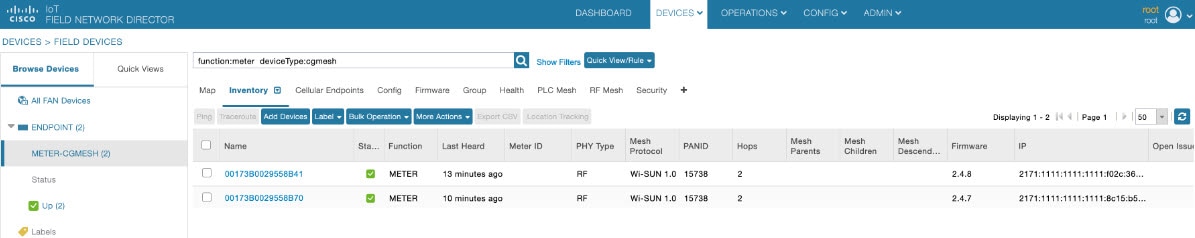
An Endpoint Operator can manage Itron Bridge Meters such as ITRON30 as a cg-mesh device type (METER-CGMESH) using IoT-FND.
This meter type was previously run in RFLAN mode.

Note
|
Only Root and Endpoint Operators (RBAC) can see and perform the endpoint operations and scheduling for the Channel Notch feature.
|
To manage an Itron Bridge Meter in cg-mesh mode, an Endpoint Operator (RBAC) must convert the RFLAN meter to a cg-mesh device
type and upgrade all cg-mesh firmware to cg-mesh 5.6.x.
After successful registration, the channel notch settings (in the bootstrap config.bin) must be pushed to all modes by the
Endpoint Operator as soon as possible to be compliant with local regulations.
There are two new properties associated with this feature:
After successful registration, the channel notch settings (in the bootstrap config.bin file) must be pushed to all nodes by
the Endpoint Operator.
There are two new properties for this feature:
-
channelNotchMaxAttempts = 20. This property defines the maximum attempts allowed to send the configuration and schedule information
to all the endpoints.
-
channelNotchSettingEnabled = true. This property allows you to enable the channel notch feature.
You can define up to four pairs of Notch Range Start and End Channels on the Channel Notch Settings page. These channel ranges
must have increasing channel numbers for each range and cannot have any overlapping ranges. The ranges are blacklist ranges
which are used to prohibit nodes from using the ranges of channels.
The page displays a list of the Config groups along with the details of group members and endpoints of each subnet. To initiate
a Config push of current channel settings to the endpoints for all routers in the selected router config groups, you can press
the Push Channel Config button. As the process of the channel config push progresses, the associated router config groups
nested tables show the updated, remaining endpoint count and endpoint state of all endpoints.
The endpoints respond with a TLV 366 with the appropriate values to the channel notch config push, TLV 365.
Two additional properties are available:
-
channelNotchMaxAttempts = 20: This setting defines the maximum attempts that the software will attempt to send the config
and schedule information to all of the endpoints.
-
allowNewNotchSettings=true: This setting allows notch settings to be changed at will and defines those setting that will
be used in the config push.



Note
|
Before you can schedule activation of a Channel Notch Config, the router config groups must have successfully received their
channel notch configuration. Note: Before you can schedule activation of a Channel Notch Config, the router config groups
must have successfully received their channel notch configuration.
|
When you select the Schedule Channel Notch Config button, a pop up panel appears for you to set a reload time (day and time)
that the Channel Notch Config will be activated.
Additionally, at the same time of the Channel Notch activation, you must also change the Channel Notch Config of the corresponding
routers through Config Push.




To enable PAN-wide nodes to use the new Channel Notch at the same time, the node employs the following three mechanisms at
the same time to guarantee that the new configuration is enabled:
-
Supports scheduling of time that the new Channel Notch Settings should take effect by using TLV 367. Note that the new Channel
Notch Settings are stored in the platform flash. When the scheduled time arrives, the setting is copied to the device flash
and then the node is rebooted to load the new config. If the node attempts to reboot before the scheduled time, the node will
continue to wait until the scheduled time.
-
CGR sends an async beacon which includes the excluded channel range (ECR) through the new Channel Hopping Schedule.
-
When the nodes have been offline for five days, nodes will immediately enable the new Channel Notch Settings.
After endpoints have completed the initial enrollment and joined the mesh network, the endpoints may need to re-enroll the
Utility IDevID and/or the LDEVID due to certificate expiration or proactive refresh of the certificates. FND 4.7 supports
on-demand and auto re-enrollment. This action is seen in the Device Configuration page for a group of devices and on the Device
Detail page for a single device.












































































































































 Feedback
Feedback