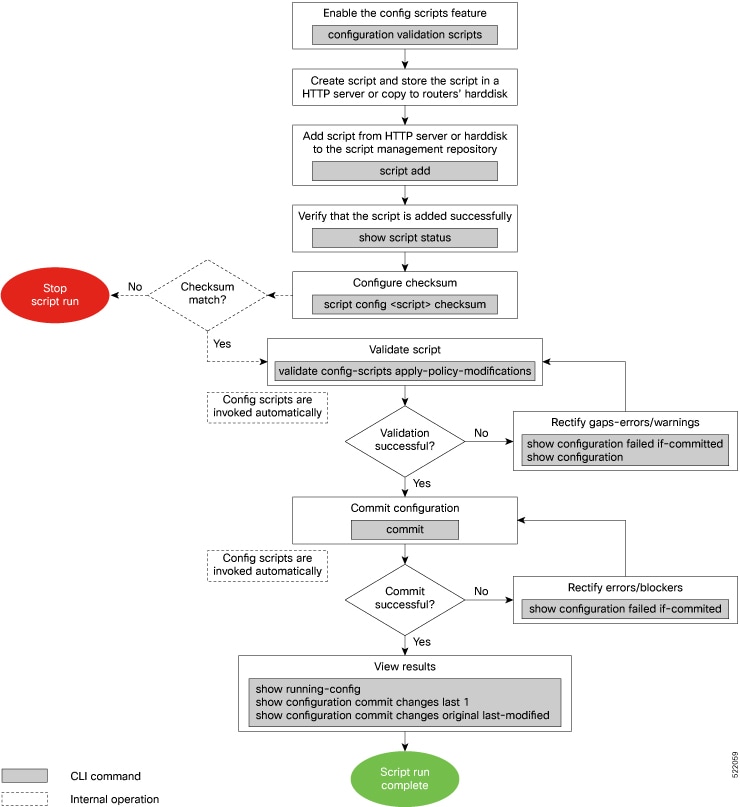
Workflow to Run Config Scripts
Complete the following tasks to provision config scripts:
-
Enable the config scripts feature—Globally activate the config scripts feature on the router using configuration validation scripts command.
-
Download the script—Store the config script on an HTTP server or copy to the harddisk of the router. Add the config script from the HTTP server to the script management repository (hardisk:/mirror/script-mgmt) on the router using the script add config command.
-
Validate the script—Check script integrity and authenticity using the script config script.py checksum command. A script cannot be used unless the checksum is configured. After the checksum is configured, the script is active.

Note
A config script is invoked automatically when you validate or commit a configuration change to modify the candidate configuration.
-
Validate the configuration—Ensure that the configuration changes comply with the predefined conditions in the script and uncover potential errors using validate config-scripts apply-policy-modifications command.
-
View the script execution details—Retrieve the operational data using the show operational Config Global Validation Script Execution command.
The following image shows a workflow diagram representing the steps involved in using a config script:
Enable Config Scripts Feature
Config scripts are driven by commit operations. To run the config scripts, you must enable the feature on the router. You must have root user privileges to enable the config scripts.
 Note |
You must commit the configuration to enable the config scripts feature before committing any script checksum configuration. |
Procedure
|
Step 1 |
Enable the config scripts. Example: |
|
Step 2 |
Commit the configuration. Example: |
Download the Script to the Router
To manage the scripts, you must add the scripts to the script management repository on the router. A subdirectory is created for each script type. By default, this repository stores the downloaded scripts in the appropriate subdirectory based on script type.
| Script Type | Download Location |
|---|---|
|
config |
harddisk:/mirror/script-mgmt/config |
|
exec |
harddisk:/mirror/script-mgmt/exec |
|
process |
harddisk:/mirror/script-mgmt/process |
|
eem |
harddisk:/mirror/script-mgmt/eem |
-
Method 1: Add script from a server
-
Method 2: Copy script from external repository to harddisk using scp or copy command
In this section, you learn how to add config-script.py script to the script management repository.
Procedure
|
Step 1 |
Add the script to the script management repository on the router using one of the two options:
|
||
|
Step 2 |
Verify that the scripts are downloaded to the script management repository on the router. Example:config_ssh_script.py is copied to harddisk:/mirror/script-mgmt/config directory on the router.
|
Configure Checksum for Config Script
Every script is associated with a checksum hash value. This value ensures the integrity of the script, and that the script is not tampered with. The checksum is a string of numbers and letters that act as a fingerprint for script. The checksum of the script is compared with the configured checksum. If the values do not match, the script is not run and a syslog warning message is displayed.
It is mandatory to configure the checksum to run the script.
 Note |
Config scripts support SHA256 checksum. |
Before you begin
Procedure
|
Step 1 |
Retrieve the SHA256 checksum hash value for the script. Ideally this action would be performed on a trusted device, such as the system on which the script was created. This minimizes the possibility that the script is tampered with. However, if the router is secure, you can retrieve the checksum hash value from the IOS XR Linux bash shell. Example:Make note of the checksum value. |
||
|
Step 2 |
View the status of the script. Example:The |
||
|
Step 3 |
Configure the checksum. Example:
If you are configuring multiple scripts, the system decides an appropriate order to run the scripts. However, you can control the order in which scripts execute using a priority value. For more information on configuring the priority value, see Control Priority When Running Multiple Scripts. |
||
|
Step 4 |
Verify the status of the script. Example:The status |
Validate or Commit Configuration to Invoke Config Script
|
Feature Name |
Release Information |
Description |
|---|---|---|
|
Validate Pre-configuration Using Config Scripts |
Release 7.5.1 |
This feature allows you to use config scripts to validate pre-configuration during a commit or validate operation. Any active config scripts can read and validate (accept, reject or modify) pre-configuration. The pre-configuration is only applied to the system later on, when the relevant hardware is inserted, and does not require further script validation at that point. Previously, config scripts did not allow validating configuration until the corresponding hardware was present. |
You can validate a configuration change on the set of active config scripts (including any scripts newly activated as part of the configuration change) before committing the changes. This validation ensures that the configuration complies with predefined conditions defined in the active scripts based on your network requirements. With validation, you can update the target configuration buffer with any modifications that are made by the config scripts. You can review the target configuration using the show configuration command, and further refine the changes to resolve any outstanding errors before revalidating or committing the configuration.
 Note |
If the config script rejects one or more items in the commit operation, the entire commit operation is rejected. |
You can also validate pre-configuration during a commit operation. Pre-configuration is any configuration specific to a particular hardware resource such as an interface or a line card that is committed before that resource is present. For example, commit configuration for a line card before it is inserted into the chassis. Any active config scripts can read and validate (accept, reject or modify) the pre-configuration. However, when the configuration is committed, the pre-configuration is not applied to the system. Later, when the relevant hardware resource is available, the pre-configuration becomes active and is applied to the system. The config scripts are not run to validate the configuration at this point as the scripts have already validated this configuration.
Before you begin
Procedure
|
Step 1 |
Validate the configuration with the conditions in the config script. Example:The output shows that there are no errors in the changed configuration. You can view the modifications made to the target configuration.
|
||
|
Step 2 |
View the modified target configuration. Example: |
||
|
Step 3 |
Commit the configuration. Example:If the script returns an error, use the show configuration failed if-committed command to view the errors. If there are no validation errors, the commit operation is successful including any modifications that are made by config scripts. You can view the recent commit operation that the script modified, and display the original configuration changes before the script modified the values using show configuration commit changes original last-modified command. If the commit operation is successful, you can check what changes were committed including the script modifications using show configuration commit changes last 1 command.
|
||
|
Step 4 |
After the configuration change is successful, view the running configuration and logs for details. Example: |
 Feedback
Feedback