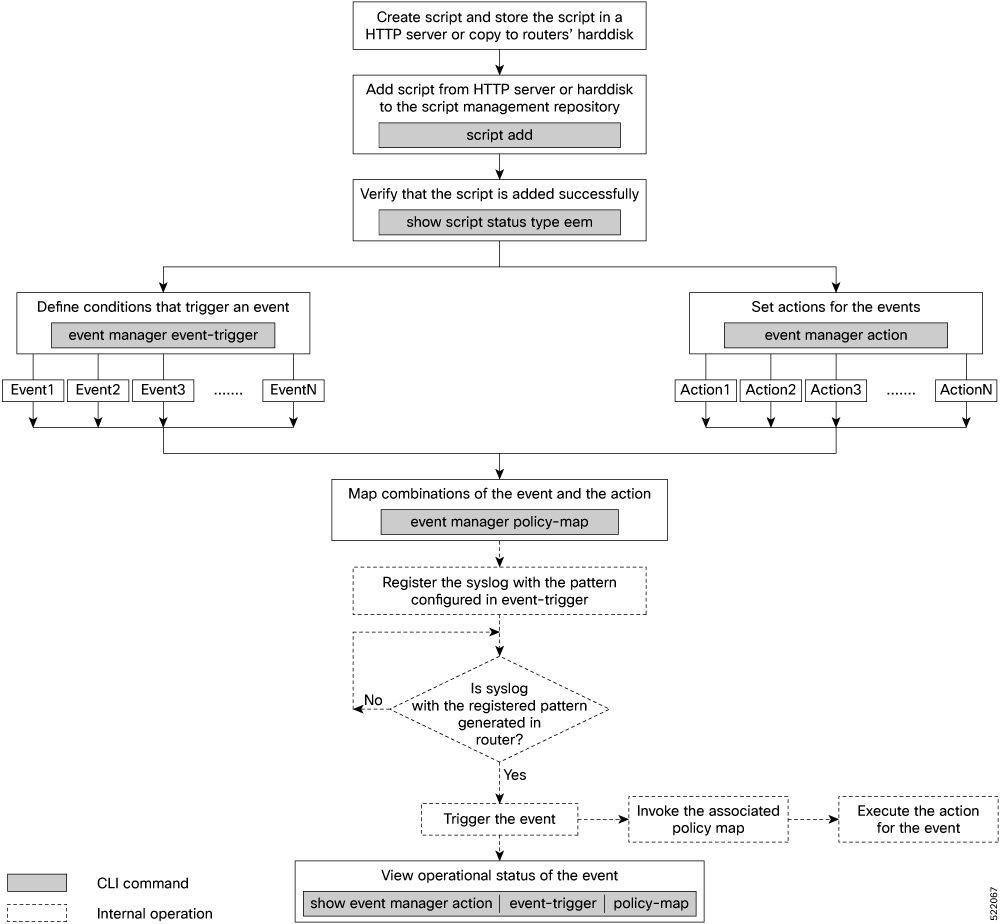
Workflow to Run Event Scripts
Complete the following tasks to provision eem scripts:
-
Download the script—Store the eem script on an HTTP server or copy to the harddisk of the router. Add the eem script from the HTTP server or harddisk to the script management repository on the router using the script add eem command.
-
Define events—Configure the events with the trigger conditions using the event manager event-trigger command.
-
Define actions to the events—Setup the actions that must be performed in response to an event using event manager action command.
-
Create policy map—Put together the events and the actions in a policy map using event manager policy-map command.

Note
An eem script is invoked automatically when the event occurs. With the event, the event-trigger invokes the corresponding policy-map to implement the actions in response to the event.
-
View operational status of the event—Retrieve the operational data using the show event-manager action | event-trigger | policy-map command.
The following image shows a workflow diagram representing the steps involved in using an event script:
Download the Script to the Router
To manage the scripts, you must add the scripts to the script management repository on the router. A subdirectory is created for each script type. By default, this repository stores the downloaded scripts in the appropriate subdirectory based on script type.
| Script Type | Download Location |
|---|---|
|
config |
harddisk:/mirror/script-mgmt/config |
|
exec |
harddisk:/mirror/script-mgmt/exec |
|
process |
harddisk:/mirror/script-mgmt/process |
|
eem |
harddisk:/mirror/script-mgmt/eem |
-
Method 1: Add script from a server
-
Method 2: Copy script from external repository to harddisk using scp or copy command
In this section, you learn how to add eem-script.py script to the script management repository.
Procedure
| Step 1 |
Add the script to the script management repository on the router using one of the two options:
|
||
| Step 2 |
Verify that the scripts are downloaded to the script management repository on the router. Example:eem-script.py is copied to harddisk:/mirror/script-mgmt/eem directory on the router.
|
Define Trigger Conditions for an Event
You define the event, and create a set of instructions that trigger a match to this event. You can create multiple events.
Before you begin
Ensure that the script is added to the script management repository. See Download the Script to the Router.
Procedure
| Step 1 |
Register the event. Example:You can configure more options to trigger an event:
|
||||||||||||||||
| Step 2 |
Configure the type for the event.
|
Example
all, where only pattern match is considered for the event to trigger.
Router(config)#event manager event-trigger eventT10
type syslog pattern "<pattern-to-match>" severity <value>Router(config)#event manager event-trigger eventT10
rate-limit seconds <time-in-seconds>
type syslog pattern "<pattern-to-match>" severity <value>
alert Syslog priority 1
critical Syslog priority 2
debug Syslog priority 7 (lowest)
emergency Syslog priority 0 (highest)
error Syslog priority 3
info Syslog priority 6
notice Syslog priority 5
warning Syslog priority 4
The following example shows a syslog pattern L2-BM-6-ACTIVE with severity value critical:
Router(config)#event manager event-trigger eventT10
type syslog pattern "L2-BM-6-ACTIVE" severity infoL2-BM-6-ACTIVE and severity value info match.
Create Actions for Events
Define the actions that must be taken when an event occurs.
Before you begin
Ensure that the following prerequisites are met before you configure the action:
Procedure
| Step 1 |
Set the event action. Example: |
| Step 2 |
Define the type of action. For example, the action is a Python script. Example: |
| Step 3 |
Configure the maximum run time of the script for the event. Example:The default value is 20 seconds. |
| Step 4 |
Configure the checksum for the script. This configuration is mandatory. Every script is associated with a checksum hash value. This value ensures the integrity of the script, and that the script is not tampered. The checksum is a string of numbers and letters that act as a fingerprint for script. |
| Step 5 |
Enter the username for the script to execute. Example: |
Create a Policy Map of Events and Actions
|
Feature Name |
Release Information |
Description |
|---|---|---|
|
Add Multiple Events In a Policy Map With a Single EEM Script |
Release 7.5.1 |
With this feature, you can add multiple events to a policy map with boolean (AND or OR) correlation. EEM triggers the script when the correlation defined in the policy map for the events is true. Using EEM scripts, you can create a logical correlation of events in the policy map and configure multiple actions for detectors such as timer, object-tracking, and telemetry events via sensor path. |
Create a policy to map events and actions. You can configure a policy that associates multiple actions with an event or use
the same action with different events. The policy can be triggered if an event or multiple events occur at a specified number of times within a specified period
of time. The occurrence and period are optional parameters. You can add multiple events to a policy-map with boolean (AND or OR) correlation. EEM triggers the
script when correlation defined in the policy-map for the events is true. For example, a multi-event policy-map for event1 and event2 with event1 AND event2 boolean operation is triggered only when both event1 and event2 are true.
Before you begin
Ensure that the following prerequisites are met before you create a policy map:
Procedure
| Step 1 |
Create a policy map. Example:
|
||
| Step 2 |
Define the action that must be implemeted when the event occurs. Maximum of 5 actions can be mapped to a policy map. Example: |
||
| Step 3 |
Configure the name of the event or multiple events to trigger the policy-map. Example: |
View Operational Status of Event Scripts
Retrieve the operational status of events, actions and policy maps.
Before you begin
Ensure that the following prerequisites are met before you trigger the event:
Procedure
| Step 1 |
Run the show event manager event-trigger all command to view the summary of basic data of all events that are configured. Example:Use the show event manager event-trigger all detailed command to view the details about the match criteria that you configured, severity level, policies mapped to the events and so on. |
| Step 2 |
Run the show event manager policy-map all command to view the summary of all the configured policy maps. Example: |
| Step 3 |
Run the show event manager action <action-name> detailed commad to view the details of an action. Example:Use the show event manager action all and show event manager action all detailed command to view the summary and details about all the configured actions. |
 Feedback
Feedback