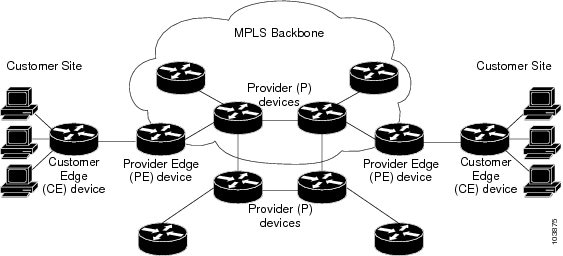
Consider two customers
having two VPN sites each, that are connected to the same PE router. VRFs are
used to create a separate routing table for each customer. We create one VRF
for each customer (say, vrf1 and vrf2) and then add the corresponding
interfaces of the router to the respective VRFs. Each VRF has its own routing
table with the interfaces configured under it. The global routing table of the
router does not show these interfaces, whereas the VRF routing table shows the
interfaces that were added to the VRF. PE routers exchange routing information
with CE devices by using static routing or a routing protocol such as BGP or
RIP.
To summarize, VRF-lite
configuration involves these main tasks:
Configuration
Example
-
Create VRF:
Router#configure
Router(config)#vrf vrf1
Router(config-vrf)#address-family ipv4 unicast
/* You must create route-policy pass-all before this configuration */
Router(config-vrf-af)#import from default-vrf route-policy pass-all
Router(config-vrf-af)#import route-target
Router(config-vrf-import-rt)#100:100
Router(config-vrf-import-rt)#exit
Router(config-vrf-af)#export route-target
Router(config-vrf-import-rt)#100:100
Router(config-vrf-import-rt)#exit
Router(config-vrf-import-rt)#commit
Similarly create
vrf2, with route-target as 100:100.
-
Configure VRF
under the interface:
Router#configure
Router(config)#
Router(config-subif)#vrf vrf1
Router(config-subif)#ipv4 address 192.0.2.2 255.255.255.252
Router(config-subif)#encapsulation dot1q 2001
Router(config-subif)#exit
Router(config)#
Router(config-subif)#vrf vrf2
Router(config-subif)#ipv4 address 192.0.2.5/30 255.255.255.252
Router(config-subif)#encapsulation dot1q 2000
Router(config-vrf-import-rt)#commit
Similarly configure vrf1 under interface TenGigE0/0/0/1.2001 and vrf2 under interface TenGigE0/0/0/1.2000
-
Configure VRF under routing protocol:
Router#configure
Router(config)#router rip
Router(config-rip)#vrf vrf1
Router(config-rip-vrf)#
Router(config-rip-vrf-if)#exit
Router(config-rip-vrf)#
Router(config-rip-vrf-if)#exit
Router(config-rip-vrf)#default-information originate
Router(config-vrf-import-rt)#commit
Similarly configure vrf2 under rip, with
Running
Configuration
/* VRF Configuration */
vrf vrf1
address-family ipv4 unicast
import route-target
100:100
!
export route-target
100:100
!
!
!
vrf vrf2
address-family ipv4 unicast
import route-target
100:100
!
export route-target
100:100
!
!
!
/* Interface Configuration */
interface
vrf vrf1
ipv4 address 192.0.2.2 255.255.255.252
encapsulation dot1q 2001
!
interface
vrf vrf2
ipv4 address 192.0.2.5/30 255.255.255.252
encapsulation dot1q 2000
!
interface
vrf vrf1
ipv4 address 203.0.113.2 255.255.255.252
encapsulation dot1q 2001
!
interface
vrf vrf2
ipv4 address 203.0.113.5 255.255.255.252
encapsulation dot1q 2000
!
/* Routing Protocol Configuration */
router rip
interface Loopback0
!
interface
!
interface
!
interface
!
interface
!
interface
!
interface
!
vrf vrf1
interface
!
interface
!
default-information originate
!
vrf vrf2
interface
!
interface
!
default-information originate
!
Verification
Router#show route vrf vrf1
Mon Jul 4 19:12:54.739 UTC
Codes: C - connected, S - static, R - RIP, B - BGP, (>) - Diversion path
O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - ISIS, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, su - IS-IS summary null, * - candidate default
U - per-user static route, o - ODR, L - local, G - DAGR, l - LISP
A - access/subscriber, a - Application route
M - mobile route, r - RPL, (!) - FRR Backup path
Gateway of last resort is not set
C 203.0.113.0/24 is directly connected, 00:07:01,
L 203.0.113.2/30 is directly connected, 00:07:01,
C 192.0.2.0/24 is directly connected, 00:05:51,
L 192.0.2.2/30 is directly connected, 00:05:51,
Router#show route vrf vrf2
Mon Jul 4 19:12:59.121 UTC
Codes: C - connected, S - static, R - RIP, B - BGP, (>) - Diversion path
O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - ISIS, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, su - IS-IS summary null, * - candidate default
U - per-user static route, o - ODR, L - local, G - DAGR, l - LISP
A - access/subscriber, a - Application route
M - mobile route, r - RPL, (!) - FRR Backup path
Gateway of last resort is not set
R 198.51.100.53/30 [120/1] via 192.0.2.1, 00:01:42,
C 203.0.113.0/24 is directly connected, 00:08:43,
L 203.0.113.5/30 is directly connected, 00:08:43,
C 192.0.2.0/24 is directly connected, 00:06:17,
L 192.0.2.5/30 is directly connected, 00:06:17,









 Feedback
Feedback