As in IPv4, path MTU discovery in IPv6 allows a host to dynamically discover and adjust to differences in the MTU size of
every link along a given data path. In IPv6, however, fragmentation is handled by the source of a packet when the path MTU
of one link along a given data path is not large enough to accommodate the size of the packets. Having IPv6 hosts handle packet
fragmentation saves IPv6 device processing resources and helps IPv6 networks run more efficiently.

Note |
In IPv6, the minimum link MTU is 1280 octets. We recommend using an MTU value of 1500 octets for IPv6 links.
|
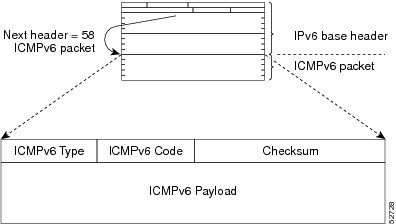
With IPv6 path MTU discovery, a device originating IPv6 traffic has an MTU cache that contains MTU values received in ICMPv6
"toobig" messages. In order to prevent an attacker from filling the MTU cache, the device keeps track of the destinations
to which it has originated (sent) traffic, and only accepts toobig ICMPv6 messages that have an inner destination matching
one of these tracked destinations.
If a malicious device can learn to which destination the device is originating traffic, it could still send a toobig ICMPv6
message to the device for this destination, even if the attacker is not on the path to this destination, and succeeds in forcing
his entry into the MTU cache. The device then starts fragmenting traffic to this destination, which significantly affects
device performance.
Enabling flow-label marking for locally generated traffic can mitigate this attack. Originated packets are marked with a
flow label (which is randomly generated and changed every minute), and toobig messages received are checked against the values
sent. Unless an attacker can snoop traffic, the attacker will not know which flow label to use, and its toobig message will
be dropped.

 Feedback
Feedback