Switch Management Security
Management security in any switch in the Cisco MDS 9000 Family provides security to all management access methods, including the command-line interface (CLI) or Simple Network Management Protocol (SNMP).
This section includes the following topics:
CLI Security Options
You can access the CLI using the console (serial connection), Telnet, or Secure Shell (SSH).
-
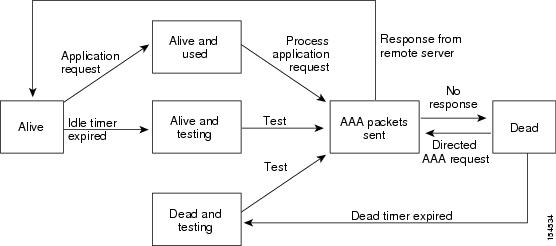
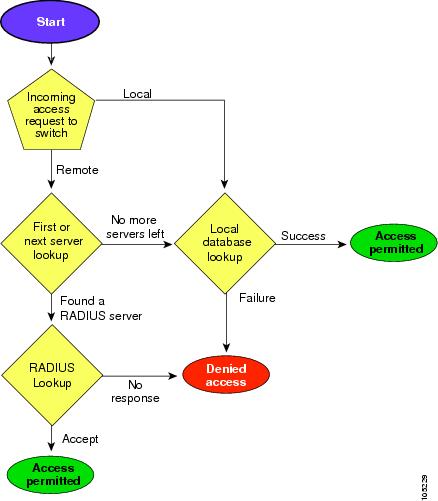
Remote security control
-
Using RADIUS
-
Using TACACS+
-
-
Local security control
See the Local AAA Services
These security features can also be configured for the following scenarios:
-
iSCSI authentication
See the Cisco MDS 9000 Family NX-OS IP Services Configuration Guide and Cisco Fabric Manager IP Services Configuration Guide.
-
Fibre Channel Security Protocol (FC-SP) authentication
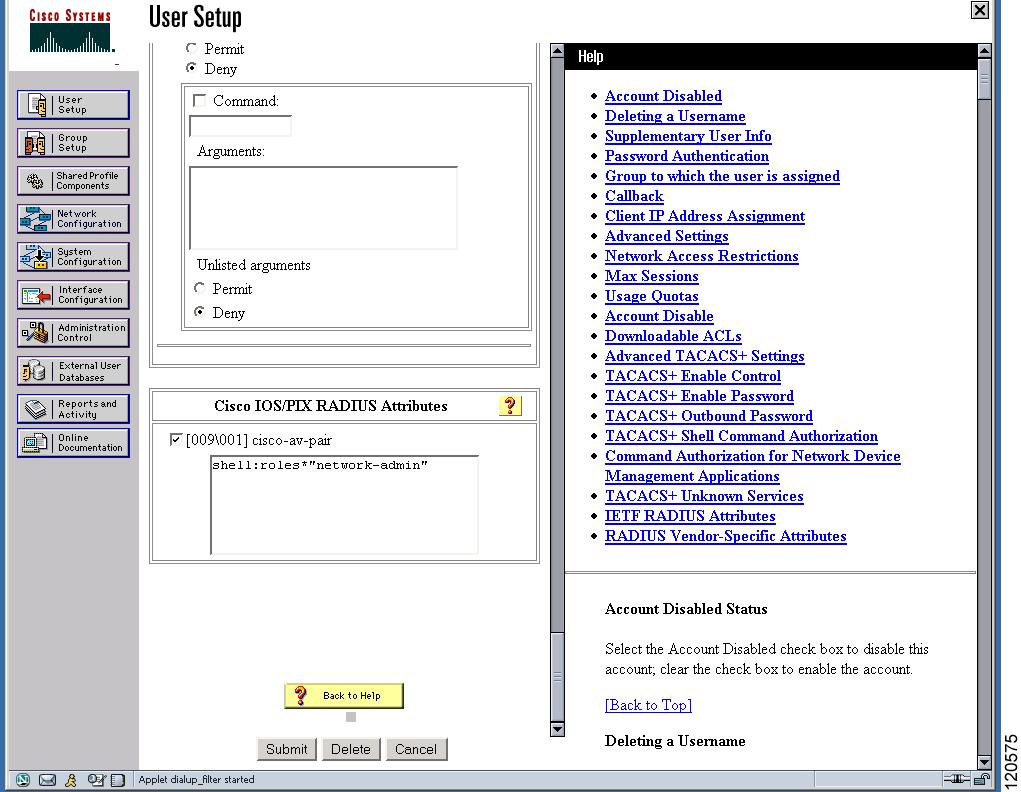
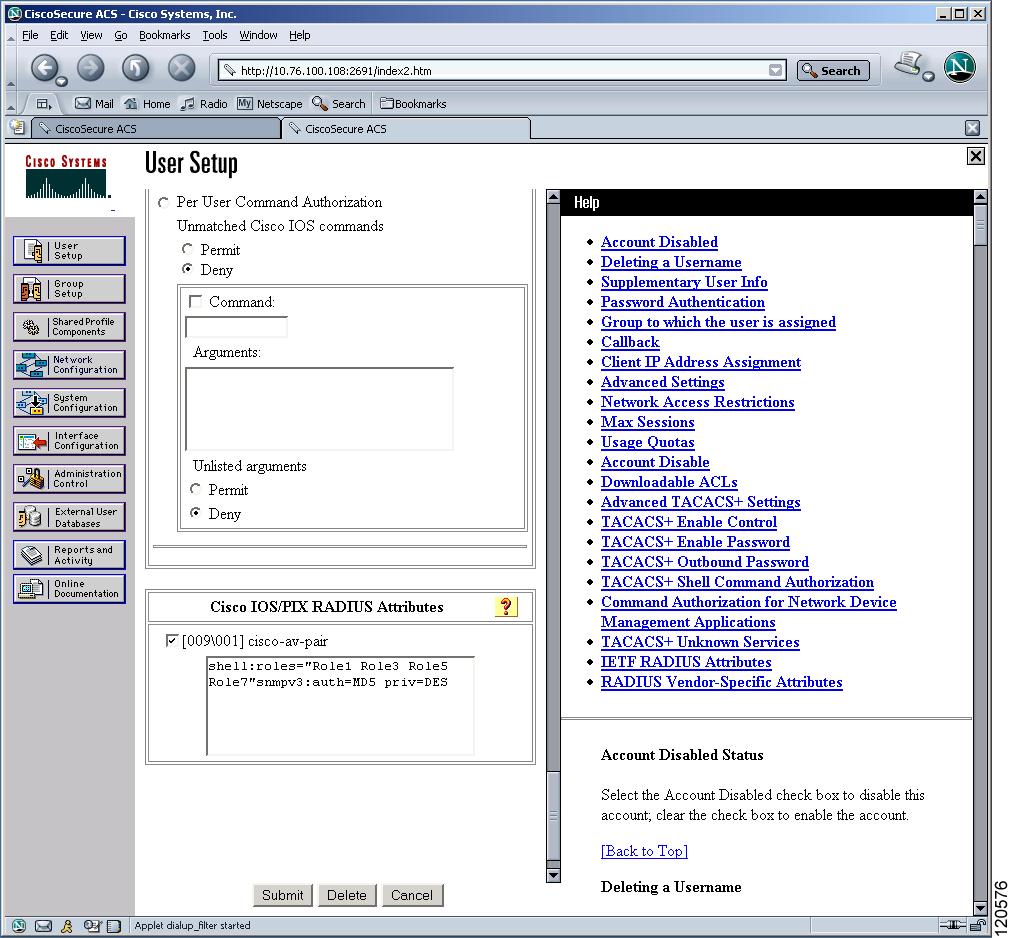
SNMP Security Options
The SNMP agent supports security features for SNMPv1, SNMPv2c, and SNMPv3. Normal SNMP security features apply to all applications that use SNMP (for example, Cisco MDS 9000 Fabric Manager).
SNMP security options also apply to the Fabric Manager and Device Manager.
See the Cisco MDS 9000 NX-OS Family System Management Configuration Guide for more information on the SNMP security options.
Refer to the Cisco Fabric Manager Fundamentals Configuration Guide for information on Fabric Manager and Device Manager.




 Feedback
Feedback