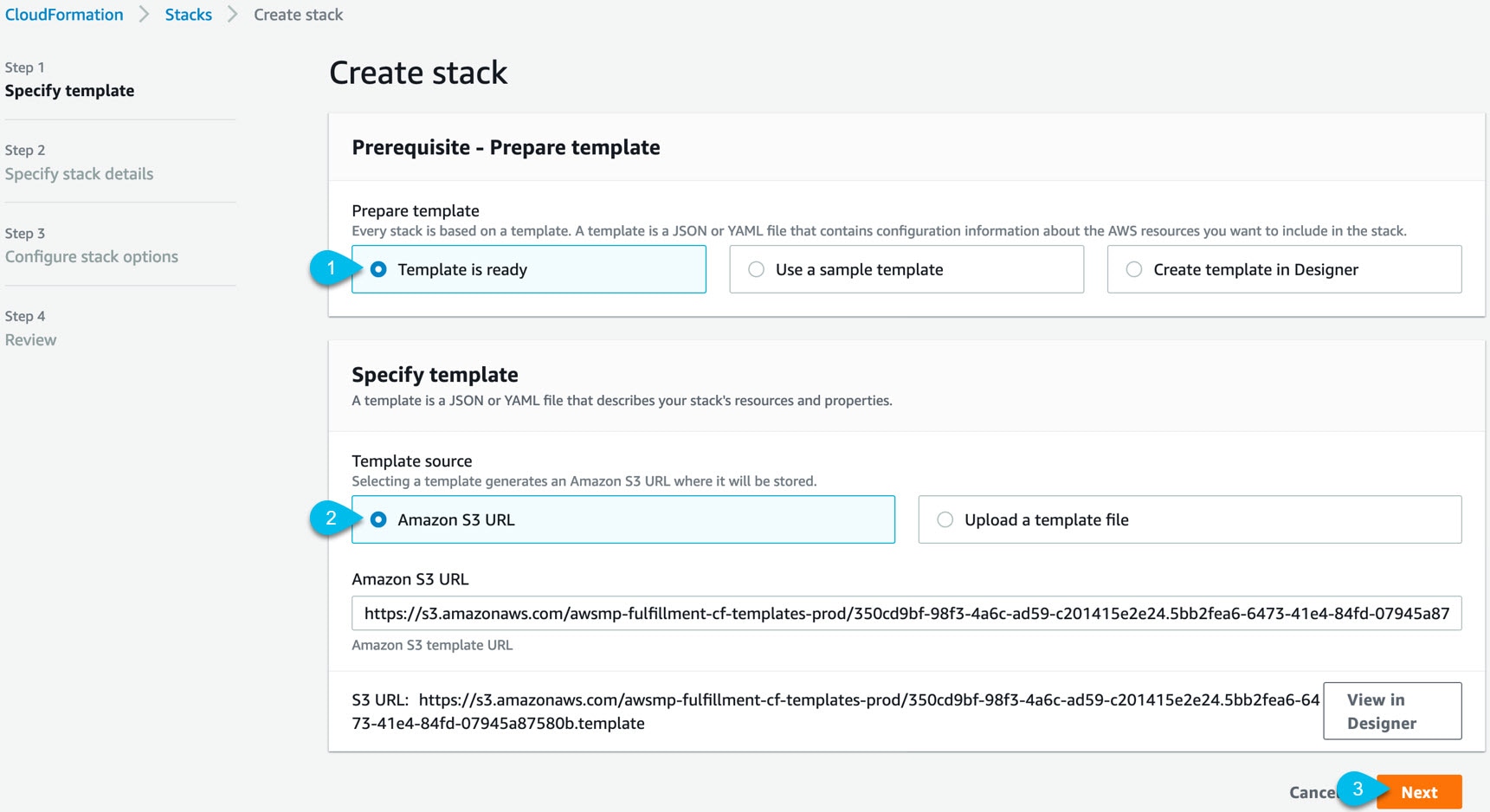
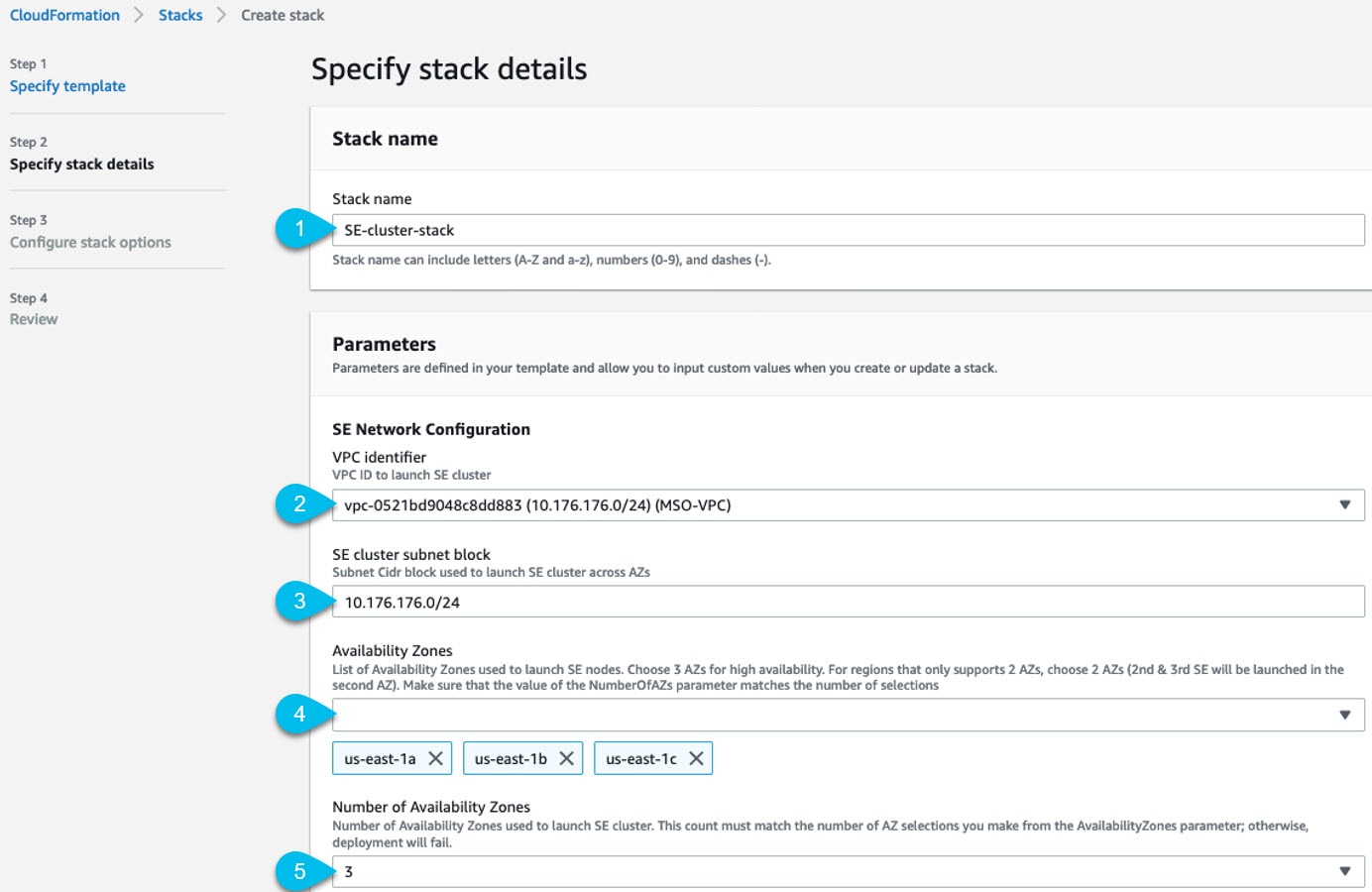
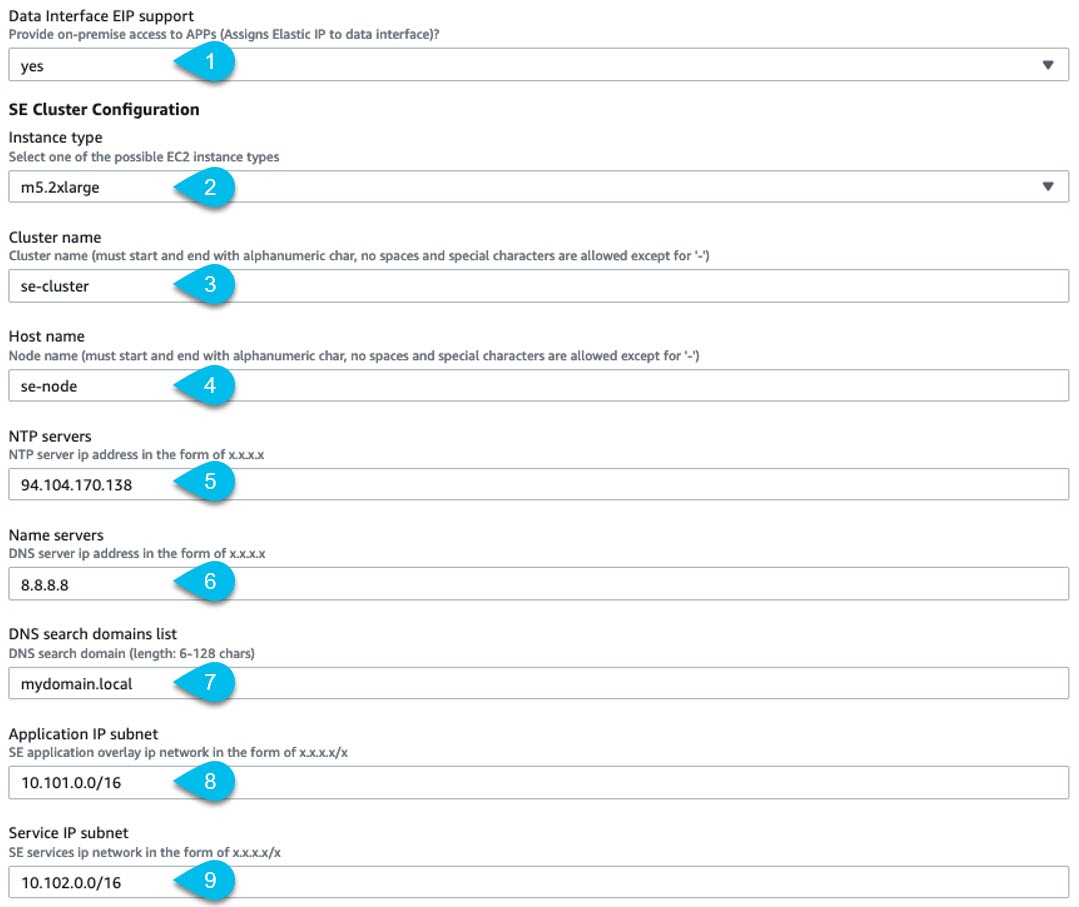
Prerequisites and Guidelines
You must have reviewed and completed the general prerequisites described in the Deployment Overview.
In addition, the following apply when deploying in the Amazon Web Services (AWS):
-
You must have appropriate access privileges for your AWS account.
You must be able to launch multiple instances of Elastic Compute Cloud (
m5.2xlarge) to host the Application Services Engine cluster. -
At least 6 AWS Elastic IP addresses.
A typical Application Services Engine deployment in AWS requires 6 AWS Elastic IP addresses as shown in the following figure:
Figure 1. Elastic IPs 
-
Detailed information about AWS configuration is outside the scope of this document, but in short, to create a VPC:
-
In your AWS console, navigate to Computer > EC2.
-
In the EC2 Dashboard, click and note how many Elastic IPs are already being used.
-
In the EC2 Dashboard, click Limits and note the maximum number of EC2-VPC Elastic IPs allowed.
Subtract the number of IPs already being used from the limit to get. Then if necessary, click Request limit increase to request additional Elastic IPs.
-
-
You must create a VPC (Virtual Private Cloud).
A VPC is an isolated portion of the AWS cloud for AWS objects, such as Amazon EC2 instances. Detailed information about AWS configuration is outside the scope of this document, but in short, to create a VPC:
-
In your AWS console, navigate to Networking & Content Delivery Tools > VPC.
-
In the VPC Dashboard, click Your VPCs and choose Create VPC. Then provide the Name Tag and IPv4 CIDR block.
The CIDR block is a range of IPv4 addresses for your VPC and must be in the
/16to/28range. For example,10.9.0.0/16.
-
-
You must create an Internet Gateway and attach it to the VPC.
Internet Gateway is a virtual router that allows a VPC to connect to the Internet. Detailed information about AWS configuration is outside the scope of this document, but in short, to create an Internet Gateway:
-
In the VPC Dashboard, click Internet Gateways and choose Create internet gateway. Then provide the Name Tag.
-
In the Internet Gateways screen, select the Internet Gateway you created, then choose . Finally, from the Available VPCs dropdown, select the VPC you created and click Attach internet gateway.
-
-
You must create a routes table.
Routes table is used for connecting the subnets within your VPC and Internet Gateway to your Application Services Engine cluster. Detailed information about AWS configuration is outside the scope of this document, but in short, to create a routes table:
-
In the VPC Dashboard, click Route Tables, choose the Routes tab, and click Edit routes.
-
In the Edit routes screen, click Add route and create a
0.0.0.0/0destination. From the Target dropdown, selectInternet Gatewayand choose the gateway you created. Finally, click Save routes.
-
-
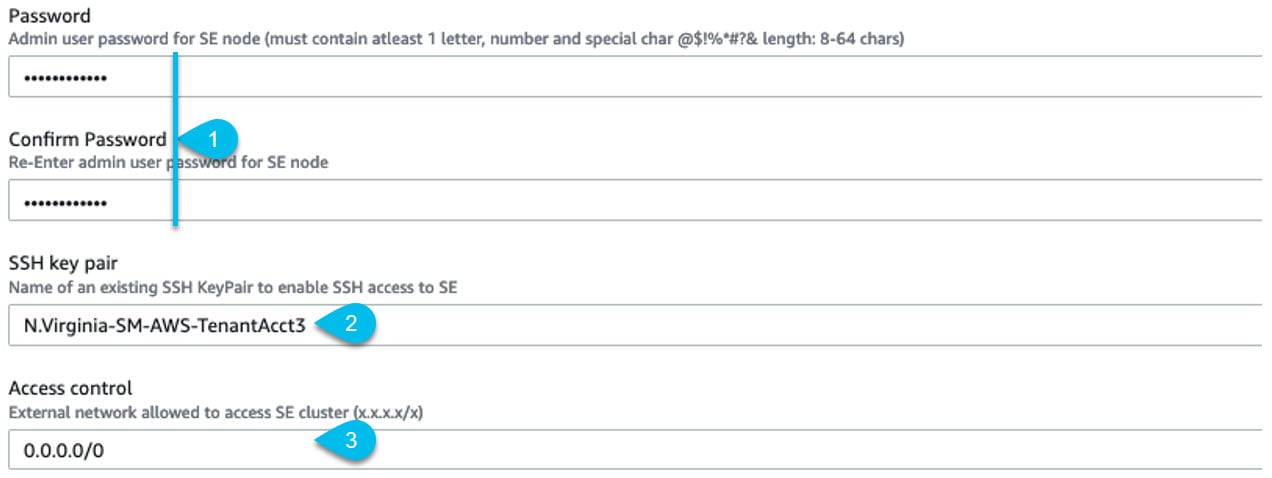
You must also create a key pair.
A key pair consists of a private key and a public key, which are used as security credentials to verify your identity when connecting to an EC2 instance. To create a key pair:
-
Navigate to .
-
In the EC2 Dashboard, click . Then click Create Key Pairs.
-
Provide a name for your key pair, select the pem file format, and click Create key pair.
This will download the
.pemprivate key file to your system. Move the file to a safe location, you will need to use it the first time you log in to an EC2 instance's console.
By default only PEM-based login is enabled for each node. If you'd like to be able to SSH into the nodes using a password, you will need to explicitly enable password-based logins. You can do that by logging into each node separately using the PEM file the first time, then executing the following command:
# acidiag login prompt enable -

 Feedback
Feedback