Upgrading the System
 Note |
If an interface on a router does not have a configuration and is brought up by performing no-shut operation, then upon router reload, the interface state changes to admin-shutdown automatically. |
 Note |
Ensure that you have adequate disk space. Run the fsck command to check the status of the file system, for a successful IOS XR upgrade. You must run the fsck command in the System Admin EXEC mode to install a System Admin package, and in the XR EXEC mode to install the XR package. All install commands are applicable in both the System Admin EXEC mode and in XR EXEC mode. System Admin install operations are done from XR EXEC mode. |
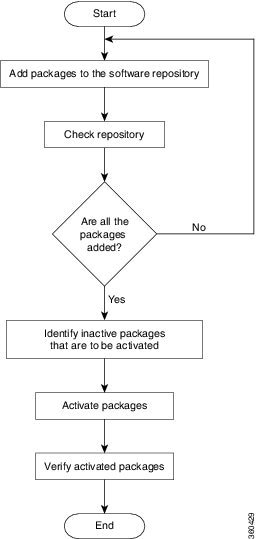
System upgrade is done by installing a base package–Cisco IOS XR Unicast Routing Core Bundle.
The filename for this bundle is ncs560-mini-x.iso.
Install this ISO image using install commands. For more information about the install process, see Workflow for Install Process.
 Caution |
Do not perform any install operations when the router is reloading. Do not reload the router during an upgrade operation. |
 Note |
If you perform a manual or automatic system reload without completing the transaction with the install commit command, the action will revert the system to the point before the install transaction commenced, including any configuration changes. Only the log is preserved for debugging. This action clears all configuration rollback points available. You will not be able to rollback to, or view, any commits made until the install rollback event. Any new commits made after the install rollback event will start from commit ID ‘1000000001’. |
 Note |
Ensure that you perform a chassis reload to enable hardware programming if a chassis upgrade through ISSU to IOS XR Release 7.6.x and later from an earlier software version. The chassis reload is mandatory, if you must enable a maximum MTU value of 9646 on applicable interfaces. |
Cisco IOS XR supports RPM signing and signature verification for Cisco IOS XR RPM packages in the ISO and upgrade images. All RPM packages in the Cisco IOS XR ISO and upgrade images are signed to ensure cryptographic integrity and authenticity. This guarantees that the RPM packages have not been tampered with and the RPM packages are from Cisco IOS XR. The private key, which is used for signing the RPM packages, is created and securely maintained by Cisco.
For more information on upgrading the system and the Cisco RPMS, see Manage Automatic Dependency chapter.


 Feedback
Feedback