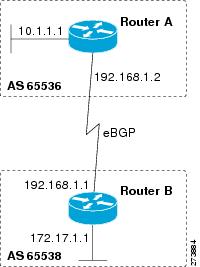
Prior to January 2009, BGP autonomous system numbers that were allocated to companies were 2-octet numbers in the range from
1 to 65535 as described in RFC 4271,
A Border Gateway Protocol 4 (BGP-4) . Due to increased demand for autonomous system numbers, the Internet Assigned Number Authority (IANA) will start in January
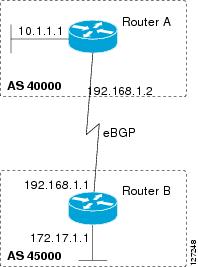
2009 to allocate four-octet autonomous system numbers in the range from 65536 to 4294967295. RFC 5396,
Textual Representation of Autonomous System (AS) Numbers , documents three methods of representing autonomous system numbers. Cisco has implemented the following two methods:
-
Asplain--Decimal value notation where both 2-byte and 4-byte autonomous system numbers are represented by their decimal value.
For example, 65526 is a 2-byte autonomous system number and 234567 is a 4-byte autonomous system number.
-
Asdot--Autonomous system dot notation where 2-byte autonomous system numbers are represented by their decimal value and 4-byte
autonomous system numbers are represented by a dot notation. For example, 65526 is a 2-byte autonomous system number and 1.169031
is a 4-byte autonomous system number (this is dot notation for the 234567 decimal number).
For details about the third method of representing autonomous system numbers, see RFC 5396.
Asdot Only Autonomous System Number Formatting
In Cisco IOS Release 12.0(32)S12, 12.4(24)T, and later releases, the 4-octet (4-byte) autonomous system numbers are entered
and displayed only in asdot notation, for example, 1.10 or 45000.64000. When using regular expressions to match 4-byte autonomous
system numbers the asdot format includes a period which is a special character in regular expressions. A backslash must be
entered before the period (for example, 1\.14) to ensure the regular expression match does not fail. The table below shows
the format in which 2-byte and 4-byte autonomous system numbers are configured, matched in regular expressions, and displayed
in
show command output in Cisco IOS images where only asdot formatting is available.
Table 1. Asdot Only 4-Byte Autonomous System Number Format
|
Format
|
Configuration Format
|
Show Command Output and Regular Expression Match Format
|
|
asdot
|
2-byte: 1 to 65535 4-byte: 1.0 to 65535.65535
|
2-byte: 1 to 65535 4-byte: 1.0 to 65535.65535
|
Asplain as Default Autonomous System Number Formatting
In Cisco IOS Release 12.0(32)SY8, 12.0(33)S3, 12.2(33)SRE, 12.2(33)XNE, 12.2(33)SXI1, and later releases, the Cisco implementation
of 4-byte autonomous system numbers uses asplain as the default display format for autonomous system numbers, but you can
configure 4-byte autonomous system numbers in both the asplain and asdot format. In addition, the default format for matching
4-byte autonomous system numbers in regular expressions is asplain, so you must ensure that any regular expressions to match
4-byte autonomous system numbers are written in the asplain format. If you want to change the default
show command output to display 4-byte autonomous system numbers in the asdot format, use the
bgp
asnotation
dot command under router configuration mode. When the asdot format is enabled as the default, any regular expressions to match
4-byte autonomous system numbers must be written using the asdot format, or the regular expression match will fail. The tables
below show that although you can configure 4-byte autonomous system numbers in either asplain or asdot format, only one format
is used to display
show command output and control 4-byte autonomous system number matching for regular expressions, and the default is asplain format.
To display 4-byte autonomous system numbers in
show command output and to control matching for regular expressions in the asdot format, you must configure the
bgp
asnotation
dot command. After enabling the
bgp
asnotation
dot command, a hard reset must be initiated for all BGP sessions by entering the
clear
ip
bgp
* command.

Note |
If you are upgrading to an image that supports 4-byte autonomous system numbers, you can still use 2-byte autonomous system
numbers. The
show command output and regular expression match are not changed and remain in asplain (decimal value) format for 2-byte autonomous
system numbers regardless of the format configured for 4-byte autonomous system numbers.
|
Table 2. Default Asplain 4-Byte Autonomous System Number Format
|
Format
|
Configuration Format
|
Show Command Output and Regular Expression Match Format
|
|
asplain
|
2-byte: 1 to 65535 4-byte: 65536 to 4294967295
|
2-byte: 1 to 65535 4-byte: 65536 to 4294967295
|
|
asdot
|
2-byte: 1 to 65535 4-byte: 1.0 to 65535.65535
|
2-byte: 1 to 65535 4-byte: 65536 to 4294967295
|
Table 3. Asdot 4-Byte Autonomous System Number Format
|
Format
|
Configuration Format
|
Show Command Output and Regular Expression Match Format
|
|
asplain
|
2-byte: 1 to 65535 4-byte: 65536 to 4294967295
|
2-byte: 1 to 65535 4-byte: 1.0 to 65535.65535
|
|
asdot
|
2-byte: 1 to 65535 4-byte: 1.0 to 65535.65535
|
2-byte: 1 to 65535 4-byte: 1.0 to 65535.65535
|
Reserved and Private Autonomous System Numbers
In Cisco IOS Release 12.0(32)S12, 12.0(32)SY8, 12.0(33)S3, 12.2(33)SRE, 12.2(33)XNE, 12.2(33)SXI1, 12.4(24)T, and later releases,
the Cisco implementation of BGP supports RFC 4893. RFC 4893 was developed to allow BGP to support a gradual transition from
2-byte autonomous system numbers to 4-byte autonomous system numbers. A new reserved (private) autonomous system number, 23456,
was created by RFC 4893 and this number cannot be configured as an autonomous system number in the Cisco IOS CLI.
RFC 5398,
Autonomous System (AS) Number Reservation for Documentation Use , describes new reserved autonomous system numbers for documentation purposes. Use of the reserved numbers allow configuration
examples to be accurately documented and avoids conflict with production networks if these configurations are literally copied.
The reserved numbers are documented in the IANA autonomous system number registry. Reserved 2-byte autonomous system numbers
are in the contiguous block, 64496 to 64511 and reserved 4-byte autonomous system numbers are from 65536 to 65551 inclusive.
Private 2-byte autonomous system numbers are still valid in the range from 64512 to 65534 with 65535 being reserved for special
use. Private autonomous system numbers can be used for internal routing domains but must be translated for traffic that is
routed out to the Internet. BGP should not be configured to advertise private autonomous system numbers to external networks.
Cisco IOS software does not remove private autonomous system numbers from routing updates by default. We recommend that ISPs
filter private autonomous system numbers.

Note |
Autonomous system number assignment for public and private networks is governed by the IANA. For information about autonomous-system
numbers, including reserved number assignment, or to apply to register an autonomous system number, see the following URL:
http://www.iana.org/.
|


 Feedback
Feedback