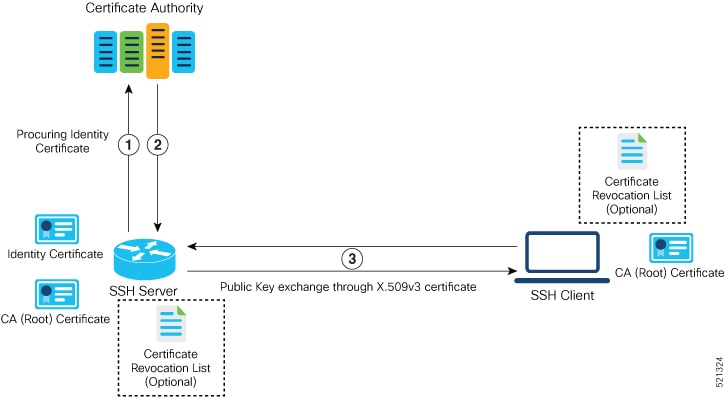
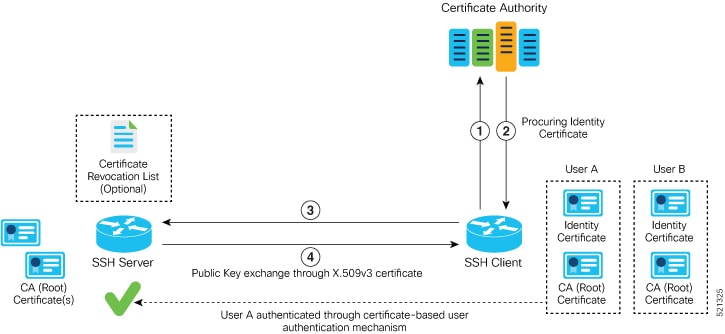
To enable X.509v3 certificate-based authentication for SSH, these tasks for server and user authentication:
Server Authentication:
-
Configure the list of host key algorithms—With this configuration, the SSH server decides the list of host keys to be offered
to the client. In the absence of this configuration, the SSH server sends all available algorithms to the user as host key
algorithms. The SSH server sends these algorithms based on the availability of the key or the certificate.
-
Configure the SSH trust point for server authentication—With this configuration, the SSH server uses the given trust point
certificate for server authentication. In the absence of this configuration, the SSH server does not send x509v3-ssh-rsa as a method for server verification. This configuration is not VRF-specific; it is applicable to SSH running in all VRFs.
The above two tasks are for server authentication and the following ones are for user authentication.
User Authentication:
-
Configure the trust points for user authentication—With this configuration, the SSH server uses the given trust point for
user authentication. This configuration is not user-specific; the configured trust points are used for all users. In the absence
of this configuration, the SSH server does not authenticate using certificates. This configuration is not specific to a VRF;
it is applicable to SSH running in all VRFs.
You can configure up to ten user trust points.
-
Specify the username to be picked up from the certificate—This configuration specifies which field in the certificate is to be considered as the
username . The common-name from the subject name or the user-principle-name(othername) from the subject alternate name , or both can be configured.
-
Specify the maximum number of authentication attempts allowed by the SSH server—The value ranges from 4 to 20. The default
value is 20. The server closes the connection if the number of user attempts exceed the configured value.
-
AAA authentication configuration—The AAA configuration for public key is the same as that for the regular or keyboard-interactive
authentication, except that it mandates local method in the authentication method list.
Configuration Example
In this example, the x509v3-ssh-rsa is specified as the allowed host key algorithm to be sent to the client. Similarly, you can configure other algorithms, such
as ecdsa-sha2-nistp521, ecdsa-sha2-nistp384, ecdsa-sha2-nistp256, ssh-rsa , and ssh-dsa .
/* Configure the lits of host key algorithms */
Router#configure
Router(config)#ssh server algorithms host-key x509v3-ssh-rsa
Router(config)#commit
/* Configure the SSH trustpoint for server authentication */
Router#configure
Router(config)#ssh server certificate trustpoint host tp1
Router(config)#commit
/* Configure the trustpoints to be used for user authentication */
Router#configure
Router(config)#ssh server trustpoint user tp1
Router(config)#ssh server trustpoint user tp2
Router(config)#commit
/* Specifies the username to be picked up from the certificate.
In this example, it specifies the user common name to be picked up from the subject name field */
Router#configure
Router(config)#ssh server certificate username common-name
Router(config)#commit
/* Specifies the maximum authentication limit for the SSH server */
Router#configure
Router(config)#ssh server max-auth-limit 5
Router(config)#commit
/* AAA configuration for local authentication with certificate and
remote authorization with TACACS+ or RADIUS */
Router#configure
Router(config)#aaa authentication login default group tacacs+ local
Router(config)#aaa authorization exec default group radius group tacacs+
Router(config)#commit
Running Configuration
ssh server algorithms host-key x509v3-ssh-rsa
!
ssh server certificate trustpoint host tp1
!
ssh server trustpoint user tp1
ssh server trustpoint user tp2
!
ssh server certificate username common-name
!
ssh server max-auth-limit 5
!
Verification of Certificate-based Authentication for SSH
You can use the show ssh server command to see various parameters of the SSH server. For certificate-based authentication for SSH, the Certificate Based field displays Yes . Also, the two new fields, Host Trustpoint and User Trustpoints , display the respective trust point names.
Router#show ssh server
Wed Feb 19 15:23:38.752 IST
---------------------
SSH Server Parameters
---------------------
Current supported versions := v2
SSH port := 22
SSH vrfs := vrfname:=default(v4-acl:=, v6-acl:=)
Netconf Port := 830
Netconf Vrfs := vrfname:=default(v4-acl:=, v6-acl:=)
Algorithms
---------------
Hostkey Algorithms := x509v3-ssh-rsa, ecdsa-sha2-nistp521,ecdsa-sha2-nistp384,ecdsa-sha2-nistp256,ssh-rsa,ssh-dsa
Key-Exchange Algorithms := ecdh-sha2-nistp521,ecdh-sha2-nistp384,ecdh-sha2-nistp256,diffie-hellman-group14-sha1
Encryption Algorithms := aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
Mac Algorithms := hmac-sha2-512,hmac-sha2-256,hmac-sha1
Authetication Method Supported
------------------------------------
PublicKey := Yes
Password := Yes
Keyboard-Interactive := Yes
Certificate Based := Yes
Others
------------
DSCP := 16
Ratelimit := 60
Sessionlimit := 100
Rekeytime := 60
Server rekeyvolume := 1024
TCP window scale factor := 1
Backup Server := Enabled, vrf:=default, port:=11000
Host Trustpoint := tp1
User Trustpoints := tp1 tp2
You can use the show ssh session details command to see the chosen algorithm for an SSH session:
Router#show ssh session details
Wed Feb 19 15:33:00.405 IST
SSH version : Cisco-2.0
id key-exchange pubkey incipher outcipher inmac outmac
----------------------------------------------------------------------------------------------------
Incoming Sessions
1 ecdh-sha2-nistp256 x509v3-ssh-rsa aes128-ctr aes128-ctr hmac-sha2-256 hmac-sha2-256
Similarly, you can use the show ssh command to verify the authentication method used. In this example, it shows as x509-rsa-pubkey :
Router#show ssh
Sun Sep 20 18:14:04.122 UTC
SSH version : Cisco-2.0
id chan pty location state userid host ver authentication connection type
----------------------------------------------------------------------------------------------------------------------------
Incoming sessions
4 1 vty0 0/RP0/CPU0 SESSION_OPEN 9chainuser 10.105.230.198 v2 x509-rsa-pubkey Command-Line-Interface
Outgoing sessions
SYSLOGS
You can observe relevant SYSLOGS on the router console in various scenarios listed here:
-
On successful verification of peer certificate:
RP/0/RP0/CPU0:Aug 10 15:01:34.793 UTC: locald_DLRSC[133]: %SECURITY-PKI-6-LOG_INFO : Peer certificate verified successfully
-
When user certificate CA is not found in the trust point:
RP/0/RP0/CPU0:Aug 9 22:06:43.714 UTC: locald_DLRSC[260]: %SECURITY-PKI-3-ERR_GENERAL : issuer not found in trustpoints configured
RP/0/RP0/CPU0:Aug 9 22:06:43.714 UTC: locald_DLRSC[260]: %SECURITY-PKI-3-ERR_ERRNO : Error:='Crypto Engine' detected the 'warning' condition 'Invalid trustpoint or trustpoint not exist'(0x4214c000), cert verificationn failed
-
When there is no CA certificate or host certificate in the trust point:
RP/0/RP1/CPU0:Aug 10 00:23:28.053 IST: SSHD_[69552]: %SECURITY-SSHD-4-WARNING_X509 : could not get the host cert chain, 'sysdb' detected the 'warning' condition 'A SysDB client tried to access a nonexistent item or list an empty directory', x509 host auth will not be used
RP/0/RP1/CPU0:Aug 10 00:23:30.442 IST: locald_DLRSC[326]: %SECURITY-PKI-3-ERR_ERRNO : Error:='Crypto Engine' detected the 'warning' condition 'Invalid trustpoint or trustpoint not exist'(0x4214c000), Failed to get trustpoint name from
How to Disable X.509v3 Certificate-based Authentication for SSH
-
Server Authentication — You can disable X.509v3 certificate-based server authentication for SSH by using the ssh server algorithms host-key command. From the list of auto-generated host-key pairs algorithms on the SSH server, this command configures allowed SSH
host-key pair algorithms. Hence, if you have this configuration without specifying the x509-ssh-rsa option in the preceding command, it is equivalent to disabling the X.509v3 certificate-based server authentication for the
SSH server.
-
User Authentication — You can remove the user trust point configuration (ssh server trustpoint user ) so that the SSH server does not allow the X.509v3 certificate-based authentication.
Failure Modes for X.509v3 Certificate-based Authentication for SSH
If the ssh server certificate trustpoint host configuration is missing, or if the configuration is present, but the router certificate is not present under the trust point,
then the SSH server does not add x509-ssh-rsa to the list of supported host key methods during key exchange.
Also, the user authentication fails with an error message if:
-
User certificate is in an incorrect format.
-
The chain length of the user certificate is more than the maximum limit of 9.
-
Certificate verification fails due to any reason.
Associated Commands
-
ssh server algorithms hostkey
-
ssh server certificate username
-
ssh server max-auth-limit
-
ssh server trustpoint host
-
ssh server trustpoint user
-
show ssh server
-
show ssh session details





 Feedback
Feedback