- Finding Feature Information
- Prerequisites for Unicast Reverse Path Forwarding
- Restrictions for Unicast Reverse Path Forwarding
- Information About Unicast Reverse Path Forwarding
Configuring Unicast Reverse Path Forwarding
The Unicast Reverse Path Forwarding feature limits the malicious traffic on a network. This feature enables devices to verify the reachability of the source address in packets that are being forwarded and limit the appearance of spoofed or malformed addresses on a network. If the source IP address is not valid, Unicast Reverse Path Forwarding (RPF) discards the packet.
This module describes the Unicast Reverse Path Forwarding feature.
- Finding Feature Information
- Prerequisites for Unicast Reverse Path Forwarding
- Restrictions for Unicast Reverse Path Forwarding
- Information About Unicast Reverse Path Forwarding
- How to Configure Unicast Reverse Path Forwarding
- Configuration Examples for Unicast Reverse Path Forwarding
- Additional References
- Feature Information for Unicast Reverse Path Forwarding
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table at the end of this module.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
Prerequisites for Unicast Reverse Path Forwarding
- Unicast Reverse Path Forwarding (RPF) requires Cisco Express Forwarding to function properly on a device.
-
Prior to configuring Unicast RPF, you must configure the following access control lists (ACLs): - Configure standard or extended ACL to mitigate the transmission of invalid IP addresses (by performing egress filtering). Configuring standard or extended ACLs permit only valid source addresses to leave your network and enter the Internet.
- Configure standard or extended ACL entries to drop (deny) packets that have invalid source IP addresses (by performing ingress filtering). Invalid source IP addresses include the following types:
- Configure standard or extended ACL entries to forward (permit) packets that fail the Unicast RPF checks and allow specific traffic from known asymmetric routed sources.
- Configure ACLs to track Unicast RPF events to provide additional information about network attacks.
Restrictions for Unicast Reverse Path Forwarding
The following basic restrictions apply to multihomed clients:
- Clients should not be multihomed on the same device because multihoming defeats the purpose of creating a redundant service for a client.
- Ensure that packets that flow up the link (out to the Internet) match the route advertised out of the link. Otherwise, Unicast RPF filters these packets as malformed packets.
- Unicast RPF is available only on images that support Cisco Express Forwarding.
Information About Unicast Reverse Path Forwarding
- Overview of Unicast Reverse Path Forwarding
- Unicast RPF Operation
- Access Control Lists and Logging
- Per-Interface Statistics
- Rules for Implementing Unicast RPF
Overview of Unicast Reverse Path Forwarding
The Unicast Reverse Path Forwarding feature helps to mitigate problems that are caused by the introduction of malformed or forged (spoofed) IP source addresses into a network by discarding IP packets that lack verifiable IP source addresses. For example, a number of common types of denial-of-service (DoS) attacks, including Smurf and Tribal Flood Network (TFN), can take advantage of forged or rapidly changing source IP addresses to allow attackers to thwart efforts to locate or filter these attacks. For ISPs that provide public access, Unicast RPF deflects such attacks by forwarding only packets that have source addresses that are valid and consistent with the IP routing table, thereby protecting the network of the ISP, ISP customers, and the Internet.
Unicast RPF Operation
When Unicast RPF is enabled on an interface of a device, the device examines all packets received as input on that interface to ensure that the source address and source interface information appears in the routing table and matches the interface on which packets are received. This ability to “look backwards” is available only when Cisco Express Forwarding is enabled on a device because the lookup relies on the presence of a Forwarding Information Base (FIB). Cisco Express Forwarding generates a FIB as part of its operation.
 Note |
In Cisco ASR 1000 Series Aggregation Services Routers, Cisco Express Forwarding is enabled by default and cannot be disabled. |
 Note |
Unicast RPF is an input function and is applied only on the input interface of a device at the upstream end of a connection. |
Unicast RPF does a reverse lookup in the Cisco Express Forwarding table to check if any packet received at the interface of a device arrives on the best return path (or return route) to the source of the packet. If the packet was received from one of the best reverse path routes, the packet is forwarded as normal. No reverse path route on the interface from which the packet was received can mean that the source address was modified. If Unicast RPF cannot find a reverse path for the packet, the packet is dropped or forwarded, depending on whether an access control list (ACL) is specified by using the ip verify unicast source reachable via command.
 Note |
With Unicast RPF, all equal-cost “best” return paths are considered valid. Unicast RPF supports multiple return paths, provided that each path is equal to the others in terms of the routing cost (such as number of hops, weights, and so on) and the route is available in the FIB. Unicast RPF also functions where Enhanced Interior Gateway Routing Protocol (EIGRP) variants are used. |
- If input ACLs are configured on the inbound interface.
- If the packet has arrived on the best return path to the source by doing a reverse lookup in the FIB table.
- Does a lookup of the Cisco Express Forwarding table for packet forwarding.
- Checks output ACLs on the outbound interface.
- Forwards the packet.
Access Control Lists and Logging
When you configure an access control list (ACL) and a packet fails the Unicast RPF check, the Unicast RPF checks the ACL to see if the packet should be dropped (by using a deny statement in the ACL) or forwarded (by using a permit statement in the ACL). Regardless of whether the packet is dropped or forwarded, the packet is counted in the global IP traffic statistics for Unicast RPF drops and in the interface statistics for Unicast RPF.
If no ACL is configured, the device drops the forged or malformed packet immediately, and no ACL logging occurs. The device and the interface Unicast RPF logging counters are updated.
To log Unicast RPF events, specify the logging option for ACL entries. Using the log information, administrators can view source addresses that are used in an attack, the time at which packets arrived at an interface, and so on.
 Caution |
Logging requires CPU and memory resources. Logging Unicast RPF events for attacks that have a high rate of forged packets can degrade the performance of a device. |
Per-Interface Statistics
Each time a packet is dropped or forwarded at an interface, that information is counted two ways: globally on the router and at each interface where you have applied Unicast RPF. Global statistics on dropped packets provide information about potential attacks on the network; however, these global statistics do not help to specify which interface is the source of the attack.
Per-interface statistics allow network administrators to track two types of information about malformed packets: Unicast RPF drops and Unicast RPF suppressed drops. Statistics on the number of packets that Unicast RPF drops help to identify the interface that is the entry point of the attack. The Unicast RPF drop count tracks the number of drops at the interface. The Unicast RPF suppressed drop count tracks the number of packets that failed the Unicast RPF check but were forwarded because of the permit permission set up in the ACL. Using the drop count and suppressed drop count statistics, a network administrator can takes steps to isolate the attack at a specific interface.
 Note |
Judicious use of ACL logging can further identify the address or addresses that are being dropped by Unicast RPF. |
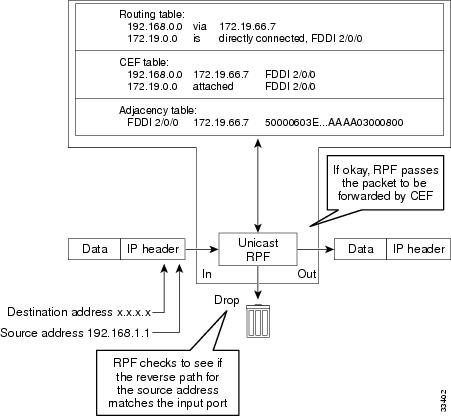
The figure below illustrates how Unicast RPF and CEF work together to validate IP source addresses by verifying packet return paths. In this example, a customer has sent a packet having a source address of 192.168.1.1 from interface FDDI 2/0/0. Unicast RPF checks the FIB to see if 192.168.1.1 has a path to FDDI 2/0/0. If there is a matching path, the packet is forwarded. If there is no matching path, the packet is dropped.
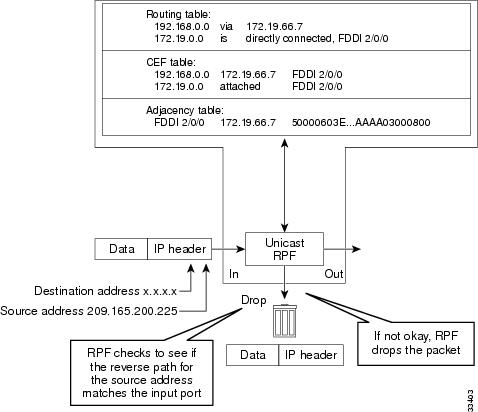
The figure below illustrates how Unicast RPF drops packets that fail validation. In this example, a customer has sent a packet having a source address of 209.165.200.225, which is received at interface FDDI 2/0/0. Unicast RPF checks the FIB to see if 209.165.200.225 has a return path to FDDI 2/0/0. If there is a matching path, the packet is forwarded. In this case, there is no reverse entry in the routing table that routes the customer packet back to source address 209.165.200.225 on interface FDDI 2/0/0, and so the packet is dropped.
Rules for Implementing Unicast RPF
The following rules apply when implementing Unicast Reverse Path Forwarding (RPF):
- Packets must be received at an interface that has the best return path (route) to the packets’ source. This process is called symmetric routing. A route in the Forwarding Information Base (FIB) must match the route to the receiving interface. Add a route in the FIB through dynamic or static routing or by using a network statement. Access control lists (ACLs) permit Unicast RPF to be used when packets arrive by specific, less-optimal asymmetric input paths.
- IP source addresses at the receiving interface must match the routing entry for the interface.
- Unicast RPF is an input function and can be applied at the input interface of a device at the upstream end of a connection.
Network administrators can use Unicast RPF for their customers and also for their downstream network or ISP, even if the downstream network or ISP has other connections to the Internet.
 Caution |
Using optional Border Gateway Protocol (BGP) attributes, such as weight and local preference, the best path back to source addresses can be modified. The best path modification will affect the operation of Unicast RPF. |
The following sections provides information about the implementation of Unicast RPF:
- Security Policy and Unicast RPF
- Ingress and Egress Filtering Policy for Unicast RPF
- Where to Use Unicast RPF
- Routing Table Requirements
- Where Not to Use Unicast RPF
- Unicast RPF with BOOTP and DHCP
Security Policy and Unicast RPF
When determining how to deploy Unicast Reverse Path Forwarding (RPF), consider the following points:
- Apply Unicast RPF at the downstream interface, away from the larger portion of the network, preferably at the edges of your network. The further you apply Unicast RPF, the finer the granularity you have in mitigating address spoofing and in identifying sources of spoofed addresses. For example, applying Unicast RPF on an aggregation device helps to mitigate attacks from many downstream networks or clients and is simple to administer, but Unicast RPF does not help in identifying the source of the attack. Applying Unicast RPF at the network access server helps to limit the scope of the attack and trace the source of the attack. However, deploying Unicast RPF across many sites adds to the administration cost of operating a network.
- When you deploy Unicast RPF on many entities on a network (for example, across the Internet, intranet, and extranet resources), you have better chances of mitigating large-scale network disruptions throughout the Internet community, and of tracing the source of an attack.
- Unicast RPF does not inspect IP packets that are encapsulated in tunnels, such as the generic routing encapsulation (GRE), Layer 2 Tunneling Protocol (L2TP), or Point-to-Point Tunneling Protocol (PPTP). Configure Unicast RPF on a home gateway so that Unicast RPF processes network traffic only after tunneling and encryption layers are stripped off from the packets.
Ingress and Egress Filtering Policy for Unicast RPF
Unicast Reverse Path Forwarding (RPF) can be more effective at mitigating spoofing attacks when combined with a policy of ingress and egress filtering by using access control lists (ACLs).
Ingress filtering applies filters to traffic that is received at a network interface from either internal or external networks. With ingress filtering, packets that arrive from other networks or the Internet and that have a source address that matches a local network or private or broadcast addresses are dropped. For example, in ISP environments, ingress filtering can be applied to traffic that is received at a device from either a client (customer) or the Internet.
Egress filtering applies filters to the traffic that exits a network interface (the sending interface). By filtering packets on devices that connect your network to the Internet or to other networks, you can permit only packets with valid source IP addresses to leave your network.
For more information on network filtering, refer to RFC 2267, Network Ingress Filtering: Defeating Denial of Service Attacks which employ IP Source Address Spoofing.
Where to Use Unicast RPF
Unicast Reverse Path Forwarding (RPF) can be used in any “single-homed” environment where there is essentially only one access point out of the network, which means that there is only one upstream connection to the network. Networks having one access point offer the best example of symmetric routing, which means that the interface where a packet enters the network is also the best return path to the source of the IP packet. Unicast RPF is best used at the network perimeter for Internet, intranet, or extranet environments, or in ISP environments for customer network terminations.
The following sections describe two sample network environments in which Unicast RPF is implemented:
- Enterprise Networks with a Single Connection to an ISP
- Applying Unicast RPF to Network Access Servers
Enterprise Networks with a Single Connection to an ISP
In enterprise networks, you can use Unicast Reverse Path Forwarding (RPF) to filter traffic at the input interface (a process called ingress filtering) to protect from malformed packets that arrive from the Internet. Traditionally, local networks that have one connection to the Internet use access control lists (ACLs) at the receiving interface to prevent spoofed packets from entering their local network.
ACLs work well for single-homed customers. However, when ACLs are used as ingress filters, the following two commonly referenced limitations apply:
- Packet-per-second (PPS) performance at very high packet rates
- ACL maintenance (whenever there are new addresses added to the network)
Unicast RPF addresses both the limitations described above. With Unicast RPF, ingress filtering is done at Cisco Express Forwarding PPS rates. Because Unicast RPF uses the Forwarding Information Base (FIB), ACL maintenance is not required, and thus, the administration overhead of traditional ACLs is reduced. The following figure and example demonstrate how Unicast RPF is configured for ingress filtering.
The figure below illustrates an enterprise network that has a single link to an upstream ISP. In this example, Unicast RPF is applied at serial interface 0/1/0 on the enterprise device for protection from malformed packets arriving from the Internet. Unicast RPF is also applied at serial interface 2/0/0 on the ISP device for protection from malformed packets arriving from the enterprise network.

A typical configuration on an ISP device that uses the topography in the figure above would be as follows:
ip cef interface loopback 0 description Loopback interface on Gateway Device 2 ip address 192.168.3.1 255.255.255.255 no ip redirects no ip directed-broadcast no ip proxy-arp ! interface Serial 2/0/0 description 128K HDLC link to ExampleCorp WT50314E R5-0 bandwidth 128 ip unnumbered loopback 0 ip verify unicast reverse-path no ip redirects no ip directed-broadcast no ip proxy-arp ! ip route 192.168.10.0 255.255.252.0 Serial 2/0/0
The gateway device configuration of the enterprise network will be similar to the following:
ip cef interface FastEthernet 0/0/0 description ExampleCorp LAN ip address 192.168.10.1 255.255.252.0 no ip redirects no ip directed-broadcast no ip proxy-arp ! interface Serial 0/1/0 description 128K HDLC link to ExampleCorp Internet Inc WT50314E C0 bandwidth 128 ip unnumbered FastEthernet 0/0/0 ip verify unicast reverse-path no ip redirects no ip directed-broadcast no ip proxy-arp ! ip route 0.0.0.0 0.0.0.0 Serial 0/1/0
Notice that Unicast RPF works with a single default route. There are no additional routes or routing protocols. Network 192.168.10.0/22 is a connected network. Hence, packets coming from the Internet with a source address in the network 192.168.10.0/22 will be dropped by Unicast RPF.
Applying Unicast RPF to Network Access Servers
If a network access server supports Cisco Express Forwarding, Unicast RPF will work on that network. A network access server (NAS) allows users to access a network by checking the credentials of the users accessing the network. Aggregation devices support Unicast RPF with single-homed clients. Unicast RPF works well on leased lines or on a digital subscriber line (DSL), ISDN, or public switched telephone network (PSTN) customer connections that are connected to the Internet. Dialup connections are a big source of denial of service (Dos) attacks that use forged IP addresses.
Aggregation devices need routing prefixes information (IP address block) for routing traffic. In the topology described below, aggregation devices do not have a full Internet routing table, and as a result, Unicast RPF uses the information configured or redistributed by the Interior Gateway Protocol (IGP) or Internal Border Gateway Protocol (IBGP) (based on how customer routes are added to the network) to route traffic. Unicast RPF is applied upstream on the customer dialup connection device that is on the receiving (input) interfaces of ISP aggregation devices.
The figure below illustrates how Unicast RPF is applied to aggregation and access devices for an ISP or point of presence (PoP) with ISP devices providing dialup connections.

Routing Table Requirements
Unicast Reverse Path Forwarding (RPF) uses the routing information in Cisco Express Forwarding tables for routing traffic. The amount of routing information that must be available in Cisco Express Forwarding tables depends on the device where Unicast RPF is configured and the functions the device performs in the network. For example, in an ISP environment where a device is a leased-line aggregation device for customers, the information about static routes that are redistributed into the Interior Gateway Protocol (IGP) or Internal Border Gateway Protocol (IBGP) (depending on which technique is used in the network) is required in the routing table. Because Unicast RPF is configured on customer interfaces, only minimal routing information is required. If a single-homed ISP configures Unicast RPF on the gateway to the Internet, the full Internet routing table information is required by Unicast RPF to help protect the ISP from external denial of service (DoS) attacks that use addresses that are not in the Internet routing table.
Where Not to Use Unicast RPF
Do not use Unicast Reverse Path Forwarding (RPF) on interfaces that are internal to a network. Internal interfaces are likely to have routing asymmetry (see the figure below), which means that there can be multiple routes to the source of a packet. Unicast RPF is applied only where there is a natural or configured symmetry.
For example, devices at the edge of an ISP network are more likely to have symmetrical reverse paths than devices that are in the core of an ISP network. The best forwarding path to forward packets from devices that are at the core of an ISP network may not be the best forwarding path that is selected for packets that are returned to the device.
We recommend that you do not apply Unicast RPF where there is a chance of asymmetric routing, unless you configure access control lists (ACLs) to allow the device to accept incoming packets. ACLs permit the use of Unicast RPF when packets arrive through specific, less-optimal asymmetric input paths.
The figure below illustrates how Unicast RPF can block legitimate traffic in an asymmetric routing environment.

Unicast RPF with BOOTP and DHCP
Unicast RPF allows packets with 0.0.0.0 as the source IP address and 255.255.255.255 as the destination IP address to pass through a network to enable Bootstrap Protocol (BOOTP) and DHCP functions to work properly when Unicast RPF is configured.
How to Configure Unicast Reverse Path Forwarding
Configuring Unicast RPF
To use Unicast Reverse Path Forwarding, you must configure a device for Cisco Express Forwarding switching or distributed Cisco Express Forwarding switching. If Cisco Express Forwarding is not enabled globally on a device, Unicast RPF will not work on that device. If Cisco Express Forwarding is running on a device, individual interfaces on the device can be configured with other switching modes. Unicast RPF is an input-side function that is enabled on an interface or subinterface that supports any type of encapsulation, and Unicast RPF operates on IP packets that are received by the device.
 Note |
Cisco Express Forwarding is enabled by default on Cisco ASR 1000 Series Aggregation Services Routers and cannot be disabled. |
1. enable
2. configure terminal
3. ip cef distributed
4. interface slot/subslot/port
5. ip verify unicast reverse-path list
6. no ip verify unicast reverse-path
7. exit
8. Repeat Steps 4 and 5 for each interface on which you want to apply Unicast RPF.
9. end
10. show cef interface [type number]
11. show ip traffic
12. show ip interface[type number]
DETAILED STEPS
Example:
The following sample output from the show cef interface command shows that Unicast RPF is enabled on serial interface 2/0/0:
Device# show cef interface serial 2/0/0 Serial2/0/0 is up (if_number 8) Internet address is 192.168.10.2/30 ICMP redirects are never sent Per packet loadbalancing is disabled !The next line displays Unicast RPF packet dropping information. IP unicast RPF check is enabled Inbound access list is not set Outbound access list is not set Interface is marked as point to point interface Packets switched to this interface on linecard are dropped to next slow path Hardware idb is Serial2/0/0 Fast switching type 4, interface type 6 !The next line displays Unicast RPF packet dropping information. IP Distributed CEF switching enabled IP LES Feature Fast switching turbo vector IP Feature CEF switching turbo vector Input fast flags 0x40, Output fast flags 0x0, ifindex 7(7) Slot 2 Slot unit 0 VC -1 Transmit limit accumulator 0x48001A02 (0x48001A02) IP MTU 1500
 Caution |
To disable Cisco Express Forwarding, you must first disable Unicast RPF. The failure to disable Unicast RPF before disabling Cisco Express Forwarding can cause Hot Standby Router Protocol (HSRP) failure. |
The following is sample output from the show ip traffic command. The command displays the total number (global count) of dropped or suppressed packets for all interfaces that are configured on the device. The Unicast RPF drop count is included in the IP statistics section of the command output. Unicast RPF counts the number of packets dropped or suppressed because of malformed or forged source addresses. Unicast RPF counts dropped or forwarded packets that include the following global and per-interface information:
Device# show ip traffic
IP statistics:
Rcvd: 1471590 total, 887368 local destination
0 format errors, 0 checksum errors, 301274 bad hop count
0 unknown protocol, 0 not a gateway
0 security failures, 0 bad options, 0 with options
Opts: 0 end, 0 nop, 0 basic security, 0 loose source route
0 timestamp, 0 extended security, 0 record route
0 stream ID, 0 strict source route, 0 alert, 0 other
Frags: 0 reassembled, 0 timeouts, 0 couldn't reassemble
0 fragmented, 0 couldn't fragment
Bcast: 205233 received, 0 sent
Mcast: 463292 received, 462118 sent
Sent: 990158 generated, 282938 forwarded
Drop: 3 encapsulation failed, 0 unresolved, 0 no adjacency
0 no route, 0 unicast RPF, 0 forced drop ! This line displays the Unicast RPF packet dropping information.
The following is sample output from the show ip interface command. This command displays the total number of dropped or suppressed packets at a specific interface. A nonzero value for the count of dropped or suppressed packets can be either of the following:
- Unicast RPF is dropping or suppressing packets that have a bad source address (normal operation).
- Unicast RPF is dropping or suppressing legitimate packets because the route is not configured correctly to use Unicast RPF where asymmetric routing exists. In asymmetric routing multiple paths can exist as best return paths for a source address.
Device# show ip interface fastethernet0/1/1 1 unicast RPF drop 1 unicast RPF suppressed drop
Troubleshooting Tips
HSRP Failure
The failure to disable Unicast RPF before disabling Cisco Express Forwarding can cause a Hot Standby Router Protocol (HSRP) failure. If you want to disable Cisco Express Forwarding on a device, you must first disable Unicast RPF.
Dropped Boot Requests
Unicast RPF can drop Bootstrap Protocol (BOOTP) request packets that have a source address of 0.0.0.0 because of the source address verification at the interface. To enable BOOTP requests to work on an interface, you must use ACLs instead of Unicast RPF.
Configuration Examples for Unicast Reverse Path Forwarding
Example: Configuring Unicast RPF
Device# configure terminal Device(config)# ip cef distributed Device(config)# interface Serial 5/0/0 Device(config-if)# description Connection to Upstream ISP Device(config-if)# ip address 209.165.200.225 255.255.255.252 Device(config-if)# no ip redirects Device(config-if)# no ip directed-broadcast Device(config-if)# no ip proxy-arp Device(config-if)# ip verify unicast reverse-path
Additional References
Related Documents
| Related Topic |
Document Title |
|---|---|
| Cisco IOS commands |
|
| Unicast RPF command descriptions |
|
| Cisco Express Forwarding commands |
Standards & RFCs
| Standard/RFC |
Title |
|---|---|
| RFC 1918 |
Address Allocation for Private Internets |
| RFC 2267 |
Network Ingress Filtering: Defeating Denial of Service Attacks which employ IP Source Address Spoofing |
Technical Assistance
| Description |
Link |
|---|---|
| The Cisco Support and Documentation website provides online resources to download documentation, software, and tools. Use these resources to install and configure the software and to troubleshoot and resolve technical issues with Cisco products and technologies. Access to most tools on the Cisco Support and Documentation website requires a Cisco.com user ID and password. |
Feature Information for Unicast Reverse Path Forwarding
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
| Feature Name |
Releases |
Feature Information |
|---|---|---|
| Unicast Reverse Path Forwarding |
Cisco IOS XE Release 2.1 |
The Unicast Reverse Path Forwarding feature limits the malicious traffic on a network. This feature enables devices to verify the reachability of the source address in packets that are being forwarded and limit the appearance of spoofed or malformed addresses on a network. If the source IP address is not valid, Unicast Reverse Path Forwarding (RPF) discards the packet. |
 Feedback
Feedback