Information About the gRPC Network Operations Interface
gNOI Protocol
gNOI defines a set of gRPC-based microservices for executing operational commands on network devices. The gNMI service defines operations for configuration management, operational state retrieval, and bulk data collection through streaming telemetry. gNOI only allows the adoption of services that a device supports. gNOI supports the OS installation service.
gNOI can be used with or without user authentication. User authentication is disabled by default. Use the gnxi secure-password-auth command to enable user authentication. For information about enabling user authentication through the OpenConfig model, see https://github.com/YangModels/yang/blob/master/vendor/cisco/xe/1751/openconfig-system-management.yang.
The gNOI protocol supports the following operations:
-
Certificate Management
-
Bootstrapping
-
OS Installation Service
-
Factory Reset Service
Certificate Management Service
The Certificate Management Service primarily exports two main RPCs, Install and Rotate, that are used for the installation of new certificates, and the rotation of existing certificates on a device, respectively.
The following RPCs are supported by the Certificate Management Service:
-
Install: Installs a certificate. All certificates are uniquely identified by a certificate ID. The certificate ID is a string.
-
Rotate: Rotates an existing certificate.
-
RevokeCertificates: Revokes one or more certificates.
-
GetCertificates: Queries all certificates.
-
CanGenerateCSR: Queries whether the device can generate a Certificate Signing Request (CSR).
Trustpoints and certificates created through the RPCs mentioned above persist across switchovers and device reboots.
The following is a sample Certificate Management Service definition:
service CertificateManagement {
rpc Install(stream InstallCertificateRequest)
returns (stream InstallCertificateResponse);
rpc Rotate(stream RotateCertificateRequest)
returns (stream RotateCertificateResponse);
rpc RevokeCertificates(RevokeCertificateRequest)
returns (RevokeCertificateResponse);
rpc GetCertificates(GetCertificateRequest)
returns (GetCertificateResponse);
rpc CanGenerateCSR(CanGenerateCSRRequest)
returns (CanGenerateCSRResponse);
}
Install RPC
The Install RPC adds a new certificate to a device by creating a new CSR request. The new certificate is associated with a new certificate ID on the device. If the device has a pre-existing certificate with the given certificate ID, the operation fails.
The Install RPC is a bidirectional streaming RPC. It has an input (InstallCertificateRequest) and an output (IntsallCertificateResponse) both of which are streaming. If the stream is broken, or any steps in the process fail, the device rolls back the changes.
The following is an example of the Install RPC definition and messages:
rpc Install(stream InstallCertificateRequest)
returns (stream InstallCertificateResponse);
// Request messages to install new certificates on the target.
message InstallCertificateRequest {
// Request Messages.
oneof install_request {
GenerateCSRRequest generate_csr = 1;
LoadCertificateRequest load_certificate = 2;
}
}
// Request to generate the CSR.
message GenerateCSRRequest {
// Parameters for creating a CSR.
CSRParams csr_params = 1;
// The certificate id with which this CSR will be associated. The target
// configuration should bind an entity which wants to use a certificate to
// the certificate_id it should use.
string certificate_id = 2;
}
// Parameters to be used when generating a Certificate Signing Request.
message CSRParams {
// The type of certificate which will be associated for this CSR.
CertificateType type = 1;
// Minimum size of the key to be used by the target when generating a
// public/private key pair.
uint32 min_key_size = 2;
// If provided, the target must use the provided key type. If the target
// cannot use the algorithm specified in the key_type, it should cancel the
// stream with an Unimplemented error.
KeyType key_type = 3;
// --- common set of parameters applicable for any type of certificate --- //
string common_name = 4; // e.g "device.corp.google.com"
string country = 5; // e.g "US"
string state = 6; // e.g "CA"
string city = 7; // e.g "Mountain View"
string organization = 8; // e.g "Google"
string organizational_unit = 9; // e.g "Security"
string ip_address = 10;
string email_id = 11;
}
// A certificate.
message Certificate {
// Type of certificate.
CertificateType type = 1;
// Actual certificate.
// The exact encoding depends upon the type of certificate.
// for X509, this should be a PEM encoded Certificate.
bytes certificate = 2;
}
message LoadCertificateRequest {
// The certificate to be Loaded on the target.
Certificate certificate = 1;
// The key pair to be used with the certificate. This is provided in the event
// that the target cannot generate a CSR (and the corresponding public/private
// keys).
KeyPair key_pair = 2;
// Certificate Id of the above certificate. This is to be provided only when
// there is an externally generated key pair.
string certificate_id = 3;
// Optional pool of CA certificates to be used for authenticating the client.
repeated Certificate ca_certificate = 4;
}
// A message representing a pair of public/private keys.
message KeyPair {
bytes private_key = 1;
bytes public_key = 2;
}
// Response Messages from the target for the InstallCertificateRequest.
message InstallCertificateResponse {
// Response messages.
oneof install_response {
GenerateCSRResponse generated_csr = 1;
LoadCertificateResponse load_certificate = 2;
}
}
// GenerateCSRResponse contains the CSR associated with the Certificate ID
// supplied in the GenerateCSRRequest. When a Certificate is subsequently
// installed on the target in the same streaming RPC session, it must be
// associated to that Certificate ID.
//
// An Unimplemented error will be returned if the target cannot generate a CSR
// as per the request. In this case, the caller must generate its own key pair.
message GenerateCSRResponse {
CSR csr = 1;
}
// A Certificate Signing Request.
message CSR {
// Type of certificate.
CertificateType type = 1;
// Bytes representing the CSR.
// The exact encoding depends upon the type of certificate requested.
// for X509: This should be the PEM encoded CSR.
bytes csr = 2;
}
After the target device is up and gNOI is in default state, the controller (a third-party implementation) uses the Install RPC to install a certificate that is signed by a Certificate Authority (CA). The certificate is uniquely identified by a certificate ID. This ID is used as the trustpoint name in the Public Key Infrastructure (PKI) configuration. The installation will fail, if you try to install a certificate that has an existing certificate ID.
The following section describes how a CSR is generated by a device:
-
The device generates a self-signed certificate through the Install RPC. The controller does not require a copy of this certificate because in encrypted mode (or gNMI default state) the controller does not validate the certificate presented by the target device. This is the default state.
-
The controller requests the device to generate a CSR, sends the CSR to the CA, and gets the signed certificate back from the CA.
-
The signed certificate is installed into the device along with the CA certificates used to sign the certificate. The CA certificate is present in the ca_certificates bundle, and is required by the PKI to install the device certificate.
-
The gNMI or the gNOI service restarts using the newly installed certificate that is now in the provisioned state.
Rotate RPC
The Rotate RPC renews an existing certificate; a certificate that is already installed. If a certificate is not already installed, the Rotate RPC fails. A certificate that is not in use can be rotated, but the client cannot test it.
The following is a sample Rotate RPC definition:
rpc Rotate(stream RotateCertificateRequest)
returns (stream RotateCertificateResponse);
// Request messages to rotate existing certificates on the target.
message RotateCertificateRequest {
// Request Messages.
oneof rotate_request {
GenerateCSRRequest generate_csr = 1;
LoadCertificateRequest load_certificate = 2;
FinalizeRequest finalize_rotation = 3;
}
}
// A Finalize message is sent to the target to confirm the Rotation of
// the certificate and that the certificate should not be rolled back when
// the RPC concludes. The certificate must be rolled back if the target returns
// an error after receiving a Finalize message.
message FinalizeRequest {
}
message RotateCertificateResponse {
// Response messages.
oneof rotate_response {
GenerateCSRResponse generated_csr = 1;
LoadCertificateResponse load_certificate = 2;
}
}
The Rotate RPC differs from the Install RPC in the following ways:
-
PKI has to save or cache the old certificate and the CA certificate when installing a new certificate (for the purpose of rollback).
-
The controller creates a new connection to test whether the renewed certificate works, and in case of success, finalizes the certificate rotation.
Revoke RPC
This RPC is used to revoke one or more certificates, each uniquely identified by a certificate ID. Revocation of a certificate results in the corresponding trustpoint to be removed from the Cisco IOS XE configuration. If the corresponding trustpoints are currently in use, or if the trustpoints do not exist, revocation of the certificates may fail.
A RevokeCertificate RPC may have certificates revoked successfully or unsuccessfully. On the target device, revocation is a simple delete operation; the actual revocation with the CA is done by the client. If the client revokes a certificate that is in use, new connections fail, but the existing connections are unaffected.
The following is a sample RevokeCertificate RPC:
// An RPC to revoke specific certificates.
// If a certificate is not present on the target, the request should silently
// succeed. Revoking a certificate should render the existing certificate
// unusable by any endpoints.
rpc RevokeCertificates(RevokeCertificatesRequest)
returns (RevokeCertificatesResponse);
message RevokeCertificatesRequest {
// Certificates to revoke.
repeated string certificate_id = 1;
}
message RevokeCertificatesResponse {
// List of certificates successfully revoked.
repeated string revoked_certificate_id = 1;
// List of errors why certain certificates could not be revoked.
repeated CertificateRevocationError certificate_revocation_error = 2;
}
// An error message indicating why a certificate id could not be revoked.
message CertificateRevocationError {
string certificate_id = 1;
string error_message = 2;
}
GetCertificate RPC
This RPC queries all certificate IDs.
The response to the query contains the following information:
-
Certificate information for all the certificates that are identified by a certificate ID.
-
The list of endpoints, for example, tunnels, daemons, and so on, that use this certificate.

Note
Endpoints are not supported.
 Note |
Responses do not contain the ca_certificate bundle. |
The following is a sample GetCertificate RPC:
// An RPC to get the certificates on the target.
rpc GetCertificates(GetCertificatesRequest) returns (GetCertificatesResponse);
// The request to query all the certificates on the target.
message GetCertificatesRequest {
}
// Response from the target about the certificates that exist on the target what
// what is using them.
message GetCertificatesResponse {
repeated CertificateInfo certificate_info = 1;
}
message CertificateInfo {
string certificate_id = 1;
Certificate certificate = 2;
// List of endpoints using this certificate.
repeated Endpoint endpoints = 3;
// System modification time when the certificate was installed/rotated in
// nanoseconds since epoch.
int64 modification_time = 4;
}
// An endpoint represents an entity on the target which can use a certificate.
message Endpoint {
// Type of endpoint that can use a cert. This list is to be extended based on
// conversation with vendors.
enum Type {
EP_UNSPECIFIED = 0;
EP_IPSEC_TUNNEL = 1;
EP_DAEMON = 2;
}
Type type = 1;
// Human readable identifier for an endpoint.
string endpoint = 2;
}
CanGenerateCSR RPC
This RPC queries whether a device can generate a CSR for a specific key type, certificate type, and key size. The supported key type is Rivest, Shamir, and Adelman (RSA), and the supported certificate type is X.509.
When this RPC request is made for installing a completely new certificate as part of the Install RPC, the device must ensure that the certificate ID is new and no entities on the device are bound to this certificate ID. If any existing certificate matches the certificate ID, this request fails.
When this RPC request is made for rotating an existing certificate as part of the Rotate RPC, the device must ensure that the certificate ID is already available. If certificate rotation proceeds to load the certificate, it must associate the new certificate with the previously created certificate ID.
The following is a sample CanGenerateCSR RPC:
// An RPC to ask a target if it can generate a Certificate.
rpc CanGenerateCSR(CanGenerateCSRRequest) returns (CanGenerateCSRResponse);
// A request to ask the target if it can generate key pairs.
message CanGenerateCSRRequest {
KeyType key_type = 1;
CertificateType certificate_type = 2;
uint32 key_size = 3;
}
// Algorithm to be used for generation the key pair.
enum KeyType {
// 1 - 500, for known types.
// 501 and onwards for private use.
KT_UNKNOWN = 0;
KT_RSA = 1;
}
// Types of certificates.
enum CertificateType {
// 1 - 500 for public use.
// 501 onwards for private use.
CT_UNKNOWN = 0;
CT_X509 = 1;
}
// Response from the target about whether it can generate a CSR with the given
// parameters.
message CanGenerateCSRResponse {
bool can_generate = 4;
}
Mutual Authentication
Mutual authentication is a two-way authentication; two parties authenticate each other at the same time. To enable mutual-authentication, use the gnmi-yang secure-peer-verify-trustpoint command. If this command is not enabled, the authentication service validates the gNMI client against all the existing trustpoints and the contents of the trustpool.
Rotation of the CA certificates for mutual authentication requires the client to present a new bundle to the target device, and the old bundle to be removed. However, the CA certificates reside in a trustpool, and cannot be selectively deleted from the trustpool.
Bootstrapping with Certificate Service
After installing gNOI certificates, bootstrapping is used to configure or operate a target device. When a target device does not have any pre-existing certificates, bootstrapping allows the installing of certificates by using the gNOI Certificate Management Service. After the certificate installation, the device is capable of establishing secure gNOI or gNMI connections. This process assumes a pre-existing secure environment.
To enable gNMI bootstrapping, use the gnxi secure-init command.
 Note |
The gNOI Certificate Management Service must be installed before bootstapping. |
The gNOI Certificate Management Service has two states. These states are supported by both the gNOI service and the gNMI service.
-
Default/Encrypted: gNOI and gNMI on the device use a self-signed (default) certificate that the client does not verify; the certificate does not require authentication. In this state, only the gNOI certificate service is enabled on the target device.
-
Provisioned: gNOI and gNMI on the device use an installed certificate that is verified by the client, and the client presents its certificate, which the device verifies against its certificate store. The device verifies the client certificate only if mutual authentication is enabled.
OS Installation Service
The OS installation service defines a gNOI API that is used for installation. The OS installation service is supported in the gNOI protocol.
This service provides an interface for the installation of an OS on a device. It supports the following three RPCs:
-
Install: This RPC transfers an image to a device. These images are uniquely identified by a version string. This RPC is the similar to the install add command; the main difference is that the image is transferred as part of the RPC.
-
Activate: This RPC sets the requested OS version, which is part of the input to the RPC, as the version to be used at the next reboot, and reboots the device. This RPC is the same as the install activate and the install commit commands.
-
Verify: This RPC verifies the current OS version.
Cisco IOS XE devices support both install mode and bundle mode to boot software images.
In install mode, you can bring up your device by booting the software package provisioning file that resides in the flash: file system. The ISO file system in each installed package is mounted to the root file system (rootfs) directly from the flash.
In bundle mode, you can boot your device by using the bundle (.bin) file. Packages are extracted from the bundle, and copied to the RAM. The ISO file system in each package is mounted to the rootfs. Unlike install boot mode, additional memory that is equivalent to the size of the bundle is used when booting in bundle mode.
In the following scenarios, an error message is generated when a device starts in bundle mode:
-
The device starts with the current image running in bundle mode.
-
The install RPC is initiated on the device to install a new image.
The following is a sample error message:
May 11 09:24:15.385 PST: %INSTALL-3-OPERATION_ERROR_MESSAGE:
Switch 1 R0/0: install_engine: Failed to install_add package
flash:gNOI_iosxe_17.05.01.0.144.1617180620.bin, Error: [2|install_add(ERR, )]:
Booted in bundle mode. For Bundle-to-Install mode conversion,
please use one-shot CLI - install add file <> activate commitEven though an error message is generated, the install RPC returns a success to the client. The error message can be safely ignored; the subsequent activate RPC is not affected. After rebooting with the new image, the device is in install mode.
 Note |
This error message is not displayed if the device was initially running in install mode. It is applicable only when the device starts in bundle mode. To view all the error messages, see https://github.com/openconfig/gnoi/blob/master/os/os.proto#L218. |
For more information about installation modes, see the "Performing Device Setup Configuration" chapter of the System Management Configuration Guide for all the Cisco Catalyst 9000 Series Switches.
Dual Route Processor Support
Cisco devices support both In-Service Software Update (ISSU) (only install mode is supported) and non-ISSU modes. When ISSU is not supported or is not possible through the Install RPC, the gNOI OS installation service will request a non-ISSU install.
If a device supports ISSU upgrade in case of dual Route Processors (RPs), the gNOI OS installation service interface invokes the install activate ISSU workflow. In all other scenarios, where ISSU not is supported, or the device supports a single RP, the gNOI OS installation service uses a regular non-ISSU image install workflow to process the gRPC activate request.
In bundle mode, the upgrade is done through the install add file filename activate commit command. This upgrade is the same for devices with a single RP. No ISSU support means that both the RPs are reloaded at the same time, and the device is down until one RP comes up.
In install mode without ISSU, both the RPs are reloaded at the same time and the device is down until one RP comes up. In install mode with ISSU, the reload of the RPs is simultaneous, and the device downtime is shorter.
OS Install RPC
The Install RPC transfers an image to a device. The RPC consists of the input InstallRequest RPC, and the output InstallResponse RPC, both of which are bidirectional streaming RPCs.
This RPC does not support Software Maintenance Update (SMU).
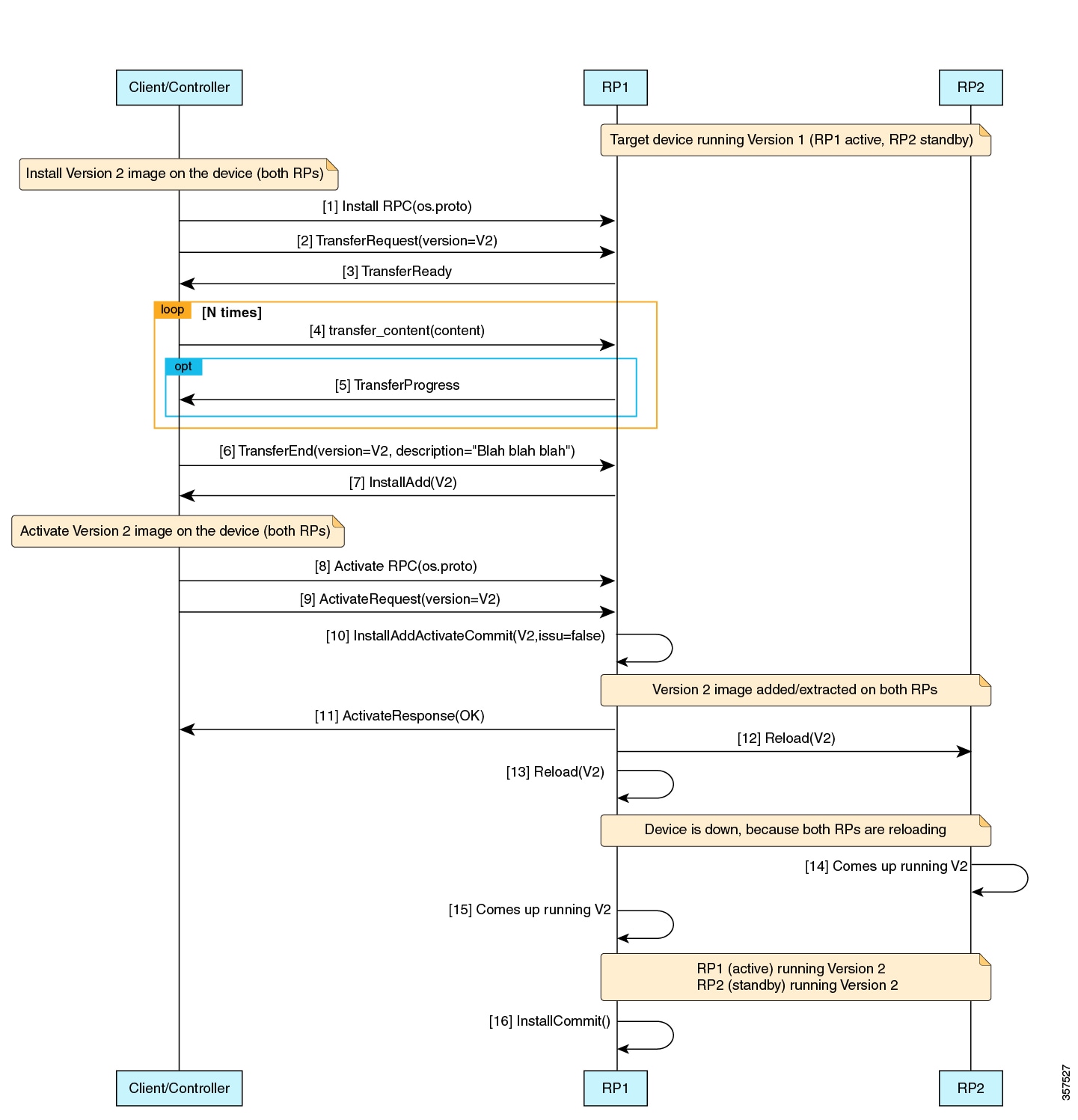
The following is a high-level message sequence for an Install RPC on a device with a single RP that is running the operating system Version 1:
-
A client initiates an Install RPC to the device.
-
The client sends a TransferRequest message to the device, with version set to Version 2.
-
The device responds with a TransferReady message to the client. This is required for the client to start transferring the image.
-
The client transfers the image by sending multiple transfer_content messages to the device.
-
Optionally, the device sends TransferProgress messages to the client.
-
The client sends a TransferEnd message to the device, indicating that the image transfer is complete.
-
In install mode, the device does an operation equivalent of the install add command programmatically. The contents of the package are extracted.
-
The device sends a Validated message, which contains the version extracted from the image, to the client, indicating that the image transfer is valid.
 Note |
If the Install RPC is stopped prematurely by the client, or if any part of the operation fails, the local image file is removed, and the install remove inactive command is invoked automatically. An appropriate status code is returned to the client. |

OS Activate RPC
The Activate RPC sets the requested operating system version as the version to be used at the next reboot, and reboots the target device. The RPC activates an installed operating system version. If the version is not already installed, the Activate RPC fails.
The client must provide a version that has been received in the Validated message of the Install RPC.
The following is the message sequence for an Activate RPC on a device with a single RP running operating system Version 1:
-
The client initiates an Activate RPC to a device.
-
The client sends an ActivateRequest message to the device with Version 2.
For the purpose of this message sequence, assume that Version 2 is already installed through the Install RPC.
-
The device does a programmatic operation equivalent to the install activate commit command, if it is in install mode, or the install add file activate commit command if it is in bundle mode.
-
Because no errors are detected in the activate process, the device responds with an ActivateResponse(OK) message to the client.
-
The device reloads with Version 2.
-
When the device comes up after the reload, it does a programmatic operation equivalent to the install commit command.
 Note |
Only one inactive image version is supported. Because of this, if a client installs Version 2 and then Version 3, the Version 2 files get deleted. The following images display the image activation workflow. |


OS Verify RPC
The Verify RPC verifies the running OS version. The response to the RPC contains information about the support and presence of a standby RP.
If there was an error in the last activate RPC, that error is returned in the response as a string. The gNOI OS installation service uses the install operational model and platform model to populate this information. Currently, the install operational model does not support different versions running on two RPs.
GNOI Factory-Reset Services
Cisco IOS XE Cupertino 17.7.1 supports gNOI factory-reset services as specified in the reset.proto.
The gNOI factory-reset service supports a single RPC, Start. This RPC instructs a device to clean the existing state, and boot the device in the same condition as it was shipped from the factory. The state includes, storage, configuration, logs, certificates, licenses, crashinfo, and Rommon variables. Not all Rommon variables are removed, enough are preserved on a per-platform basis to allow the image to automatically reboot with the preserved image. The device then reboots with the current Operating System image, and comes back into the default state, based on the simplified bootstrapping workflow. This RPC is accepted only if the target device is in a provisioned state.
The Start RPC is similar to the factory-reset all command, however; the RPC preserves the current Operating System image, unlike the command, which deletes the image. As part of the factory-reset scripts, both the flash: or harddisk:, where the current image resides is cleaned up. However, when the factory-reset scripts are run, the boot image or packages are backed up to the /tmp folder, and restored.
The regular factory-reset erases all the customer-specific data stored in a device and restores the device to its original configuration at the time of shipping. Data that is erased includes configurations, log files, boot variables, core files, and credentials such as Federal Information Processing Standard-related (FIPS-related) keys. The erasure is consistent with the clear method, as described in NIST SP 800-88 Rev. 1. For more information, see the "Performing Factory Reset Services" module of the System Management Configuration Guide for your platform.
gNOI Factory-Reset Error Messages
gNOI factory-reset services return an empty ResetSuccess message upon successfully triggering the factory reset on a device.
Some of the error messages that are returned in the context of gRPC and factory reset services are described in this section:
|
Error Message |
Error Description |
|---|---|
|
When the factory_os field is requested, the GNMIB returns a gRPC error code of INVALID_ARGUMENT along with the message, “Factory OS rollback is not supported.” |
In the ResetError message, the client will also receive the factory_os_unsupported field set to TRUE. The other fields in the message will have default values. |
|
This device does not support the requested zero-fill option. |
The StartRequest message has an optional field, zero_fill that instructs the target device to zero fill the persistent storage state data. When a client requests a zero-fill, and if the device cannot perform a zero fill, then the gRPC error code of INVALID_ARGUMENT is sent back to the client along with the message, “This device does not support the requested zero-fill option.” In the ResetError message, the zero_fill_unsupported field is set to TRUE. |
|
This device does not support the requested zero-fill option. |
When the device can perform a zero-fill, but the client has not made a request for a zero-fill, then the gRPC error code of INVALID_ARGUMENT is sent back to the client with the message, “This device does not support the requested zero-fill option.” In the ResetError message, the zero_fill_unsupported field is set to FALSE. |
|
Factory reset capability is not present. |
When the gNOI factory-reset script is run on an unsupported platform, the factory-reset services returns the gRPC error code of UNIMPLEMENTED with the message, “Factory reset capability is not present.” |
|
Factory reset interface is not ready. |
When the gNOI factory-reset management interface is down or busy, the factory-reset services returns the gRPC error code of UNAVAILABLE with the message, “Factory reset interface is not ready.” |
Without using a cert.proto provisioning operation, or configuring gNOI with a signed certificate (not self-signed), the gNOI factory-reset service will always return the FAILED_PRECONDITION error code.
 Feedback
Feedback