Prerequisites and Guidelines
Before you proceed with deploying the Nexus Dashboard cluster, you must:
-
Review and complete the general and service-specific prerequisites described in Prerequisites: Nexus Dashboard.
-
Review and complete any additional prerequisites that is described in the Release Notes for the services you plan to deploy.
You can find the service-specific documents at the following links:
-
Ensure you are using the following hardware and the servers are racked and connected as described in Cisco Nexus Dashboard Hardware Setup Guide specific to the model of server you have.
The physical appliance form factor is supported on the UCS-C220-M5 (
SE-NODE-G2) and UCS-C225-M6 (ND-NODE-L4) original Cisco Nexus Dashboard platform hardware only.
Note
A known issue exists if you are performing a fresh virtual media installation of the 3.1.1k software on a cluster with UCS-C225-M6 (ND-NODE-L4) nodes and ACI sites, where onboarding the site to NDI or NDO will fail. The workaround for this issue is to perform a fresh installation of the 3.1.1l version of the software instead. Note that upgrading from release 3.1.1k to 3.1.1l will not resolve the issue; you must perform a fresh installation of the 3.1.1l software to resolve the issue.
The following table lists the PIDs and specifications of the physical appliance servers:
Table 1. Supported UCS-C220-M5 Hardware Process ID
Hardware
SE-NODE-G2=
-
Cisco UCS C220 M5 Chassis
-
2x 10-core 2.2-GHz Intel Xeon Silver CPU
-
256 GB of RAM
-
4x 2.4-TB HDDs
400-GB SSD
1.2-TB NVME drive
-
Cisco UCS Virtual Interface Card 1455 (4x25G Ports)
-
1050-W power supply
SE-CL-L3
A cluster of 3x SE-NODE-G2=appliances.Table 2. Supported UCS-C225-M6 Hardware Process ID
Hardware
ND-NODE-L4=
-
Cisco UCS C225 M6 Chassis
-
2.8-GHz AMD CPU
-
256 GB of RAM
-
4x 2.4-TB HDDs
960-GB SSD
1.6-TB NVME drive
-
Intel X710T2LG 2x10 GbE (Copper)
-
One of the following:
-
Intel E810XXVDA2 2x25/10 GbE (Fiber Optic)
-
Cisco UCS Virtual Interface Card 1455 (4x25G Ports)
-
-
1050-W power supply
ND-CLUSTER-L4
A cluster of 3x ND-NODE-L4=appliances.
Note
The above hardware supports Cisco Nexus Dashboard software only. If any other operating system is installed, the node can no longer be used as a Cisco Nexus Dashboard node.
-
-
Ensure that you are running a supported version of Cisco Integrated Management Controller (CIMC).
The minimum that is supported and recommended versions of CIMC are listed in the "Compatibility" section of the Release Notes for your Cisco Nexus Dashboard release.
-
Ensure that you have configured an IP address for the server's CIMC.
To configure a CIMC IP address:
-
Power on the server.
After the hardware diagnostic is complete, you will be prompted with different options controlled by the function (Fn) keys.
-
Press the F8 key to enter the Cisco IMC configuration Utility.
-
Provide the following information:
-
Set NIC mode to
Dedicated. -
Choose between the IPv4 and IPv6 IP modes.
You can choose to enable or disable DHCP. If you disable DHCP, provide the static IP address, subnet, and gateway information.
-
Ensure that NIC Redundancy is set to
None. -
Press F1 for more options such as hostname, DNS, default user passwords, port properties, and reset port profiles.
-
-
Press F10 to save the configuration and then restart the server.
-
-
Ensure that Serial over LAN (SoL) is enabled in CIMC.
SoL is required for the
connect hostcommand, which you use to connect to the node to provide basic configuration information. To use the SoL, you must first enable it on your CIMC. SSH into the node using the CIMC IP address and enter the sign-in credentials. Run the following commands:Server# scope sol Server /sol # set enabled yes Server /sol *# set baud-rate 115200 Server /sol *# commit Server /sol *# Server /sol # show C220-WZP23150D4C# scope sol C220-WZP23150D4C /sol # show Enabled Baud Rate(bps) Com Port SOL SSH Port ------- --------------- -------- ------------- yes 115200 com0 2400 -
Ensure that all nodes are running the same release version image.
-
If your Cisco Nexus Dashboard hardware came with a different release image than the one you want to deploy, we recommend deploying the cluster with the existing image first and then upgrading it to the needed release.
For example, if the hardware you received came with Release 2.3.2 image pre-installed, but you want to deploy Release 3.1.1 instead, we recommend:
-
First, bring up the Release 2.3.2 cluster, as described in the deployment guide for that release.
-
Then upgrade to Release 3.1.1, as described in Upgrading Existing ND Cluster to This Release.

Note
For brand new deployments, you can also choose to simply re-image the nodes with the latest version of the Cisco Nexus Dashboard (for example, if the hardware came with an image which does not support a direct upgrade to this release through the GUI workflow) before returning to this document for deploying the cluster. This process is described in the "Re-Imaging Nodes" section of the Troubleshooting article for this release.
-
-
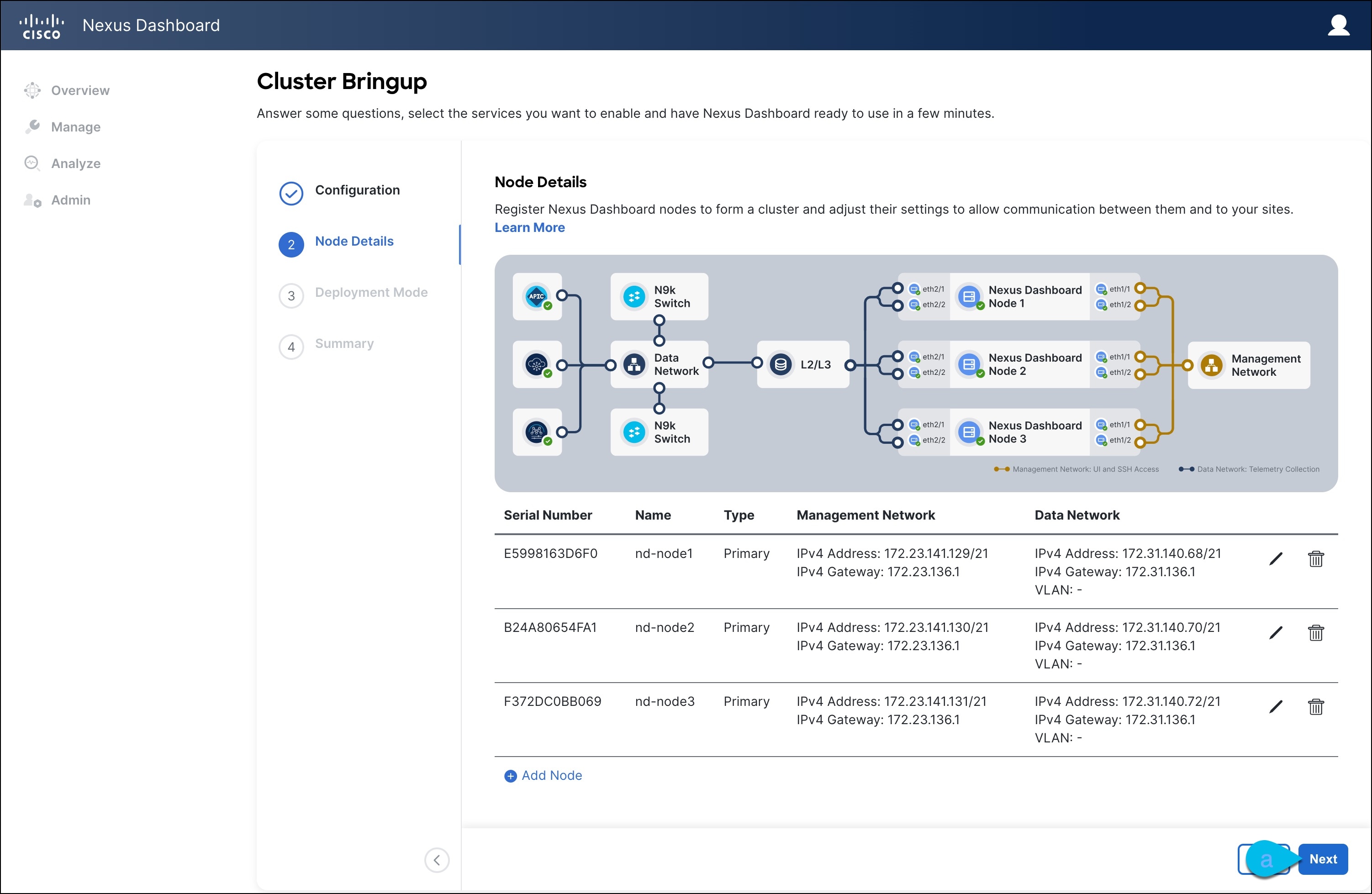
You must have at least a 3-node cluster. Extra secondary nodes can be added for horizontal scaling if required by the enter and number of services you deploy. For the maximum number of
secondaryandstandbynodes in a single cluster, see the Release Notes for your release.



 Feedback
Feedback