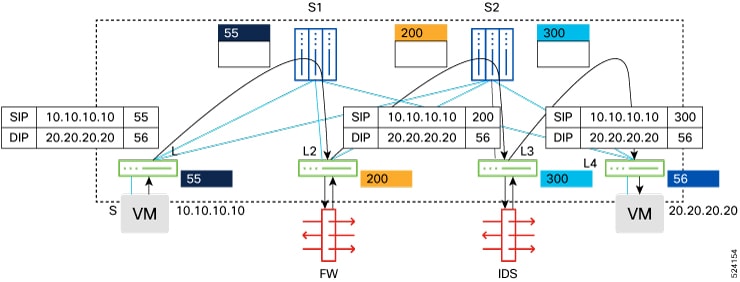
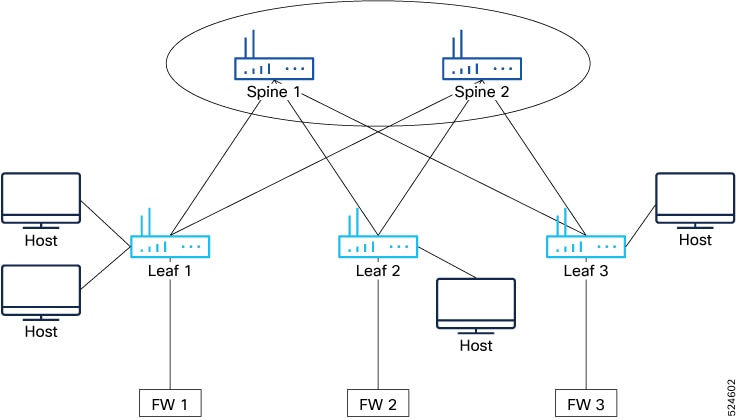
You must first create a service function, which is defined with one or more endpoints with their specific attributes. Service
endpoints are the service appliances such as firewall, IPS, and so on, that are available in the network to which traffic
needs to be redirected. You can also define probes to monitor the health of the service endpoints. ePBR also supports load
balancing along with service-chaining. ePBR allows you to configure multiple service endpoints as a part of a specific service
function and would load-balance traffic among these endpoints, always ensuring that the two legs of the same traffic flow
are using the same service endpoint. This is required when the different service endpoints defined for a given service function
are not clustered and hence do not share connection states between them.
You must specify the VRF context for the service as the context in which the service endpoints are reachable.
After creating one (or more) ePBR services, you must create an ePBR service-chain. The ePBR service-chain allows you to define
the service function (or the chain of service functions) through which traffic should be redirected along with the order in
which this needs to be done.
Services used in a chain are identified by a sequence number. In NXOS 10.5(1)F, only a single service function may be specified
inside a service-chain, thereby supporting only redirection and load-balancing capabilities to a single service functions
before traffic is permitted to its destination.
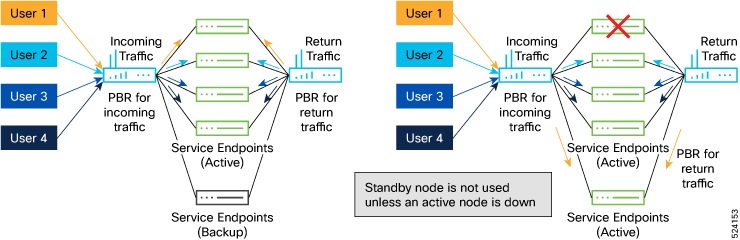
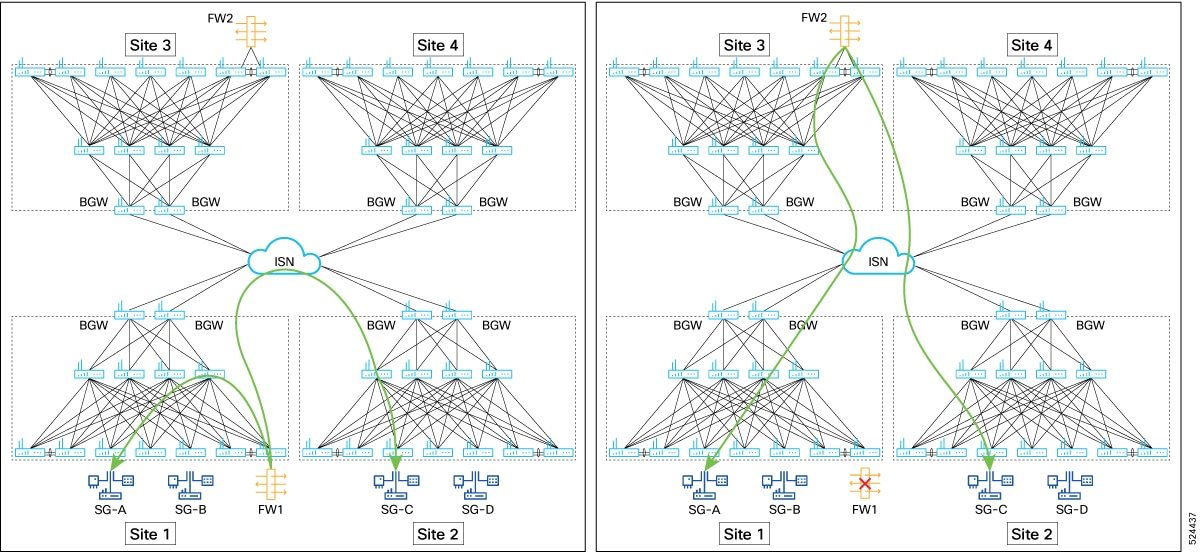
In every service sequence, you can define the fail-action method such as drop, forward, and bypass indicating the action that
needs to be taken in the event of failures of all endpoints in the service. If no fail-action is configured, the default behavior
is to drop the traffic when the service is considered as failed.
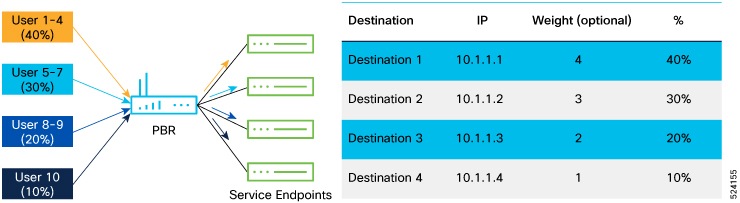
The ePBR service-chain also allows you to specify the manner in which traffic needs to be load-balanced amongst the endpoints
inside a service.
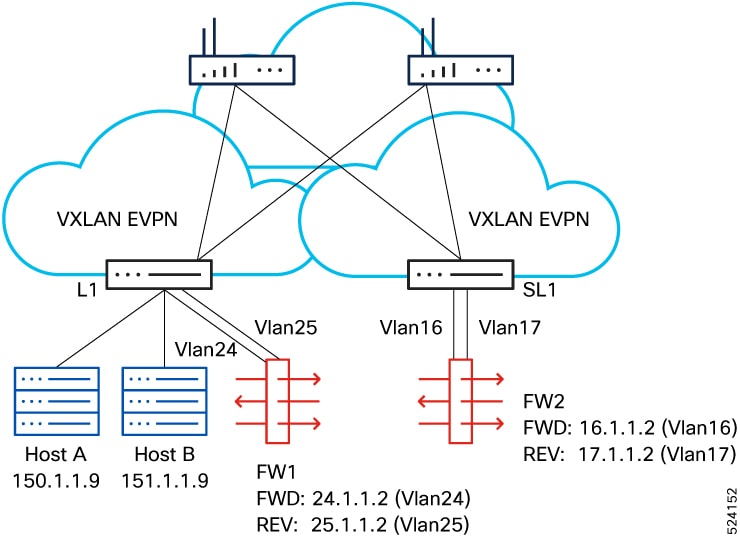
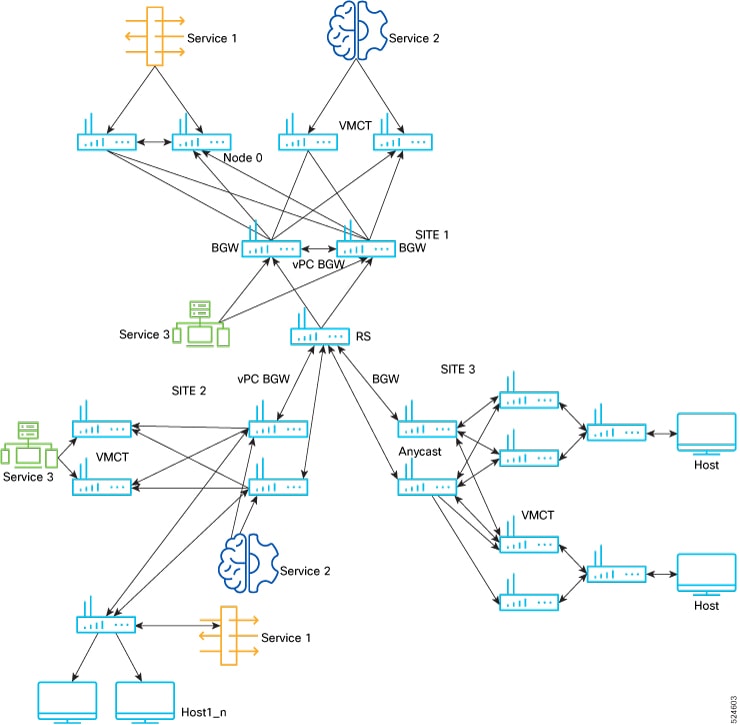
Beginning with Cisco NX-OS Release 10.5(2)F, ePBR multi-node service-chains are supported with Group Policy Options. A maximum
of 5 service functions (nodes) can be configured in a service chain. Multi node service chain can contain firewall, load balancer,
NAT, IPS and other devices.
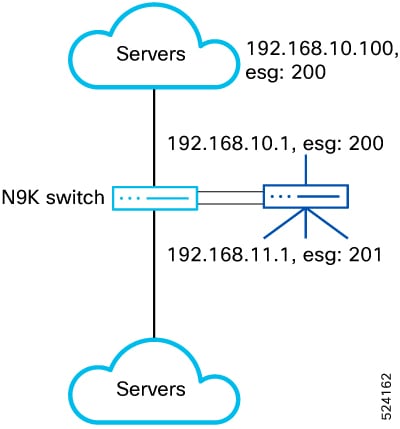
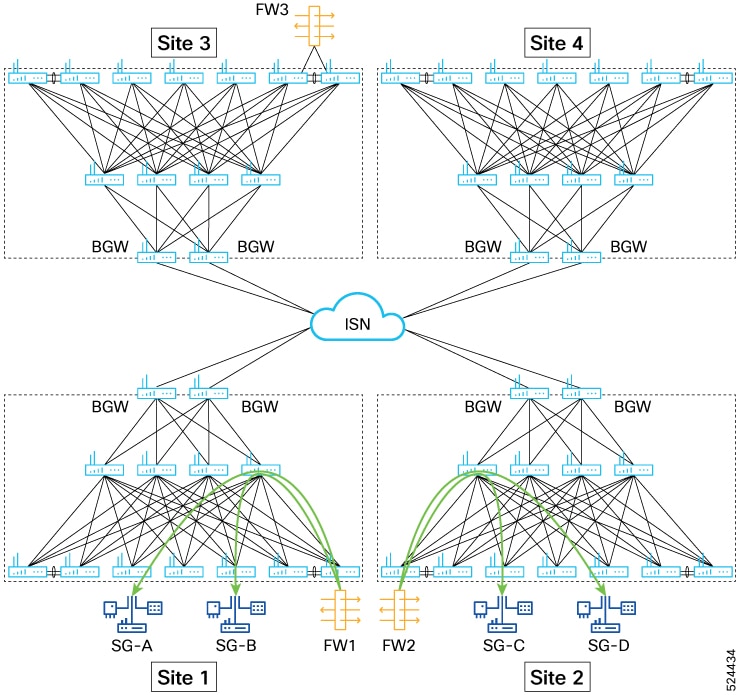
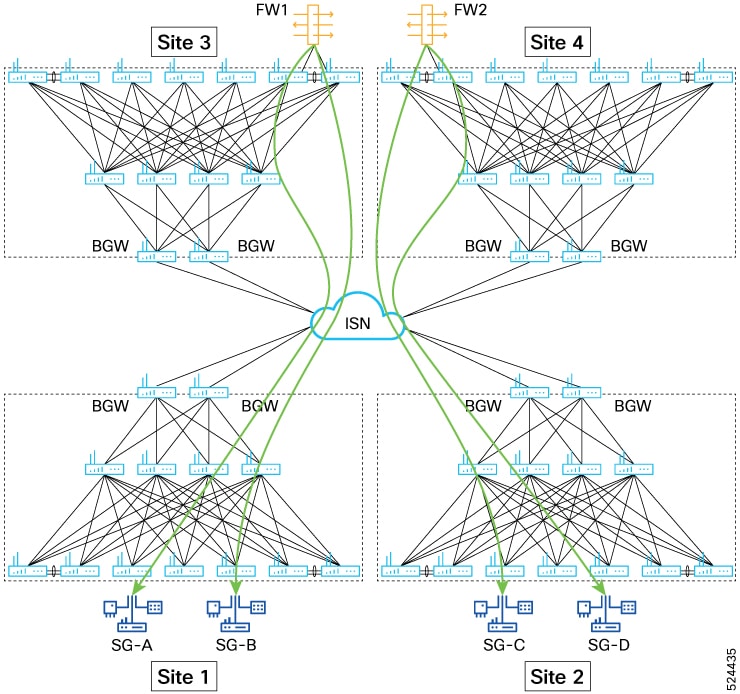
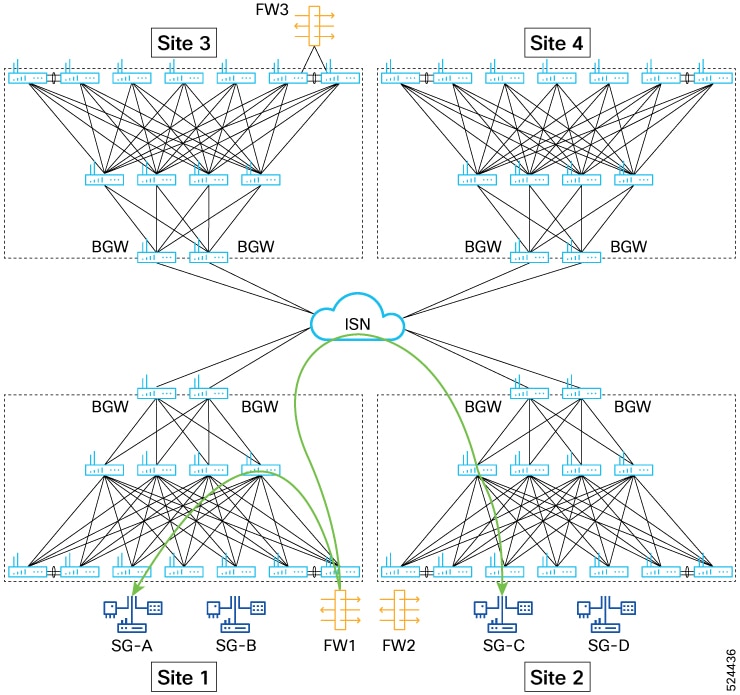
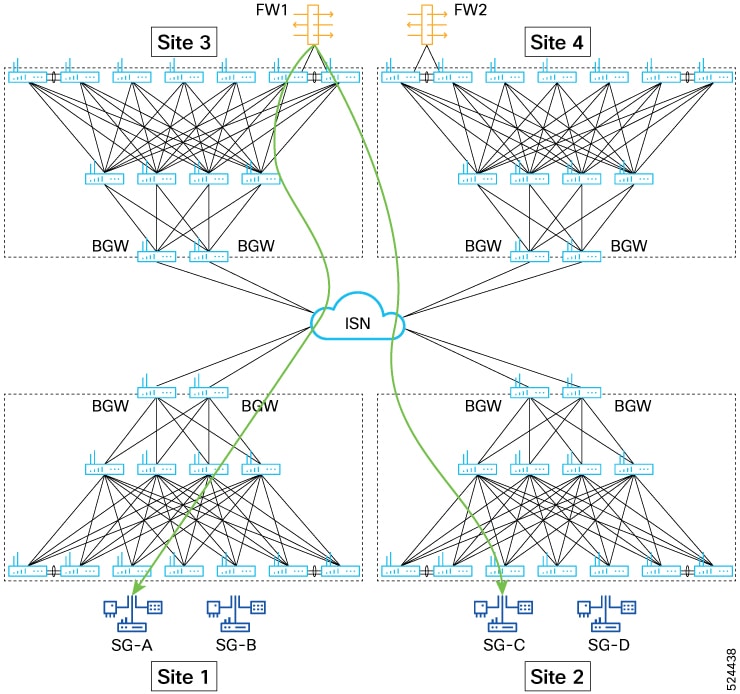
Beginning with Cisco NX-OS Release 10.5(2)F, sources and destinations for the contracts using ePBR single node or multi node
service-chains may be distributed across multiple sites using VXLAN Group Policy Options.
Beginning with Cisco NX-OS Release 10.5(2)F,ePBR multi-node service-chains and multi-site features are supported with sources
and destinations in different VRF contexts. Service devices can belong to source VRF, destination VRF, or any other VRF.
 Feedback
Feedback