- Finding Feature Information
- Restrictions for Cisco Firepower Threat Defense for ISR
- Information About Cisco Firepower Threat Defense for ISR
- Cisco Firepower Threat Defense for ISR Overview
- UCS-Based Hosting
- IDS Packet Flow in Cisco Firepower Threat Defense
- Firepower Sensor Interfaces
- Cisco Firepower Threat Defense Interoperability
- Hardware and Software Requirements for Cisco Firepower Threat Defense
- Obtaining Cisco Firepower Threat Defense License
- How to Deploy Cisco Firepower Threat Defense for ISR
- Configuration Examples for Cisco Firepower Threat Defense on ISR
- Verifying and Monitoring IDS Inspection
- Additional References for Cisco Firepower Threat Defense for ISR
- Feature Information for Cisco Firepower Threat Defense for ISR
Cisco Firepower
Threat Defense for ISR
Cisco Firepower Threat Defense is Cisco's premier network security option. It provides a comprehensive suite of security features such as firewall capabilities, monitoring, alerts, Intrusion Detection System (IDS) and Intrusion Prevention System (IPS).
This module describes how to configure and deploy IDS on Cisco Integrated Services Routers (ISRs).
- Finding Feature Information
- Restrictions for Cisco Firepower Threat Defense for ISR
- Information About Cisco Firepower Threat Defense for ISR
- How to Deploy Cisco Firepower Threat Defense for ISR
- Configuration Examples for Cisco Firepower Threat Defense on ISR
- Verifying and Monitoring IDS Inspection
- Additional References for Cisco Firepower Threat Defense for ISR
- Feature Information for Cisco Firepower Threat Defense for ISR
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
Restrictions for Cisco Firepower Threat Defense for ISR
Information About Cisco Firepower Threat Defense for ISR
Cisco Firepower Threat Defense for ISR Overview
Cisco Firepower Threat Defense is a premier security solution that provides enhanced inspection for packet flows.
-
Cisco FireSIGHT—A centralized policy and reporting entity that can run anywhere in the network. This can be the Cisco FireSIGHT appliance or a virtual installation on a server class machine.
-
Virtual Firepower sensor—Security entities that implement policies, and send events and statistics back to the defense center. The Firepower sensor is hosted on Cisco Unified Computing System (UCS) E-Series Blade. Both the FireSIGHT and sensor are distributed as virtual packages.
UCS E-Series Blades are general purpose blade servers that are housed within Cisco Integrated Services Routers (ISR) Generation 2 (G2) and Cisco ISR 4000 Series Integrated Services Routers. These blades can be deployed either as bare-metal on operating systems or as virtual machines on hypervisors. There are two internal interfaces that connect a router to an UCS E-Series Blade. On ISR G2, Slot0 is a Peripheral Component Interconnet Express (PCIe) internal interface, and UCS E-Series Slot1 is a switched interface connected to the backplane Multi Gigabit Fabric (MGF). In Cisco ISR 4000 Series Routers, both internal interfaces are connected to the MGF.
A hypervisor is installed on the UCS E-Series Blade, and Cisco Firepower Threat Defense runs as a virtual machine on it. The Cisco Firepower Threat Defense OVA file is directly installed on the UCS E-Series Blade using the hypervisor operating system. Cisco Firepower Threat Defense runs as an anonymous inline device with no additional communication with the router. Traffic is diverted from the ingress physical interface to the Cisco Firepower Threat Defense that runs on the UCS E-Series Blade.
The following figure shows a Cisco Firepower Threat Defense deployment scenario. In this figure, the traffic lines between sensors and FireSIGHT are control connections. Packets are routed through these connections using router forwarding rules.
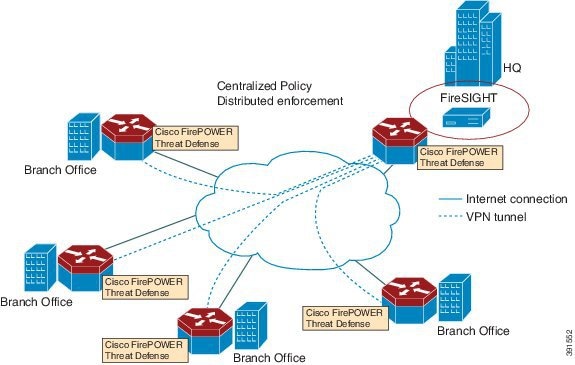
By default, the virtualized Cisco Firepower sensor comes with three interfaces, one for management, and two others for traffic analysis. These interfaces must be mapped to the UCS E-Series interfaces.
UCS-Based Hosting
The Cisco Unified Computing System (UCS) E-Series Blade provides a generic server blade for hosting applications. This blade typically runs VMware ESXi hypervisor and is managed through vSphere like other VMWare deployments.
If the Firepower sensor is hosted on the Cisco UCS E-Series Blade, you must specify the Cisco IOS interfaces connected to Cisco Firepower Threat Defense. Applications running within the UCS E-Series Blade are only loosely coupled with Cisco IOS, and to determine the interfaces that are attached to appliances a mapping of the interfaces must be done. Interfaces to connect to the Cisco UCS E-Series Blade are Bridge Domain Interfaces (BDI).
IDS Packet Flow in Cisco Firepower Threat Defense
Cisco Firepower Threat Defense supports Intrusion Detection System (IDS). In IDS mode, traffic is copied to the sensor and is analyzed for threats. IDS mode cannot enforce policies; it can detect and report violations. In IDS mode, traffic is replicated from interfaces and redirected to Cisco Firepower Threat Defense that runs on the Cisco UCS E-Series blade.
To view the interfaces that have enabled packet inspection in IDS mode, use the show platform software utd interfaces command. The packet replication occurs as one of the first output features.
For general packet processing, features that are applied to a packet form an ordered sequence that is determined by the configuration of the device. In general, these features are grouped as either input or output features, with the routing function marking the boundary between the two. The IDS packet replication occurs as one of the first output features and so if any input feature drops the packet, it will not be replicated to the IDS engine.
Firepower Sensor Interfaces
The Firepower sensor virtual appliance has three network interfaces—two for analyzing the traffic and one for management connectivity to FireSIGHT. The two traffic-bearing interfaces are represented as two virtual interfaces; Bridge Domain Interfaces (BDIs), in the configuration.
Although two interfaces are available for analyzing the traffic, only one traffic-bearing interface is used for Intrusion Detection System (IDS).
The Firepower sensor is connected to the management network and appears as another host on the LAN segment.
Cisco Firepower Threat Defense Interoperability
Cisco Firepower Threat Defense supports Intrusion Detection System (IDS). In IDS mode, selected traffic is copied to the Firepower sensor for analysis.
Cisco Firepower Threat Defense interoperates with the following features:
-
Zone-based firewall—Application layer gateways (ALGs), application inspection and controls (AICs), and policies configured between zones
-
Network Address Translation (NAT)

Note
Cisco Firepower Threat Defense does not support outside address translation, because there is no mechanism to inform Firepower Threat Defense about outside global addresses. However; you can still enable address translation on outside interfaces. Intrusion Prevention System (IPS) or IDS is invoked after NAT on the ingress interface, and before NAT on the egress interface, always using inside addresses. -
Crypto
-
Intelligent WAN (IWAN)
-
Kernel-based Virtual Machine Wide-Area Application Services (kWAAS)
Hardware and Software Requirements for Cisco Firepower Threat Defense
The following software is required to run the Cisco Firepower Threat Defense solution:
- UCS-E hypervisor
- ESXi 5.0.0, 5.1.0, or 5.5.0
- Cisco Firepower Sensor version Cisco IOS XE Release 3.14S and later releases
- Cisco FireSIGHT version 5.2, 5.3 or 5.4. FireSIGHT only supports the current version and is backward compatible with only the previous version. In case, your Cisco Firepower Sensor version is 5.4, then you have to use FireSIGHT version 5.4 or 5.3.
Obtaining Cisco Firepower Threat Defense License
Technology Package License Information:
-----------------------------------------------------------------
Technology Technology-package Technology-package
Current Type Next reboot
------------------------------------------------------------------
appx appxk9 EvalRightToUse appxk9
uc uck9 EvalRightToUse uck9
security securityk9 EvalRightToUse securityk9
ipbase ipbasek9 Permanent ipbasek9
How to Deploy Cisco Firepower Threat Defense for ISR
- Obtaining the Firepower Sensor Package
- Installing the Firepower Sensor OVA File
- Configuring Traffic Redirect on Cisco UCS E-Series Blade
- Bootstrapping the Firepower Sensor
- Enabling IDS Inspection Globally
- Enabling IDS Inspection per Interface
Obtaining the Firepower Sensor Package
To deploy the Firepower sensor on an Unified Computing System (UCS) E-Series Blade, download and save the OVA file. OVA is an Open Virtualization Archive that contains a compressed and installable version of a virtual machine. Download the OVA file from https://support.sourcefire.com/sections/1/sub_sections/51#5-2-virtual-appliances.
Installing the Firepower Sensor OVA File
Install the Firepower Sensor OVA on a UCS E-Series Blade, using a hypervisor, such as VMWare VSphere.
Installing Firepower Sensor on a UCS E-Series Blade
- Install the UCS E-Series card.
- Verify that the card is running by using the show platform command.
- Configure the Cisco
Integrated Management Controller (CIMC) port.
The CIMC GUI is a web-based management interface for E-Series Servers. You can launch the CIMC GUI to manage the server from any remote host that meets the following minimum requirements: The CIMC runs on the port that is named management. The following example shows how to bootstrap the management port with an IP address: ucse subslot 1/0 imc access-port dedicated imc ip-address 10.66.152.158 255.255.255.0 !
Connect to the CIMC through the browser by using the default login and password, which are admin and password, respectively. Based on the configuration example, the browser address is https://10.66.152.158.
- Install ESXi.
Download the ESXi image for your Cisco UCS E-Series Blade from https://my.vmware.com/web/vmware/details?downloadGroup=CISCO-ESXI-5.1.0-GA-25SEP2012&productId=284.
- Install Firepower Sensor by using VMWare VSphere on the Cisco UCS E-Series blade.
- Configure traffic redirect. For more information, see the section “Configuring Traffic Redirect on Cisco UCS E-Series Blade”.
- Configure the VMWare
vSwitch. The Virtual Machine Network Interface Card (VMNIC) mapping on ISR 4000
Series Routers is as follows:
- VMNIC0—Mapped to UCS E-Series interface x/0/0 on the router backplane
- VMNIC1—Mapped to UCS E-Series interface x/0/1 on the router backplane
- VMNIC2—Mapped to UCS E-Series frontplane GigabitEthernet 2 interface.
- VMNIC3—Mapped to UCS
E-Series frontplane GigabitEthernet 3 interface.

Note
VMNIC3 is only available on UCS E-Series 140D, 160Dm and 180D.
UCS E-Series 120S and 140S have 3 network adaptors and one management port. UCS E-Series 140D, 160Dm and 180D have 4 network adaptors.
Configuring Traffic Redirect on Cisco UCS E-Series Blade
1.
enable
2.
configure
terminal
3.
interface
type
number
4.
no
ip
address
5.
no
negotiation
auto
6.
switchport
mode
trunk
7.
no
mop
enabled
8.
no
mop
sysid
9.
service
instance
service-instance-number
ethernet
10.
encapsulation
dot1q
vlan-id
11.
rewrite
ingress
tag
pop
{1
|
2}
symmetric
12.
bridge
domain
bridge-ID
13.
end
DETAILED STEPS
Bootstrapping the Firepower Sensor
You must configure the Firepower Sensor manually. Perform this task to configure a Firepower sensor to communicate with FireSIGHT. For more information, see https://support.sourcefire.com/sections/10.
A sensor running on a Cisco Unified Computing System (UCS) E-Series Blade is bootstrapped by logging into the console of the Firepower Sensor virtual machine through VSphere.
 Note | Firepower Sensor must be installed and deployed before bootstrapping it. |
1. Provide the default username and password to login.
2.
configure
network
ipv4
manual
ip-address
network-mask
default-gateway
3.
configure
network
dns
servers
dns-server
4.
configure
network
dns
searchdomains
domain-name
5.
configure
manager
add
dc-hostname
registration-key
DETAILED STEPS
Example
The following is sample output from the show network command that displays the configured network settings of the Firepower Sensor:
Device# show network ---------------------------------------------------- IPv4 Configuration : manual Address : 10.66.152.137 Netmask : 255.255.255.0 Gateway : 10.66.152.1 MAC Address : 44:03:A7:43:05:AD Management port : 8305 ---------------------------------------------------- IPv6 Configuration : disabled Management port : 8305 ----------------------------------------------------
The following is sample output from the show dns command that displays the configured DNS settings:
Device# show dns search cisco.com nameserver 192.10.26.10
The following is sample output from the show managers command that displays the configured management settings:
Device# show managers Host : sourcefire-dc.cisco.com Registration Key : cisco-sf Registration : pending RPC Status :
Enabling IDS Inspection Globally
Based on your requirements, you can configure the Intrusion Detection System (IDS) inspection at a global level or at an interface level.
You cannot enable IDS inspection on dedicated management interfaces.
1.
enable
2.
configure terminal
3.
utd
4.
mode
ids-global
5.
ids
redirect-interface
interface
interface-number
6.
end
DETAILED STEPS
Enabling IDS Inspection per Interface
Based on your requirements, you can configure the Intrusion Detection System (IDS) inspection at a global level or at an interface level.
You cannot enable IDS inspection on dedicated management interfaces.
1.
enable
2.
configure terminal
3.
interface
type
number
4.
utd
ids
5.
exit
6. Repeat Steps 3 to 5, on all interfaces that require IDS inspection. Do not configure inspection on management interfaces.
7.
utd
8.
ids
redirect
interface
type
number
9.
end
DETAILED STEPS
Configuration Examples for Cisco Firepower Threat Defense on ISR
Example: Configuring Traffic Redirect on Cisco UCS E-Series Blade
This example shows how to configure ingress and egress interfaces for traffic redirect:
Router# configure terminal Router(config)# interface ucse 1/0/0 Router(config-if)# no ip address Router(config-if)# no negotiation auto Router(config-if)# switchport mode trunk Router(config-if)# no mop enabled Router(config-if)# no mop sysid Router(config-if)# exit Router(config)# interface ucse 1/0/1 Router(config-if)# no ip address Router(config-if)# no negotiation auto Router(config-if)# switchport mode trunk Router(config-if)# no mop enabled Router(config-if)# no mop sysid Router(config-if)# service instance 10 ethernet Router(config-if-srv)# encapsulation dot1q 10 Router(config-if-srv)# rewrite ingress tag pop 1 symmetric Router(config-if-srv)# bridge domain 10 Router(config-if-srv)# exit Router(config-if)# exit Router(config)# interface BDI 10 Router(config-if)# no shutdown Router(config-if)# ip address 10.1.1.1 255.255.255.0 Router(config-if-srv)# end
Example: Bootstrapping the Firepower Sensor
The following example shows how to bootstrap the Firepower Threat Defense sensor:
Sourcefire3D login: admin Password: Sourcefire Last login: Tue Nov 12 11:15:03 UTC 2013 on tty1 Copyright 2001-2013, Sourcefire, Inc. All rights reserved. Sourcefire is a registered trademark of Sourcefire, Inc. All other trademarks are property of their respective owners. Sourcefire Linux OS v5.2.0 (build 135) Sourcefire Virtual Device 64bit v5.2.0 (build 838) > configure password Enter current password: Enter new password: Confirm new password: > configure network ipv4 manual 10.66.152.137 255.255.255.0 10.66.152.1 Setting IPv4 network configuration. ADDRCONF(NETDEV_UP): eth0: link is not ready e1000: eth0: e1000_phy_read_status: Error reading PHY register e1000: eth0: e1000_watchdog_task: NIC Link is Up 1000 Mbps Full Duplex, Flow Control: None ADDRCONF(NETDEV_CHANGE): eth0: link becomes ready Network settings changed. > configure network dns servers 192.10.26.10 > configure network dns searchdomains cisco.com configure manager add sourcefire-dc.cisco.com cisco-sf Manager successfully configured.
Example: Enabling IDS Inspection Globally
Router# configure terminal Router(config)# utd Router(config-utd)# mode ids-global Router(config-utd)# ids redirect-interface BDI 10 Router(config-utd)# end
Example: Enabling IDS Inspection per Interface
Device# configure terminal Device(config)# interface gigabitethernet 0/1/1 Device(config-if)# utd ids Device(config-if)# end
Verifying and Monitoring IDS Inspection
Use the following commands to verify and monitor your Intrusion Detection System (IDS) deployment:
1.
enable
2.
debug
platform
condition
feature
utd
controlplane
3.
debug
platform
condition
feature
utd
dataplane
submode
4.
show
platform
hardware
qfp
active
utd
{config
|
status [all] [clear] [drop] [general]}
DETAILED STEPS
Additional References for Cisco Firepower Threat Defense for ISR
Related Documents
| Related Topic | Document Title |
|---|---|
|
IOS commands |
|
|
Security commands |
|
|
UCS E-Series Servers |
Technical Assistance
| Description | Link |
|---|---|
|
The Cisco Support website provides extensive online resources, including documentation and tools for troubleshooting and resolving technical issues with Cisco products and technologies. To receive security and technical information about your products, you can subscribe to various services, such as the Product Alert Tool (accessed from Field Notices), the Cisco Technical Services Newsletter, and Really Simple Syndication (RSS) Feeds. Access to most tools on the Cisco Support website requires a Cisco.com user ID and password. |
Feature Information for Cisco Firepower Threat Defense for ISR
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.|
Feature Name |
Releases |
Feature Information |
|---|---|---|
|
Cisco Firepower Threat Defense for ISR |
Cisco IOS XE Release 3.14S |
Cisco Firepower Threat Defense is a premier network security option. It provides a comprehensive suite of Security features such as firewall capabilities, monitoring, alerts, Intrusion Detection System (IDS) and Intrusion Prevention System (IPS). This feature is introduced on Cisco ISR 4000 Series Integrated Services Routers. The following command was introduced or modified: debug platform condition feature utd controlplane, debug platform condition feature utd dataplane submode, ids, mode (utd), show platform hardware qfp active feature utd, service utd, utd, utd ids. |
 Feedback
Feedback