About Cisco ACI with VMware vRealize
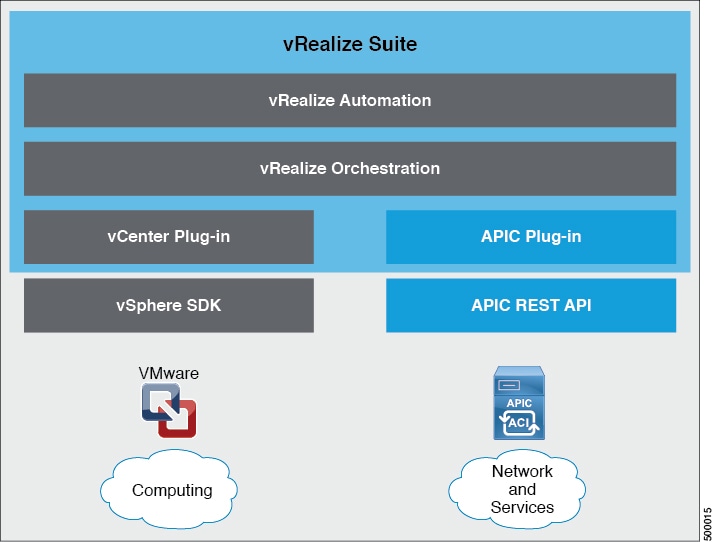
Cisco Application Centric Infrastructure (ACI), in addition to integrating with VMware vCenter, integrates with VMware's products vRealize Automation (vRA) and vRealize Orchestrator (vRO). vRA and vRO are parts of the VMware vRealize Suite for building and managing multivendor hybrid cloud environments.
Beginning with Cisco APIC Release 3.1(1), vRA and vRO support Cisco Application Centric Infrastructure (ACI) Virtual Edge (Cisco ACI Virtual Edge) in addition to VMware DVS.
This chapter discusses about vRealize Automation, Release 7.x. For details about Cisco ACI and VMware vRealize Automation, Release 8.x integration, see the Cisco ACI vRealize 8 Plug-in Guide.
 Note |
Beginning with Cisco Application Policy Infrastructure Controller (APIC) Release 5.0(1), Cisco Application Virtual Switch (AVS) is no longer supported. If you use Cisco AVS and upgrade to Cisco APIC Release 5.0(1), in case of issues, the fabric will not be supported. Also, a fault will be raised for the Cisco AVS domain. If you use Cisco AVS, we recommend that you migrate to Cisco ACI Virtual Edge. See the Cisco ACI Virtual Edge Installation Guide on Cisco.com. |
 Note |
In the Cisco APIC GUI, Cisco ACI Virtual Edge is indicated with the term AVE. |
Cisco ACI with VMware vRealize Solution Overview
vRA integration is delivered through a set of service blueprints imported into vRA. The service blueprints leverage the vRO Application Policy Infrastructure Controller (APIC) workflows, providing a set of catalog items in a self-service portal that allows Tenants to build, manage, and remove networking components. Multi-machine with ACI workflows achieve following functionalities:
-
Auto-create Tenant Endpoint Groups (EPGs)
-
Required policies in APIC
-
Create VMs and portgroups in vCenter
-
Auto-place the VMs is respective port groups
-
Created by APIC
-
Create security policy with access lists
-
Configure L4-L7 services, and provide external connectivity
This consumption model allows users to deploy single and multi-tier application workloads in single click with pre-defined as well as customizable compute and network policies. Catalog items are published by infrastructure administrators, whereby granular entitlements can be added or removed on a per-tenant basis.
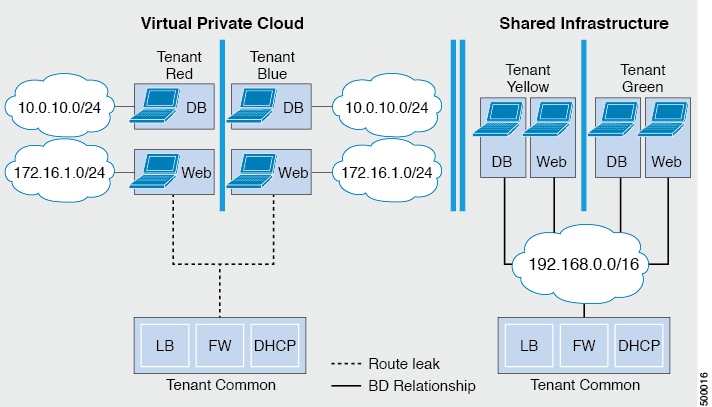
The integration offers two modes of networking:
|
Mode |
Description |
|---|---|
|
Shared |
Shared mode is for Tenants who do not have a preference for what IP address space they use and a shared address space with shared context (VRF) is used across tenants. Isolation is provided using ACI Endpoint Groups (EPGs) and connectivity among EPGs are enabled using a white listing method. |
|
Virtual Private Cloud (VPC) |
VPC mode is a bring your own address space architecture, where network connectivity is isolated via a unique context (VRF) per tenant and external connectivity is provided via a common shared L3 out. |
Physical and Logical Topology
This section shows the logical model of the vRealize ACI Integration and comparison between a Shared Services Plan and Virtual Private Cloud Plan.
For details, see the Cisco APIC Basic Configuration Guide.
About the Mapping of ACI Constructs in VMware vRealize
This table shows the mapping between the features of Cisco ACI policy and vRealize policy
|
Cisco ACI |
VMware vRealize |
|---|---|
|
Tenant |
Tenant |
|
EPGs |
Networks |
|
Layer 3 external connectivity |
External routed network |
|
Contract |
Security policy |
|
Filter |
Rule entry list |
|
L4-L7 service device |
Shared load balancer or firewall |
This list provides details regarding the features:
-
Tenant—Tenants can be employees within an organization, business units, application owners, or applications. Or if you are a service provider, they can be hosting customers (individuals or organizations that pay you to provide IT services).
-
Networks—In Cisco ACI, the term “network” refers to EPGs, which are used to provide a new model for mapping applications to the network. Rather than using forwarding constructs, such as addresses or VLANs, to apply connectivity and policy, EPGs use a grouping of application endpoints. EPGs are mapped to networks in the vRealize portal. The isolated networks act as containers for collections of applications, or of application components and tiers, that can be used to apply forwarding and policy logic. They allow the separation of network policy, security, and forwarding from addressing and instead apply these to logical application boundaries. When a network is created in vRealize, in the back end it is created as a port group in vCenter. A vRealize tenant can use vCenter to manage the computing resources and can attach the virtual machine to the appropriate network.
-
Layer 3 external connectivity—The Cisco ACI fabric connects to the outside through Layer 3 external networks. These constructs are also available for vRealize tenants to access other services within the data center, across the data center, or on the internet.
-
Security policy—Cisco ACI is built on a highly secure model, in which traffic between EPGs (isolated networks) is denied, unless explicitly allowed by policy contracts. A Cisco ACI contract is mapped to a security policy in the vRealize portal. The security policy describes which networks (EPGs) will provide and consume a service. The security policy contains one or more rule entry lists (filters), stateless firewall rules that describe a set of Layer 4 TCP or User Datagram Protocol (UDP) port numbers that define the communication between the various applications.
-
Shared load balancer and firewall—Cisco ACI treats services as an integral part of an application. Any services that are required are managed as a service graph that is instantiated on the Application Policy Infrastructure Controller (APIC) . Users define the service for the application, and service graphs identify the set of network and service functions that are needed by the application. Cisco ACI has an open ecosystem of L4-7 service vendors whose services integrate natively with Cisco ACI. This integration is achieved through device packages written and owned by the vendors. The APIC manages the network services and inserts the services according to the Cisco ACI policy model. For vRealize, Cisco ACI offers F5 and Citrix load balancers and Cisco ASA firewalls, both in virtual and physical form factors, which are connected to the Cisco ACI fabric and shared across the various vRealize tenants. After the device has been integrated into Cisco ACI, the vRealize administrator can choose to add the device as a premium service and upsell the plan. The vRealize administrator manages the virtual IP address range for the shared device, to simplify the vRealize tenant’s workflow.
-
VPC plan—In a VPC plan, vRealize tenants can define their own address spaces, bring a DHCP server, and map their address spaces to networks. A VPC tenant can also be offered services, such as load balancing, from the shared service plan. In this scenario, a device would have multiple virtual NICs (vNICs). One vNIC would connect to the private address space, and another would connect to the shared service infrastructure. The vNIC that connects to the shared service infrastructure would have an address assigned by the infrastructure and would also consume a shared load balancer owned by the infrastructure.
Event Broker VM Customization
vRealize Automation Event Broker is a workflow subscription service for vRealize Automation to call workflows from the vRealize Orchestrator under predefined conditions the user sets. It is supported beginning with Cisco APIC 3.0(1).
A deployment of a single or multitier application is automatically subscribed to the Event Broker. Machine operations such as creation or deletion on any machine, configured by the vRA, trigger the Event Broker. This invokes the preconfigured operations to the Cisco APIC defined by the Property Groups associated to a single or multitier application.
To add the Cisco APIC workflow subscription, follow the instructions at Setting Up the VMware vRealize Automation Appliance for ACI. The workflow subscription then will be added automatically.









 Feedback
Feedback