Managing Scopes
This section describes how to define and configure scopes for the DHCP server. A scope consists of one or more ranges of dynamic addresses in a subnet that a DHCP server manages. You must define one or more scopes before the DHCP server can provide leases to clients. For more on listing leases and defining lease reservations for a scope, see Managing Leases.
Creating Scopes
Creating scopes is a local cluster function. Each scope needs to have the following:
- Name
- Policy that defines the lease times, grace period, and options
- Network address and subnet mask
- Range or ranges of addresses
You can configure scopes at the local cluster only. The web UI pages are different for local basic and advanced modes.
Local Basic Web UI
Procedure
| Step 1 |
From the Design menu, choose Scopes from the DHCPv4 submenu to open the List/Add DHCP Scopes page. |
||
| Step 2 |
Choose a VPN for the scope from the Settings drop-down list at the top of the web UI, if necessary. |
||
| Step 3 |
Click the Add Scopes icon in the Scopes pane, enter a scope name, enter the subnet IP address and choose a mask value from the drop-down list. |
||
| Step 4 |
If desired, choose a preconfigured class of service (client-class) for the scope from the drop-down list. |
||
| Step 5 |
Click Add DHCP Scope . |
||
| Step 6 |
Reload the DHCP server.
|
Local Advanced Web UI
Procedure
| Step 1 |
From the Design menu, choose Scopes from the DHCPv4 submenu to open the List/Add DHCP Scopes page. |
||
| Step 2 |
Choose a VPN for the scope from the Settings drop-down list at the top of the web UI, if necessary. |
||
| Step 3 |
Click the Add Scopes icon in the Scopes pane, enter a scope name, or leave it blank to use the one defined in the scope name expression of a scope template, if any (see Using Expressions in Scope Templates). In the latter case, choose the scope template. You must always enter a subnet and mask for the scope. |
||
| Step 4 |
Choose a policy for the scope from the drop-down list. The policy defaults to the default policy. |
||
| Step 5 |
Click Add DHCP Scope . |
||
| Step 6 |
Add ranges for addresses in the scope. The ranges can be any subset of the defined scope, but cannot overlap. If you enter just the host number, the range is relative to the netmask. Do not enter ranges that include the local host or broadcast addresses (usually 0 and 255). Add the range and then click Add Range . |
||
| Step 7 |
Reload the DHCP server.
|
Configuring Multiple Scopes
You can configure multiple scopes (with disjointed address ranges) with the same network number and subnet mask. By default, the DHCP server pools the available leases from all scopes on the same subnet and offers them, in a round-robin fashion, to any client that requests a lease. However, you can also bypass this round-robin allocation by setting an allocation priority for each scope (see Configuring Multiple Scopes Using Allocation Priority).
Configuring the addresses of a a single subnet into multiple scopes helps to organize the addresses in a more natural way for administration. Even though you can configure a virtually unlimited number of leases per scope, if you have a scope with several thousand leases, it can take a while to sort them. This can be a motivation to divide the leases among multiple scopes.
You can divide the leases among the scopes according to the types of leases. Because each scope can have a separate reservations list, you can put the dynamic leases in one scope that has a policy with one set of options and lease times, and all the reservations in another scope with different options and times. Note that in cases where some of the multiple scopes are not connected locally, you should configure the router (having BOOTP relay support) with the appropriate helper address.
Configuring Multiple Scopes for Round-Robin Address Allocation
By default, the DHCP server searches through the multiple scopes in a round-robin fashion. Because of this, you would want to segment the scopes by the kind of DHCP client requests made. When multiple scopes are available on a subnet through the use of secondary scopes, the DHCP server searches through all of them for one that satisfies an incoming DHCP client request. For example, if a subnet has three scopes, only one of which supports dynamic BOOTP, a BOOTP request for which there is no reservation is automatically served by the one supporting dynamic BOOTP.
You can also configure a scope to disallow DHCP requests (the default is to allow them). By using these capabilities together, you can easily configure the addresses on a subnet so that all the DHCP requests are satisfied from one scope (and address range), all reserved BOOTP requests come from a second one, and all dynamic BOOTP requests come from a third. In this way, you can support dynamic BOOTP while minimizing the impact on the address pools that support DHCP clients.
Configuring Multiple Scopes Using Allocation Priority
You can set an allocation priority among scopes instead of the default round-robin behavior described in the previous section. In this way, you can have more control over the allocation process. You can also configure the DHCP server to allocate addresses contiguously from within a subnet and control the blocks of addresses allocated to the backup server when using DHCP server failover (see Managing DHCP Failover).
A typical installation would set the allocation priority of every scope by using the allocation-priority attribute on the scope. Some installations might also want to enable the allocate-first-available attribute on their scopes, although many would not. There is a small performance loss when using allocate-first-available, so you should only use it when absolutely required.
You can control:
- A hierarchy among scopes of which should allocate addresses first.
- Whether to have a scope allocate the first available address rather than the default behavior of the least recently accessed one.
- Allocating contiguous and targeted addresses in a failover configuration for a scope.
- Priority address allocation server-wide.
- In cases where the scopes have equal allocation priorities set, whether the server should allocate addresses from those with the most or the least number of available addresses.
When there is more than one scope in a network, then the DHCP must decide which scope to allocate an IP address from when it processes a DHCPDISCOVER request from a DHCP client that is not already associated with an existing address. The algorithm that the DHCP server uses to perform this allocation is described in the following section.
Allocation Priority Algorithm
The DHCP server examines the scopes in a network one at a time to determine if they are acceptable. When it finds an acceptable scope, it tries to allocate an IP address from it to fulfill the DHCPDISCOVER request. The allocation-priority scope attribute is used to direct the DHCP server to examine the scopes in a network in a particular order, because in the absence of any allocation priority, the DHCP server examines the scopes in a round-robin order.
The image below shows an example of a network with nine scopes (which is unusual, but serves to illustrate several possibilities of using allocation priority).

Six of these scopes were configured with an allocation priority, and three of them were not. The server examines the six that were configured with an allocation priority first, in lowest to highest priority order. As the server finds an acceptable scope, it tries to allocate an IP address from it. If the server succeeds, it then finishes processing the DHCPDISCOVER request using this address. If it cannot allocate an address from that scope, it continues examining scopes looking for another acceptable one, and tries to allocate an address from it.
This process is straightforward if no scopes have the same allocation priority configured, but in the case where (as in the example in) more than one scope has the same nonzero allocation priority, then the server has to have a way to choose between the scopes of equal priority. The default behavior is to examine the scopes with equal priority starting with the one with the fewest available addresses. This uses up all of the addresses in one scope before using any others from another scope. This is the situation shown in the image above. If you enable the equal-priority-most-available DHCP server attribute, then the situation is reversed and the scope with the most available addresses is examined first when two scopes have equal priority. This spreads out the utilization of the scopes, and more or less evenly distributes the use of addresses across all of the scopes with equal allocation priority set.
You can use this equal-priority-most-available approach because of another feature in the processing of equal priority scopes. In the situation where there are two scopes of equal priority, if the DHCPDISCOVER request, for which the server is trying to allocate an address, also has a limitation-id (that is, it is using the option 82 limitation capability; see Subscriber Limitation Using Option 82), then the DHCP server tries to allocate its IP address from the same scope as that used by some existing client with the same limitation-id (if any). Thus, all clients with the same limitation-id tend to get their addresses allocated from the same scope, regardless of the number of available addresses in the scopes of equal priority or the setting of the equal-priority-most-available server attribute.
To bring this back to the equal-priority-most-available situation, you might configure equal-priority- most-available (and have several equal priority scopes), and then the first DHCP client with a particular limitation-id would get an address from the scope with the most available addresses (since there are no other clients with that same limitation-id). Then all of the subsequent clients with the same limitation-id would go into that same scope. The result of this configuration is that the first clients are spread out evenly among the acceptable, equal priority scopes, and the subsequent clients would cluster with the existing ones with the same limitation-id.
If there are scopes with and without allocation priority configured in the same network, all of the scopes with a nonzero allocation priority are examined for acceptability first. Then, if none of the scopes were found to be acceptable and also had an available IP address, the remaining scopes without any allocation priority are processed in a round-robin manner. This round-robin examination is started at the next scope beyond the one last examined in this network, except when there is an existing DHCP client with the same limitation-id as the current one sending the DHCPDISCOVER. In this case, the round-robin scan starts with the scope from which the existing client IP address was drawn. This causes subsequent clients with the same limitation-id to draw their addresses from the same scope as the first client with that limitation-id, if that scope is acceptable and has available IP addresses to allocate.
Address Allocation Attributes
The attributes that correspond to address allocation are described in the table below.
|
Attribute |
Type |
Description |
|---|---|---|
|
allocation- priority |
Scope (set or unset) |
If defined, assigns an ordering to scopes such that address allocation takes place from acceptable scopes with a higher priority until the addresses in all those scopes are exhausted. An allocation priority of 0 (the preset value) means that the scope has no allocation priority. A priority of 1 is the highest priority, with each increasing number having a lower priority. You can mix scopes with an allocation priority along with those without one. In this case, the scopes with a priority are examined for acceptability before those without a priority. If set, this attribute overrides the DHCP server priority-address- allocation attribute setting. However, if allocation-priority is unset and priority-address-allocation is enabled, then the allocation priority for the scope is its subnet address. With allocation-priority unset and priority-address-allocation disabled, the scope is examined in the default round-robin fashion. |
|
allocate-first- available |
Scope (enable or disable) |
If enabled, forces all allocations for new addresses from this scope to be from the first available address. If disabled (the preset value), uses the least recently accessed address. If set, this attribute overrides the DHCP server priority-address-allocation attribute setting. However, if unset and priority-address-allocation is enabled, then the server still allocates the first available address. With allocate-first-available unset and priority-address-allocation disabled, the scope is examined in the default round-robin fashion. |
|
failover-backup- allocation- boundary |
Scope (set or unset) |
If allocate-first-available is enabled and the scope is in a failover configuration, this value is the IP address to use as the point from which to allocate addresses to a backup server. Only addresses below this boundary are allocated to the backup server. If there are no available addresses below this boundary, then the addresses above it are allocated to the backup server. The actual allocation works down from this address, while the normal allocation for DHCP clients works up from the lowest address in the scope. If this attribute is unset or set to zero, then the boundary used is halfway between the first and last addresses in the scope ranges. If there are no available addresses below this boundary, then the first available address is used. See Figure 9 for an illustration of how addresses are allocated in a scope using this setting. |
|
priority-address- allocation |
DHCP (enable or disable) |
Provides a way to enable priority address allocation for the entire DHCP server without having to configure it on every scope. (However, the scope allocation-priority setting overrides this one.) If priority-address-allocation is enabled and the scope allocation-priority attribute is unset, then the scope subnet address is used for the allocation priority. If the scope allocate-first-available is unset, then priority address allocation is considered enabled. Of course, when exercising this overall control of the address allocation, the actual priority of each scope depends only on its subnet address, which may or may not be desired. |
|
equal-priority- most-available |
DHCP (enable or disable) |
By default, when two or more scopes with the same nonzero allocation-priority are encountered, the scope with the least available IP addresses is used to allocate an address for a new client (if that client is not in a limitation list). If equal-priority-most- available is enabled and two or more scopes have the same nonzero allocation priority, then the scope with the most available addresses is used to allocate an address for a new client (if that client is not in a limitation list). In either case, if a client is in a limitation-list, then among those scopes of the same priority, the one that contains other clients in the same list is always used. |
Allocating Addresses In Scopes
When trying to allocate an IP address from within a scope, the default action of the DHCP server is to try to allocate the least recently accessed address first, from the list of available leases. But all the operations that require accessing the lease like listing all the leases or all leases in a scope, asking for a specific lease (nrcmd> lease addr), searching leases, or modifying leases (activate, deactivate, or force available) affect the ordering of the leases in the list of available leases with the server.
Operating on a single lease places that lease at the end of the list. Listing leases causes the leases to be arranged in numerical order, making the lowest numbered lease to end up first on the available list. Other operations that require the server to access the lease, like leasequery requests also impacts the order of leases.
Thus, in general there is no way to predict which IP address within a scope is allocated at a given time. Usually this poses no difficulty, but there are times when a more deterministic allocation strategy is desired. To configure a completely deterministic address allocation strategy, you can enable the allocate-first-available attribute on a scope. This causes the available address with the lowest numeric value to be allocated for a DHCP client. Thus, the first client gets the first address in the lowest range, and the second client the second one in that range, and so on. This is shown in the image below.
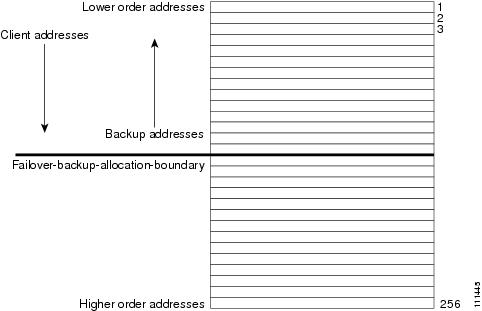
Note that there is some minor performance cost to this deterministic allocation strategy, not so much that you should not use it, but possibly enough so that you should not use it if you do not need it. When using this deterministic allocation strategy approach in a situation where the scope is in a failover relationship, the question of how to allocate the available IP addresses for the backup server comes up on the main server. By default, the address halfway between the lowest and highest ones in the scope becomes the failover-backup-allocation-boundary. The available addresses for the backup server are allocated working down from this boundary (if any addresses are available in that direction). If no address is available below this boundary, then the first available one above the boundary is used for the backup server. You can configure the failover-backup-allocation-boundary for the scope if you want to have a different address boundary than the halfway point.
You would use a deterministic allocation strategy and configure allocate-first-available in situations where you might allocate a scope with a larger number of IP addresses than you were sure you needed. you can later shrink back the ranges in the scope so as to allow moving address space to another network or server. In the nondeterministic approach, the allocated addresses are scattered all over the ranges, and it can be very hard to reconfigure the DHCP clients to free up, say, half of the scope addresses. However, if you configure allocate-first-available, then the allocated addresses tend to cluster low in the scope ranges. It is then probably simpler to remove ranges from a scope that does not need them, so that those addresses can be used elsewhere.
Editing Scopes
 Note |
You can only make changes to a scope's subnet, if there are no reservations or ranges that conflicts with the change, either in the current scope or any other scope with the same old subnet as those scopes' subnet will also be changed. |
Local Advanced Web UI
Procedure
| Step 1 |
Create a scope, as described in Creating Scopes. |
| Step 2 |
Reload the DHCP server. |
| Step 3 |
Click the name of the scope on the Scopes pane on the List/Add DHCP Scopes page to open the Edit DHCP Scope page. (If a server reload is required, a status message indicates it and you must reload first before proceeding.) |
| Step 4 |
Modify the fields or attributes as necessary. You can also modify the name of the scope. |
| Step 5 |
To edit the scope embedded policy, see Configuring Embedded Policies for Scopes. To list leases for the scope, see Viewing Leases. |
| Step 6 |
Click Save . |
| Step 7 |
Reload the DHCP server. |
CLI Commands
After you create a scope, look at the properties for all the scopes on the server, use scope list (or scope listnames , scope listbrief , scope name show , or scope name get attribute). Then:
-
To reset an attribute, use scope name set attribute=value [attribute=value ...]. For example, you can reset the name of the scope by using scope name set name =new name.
-
To enable or disable an attribute, use scope name enable attribute or scope name disable attribute.
See the scope command in the CLIGuide.html file in the /docs directory for syntax and attribute descriptions.
Related Topics
Configuring Embedded Policies for Scopes
Configuring Multiple Subnets on a Network
Enabling and Disabling BOOTP for Scopes
Setting Free Address SNMP Traps on Scopes
Staged and Synchronous Mode
New scopes or modifications to scopes can be in one of two modes—staged or synchronous:
- Staged —New scopes or modifications to existing scopes are written to the database, but not propagated to the DHCP server until the DHCP server is reloaded.
- Synchronous —Most new scopes and scope modifications (including deletions) are immediately propagated to the DHCP server (without the need for a reload). Not all scope changes are possible. For example, changing the primary subnet on a scope is not allowed (a reload is required to effect the change). Furthermore, only scope attribute changes can be propagated without a reload. For example, changes to named policies require a DHCP server reload.
If you add or modify a scope while in staged mode and then change the dhcp edit mode to synchronous, the first change in synchronous mode applies all pending changes for that scope (not just the ones made while in synchronous mode).
Local Web UI
To view the current dhcp edit mode or change the dhcp edit mode, click the Settings drop-down list at the top of the web UI and choose Session Settings . If the scope is up to date in the DHCP server, the Total synchronized scopes message appears on the List/Add DHCP Scopes page (in Advanced mode) and the Scope name status: synchronized message appears on the Edit DHCP Scope page (in both modes). If the scope is not up to date, the Scope name status: reload required message is displayed.
CLI Commands
nrcmd> scope report-staged-edits
100 Ok
example-scope: [reload-required]
Getting Scope Counts on the Server
You can view the created scopes associated with the DHCP server, hence obtain a count, in the web UI.
CLI Commands
Using the CLI, you can get an exact count of the total scopes for the DHCP server by using dhcp getScopeCount [vpn name | all ]. You can specify a VPN or all VPNs. Omitting the vpn name returns a count for the current VPN. Specifying a failover pair name returns the total scopes and networks for the failover pair. Because a failover pair definition includes explicit VPN settings in its matchlist, these counts are not limited to the current VPN only.
To create a scope, use scope name create address mask [template=template-name] [attribute=value ...]. Each scope must identify its network address and mask. When you create the scope, Cisco Prime Network Registrar places it in its current virtual private network (VPN), as defined by session set current-vpn . You cannot change the VPN once you set it at the time of creation of the scope.
To set a policy for the scope, use scope name set policy .
To add a range of IP addresses to the scope, use scope name addRange start end.
Configuring Embedded Policies for Scopes
When you create a scope, Cisco Prime Network Registrar automatically creates an embedded policy for it. However, the embedded policy has no associated properties or DHCP options until you enable or add them. An embedded policy can be useful, for example, in defining the router for the scope. As Types of Policies describes, the DHCP server looks at the embedded policy of a scope before it looks at its assigned, named policy.
 Note |
If you delete a scope policy, you remove all of its properties and attributes. |
Local Advanced Web UI
Procedure
| Step 1 |
Create a scope, as described in Creating Scopes. |
| Step 2 |
Click the name of the scope on the Scopes pane on the List/Add DHCP Scopes page to open the Edit DHCP Scope page. |
| Step 3 |
Click Create New Embedded Policy to create a new embedded policy, or Edit Existing Embedded Policy if there is already an existing one, to open the Edit DHCP Embedded Policy for Scope page. |
| Step 4 |
Modify the fields, options, and attributes on this page. If necessary, unset attributes. |
| Step 5 |
Click Save . |
CLI Commands
Create a scope first. In the CLI, scope-policy uses the same syntax as policy , except that it takes the scope name as an argument. Then, to:
-
Determine if there are any embedded property values already set for a scope, use scope-policy scope-name show .
-
Enable or disable an attribute, use scope-policy scope-name enable attribute or scope-policy scope-name disable attribute.
-
Set and unset attributes, use scope-policy scope-name set attribute=value [attribute=value...] and scope-policy scope-name unset attribute.
-
List, set, and unset vendor options (see Using Standard Option Definition Sets).
Configuring Multiple Subnets on a Network
Cisco Prime Network Registrar supports multiple logical subnets on the same network segment, which are also called secondary subnets. With several logical subnets on the same physical network, for example, 192.168.1.0/24 and 192.168.2.0/24, you might want to configure DHCP so that it offers addresses from both pools. By pooling addresses this way, you can increase the available number of leases.
To join two logical subnets, create two scopes, and elect one to be primary and the other to be a secondary. After you configure the secondary subnet, a new client on this physical network gets a lease from one or the other scope on a round-robin basis.
Local Advanced Web UI
Procedure
| Step 1 |
Create a scope (see Creating Scopes) that you will make a secondary scope. |
| Step 2 |
Click the name of the scope on the Scopes pane on the List/Add DHCP Scopes page to open the Edit DHCP Scope page. |
| Step 3 |
To make this a secondary scope, enter the network address of the subnet of the primary scope in the Primary Subnet attribute field in the Edit DHCP Scope page. It is common practice for the primary-subnet to correspond directly to the network address of the primary scope or scopes. For example, with examplescope1 created in the 192.168.1.0/24 network, associate examplescope2 with it using primary-subnet =192.168.1.0/24. (Note that if Cisco Prime Network Registrar finds that the defined subnet has an associated scope, it ignores the mask bit definition and uses the one from the primary scope, just in case they do not match.) However, the primary-subnet can be a subnet address that does not have a scope associated with it. |
| Step 4 |
Click Save . |
| Step 5 |
Restart or reload the server. |
CLI Commands
To assign the secondary scope to a primary one, use scope name set primary-subnet =value, then reload the server.
To remove the secondary scope, use scope name unset primary-subnet . When setting the primary-subnet attribute, include the number bits for the network mask, using slash notation. For example, represent the network 192.168.1.0 with mask 255.255.255.0 as 192.168.1.0/24. The mask bits are important. If you omit them, a /32 mask (single IP address) is assumed.
Enabling and Disabling BOOTP for Scopes
The BOOTstrap Protocol (BOOTP) was originally created for loading diskless computers. It was later used to allow a host to obtain all the required TCP/IP information so that it could use the Internet. Using BOOTP, a host can broadcast a request on the network and get the data required from a BOOTP server. The BOOTP server listens for incoming requests and generates responses from a configuration database for the BOOTP clients on that network. BOOTP differs from DHCP in that it has no concept of lease or lease expiration. All addresses that a BOOTP server allocates are permanent.
You can configure the Cisco Prime Network Registrar DHCP server to act like a BOOTP server. In addition, although BOOTP normally requires static address assignments, you can choose either to reserve addresses (and use static assignments) or have addresses dynamically allocated (known as dynamic BOOTP).
When you need to move or decommission a BOOTP client, you can reuse its lease simply by forcing lease availability. See Forcing Lease Availability.
Local Advanced Web UI
On the Edit DHCP Scope page, under BootP Settings, enable the bootp attribute for BOOTP, or the dynamic-bootp attribute for dynamic BOOTP. They are disabled by default. Then click Save .
CLI Commands
Use scope name enable bootp to enable BOOTP, and scope name enable dynamic-bootp to enable dynamic BOOTP. Reload the DHCP server (if in staged dhcp edit mode).
Setting Scopes to Renew-Only
You can control whether to allow existing clients to re-acquire their leases, but not to offer any leases to new clients. A renew-only scope does not change the client associated with any of its leases, other than to allow a client currently using an available IP address to continue to use it.
Local Advanced Web UI
On the Edit DHCP Scope page, under Miscellaneous Settings, explicitly enable the renew-only attribute. Then click Save .
CLI Commands
Use scope name enable renew-only to set a scope to renew-only.
Setting Free Address SNMP Traps on Scopes
You can set SNMP traps to capture unexpected free address events by enabling the traps and setting the low and high thresholds for a scope. You can also set traps based on networks and selection tags instead of scopes.
When setting the threshold values, it is advisable to maintain a small offset between the low and high values, as described in the "Simple Network Management" section in Cisco Prime Network Registrar 11.1 Administration Guide). The offset can be as little as 5%, for example, a low value of 20% and a high value of 25%, which are the preset values.
Here are some variations on how you can set the server and scope values for these attributes:
- Get each scope to trap and reset the free address values based on the server settings, as long as at least one recipient is configured.
- Disable the traps at the scope level or specify different percentages for each scope.
- Disable the traps globally on the server, but turn them on for different scopes.
- Set the traps at the network level or selection tags level.
Local Advanced and Regional Web UI
Procedure
| Step 1 |
To create a trap configuration, from the Deploy menu, choose Traps under the DHCP submenu to open the List/Add Trap Configurations page. |
| Step 2 |
Click the Add Traps icon, enter a name for the trap configuration, choose scope from the Mode drop-down list, and enter the low and high threshold values (they are 20% and 25%, respectively, by default). Click Add AddrTrapConfig . (You can go back to edit these values if you need to.) |
| Step 3 |
Edit the created scope to which you want to apply the threshold settings. Under SNMP Trap Settings, enter the name of the trap in the free-address-config attribute field. Click Save . |
| Step 4 |
In the regional web UI, you can pull replica trap configurations and push trap configurations to the local cluster on the List/Add Trap Configurations page. You can also reclaim trap configurations. |
CLI Commands
Use addr-trap name create to add a trap configuration. To set the thresholds, use the addr-trap name set method (or include the threshold settings while creating the trap). For example:
nrcmd> addr-trap trap-1 create
nrcmd> addr-trap trap-1 set low-threshold
nrcmd> addr-trap trap-1 set high-threshold
To set the free-address trap, use scope name set free-address-config= trap-name. For example:
nrcmd> scope scope-1 set free-address-config=trap-1
-
addr-trap < name | all > pull < ensure | replace | exact > cluster-name [-report-only | -report]
-
addr-trap < name | all > push < ensure | replace | exact > cluster-list [-report-only | -report]
-
addr-trap name reclaim cluster-list [-report-only | -report]
Disabling DHCP for Scopes
You can disable DHCP for a scope if you want to use it solely for BOOTP. See Enabling and Disabling BOOTP for Scopes. You can also temporarily deactivate a scope by disabling DHCP, but deactivation is more often used if you are enabling BOOTP. See Deactivating Scopes.
Local Advanced Web UI
On the Edit DHCP Scope page, under BootP Settings, disable the dhcp attribute and enable the bootp attribute and then click Save .
CLI Commands
Use scope name disable dhcp to disable DHCP. You should also enable BOOTP and reload the server (if in staged dhcp edit mode).
Deactivating Scopes
You might want to temporarily deactivate all the leases in a scope. To do this, you must disable both BOOTP and DHCP for the scope.
Local Advanced Web UI
On the Edit DHCP Scope page, under Miscellaneous Settings, explicitly enable the deactivated attribute. Then click Save .
CLI Commands
Use scope name enable deactivated to disable BOOTP and DHCP for the scope. Reload the DHCP server (if in staged dhcp edit mode).
Removing Scopes
 Caution |
Although removing a scope from a DHCP server is easy to do, be careful. Doing so compromises the integrity of your network. There are several ways to remove a scope from a server, either by re-using or not re-using addresses, as described in the following sections. |
DHCP, as defined by the IETF, provides an address lease to a client for a specific time (defined by the server administrator). Until that time elapses, the client is free to use its leased address. A server cannot revoke a lease and stop a client from using an address. Thus, while you can easily remove a scope from a DHCP server, the clients that obtained leases from it can continue to do so until it expires. This is true even if the server does not respond to their renewal attempts, which happens if the scope was removed.
This does not present a problem if the addresses you remove are not reused in some way. However, if the addresses are configured for another server before the last lease expires, the same address might be used by two clients, which can destabilize the network.
Cisco Prime Network Registrar moves the leases on the removed scope to an orphaned leases pool. When creating a scope, orphaned leases are associated with appropriate scopes.
Removing Scopes if Not Reusing Addresses
You can remove scopes if you are not reusing addresses.
Local Web UI
If you are sure you do not plan to reuse the scope, on the Manage Scopes or List/Add DHCP Scopes page, click the Delete Scopes icon in the Scopes pane after selecting the name, and confirm or cancel the deletion.
CLI Commands
Be sure that you are not immediately planning to reuse the addresses in the scope, then use scope name delete to delete it.
Removing Scopes if Reusing Addresses
If you want to reuse the addresses for a scope you want to remove, you have two alternatives:
- If you can afford to wait until all the leases in the scope expire —Remove the scope from the server, then wait for the longest lease time set in the policy for the scope to expire. This ensures that no clients are using any addresses from that scope. You can then safely reuse the addresses.
- If
you
cannot
afford
to
wait
until
all
the
leases
in
the
scope
expire —Do not remove the scope. Instead, deactivate it. See Deactivating Scopes. Unlike a removed scope, the server refuses all clients’ renewal requests, which forces many of them to request a new lease.
This moves these clients more quickly off the deactivated lease than for a removed scope.
You can use the ipconfig utility in Windows to cause a client to release (/release ) and re-acquire (/renew ) its leases, thereby moving it off a deactivated lease immediately. You can only issue this utility from the client machine, which makes it impractical for a scope with thousands of leases in use. However, it can be useful in moving the last few clients in a Windows environment off deactivated leases in a scope.

 Feedback
Feedback