- Read Me First
- RADIUS Attributes Overview and RADIUS IETF Attributes
- RADIUS Vendor-Proprietary Attributes
- RADIUS Vendor-Specific Attributes and RADIUS Disconnect-Cause Attribute Values
- Connect-Info RADIUS Attribute 77
- Encrypted Vendor-Specific Attributes
- RADIUS Attribute 8 Framed-IP-Address in Access Requests
- RADIUS Attribute 82 Tunnel Assignment ID
- RADIUS Tunnel Attribute Extensions
- RADIUS Attribute 66 Tunnel-Client-Endpoint Enhancements
- RADIUS Attribute Value Screening
- RADIUS Attribute 55 Event-Timestamp
- RADIUS Attribute 104
- RADIUS NAS-IP-Address Attribute Configurability
- RADIUS Attribute 5 NAS-Port Format Specified on a Per-Server Group Level
RADIUS Vendor-Specific Attributes and RADIUS Disconnect-Cause Attribute Values
The Internet Engineering Task Force (IETF) draft standard specifies a method for communicating vendor-specific information between the network access server and the RADIUS server by using the vendor-specific attribute (attribute 26). Attribute 26 encapsulates vendor specific attributes, thereby, allowing vendors to support their own extended attributes otherwise not suitable for general use.
- Finding Feature Information
- Information About RADIUS Vendor-Specific Attributes and RADIUS Disconnect-Cause Attribute Values
- RADIUS Disconnect-Cause Attribute Values
- Additional References
- Feature Information for RADIUS Vendor-Specific Attributes and RADIUS Disconnect-Cause Attribute Values
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
Information About RADIUS Vendor-Specific Attributes and RADIUS Disconnect-Cause Attribute Values
The Cisco RADIUS implementation supports one vendor-specific option using the format recommended in the specification. Cisco’s vendor-ID is 9, and the supported option has vendor-type 1, which is named “cisco-avpair.” The value is a string of the following format:
protocol : attribute sep value *
“Protocol” is a value of the Cisco “protocol” attribute for a particular type of authorization; protocols that can be used include IP, IPX, VPDN, VOIP, SHELL, RSVP, SIP, AIRNET, OUTBOUND. “Attribute” and “value” are an appropriate attribute-value (AV) pair defined in the Cisco TACACS+ specification, and “sep” is “=” for mandatory attributes and “*” for optional attributes. This allows the full set of features available for TACACS+ authorization to also be used for RADIUS.
For example, the following AV pair causes Cisco’s “multiple named ip address pools” feature to be activated during IP authorization (during PPP’s IPCP address assignment):
cisco-avpair= ”ip:addr-pool=first“
If you insert an “*”, the AV pair “ip:addr-pool=first” becomes optional. Note that any AV pair can be made optional.
cisco-avpair= ”ip:addr-pool*first“
The following example shows how to cause a user logging in from a network access server to have immediate access to EXEC commands:
cisco-avpair= ”shell:priv-lvl=15“
Attribute 26 contains the following three elements:
The figure below shows the packet format for a VSA encapsulated “behind” attribute 26.
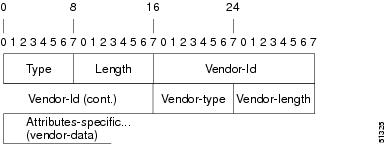
 Note | It is up to the vendor to specify the format of their VSA. The Attribute-Specific field (also known as Vendor-Data) is dependent on the vendor's definition of that attribute. |
The table below describes significant fields listed in the Vendor-Specific RADIUS IETF Attributes table (second table below), which lists supported vendor-specific RADIUS attributes (IETF attribute 26).
|
Field |
Description |
|---|---|
|
Number |
All attributes listed in the following table are extensions of IETF attribute 26. |
|
Vendor-Specific Command Codes |
A defined code used to identify a particular vendor. Code 9 defines Cisco VSAs, 311 defines Microsoft VSAs, and 529 defines Ascend VSAs. |
|
Sub-Type Number |
The attribute ID number. This number is much like the ID numbers of IETF attributes, except it is a “second layer” ID number encapsulated behind attribute 26. |
|
Attribute |
The ASCII string name of the attribute. |
|
Description |
Description of the attribute. |
See “Configuring Router to Use Vendor-Specific RADIUS Attributes” section of t he Configuring RADIUS feature module for more information on configuring your NAS to recognize and use VSAs.
RADIUS Disconnect-Cause Attribute Values
Disconnect-cause attribute values specify the reason a connection was taken offline. The attribute values are sent in Accounting request packets. These values are sent at the end of a session, even if the session fails to be authenticated. If the session is not authenticated, the attribute can cause stop records to be generated without first generating start records.
The table below lists the cause codes, values, and descriptions for the Disconnect-Cause (195) attribute.
 Note | The Disconnect-Cause is incremented by 1000 when it is used in RADIUS AVPairs; for example, disc-cause 4 becomes 1004. |
|
Cause Code |
Value |
Description |
||
|---|---|---|---|---|
|
2 |
Unknown |
Reason unknown. |
||
|
4 |
CLID-Authentication-Failure |
Failure to authenticate number of the calling-party. |
||
|
10 |
No-Carrier |
No carrier detected.
|
||
|
11 |
Lost-Carrier |
Loss of carrier. |
||
|
12 |
No-Detected-Result-Codes |
Failure to detect modem result codes. |
||
|
20 |
User-Ends-Session |
User terminates a session.
|
||
|
21 |
Idle-Timeout |
Timeout waiting for user input. Codes 21, 100, 101, 102, and 120 apply to all session types. |
||
|
22 |
Exit-Telnet-Session |
Disconnect due to exiting Telnet session. |
||
|
23 |
No-Remote-IP-Addr |
Could not switch to SLIP/PPP; the remote end has no IP address. |
||
|
24 |
Exit-Raw-TCP |
Disconnect due to exiting raw TCP. |
||
|
25 |
Password-Fail |
Bad passwords. |
||
|
26 |
Raw-TCP-Disabled |
Raw TCP disabled. |
||
|
27 |
Control-C-Detected |
Control-C detected. |
||
|
28 |
EXEC-Process-Destroyed |
EXEC process destroyed. |
||
|
40 |
Timeout-PPP-LCP |
PPP LCP negotiation timed out.
|
||
|
41 |
Failed-PPP-LCP-Negotiation |
PPP LCP negotiation failed. |
||
|
42 |
Failed-PPP-PAP-Auth-Fail |
PPP PAP authentication failed. |
||
|
43 |
Failed-PPP-CHAP-Auth |
PPP CHAP authentication failed. |
||
|
44 |
Failed-PPP-Remote-Auth |
PPP remote authentication failed. |
||
|
45 |
PPP-Remote-Terminate |
PPP received a Terminate Request from remote end. |
||
|
46 |
PPP-Closed-Event |
Upper layer requested that the session be closed. |
||
|
63 |
PPP-Echo-Replies |
TCP connection has been closed. |
||
|
100 |
Session-Timeout |
Session timed out. |
||
|
101 |
Session-Failed-Security |
Session failed for security reasons. |
||
|
102 |
Session-End-Callback |
Session terminated due to callback. |
||
|
120 |
Invalid-Protocol |
Call refused because the detected protocol is disabled. |
||
|
600 |
VPN-User-Disconnect |
Call disconnected by client (through PPP). Code is sent if the LNS receives a PPP terminate request from the client. |
||
|
601 |
VPN-Carrier-Loss |
Loss of carrier. This can be the result of a physical line going dead. Code is sent when a client is unable to dial out using a dialer. |
||
|
602 |
VPN-No-Resources |
No resources available to handle the call. Code is sent when the client is unable to allocate memory (running low on memory). |
||
|
603 |
VPN-Bad-Control-Packet |
Bad L2TP or L2F control packets. This code is sent when an invalid control packet, such as missing mandatory Attribute-Value pairs (AVP), from the peer is received. When using L2TP, the code will be sent after six retransmits; when using L2F, the number of retransmits is user configurable.
|
||
|
604 |
VPN-Admin-Disconnect |
Administrative disconnect. This can be the result of a VPN soft shutdown, which is when a client reaches maximum session limit or exceeds maximum hopcount. Code is sent when a tunnel is brought down by issuing the clear vpdn tunnel command. |
||
|
605 |
VPN-Tunnel-Shut |
Tunnel teardown or tunnel setup has failed. Code is sent when there are active sessions in a tunnel and the tunnel goes down.
|
||
|
606 |
VPN-Local-Disconnect |
Call is disconnected by LNS PPP module. Code is sent when the LNS sends a PPP terminate request to the client. It indicates a normal PPP disconnection initiated by the LNS. |
||
|
607 |
VPN-Session-Limit |
VPN soft shutdown is enabled. Code is sent when a call has been refused due to any of the soft shutdown restrictions previously mentioned. |
||
|
611 |
VPDN-Tunnel-In-Resync |
VPDN tunnel is in HA resync. |
Additional References
The following sections provide references related to RADIUS Vendor-Specific Attributes (VSA) and RADIUS Disconnect-Cause Attribute Values.
Related Documents
|
Related Topic |
Document Title |
|---|---|
|
Cisco IOS commands |
|
|
Security commands |
Cisco IOS Security Command Reference |
|
Security Features |
Cisco IOS XE Security Configuration Guide: Securing User Services , Release 2 |
|
Security Server Protocols |
Security Server Protocols section of the Cisco IOS XE Security Configuration Guide: Securing User Services , Release 2 |
|
RADIUS Configuration |
Configuring RADIUS feature module. |
Standards
|
Standard |
Title |
|---|---|
|
Internet Engineering Task Force (IETF) Internet Draft: Network Access Servers Requirements |
Network Access Servers Requirements: Extended RADIUS Practices |
MIBs
|
MIB |
MIBs Link |
|---|---|
|
None. |
To locate and download MIBs for selected platforms, Cisco software releases, and feature sets, use Cisco MIB Locator found at the following URL: |
RFCs
|
RFC |
Title |
|---|---|
|
RFC 2865 |
Technical Assistance
|
Description |
Link |
|---|---|
|
The Cisco Support website provides extensive online resources, including documentation and tools for troubleshooting and resolving technical issues with Cisco products and technologies. To receive security and technical information about your products, you can subscribe to various services, such as the Product Alert Tool (accessed from Field Notices), the Cisco Technical Services Newsletter, and Really Simple Syndication (RSS) Feeds. Access to most tools on the Cisco Support website requires a Cisco.com user ID and password. |
Feature Information for RADIUS Vendor-Specific Attributes and RADIUS Disconnect-Cause Attribute Values
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.|
Feature Name |
Releases |
Feature Information |
|---|---|---|
|
Accounting of VPDN Disconnect Cause |
Cisco IOS XE Release 2.1 |
This feature was introduced on Cisco ASR 1000 Series Routers. |
|
Vendor-Specific RADIUS Attributes |
Cisco IOS XE Release 2.1 |
This document discusses the Internet Engineering Task Force (IETF) draft standard, which specifies a method for communicating vendor-specific information between the network access server and the RADIUS server by using the vendor-specific attribute (attribute 26). Attribute 26 encapsulates vendor specific attributes, thereby, allowing vendors to support their own extended attributes otherwise not suitable for general use. In Cisco IOS XE Release 2.1, this feature was introduced on the Cisco ASR 1000 Series Aggregation Services Routers. |
 Feedback
Feedback