Learn about Zero Touch Provisioning
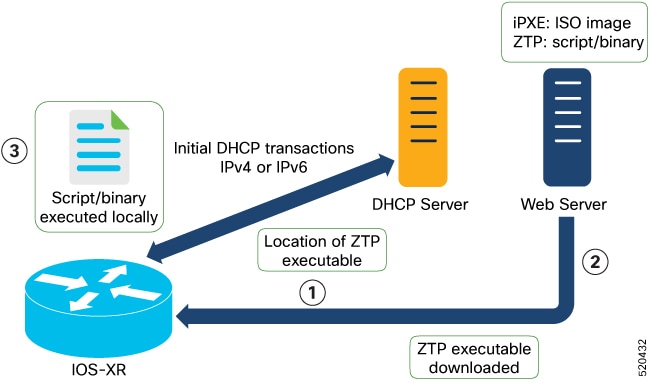
ZTP allows you to provision the network device with day 0 configurations and supports both management ports and data ports.
ZTP provides multiple options, such as:
-
Automatically apply specific configuration in a large-scale environment.
-
Download and install specific IOS XR image.
-
Install specific application package or third party applications automatically.
-
Deploy containers without manual intervention.
-
Upgrade or downgrade software versions effortlessly on thousands of network devices at a time
Benefits of Using ZTP
ZTP helps you manage large-scale service providers infrastructures effortlessly. Following are the added benefits of using ZTP:
-
ZTP helps you to remotely provision a router anywhere in the network. Thus eliminates the need to send an expert to deploy network devices and reduces IT cost.
-
Automated provisioning using ZTP can remove delay and increase accuracy and thus is cost-effective and provides better customer experience.
By automating repeated tasks, ZTP allows network administrators to concentrate on more important stuff.
-
ZTP process helps you to quickly restore service. Rather than troubleshooting an issue by hand, you can reset a system to well-known working status.
Use Cases
The following are some of the useful use cases for ZTP:
-
Using ZTP to install Chef
-
Using ZTP to integrate IOS-XR with NSO
-
Using ZTP to install Puppet
You can initiate ZTP in one of the following ways:
-
Fresh Boot: Use this method for devices that has no pre-loaded configuration. See Getting Started with ZTP on a Fresh Boot of a Router. See Zero Touch Provisioning on a Fresh Boot of a Router.
-
Manual Invocation: Use this method when you want to forcefully initiate ZTP on a fully configured device. See Manual ZTP Invocation.
-
ZTP Bootscript: Use this method when you want to hard code a script to be executed on every boot. See Configure ZTP BootScript.

 Feedback
Feedback