- Finding Feature Information
- Prerequisites for Zone-Based Policy Firewall
- Restrictions for Zone-Based Policy Firewall
- Information About Zone-Based Policy Firewall
- Top-level Class Maps and Policy Maps
- Overview of Zones
- Class Maps and Policy Maps for Zone-Based Policy Firewalls
- Firewall and Network Address Translation
- WAAS and Firewall Integration Support
- WAAS Traffic Flow Optimization Deployment Scenarios
- Out-of-Order Packet Handling in Zone-Based Policy Firewall
- How to Configure Zone-Based Policy Firewall
- Configuration Examples for Zone-Based Policy Firewall
- Example: Configuring Layer 3 or Layer 4 Firewall Policies
- Example: Configuring an Inspect Parameter Map
- Example: Creating Security Zones and a Zone Pair and Attaching a Policy Map to a Zone Pair
- Example: Configuring NetFlow Event Logging
- Example: Firewall Configuration with WAAS
- Example: LDAP-Enabled Firewall Configuration
- Additional References
- Feature Information for Zone-Based Policy Firewall
Zone-Based Policy Firewall
This module describes the Cisco IOS XE unidirectional firewall policy between groups of interfaces known as zones.
- Finding Feature Information
- Prerequisites for Zone-Based Policy Firewall
- Restrictions for Zone-Based Policy Firewall
- Information About Zone-Based Policy Firewall
- How to Configure Zone-Based Policy Firewall
- Configuration Examples for Zone-Based Policy Firewall
- Additional References
- Feature Information for Zone-Based Policy Firewall
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest feature information and caveats, see the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the Feature Information Table at the end of this document.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
Prerequisites for Zone-Based Policy Firewall
The general guideline before you create zones is that you should group interfaces that are similar when they are viewed from a security perspective.
Restrictions for Zone-Based Policy Firewall
- Application-level maps (also referred to as Layer 7 class maps) are not supported in Cisco IOS XE software.
- In a Cisco Wide Area Application Services (WAAS) and Cisco IOS XE firewall configuration, all packets processed by a Wide Area Application Engine (WAE) device must go over the Cisco IOS XE firewall in both directions to support the Web Cache Coordination Protocol (WCCP) generic routing encapsulation (GRE) redirect. This situation occurs when the Layer 2 redirect is not available. If Layer 2 redirect is configured on the WAE, the system defaults to the GRE redirect to continue to function.
- When an in-to-out zone-based policy is configured to match the Internet Control Message Protocol (ICMP) on a Windows system, the traceroute command works. However, the same configuration on an Apple system does not work because it uses a UDP-based traceroute. To overcome this issue, configure an out-to-in zone-based policy with the icmp time-exceeded and icmp host unreachable commands with the pass command (not the inspect command).
- In a WAAS and Cisco IOS XE firewall configuration, WCCP does not support traffic redirection using policy-based routing (PBR).
- Stateful inspection support for multicast traffic is not supported between any zones, including the self zone. Use Control Plane Policing for protection of the control plane against multicast traffic.
- A UDP-based traceroute is not supported through ICMP inspection.
Information About Zone-Based Policy Firewall
- Top-level Class Maps and Policy Maps
- Overview of Zones
- Class Maps and Policy Maps for Zone-Based Policy Firewalls
- Firewall and Network Address Translation
- WAAS and Firewall Integration Support
- WAAS Traffic Flow Optimization Deployment Scenarios
- Out-of-Order Packet Handling in Zone-Based Policy Firewall
Top-level Class Maps and Policy Maps
Top-level class maps allow you to identify the traffic stream at a high level. This is accomplished by using the match access-group and match protocol commands. Top-level class maps are also referred to as Layer 3 and Layer 4 class maps.
Top-level policy maps allow you to define high-level actions by using the inspect, drop, and pass commands. You can attach policy maps to a target (zone pair).
 Note |
Only inspect type policies can be configured on a zone pair. |
Overview of Zones
A zone is a group of interfaces that have similar functions or features. They help you specify where a Cisco IOS XE firewall should be applied.
For example, on a router, the Gigabit Ethernet interface 0/0/0 and the Gigabit Ethernet interface 0/0/1 may be connected to the local LAN. These two interfaces are similar because they represent the internal network, so they can be grouped into a zone for firewall configurations.
By default, the traffic between interfaces in the same zone is not subject to any firewall policy and traffic passes freely between the interfaces. Firewall zones are used for security.
 Note |
Zones may not span interfaces in different VPN routing and forwarding (VRF) instances. |
- Security Zones
- Overview of Security Zone Firewall Policies
- Virtual Interfaces as Members of Security Zones
- Zone Pairs
- Zones and Inspection
- Zones and ACLs
Security Zones
A security zone is a group of interfaces to which a policy can be applied.
Grouping interfaces into zones involves the following two procedures:
- Creating a zone so that interfaces can be attached to it.
- Configuring an interface to be a member of a given zone.
By default, traffic flows among interfaces that are members of the same zone.
When an interface is a member of a security zone, all traffic to and from that interface (except traffic going to the router or initiated by the router) is dropped. To permit traffic to and from a zone-member interface, you must make that zone part of a zone pair and then apply a policy to that zone pair. If the policy permits traffic (through inspect or pass actions), traffic can flow through the interface.
Basic rules to consider when setting up zones are as follows:
- Traffic from a zone interface to a nonzone interface or from a nonzone interface to a zone interface is always dropped.
- Traffic between two zone interfaces is inspected if there is a zone pair relationship for each zone and if there is a configured policy for that zone pair.
- By default, all traffic between two interfaces in the same zone is always allowed as if the pass action is configured.
- A zone pair can be configured with a zone as both the source and the destination zone. An inspect policy can be configured on this zone pair to inspect or drop the traffic between two interfaces in the same zone.
For traffic to flow among all interfaces in a router, these interfaces must be a member of a security zone.
It is not necessary for all router interfaces to be members of security zones.
The figure below illustrates the following:
| Figure 1 | Security Zone Restrictions |
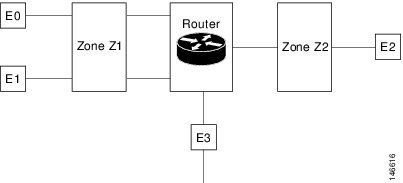
The following situations exist:
- The zone pair and policy are configured in the same zone. Traffic flows freely between interfaces E0 and E1 because they are members of the same security zone (Z1).
- If no policies are configured, traffic will not flow between any other interfaces (for example, E0 and E2, E1 and E2, E3 and E1, and E3 and E2).
- Traffic can flow between E0 or E1 and E2 only when an explicit policy permitting traffic is configured between zone Z1 and zone Z2.
- Traffic can never flow between E3 and E0/E1/E2 unless default zones are enabled.
Overview of Security Zone Firewall Policies
A class identifies a set of packets based on its contents. Normally, you define a class so that you can apply an action on the identified traffic that reflects a policy. A class is designated through class maps.
An action is a functionality that is typically associated with a traffic class. For example, inspect, drop, and pass are actions.
To create firewall policies, you must complete the following tasks:
- Define match criteria (class map)
- Associate actions to the match criteria (policy map)
- Attach the policy map to a zone pair (service policy)
The class-map command creates a class map to be used for matching packets to a specified class. Packets arriving at the targets (such as the input interface, output interface, or zone pair), determined by how the service-policy command is configured, are checked against the match criteria configured for a class map to determine if the packet belongs to that class.
The policy-map command creates or modifies a policy map that can be attached to one or more targets to specify a service policy. Use the policy-map command to specify the name of the policy map to be created, added to, or modified before you can configure policies for classes whose match criteria are defined in a class map.
Virtual Interfaces as Members of Security Zones
A virtual interface is a logical interface configured with generic configuration information for a specific purpose or for configuration common to specific users, plus router-dependent information. The template contains Cisco IOS XE software interface commands that are applied to virtual access interfaces, as needed. To configure a virtual template interface, use the interface virtual-template command.
Zone member information is acquired from a RADIUS server and then the dynamically created virtual interface is made a member of that zone. The zone-member security command puts the interface into the corresponding zone.
For more information on Per Subscriber Firewall on LNS feature, see the Release Notes for Cisco ASR 1000 Series Aggregation Services Routers for Cisco IOS XE Release 2.
Zone Pairs
A zone pair allows you to specify a unidirectional firewall policy between two security zones.
To define a zone pair, use the zone-pair security command. The direction of the traffic is specified by configuring a source and a destination zone. The source and destination zones of a zone pair must be security zones.
You can select the default or self zone as either the source or the destination zone. The self zone is a system-defined zone. It does not have any interfaces as members. A zone pair that includes the self zone, along with the associated policy, is applied to traffic directed to the router or traffic generated by the router. It does not apply to traffic through the router. The most common use of firewalls is to apply them to traffic through a router, so you need at least two zones (that is, you cannot use the self zone).
To permit traffic between zone member interfaces, you must configure a policy that permits (or inspects) traffic between that zone and another zone. To attach a firewall policy map to the target zone pair, use the service-policy type inspect command.
The figure below shows the application of a firewall policy to traffic flowing from zone Z1 to zone Z2, which means that the ingress interface for the traffic is a member of zone Z1 and the egress interface is a member of zone Z2.
| Figure 2 | Zone Pairs |
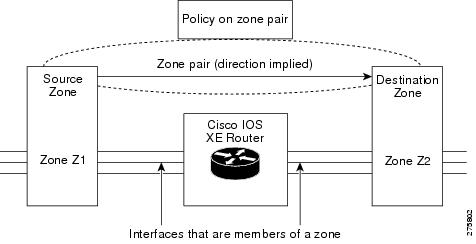
If there are two zones and you require policies for traffic going in both directions (from Z1 to Z2 and Z2 to Z1), you must configure two zone pairs (one for each direction).
If a policy is not configured between a pair of zones, traffic is dropped. However, it is not necessary to configure a zone pair and a service policy solely for the return traffic. By default, return traffic is not allowed. If a service policy inspects the traffic in the forward direction and there is no zone pair and service policy for the return traffic, the return traffic is inspected. If a service policy passes the traffic in the forward direction and there is no zone pair and service policy for the return traffic, the return traffic is dropped. In both these cases, you need to configure a zone pair and a service policy to allow the return traffic. In the above figure, it is not mandatory that you configure a zone pair source and destination solely for allowing return traffic from Z2 to Z1. The service policy on the Z1 to Z2 zone pair takes care of it.
Zones and Inspection
Zone-based policy firewalls examine the source and destination zones from the ingress and egress interfaces for a firewall policy. It is not necessary that all traffic flowing to or from an interface be inspected; you can designate that individual flows in a zone pair be inspected through your policy map that you apply across the zone pair. The policy map will contain class maps that specify the individual flows.
You can also configure inspect parameters like TCP thresholds and timeouts on a per-flow basis.
Zones and ACLs
ACLs applied to interfaces that are members of zones are processed before the policy is applied on the zone pair. You must make sure that interface ACLs do not interfere with the policy firewall traffic when there are policies between zones.
Pinholes (are ports opened through a firewall that allows applications controlled access to a protected network) are not punched for return traffic in interface Access Control Lists (ACLs).
Class Maps and Policy Maps for Zone-Based Policy Firewalls
Quality of service (QoS) class maps have numerous match criteria; firewalls have fewer match criteria. Firewall class maps have the type inspect and this information controls what shows up under firewall class maps.
A policy is an association of traffic classes and actions. It specifies what actions should be performed on defined traffic classes. An action is a specific function, and it is typically associated with a traffic class. For example, inspect and drop are actions.
- Layer 3 and Layer 4 Class Maps and Policy Maps
- Class-Map Configuration Restriction
- Class-Default Class Map
- Access Control List and Class Map
Layer 3 and Layer 4 Class Maps and Policy Maps
Layer 3 and Layer 4 class maps identify traffic streams on which different actions are performed.
A Layer 3 or Layer 4 policy map is sufficient for the basic inspection of traffic.
The following example shows how to configure class map c1 with the match criteria of ACL 101 and the FTP protocol, and create an inspect policy map named p1 to specify that packets will be dropped on the traffic at c1:
Router(config)# class-map type inspect match-all c1 Router(config-cmap)# match access-group 101 Router(config-cmap)# match protocol ftp Router(config-cmap)# exit Router(config)# policy-map type inspect p1 Router(config-pmap)# class type inspect c1 Router(config-pmap-c)# drop
Supported Protocols
The following protocols are supported:
- FTP
- H.323
- ICMP
- Lightweight Directory Access Protocol (LDAP)
- LDAP over Transport Layer Security/Secure Socket Layer (LDAPS)
- Real-time Streaming Protocol (RTSP)
- Session Initiation Protocol (SIP)
- SCCP (Skinny Client Control Protocol)
- TCP
- TFTP
- UDP
Class-Map Configuration Restriction
If a traffic meets multiple match criteria, these match criteria must be applied in the order of specific to less specific. For example, consider the following class map example:
class-map type inspect match-any my-test-cmap match protocol ftp match protocol tcp
In this example, the FTP traffic must first encounter the match protocol ftp command to ensure that the traffic will be handled by the service-specific capabilities of FTP inspection. If the "match" lines were reversed so that the traffic encountered the match protocol tcp command before it was compared to the match protocol ftp command, the traffic would simply be classified as TCP traffic and inspected according to the capabilities of the firewall's TCP Inspection component.
Class-Default Class Map
In addition to user-defined classes, a system-defined class map named class-default represents all packets that do not match any of the user-defined classes in a policy. It always is the last class in a policy map.
You can define explicit actions for this group of packets. If you do not configure any actions for class-default in an inspect policy, the default action is drop.
Access Control List and Class Map
Access lists are packet-classifying mechanisms. Access lists define the actual network traffic that is permitted or denied when an ACL is applied to a particular router network interface. Thus, the ACL is a sequential collection of permit and deny conditions that applies to a packet. A router tests packets against the conditions set in the ACL one at a time. A deny condition is interpreted as "do not match." Packets that match a deny access control entry (ACE) cause an ACL process to terminate and the next match statement within the class to be examined.
Class maps are used to match a range of variables in an ACL based on the following criteria:
- If a class map does not match a permit or a deny condition, then the ACL fails.
- If a class map is specified, the class map performs either an AND (match-all) or an OR (match-any) operation on the ACL variables.
- If a match-all attribute is specified and any match condition, ACL, or protocol fails to match the packet, further evaluation of the current class is stopped, and the next class in the policy is examined.
- If any match in a match-any attribute succeeds, the class map criteria are met and the action defined in the policy is performed.
- If an ACL matches the match-any attribute, the firewall attempts to ascertain the Layer 7 protocol based on the destination port.
If you specify the match-all attribute in a class map, the Layer 4 match criteria (ICMP, TCP, and UDP) are set and the Layer 7 match criteria are not set. Hence, the Layer 4 inspection is performed and Layer 7 inspection is omitted.
Access lists come in different forms: standard and extended access lists. Standard access lists are defined to permit or deny an IP address or a range of IP addresses. Extended access lists define both the source and the destination IP address or an IP address range. Extended access lists can also be defined to permit or deny packets based on ICMP, TCP, and UDP protocol types and the destination port number of the packet.
The following example shows how a packet received from the IP address 10.2.3.4 is matched with the class test1. In this example, the access list 102 matches the deny condition and stops processing other entries in the access list. Because the class map is specified with a match-all attribute, the "class-map test1" match fails. However, the class map is inspected if it matches one of the protocols listed in test1 class map.
If the class map test1 had a match-any attribute (instead of match-all), then the ACL would have matched deny and failed, but then the ACL would have matched the HTTP protocol and performed the inspection using "pmap1."
access-list 102 deny ip 10.2.3.4 0.0.0. any access-list 102 permit any any class-map type inspect match-all test1 match access-list 102 match protocol http class-map type inspect match-any test2 match protocol sip match protocol ftp match protocol http parameter-map type inspect pmap1 tcp idle-time 15 parameter-map type inspect pmap2 udp idle-time 3600 policy-map type inspect test class type inspect test1 inspect pmap1 class type inspect test2 inspect pmap2 class type inspect class-default drop log
Firewall and Network Address Translation
Network Address Translation (NAT) enables private IP internetworks that use nonregistered IP addresses to connect to the Internet. NAT operates on a router, usually connecting two networks, and translates the private (not globally unique) addresses in the internal network into legal addresses before packets are forwarded onto another network. NAT can be configured to advertise only one address for the entire network to the outside world. A router configured with NAT will have at least one interface to the inside network and one to the outside network.
In a typical environment, NAT is configured at the exit router between a stub domain and the backbone. When a packet leaves the domain, NAT translates the locally significant source address into a globally unique address. When a packet enters the domain, NAT translates the globally unique destination address into a local address. If more than one exit point exists, each NAT must have the same translation table. If the software cannot allocate an address because it has run out of addresses, it drops the packet and sends an ICMP host unreachable packet.
With reference to NAT, the term "inside" refers to those networks that are owned by an organization and that must be translated. Inside this domain, hosts will have addresses in one address space. When NAT is configured and when the hosts are outside, hosts will appear to have addresses in another address space. The inside address space is referred to as the local address space and the outside address space is referred to as the global address space.
Consider a scenario where NAT translates both the source and the destination IP addresses. A packet is sent to a router from inside NAT with the source address 192.168.1.1 and the destination address 10.1.1.1. NAT translates these addresses and sends the packet to the external network with the source address 209.165.200.225 and the destination address 209.165.200.224.
Similarly, when the response comes back from outside NAT, the source address will be 209.165.200.225 and the destination address will be 209.165.200.224. Therefore, inside NAT, the packets will have a source address of 10.1.1.1 and a destination address of 192.168.1.1.
In this scenario, if you want to create an Application Control Engine (ACE) to be used in a firewall policy, the pre-NAT IP addresses (also known as inside local and outside global addresses) 192.168.1.1 and 209.165.200.224 must be used.
WAAS and Firewall Integration Support
The WAAS software optimizes security-compliant WANs and application acceleration solutions with the following benefits:
- Optimizes a WAN through full stateful inspection capabilities.
- Simplifies Payment Card Industry (PCI) compliance.
- Protects transparent WAN accelerated traffic.
- Integrates WAAS networks transparently.
- Supports the Network Management Equipment (NME) WAE modules or standalone WAAS device deployment.
WAAS has an automatic discovery mechanism that uses TCP options during the initial three-way handshake used to identify WAE devices transparently. After automatic discovery, optimized traffic flows (paths) experience a change in the TCP sequence number to allow endpoints to distinguish between optimized and nonoptimized traffic flows.
 Note |
Paths are synonymous with connections. |
The Cisco IOS XE firewall automatically discovers WAAS optimized traffic by enabling the sequence number to change without compromising the stateful Layer 4 inspection of TCP traffic flows that contain internal firewall TCP state variables. These variables are adjusted for the presence of WAE devices.
If the Cisco IOS XE firewall notices that a traffic flow has successfully completed WAAS automatic discovery, it permits the initial sequence number shift for the traffic flow and maintains the Layer 4 state on the optimized traffic flow.
WAAS Traffic Flow Optimization Deployment Scenarios
The following sections describe three different WAAS traffic flow optimization scenarios for branch office deployments. WAAS traffic flow optimization works with the Cisco IOS XE firewall feature on Cisco Aggregation Services Routers (ASRs).
The figure below shows an example of an end-to-end WAAS traffic flow optimization with the Cisco IOS XE firewall. In this particular deployment, an NME-WAE device is on the Cisco IOS Integrated Services Router (ISR). WCCP is used to redirect traffic for interception.
| Figure 3 | End-to-End WAAS Optimization Path |

 Note |
NME-WAE is not supported on ASR. Therefore, to support NME-WAE in the branch office must be an ISR. |
WAAS Branch Deployment with an Off-Path Device
A WAE device can be either an NME-WAE that is installed on an ISR as an integrated service engine or a standalone WAE device.
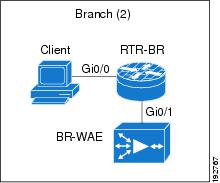
The figure below shows a WAAS branch deployment that uses WCCP to redirect traffic to an off-path, standalone WAE device for traffic interception. The configuration for this option is the same as the WAAS branch deployment with an NME-WAE.
| Figure 4 | WAAS Off-Path Branch Deployment |
WAAS Branch Deployment with an Inline Device
The figure below shows a WAAS branch deployment that has an inline WAE device that is physically in front of the router. Because the WAE device is in front of the router, Layer 7 inspection on the client side is not supported because the Cisco IOS XE firewall receives WAAS optimized packets.
| Figure 5 | WAAS Inline Path Branch Deployment |

An edge WAAS device with the Cisco IOS XE firewall is applied at branch office sites that must inspect traffic moving to and from a WAN connection. The Cisco IOS XE firewall monitors traffic for optimization indicators (TCP options and subsequent TCP sequence number changes) and allows optimized traffic to pass while still applying Layer 4 stateful inspection and deep packet inspection to all traffic, maintaining security while accommodating WAAS optimization advantages.
 Note |
If the WAE device is in the inline location, the device enters its bypass mode after the automatic discovery process. Although the router is not directly involved in WAAS optimization, the router must be aware that WAAS optimization is applied to the traffic in order to apply the Cisco IOS XE firewall inspection to network traffic and make allowances for optimization activity if optimization indicators are present. |
Out-of-Order Packet Handling in Zone-Based Policy Firewall
By default, the Cisco IOS XE firewall drops all out-of-order (OoO) packets when Layer 7 deep packet inspection (DPI) is enabled or when Layer 4 inspection with Layer 7 protocol match is enabled. Dropping out-of-order packets can cause significant delays in end applications because packets are dropped only after the retransmission timer expires (on behalf of the sender). Layer 7 inspection is a stateful packet inspection and it does not work when TCP packets are out of order.
In Cisco IOS XE Release 3.5S, if a session does not require DPI, OoO packets are allowed to pass through the router and reach their destination. All Layer 4 traffic with OoO packets are allowed to pass through to their destination. However, if a session requires Layer 7 inspection, OoO packets are still dropped. By not dropping OoO packets when DPI is not required, the need to retransmit dropped packets and the bandwidth needed to retransmit on the network is reduced.
How to Configure Zone-Based Policy Firewall
- Configuring Layer 3 and Layer 4 Firewall Policies
- Configuring an Inspect Parameter Map
- Configuring NetFlow Event Logging
- Creating Security Zones and a Zone Pair and Attaching a Policy Map to a Zone Pair
- Configuring the Firewall with WAAS
- Configuring an LDAP-Enabled Firewall
Configuring Layer 3 and Layer 4 Firewall Policies
Layer 3 and Layer 4 policies are "top level" policies that are attached to the target (zone pair). Use the following tasks to configure Layer 3 and Layer 4 firewall policies:
- Configuring a Class Map for a Layer 3 or Layer 4 Firewall Policy
- Creating a Policy Map for a Layer 3 or Layer 4 Firewall Policy
Configuring a Class Map for a Layer 3 or Layer 4 Firewall Policy
Perform the following task to configure a class map for classifying network traffic.
 Note |
You must perform at least one step from Step 4, 5, or 6. |
DETAILED STEPS
Creating a Policy Map for a Layer 3 or Layer 4 Firewall Policy
Perform the following task to create a policy map for a Layer 3 or Layer 4 firewall policy that will be attached to zone pairs.
If you are creating an inspect type policy map, note that only the following actions are allowed: drop, inspect, and pass.
 Note |
You must perform at least one step from Step 5, 6, or 7. |
DETAILED STEPS
Configuring an Inspect Parameter Map
An inspect parameter map is optional if you are using an inspect type policy. If you do not configure a parameter map, the firewall uses default parameters. Parameters associated with the inspect action apply to all nested actions (if any). If parameters are specified in both the top and lower levels, those in the lower levels override those in the top levels.
Changes to the parameter map are not reflected on connections already established through the firewall. Changes are applicable only to new connections permitted through the firewall. To ensure that your firewall enforces policies strictly, clear all connections in the firewall after you change the parameter map. To clear existing connections, use the clear zone-pair inspect sessions command.
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
|
|
Example: Router> enable |
Enables privileged EXEC mode. |
|
|
Example: Router# configure terminal |
Enters global configuration mode. |
|
|
Example: Router(config)# parameter-map type inspect eng-network-profile |
Configures an inspect parameter map for connecting thresholds, timeouts, and other parameters pertaining to the inspect keyword. |
|
|
Example: Router(config-profile)# alert on |
(Optional) Turns on stateful packet inspection alert messages that are displayed on the console. |
|
|
Example: Router(config-profile)# audit-trail on |
(Optional) Turns on audit trail messages. |
|
|
Example: Router(config-profile)# dns-timeout 60 |
(Optional) Specifies the DNS idle timeout (the length of time for which a DNS lookup session will continue to be managed while there is no activity). |
|
|
Example: Router(config-profile)# icmp idle-timeout 90 |
(Optional) Configures the timeout for ICMP sessions. |
|
|
Example: Router(config-profile)# max-incomplete low 800 |
(Optional) Defines the number of existing half-opened sessions that will cause the Cisco IOS XE firewall to start and stop deleting half-opened sessions. |
|
|
Example: Router(config-profile)# one-minute low 300 |
(Optional) Defines the number of new unestablished sessions that will cause the system to start and stop deleting half-opened sessions. |
|
|
Example: Router(config-profile)# sessions maximum 200 |
(Optional) Sets the maximum number of allowed sessions for the class it is associated with. |
|
|
Example: Router(config-profile)# tcp finwait-time 5 |
(Optional) Specifies how long a TCP session will be managed after the firewall detects a finish (FIN)-exchange. |
|
|
Example: Router(config-profile)# tcp idle-time 90 |
(Optional) Configures the timeout for TCP sessions. |
|
|
Example: Router(config-profile)# tcp max-incomplete host 500 block-time 10 |
(Optional) Specifies threshold and blocking time values for TCP host-specific denial of service (DoS) detection and prevention. |
|
|
Example: Router(config-profile)# tcp synwait-time 3 |
(Optional) Specifies how long the software will wait for a TCP session to reach the established state before dropping the session. |
|
|
Example: Router(config-profile)# udp idle-time 75 |
(Optional) Configures the idle timeout of UDP sessions going through the firewall. |
|
|
Example: Router(config-profile)# end |
Exits parameter-map type inspect configuration mode and enters privileged EXEC mode. |
Configuring NetFlow Event Logging
Global parameter maps are used for NetFlow event logging. With NetFlow event logging enabled, logs are sent to an off-box, high-speed log collector. By default, this functionality is not enabled. (If this functionality is not enabled, firewall logs are sent to a logger buffer located in the Route Processor or console.)
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
|
|
Example: Router> enable |
Enables privileged EXEC mode. |
|
|
Example: Router# configure terminal |
Enters global configuration mode. |
|
|
Example: Router(config)# parameter-map type inspect global |
Configures a global parameter map. |
|
|
Example: Router(config-profile)# log dropped-packets |
Enables dropped packet logging. |
|
|
Example: Router(config-profile)# log flow-export v9 udp destination 192.0.2.0 5000 |
Enables NetFlow event logging and provides the collector's IP address and port. |
|
|
Example: Router(config-profile)# log flow-export template timeout-rate 5000 |
Specifies the template timeout value. |
|
|
Example: Router(config)# end |
Exits global configuration mode and enters privileged EXEC mode. |
|
|
Example: Router# show parameter-map type inspect global |
Displays logging configurations. |
Creating Security Zones and a Zone Pair and Attaching a Policy Map to a Zone Pair
You need two security zones to create a zone pair. However, you can create only one security zone and use a system-defined security zone called "self." Note that if you select a self zone, you cannot configure inspect policing.
Use this process to complete the following tasks:
- Create at least one security zone.
- Define zone pairs.
- Assign interfaces to security zones.
- Attach a policy map to a zone pair.
 Tip |
The general guideline for creating a zone is that you should group interfaces that are similar when they are viewed from a security perspective. |
 Note |
|
DETAILED STEPS
| Command or Action | Purpose | |||
|---|---|---|---|---|
|
|
Example: Router> enable |
Enables privileged EXEC mode. |
||
|
|
Example: Router# configure terminal |
Enters global configuration mode. |
||
|
|
Example: Router(config)# zone security zone1 |
Creates a security zone to which interfaces can be assigned and enters security zone configuration mode. |
||
|
|
Example: Router(config-sec-zone)# description Internet Traffic |
(Optional) Describes the zone. |
||
|
|
Example: Router(config-sec-zone)# exit |
Returns to global configuration mode. |
||
|
|
Example: Router(config)# zone-pair security self-default-zp source self destination zone1 |
Creates a zone pair and enters security zone-pair configuration mode.
|
||
|
|
Example: Router(config-sec-zone-pair)# description accounting network |
(Optional) Describes the zone pair. |
||
|
|
Example: Router(config-sec-zone-pair)# service-policy type inspect p1 |
Attaches a firewall policy map to the destination zone pair.
|
||
|
|
Example: Router(config-sec-zone-pair)# exit |
Returns to global configuration mode. |
||
|
|
Example: Router(config)# interface gigabitethernet 0 |
Configures an interface and enters interface configuration mode. |
||
|
|
Example: Router(config-if)# zone-member security zone1 |
Assigns an interface to a specified security zone.
|
||
|
|
Example: Router(config-if)# end |
Exits interface configuration mode and enters privileged EXEC mode. |
Configuring the Firewall with WAAS
Perform the following task to configure an end-to-end WAAS traffic flow optimization for the firewall that uses WCCP to redirect traffic to a WAE device for traffic interception.
In Cisco IOS XE software, WAAS support is always enabled and WAAS processing is always discovered. Thus, the ip inspect waas enable command is not necessary and therefore not supported.
DETAILED STEPS
| Command or Action | Purpose | |||
|---|---|---|---|---|
|
|
Example: Router> enable |
Enables privileged EXEC mode. |
||
|
|
Example: Router# configure terminal |
Enters global configuration mode. |
||
|
|
Example: Router(config)# ip wccp 61 |
Enters the WCCP dynamically defined service identifier number. |
||
|
|
Example: Router(config)# class-map type inspect match-any most-traffic |
Creates an inspect type class map for the traffic class and enters QoS class-map configuration mode. |
||
|
|
Example: Router(config-cmap)# match protocol http |
Configures the match criteria for a class map based on the specified protocol. |
||
|
|
Example: Router(config-cmap)# exit |
Exits QoS class-map configuration mode and enters global configuration mode. |
||
|
|
Example: Router(config)# policy-map type inspect match-any p1 |
Creates a Layer 3 or Layer 4 inspect type policy map and enters policy map configuration mode. |
||
|
|
Example: Router(config-pmap)# class type inspect most-traffic |
Specifies the firewall traffic (class) map on which an action is to be performed. |
||
|
|
Example: Router(config-pmap-c)# inspect |
Enables Cisco IOS XE stateful packet inspection. |
||
|
|
Example: Router(config-pmap-c)# class class-default |
Specifies the matching of the system default class. |
||
|
|
Example: Router(config-pmap-c)# exit |
Exits policy-map class configuration mode and enters policy map configuration mode. |
||
|
|
Example: Router(config-pmap)# exit |
Exits policy map configuration mode and enters global configuration mode. |
||
|
|
Example: Router(config)# zone security zone1 |
Creates a security zone to which interfaces can be assigned and enters security zone configuration mode. |
||
|
|
Example: Router(config-sec-zone)# description Internet Traffic |
(Optional) Describes the zone. |
||
|
|
Example: Router(config-sec-zone)# exit |
Returns to global configuration mode. |
||
|
|
Example: Router(config)# zone-pair security self-default-zp source self destination zone1 |
Creates a zone pair and enters security zone-pair configuration mode.
|
||
|
|
Example: Router(config-sec-zone-pair)# description accounting network |
(Optional) Describes the zone pair. |
||
|
|
Example: Router(config-sec-zone-pair)# service-policy type inspect p1 |
Attaches a firewall policy map to the destination zone pair.
|
||
|
|
Example: Router(config-sec-zone-pair)# exit |
Exits security zone-pair configuration mode and enters global configuration mode. |
||
|
|
Example: Router(config)# interface gigabitethernet 0/0/0 |
Configures an interface and enters interface configuration mode. |
||
|
|
Example: Router(config-if)# description 123 |
(Optional) Describes the interface. |
||
|
|
Example: Router(config-if)# zone-member security zone1 |
Assigns an interface to a specified security zone.
|
||
|
|
Example: Router(config-if)# ip address 10.70.0.1 255.255.255.0 |
Assigns the interface IP address for the security zone. |
||
|
|
Example: Router(config-if)# ip wccp 61 redirect in |
Specifies the following WCCP parameters on the interface:
|
||
|
|
Example: Router(config-if)# end |
Exits interface configuration mode and enters privileged EXEC mode. |
Configuring an LDAP-Enabled Firewall
Lightweight Directory Access Protocol (LDAP) is an application protocol that is used for querying and updating information stored on directory servers. The LDAP-Enabled Firewall feature enables Cisco firewalls to support Layer 4 LDAP inspection by default.
You can configure an LDAP-enabled firewall in interface configuration mode or in global configuration mode. Before you configure an LDAP-enabled firewall in interface configuration mode, you must configure a zone by using the zone security command.
DETAILED STEPS
| Command or Action | Purpose | |||
|---|---|---|---|---|
|
|
Example: Router> enable |
Enables privileged EXEC mode. |
||
|
|
Example: Router# configure terminal |
Enters global configuration mode. |
||
|
|
Example: Router(config)# zone security private |
Creates a security zone to which interfaces can be assigned and enters security zone configuration mode. |
||
|
|
Example: Router(config-sec-zone)# exit |
Exits security zone configuration mode and enters global configuration mode. |
||
|
|
Example: Router(config)# zone security internet |
Creates a security zone to which interfaces can be assigned and enters security zone configuration mode. |
||
|
|
Example: Router(config-sec-zone)# exit |
Exits security zone configuration mode and enters global configuration mode. |
||
|
|
Example: Router(config)# class-map type inspect match-any internet-traffic-class |
Creates an inspect type class map for the traffic class and enters QoS class-map configuration mode. |
||
|
|
Example: Router(config-cmap)# match protocol ldap |
Configures the match criteria for a class map based on the specified protocol. |
||
|
|
Example: Router(config-cmap)# exit |
Exits QoS class-map configuration mode and enters global configuration mode. |
||
|
|
Example: Router(config)# policy-map type inspect private-internet-policy |
Creates a Layer 3 or Layer 4 inspect type policy map and enters policy map configuration mode. |
||
|
|
Example: Router(config-pmap)# class type inspect internet-traffic-class |
Specifies the firewall traffic (class) map on which an action is to be performed. |
||
|
|
Example: Router(config-pmap-c)# inspect |
Enables Cisco IOS XE stateful packet inspection. |
||
|
|
Example: Router(config-pmap-c)# class class-default |
Specifies the matching of the system default class. |
||
|
|
Example: Router(config-pmap-c)# exit |
Exits policy-map class configuration mode and enters policy map configuration mode. |
||
|
|
Example: Router(config-pmap)# exit |
Exits policy map configuration mode and enters global configuration mode. |
||
|
|
Example: Router(config)# zone-pair security private-internet source private destination internet |
Creates a zone pair and enters security zone-pair configuration mode.
|
||
|
|
Example: Router(config-sec-zone-pair)# service-policy type inspect private-internet-policy |
Attaches a firewall policy map to the destination zone pair.
|
||
|
|
Example: Router(config-sec-zone-pair)# end |
Exits security zone-pair configuration mode and enters privileged EXEC mode. |
Configuration Examples for Zone-Based Policy Firewall
- Example: Configuring Layer 3 or Layer 4 Firewall Policies
- Example: Configuring an Inspect Parameter Map
- Example: Creating Security Zones and a Zone Pair and Attaching a Policy Map to a Zone Pair
- Example: Configuring NetFlow Event Logging
- Example: Firewall Configuration with WAAS
- Example: LDAP-Enabled Firewall Configuration
Example: Configuring Layer 3 or Layer 4 Firewall Policies
class-map type inspect match-all c1 match access-group 101 match protocol ftp ! policy-map type inspect p1 class type inspect c1 inspect inspect-params pass !
Example: Configuring an Inspect Parameter Map
parameter-map type inspect eng-network-profile alert on audit-trail on dns-timeout 60 icmp idle-timeout 90 max-incomplete low 800 one-minute low 300 sessions maximum 200 tcp finwait-time 5 tcp idle-time 90 tcp max-incomplete host 500 block-time 10 tcp synwait-time 3 udp idle-time 75
Example: Creating Security Zones and a Zone Pair and Attaching a Policy Map to a Zone Pair
zone security zone1 description Internet Traffic ! zone-pair security self-default-zp source self destination zone1 description accounting network service-policy type inspect p1 ! interface gigabitethernet 0 zone-member security zone1
Example: Configuring NetFlow Event Logging
parameter-map type inspect global log dropped-packets log flow-export v9 udp destination 192.0.2.0 5000 log flow-export template timeout rate 5000
Example: Firewall Configuration with WAAS
The following example provides an end-to-end WAAS traffic flow optimization configuration for the firewall that uses WCCP to redirect traffic to a WAE device for traffic interception.
The following configuration example prevents traffic from being dropped between security zone members because the integrated-service-engine interface is configured on a different zone and each security zone member is assigned an interface.
ip wccp 61 ip wccp 62 class-map type inspect match-any most-traffic match protocol icmp match protocol ftp match protocol tcp match protocol udp policy-map type inspect p1 class type inspect most--traffic inspect class class-default zone security zone-hr zone security zone-outside zone security z-waas zone-pair security hr-out source zone-hr destination zone-outside service-policy type inspect p1 zone-pair security out--hr source zone-outside destination zone-hr service-policy type inspect p1 zone-pair security eng-out source zone-eng destination zone-outside service-policy type inspect p1 interface GigabitEthernet 0/0/0 description Trusted Interface ipaddress 10.70.0.1 255.0.0.0 ip wccp 61 redirect in zone-member security zone-hr interface GigabitEthernet 0/0/1 description Trusted Interface ipaddress 10.71.0.2 255.0.0.0 ip wccp 61 redirect in zone-member security zone-eng interface GigabitEthernet 0/0/1 description Untrusted Interface ipaddress 10.72.2.3 255.0.0.0 ip wccp 62 redirect in zone-member security zone-outside interface Integrated-Service-Engine l/0 ipaddress 10.70.100.1 255.0.0.0 ip wccp redirect exclude in zone-member security z-waas
Example: LDAP-Enabled Firewall Configuration
Interface Configuration
interface GigabitEthernet 0/1/5 ip address 192.168.0.1 255.255.255.0 zone-member security private no shutdown interface GigabitEthernet 0/1/6 ip address 192.168.1.1 255.255.255.0 zone-member security internet no shutdown
Global Firewall Configuration
zone security private zone security internet class-map type inspect match-any internet-traffic-class match protocol ldap match protocol ldaps match protocol ldap-admin policy-map type inspect private-internet-policy class type inspect internet-traffic-class inspect class class-default zone-pair security private-internet source private destination internet service-policy type inspect private-internet-policy
Additional References
Related Documents
| Related Topic |
Document Title |
|---|---|
| Cisco IOS commands |
|
| Security commands |
|
| Quality of Service commands |
|
| Per subscriber firewall support |
Release Notes for Cisco ASR 1000 Series Aggregation Services Routers for Cisco IOS XE Release 2 |
Standards and RFCs
| Standard/RFC |
Title |
|---|---|
| RFC 4511 |
Lightweight Directory Access Protocol (LDAP): The Protocol |
MIBs
| MIB |
MIBs Link |
|---|---|
| None |
To locate and download MIBs for selected platforms, Cisco software releases, and feature sets, use Cisco MIB Locator found at the following URL: |
Technical Assistance
| Description |
Link |
|---|---|
| The Cisco Support and Documentation website provides online resources to download documentation, software, and tools. Use these resources to install and configure the software and to troubleshoot and resolve technical issues with Cisco products and technologies. Access to most tools on the Cisco Support and Documentation website requires a Cisco.com user ID and password. |
Feature Information for Zone-Based Policy Firewall
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and software image support. Cisco Feature Navigator enables you to determine which software images support a specific software release, feature set, or platform. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn . An account on Cisco.com is not required.
| Table 1 | Feature Information for Zone-Based Policy Firewall |
| Feature Name |
Releases |
Feature Configuration Information |
|---|---|---|
| Firewall High Speed Logging (HSL) Support |
Cisco IOS XE Release 2.1 |
The Firewall High Speed Logging Support feature introduces support for the firewall HSL using NetFlow v9 as the export format. The following commands were introduced or modified: log dropped-packet, log flow-export v9 udp destination, log flow-export template timeout-rate, parameter-map type inspect global. |
| Firewall--NetMeeting Directory (LDAP) ALG Support |
Cisco IOS XE Release 2.4 |
LDAP is an application protocol that is used for querying and updating information stored on directory servers. The Firewall--Netmeeting Directory ALG Support feature enables Cisco firewalls to support Layer 4 LDAP inspection by default. The following commands were introduced or modified: match protocol. |
| Out-of-Order Packet Handling in Zone-Based Policy Firewall |
Cisco IOS XE Release 3.5S |
The Out-of-Order Packet Handling feature allows OoO packets to pass through the router and reach their destination if a session does not require DPI. All Layer 4 traffic with OoO packets are allowed to pass through to their destination. However, if a session requires Layer 7 inspection, the OoO packets are still dropped. |
| Zone-Based Policy Firewall |
Cisco IOS XE Release 2.1 |
The Zone-Based Policy Firewall feature provides a Cisco IOS XE software unidirectional firewall policy between groups of interfaces known as zones. |
| Zone-Based Firewall--Default Zone |
Cisco IOS XE Release 2.6 |
The Zone-Based Firewall--Default Zone feature introduces a default zone that enables a firewall policy to be configured on a zone pair that consist of a zone and a default zone. Any interface without explicit zone membership belongs to a default zone. The following commands were introduced or modified: zone-pair security and zone security. |
 Feedback
Feedback