A full-mesh configuration requires a full mesh of tunnel label switched paths (LSPs) between all provider edge (PE) devices
that participate in Virtual Private LAN Services (VPLS). With a full mesh, signaling overhead and packet replication requirements
for each provisioned virtual circuit (VC) on a PE can be high.
You set up a VPLS by first creating a virtual forwarding instance (VFI) on each participating PE device. The VFI specifies
the VPN ID of a VPLS domain, the addresses of other PE devices in the domain, and the type of tunnel signaling and encapsulation
mechanism for each peer PE device.
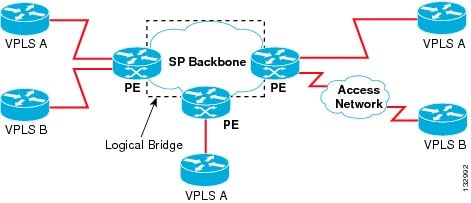
The set of VFIs formed by the interconnection of the emulated VCs is called a VPLS instance; it is the VPLS instance that
forms the logic bridge over a packet switched network. After the VFI has been defined, it needs to be bound to an attachment
circuit to the CE device.
The VPLS instance is assigned a unique VPN ID.
PE devices use the VFI to establish a full-mesh LSP of emulated VCs to all other PE devices in the VPLS instance. PE devices
obtain the membership of a VPLS instance through static configuration using the Cisco IOS CLI.
A full-mesh configuration allows the PE device to maintain a single broadcast domain. When the PE device receives a broadcast,
multicast, or unknown unicast packet on an attachment circuit (AC), it sends the packet out on all other ACs and emulated
circuits to all other CE devices participating in that VPLS instance. The CE devices see the VPLS instance as an emulated
LAN.
To avoid the problem of a packet looping in the provider core, PE devices enforce a “split-horizon” principle for emulated
VCs. In a split horizon, if a packet is received on an emulated VC, it is not forwarded on any other emulated VC.
The packet forwarding decision is made by looking up the Layer 2 VFI of a particular VPLS domain.
A VPLS instance on a particular PE device receives Ethernet frames that enter on specific physical or logical ports and populates
a MAC table similarly to how an Ethernet switch works. The PE device can use the MAC address to switch these frames into the
appropriate LSP for delivery to the another PE device at a remote site.
If the MAC address is not available in the MAC address table, the PE device replicates the Ethernet frame and floods it to
all logical ports associated with that VPLS instance, except the ingress port from which it just entered. The PE device updates
the MAC table as it receives packets on specific ports and removes addresses not used for specific periods.


 Feedback
Feedback