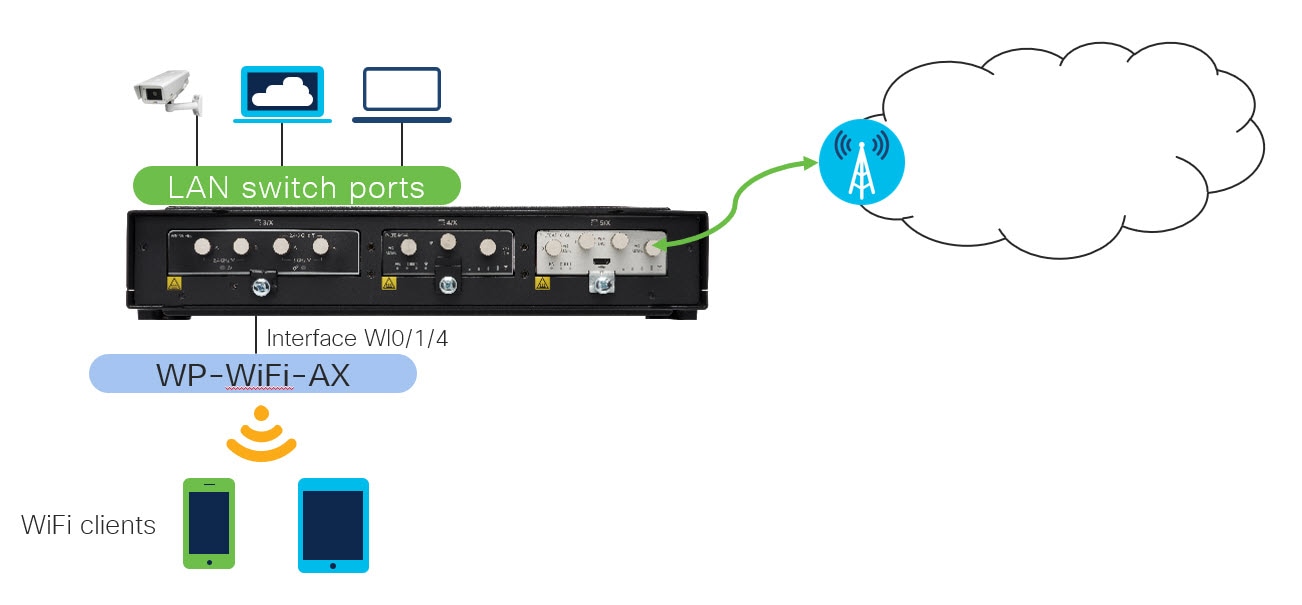
The following are examples of Root AP radio configuration when uWGB as uplink backhaul.
WIFI module uWGB configuration:
=============================
AP6879.0974.F728#sh running-config
AP Name : AP6879.0974.F728
AP Mode : WorkGroupBridge
CDP State : Enabled
Watchdog monitoring : Enabled
SSH State : Enabled
AP Username : admin
Session Timeout : 0
WGB Trace : Disabled
Syslog Host : 0.0.0.0
Radio and WLAN-Profile mapping:-
====================================
Radio ID Radio Mode SSID-Profile SSID
Authentication
0 RootAP root_wlan root_wlan
OPEN
1 UWGB Test Test
OPEN
Radio configurations:-
===============================
Radio Id : 0
Admin state : ENABLED
Mode : RootAP
Spatial Stream : AUTO
Mgmt Frame Retries : 15
Channel(Band) : 1 (20)
Beacon Period : 100 mSec
Tx Power : 1
802.11ac : Disabled
802.11ax : Enabled
802.11n : Enabled
Encryption mode : AES128
Radio Id : 1
Admin state : ENABLED
Mode : UWGB
Spatial Stream : AUTO
Mgmt Frame Retries : 15
Uclient mac : C014.FE60.EF8D
Current state : UWGB
UClient timeout : 0 Sec
Dot11 type : 11ax
11v BSS-Neighbor : Disabled
A-MPDU priority : 0x3f
A-MPDU subframe number : 255
RTS Protection : 2347(default)
Rx-SOP Threshold : AUTO
Radio profile : NA
Encryption mode : AES128
List of Root-AP SSID-Profiles:
========================================
Radio id : 0, SSID-Profile_8 : root_wlan
WGB specific configuration:-
====================================
WGB Radio Id : NA
Mode State : NA
SSID Profile : NA
UWGB Radio Id : 1
Mode Enable : Enable
SSID Profile : Test
Uclient MAC Address: C014.FE60.EF8D
Password Policy configured:-
====================================
password policy : Enable
password minimum length : 8
password lifetime : Disable
Upper Case Required : 1
Lower Case Required : 1
Digit Required : 1
Special Character Required : 1
Rx Beacon Missing Action : Enable
Rx Beacon Missing Count : 100
Packet retries Action : Reconnect
Packet retries Value : 64
RSSI Threshold Value : 70 dBm
Threshold timeout : 5 Sec
HSR-Scan status : Disable
Auth response timeout : 5000 Msec
Assoc response timeout : 5000 Msec
11v neighbor query timeout : 10 sec
WGB channel scan timeout : 20 Msec
Dhcp response timeout : 60 Sec
EAP timeout : 3 sec
Bridge table aging-time : 300 Sec
Probe pak data rate type : NA
Probe pak data rate : 0
Antenna Band Mode : Dual
Broadcast tagging : Disable
Wired Client 802.1x Auth : Disable
IGMP querier IP address : ::
Offchan scan status : Disable
Total configurations size on different structure:-
=====================================================
Total channels : 0
Total SSID-Profiles : 3
Total Root-AP SSID-Profile : 1
Total EAP Profiles : 0
Total QOS Profiles : 0
Total dot1x credentials : 0
Total PKI truspoints : 0
Total bridge groups : 0
Total SSID profiles configured are:
===========================================
SSID-Profile : Test
SSID Name : Test
SSID Profile path : /data/platform/wbridge/Test
Auth type : OPEN
DTIM Period : 1
QOS profile :
SSID-Profile : root_wlan
SSID Name : root_wlan
SSID Profile path : /data/platform/wbridge/root_wlan
Auth type : OPEN
DTIM Period : 1
QOS profile :
L2NAT Configuration are:
====================================
Status: disabled
Default Vlan: 0
The Number of L2nat Rules: 0
Dir Inside Outside Vlan
Ethernet Port Native VLAN Configuration are:
====================================
Ethernet Port: 0
Status: disabled
Native VLAN ID: 0
Ethernet Port: 1
Status: disabled
Native VLAN ID: 0
Total QoS Mapping profiles configured are:
===========================================
Number of QoS Mapping Profiles: 0
Configuration command list:
============================
### WGB Running config - Hostname: AP6879.0974.F728 ###
configure ap management add username admin password $1$$khxfBj0qAAV4gFMFboJcg. s
ecret $1$$khxfBj0qAAV4gFMFboJcg.
configure ssid-profile Test ssid Test authentication open
configure ssid-profile root_wlan ssid root_wlan authentication open
configure dot11Radio 1 mode uwgb C014.FE60.EF8D ssid-profile Test
configure dot11Radio 1 enable
configure wgb mobile period 5 70
configure dot11Radio 0 mode root-ap
configure dot11Radio 0 wlan add root_wlan 8 vlan 10
configure dot11Radio 0 encryption mode ciphers aes-ccm
configure dot11Radio 0 antenna ab-antenna
configure dot11Radio 0 channel 7 20
configure dot11Radio 0 802.11ac disable
configure dot11Radio 0 tx-power 1
configure dot11Radio 0 enable
configure dot11Radio 1 encryption mode ciphers aes-ccm
configure dot11Radio 1 tx-power 1

 Feedback
Feedback