IP Service Level Agreements Technology Overview
IP SLA uses active traffic monitoring, which generates traffic in a continuous, reliable, and predictable manner to measure network performance. IP SLA sends data across the network to measure performance between multiple network locations or across multiple network paths. It simulates network data and IP services, and collects network performance information in real time. The following information is collected :
-
Response times
-
One-way latency, jitter (inter-packet delay variance)
-
Packet loss
-
Network resource availability
IP SLA performs active monitoring by generating and analyzing traffic to measure performance, either between the router or from a router to a remote IP device such as a network application server. Measurement statistics, which are provided by the various IP SLA operations, are used for troubleshooting, problem analysis, and designing network topologies.
This section covers the following topics:
Service Level Agreements
Internet commerce has grown significantly in the past few years as the technology has advanced to provide faster, more reliable access to the Internet. Many companies need online access and conduct most of their business on line and any loss of service can affect the profitability of the company. Internet service providers (ISPs) and even internal IT departments now offer a defined level of service—a service level agreement—to provide their customers with a degree of predictability.
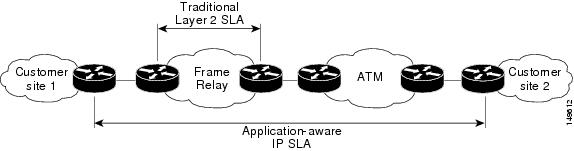
Network administrators are required to support service level agreements that support application solutions. Scope of Traditional Service Level Agreement Versus IP SLA shows how IP SLA has taken the traditional concept of Layer 2 service level agreements and applied a broader scope to support end-to-end performance measurement, including support of applications.
 Note |
|
This table lists the improvements with IP SLA over a traditional service level agreement.
|
Type of Improvement |
Description |
|---|---|
|
End-to-end measurements |
The ability to measure performance from one end of the network to the other allows a broader reach and more accurate representation of the end-user experience. |
|
Sophistication |
Statistics, such as delay, jitter, packet sequence, Layer 3 connectivity, and path and download time, that are divided into bidirectional and round-trip numbers provide more data than just the bandwidth of a Layer 2 link. |
|
Accuracy |
Applications that are sensitive to slight changes in network performance require the precision of the submillisecond measurement of IP SLA. |
|
Ease of deployment |
Leveraging the existing Cisco devices in a large network makes IP SLA easier to implement than the physical operations that are often required with traditional service level agreements. |
|
Application-aware monitoring |
IP SLA can simulate and measure performance statistics generated by applications running over Layer 3 through Layer 7. Traditional service level agreements can measure only Layer 2 performance. |
|
Pervasiveness |
IP SLA support exists in Cisco networking devices ranging from low-end to high-end routers and switches. This wide range of deployment gives IP SLA more flexibility over traditional service level agreements. |
Benefits of IP Service Level Agreements
This table lists the benefits of implementing IP SLA.
|
Benefit |
Description |
|---|---|
|
IP SLA monitoring |
Provides service level agreement monitoring, measurement, and verification. |
|
Network performance monitoring |
Measure the jitter, latency, or packet loss in the network. In addition, IP SLA provides continuous, reliable, and predictable measurements along with proactive notification. |
|
IP service network health assessment |
Verifies that the existing QoS is sufficient for the new IP services. |
|
Troubleshooting of network operation |
Provides consistent, reliable measurement that immediately identifies problems and saves troubleshooting time. |


 Feedback
Feedback