Prerequisites for Layer 2 Tunnel Protocol Version 3
The following prerequisites are required to implement L2TPv3:
-
To perform these configuration tasks, your Cisco IOS XR software system administrator must assign you to a user group associated with a task group that includes the corresponding command task IDs. All command task IDs are listed in individual command references and in the Cisco IOS XR Task ID Reference Guide.
If you need assistance with your task group assignment, contact your system administrator.
-
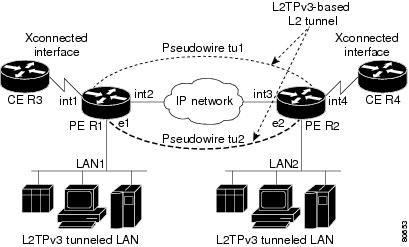
You must enable Cisco Express Forwarding (CEF) before you configure a cross-connect attachment circuit (AC) for a customer edge (CE) device.
-
You must configure a Loopback interface on the router for originating and terminating the L2TPv3 traffic. The Loopback interface must have an IP address that is reachable from the remote provider edge (PE) device at the other end of an L2TPv3 control-channel.
-
You must enable Simple Network Management Protocol (SNMP) notifications of L2TP session up and session down events.
 Note |
A cross-connection is expressed as xconnect in the CLI. |

 Feedback
Feedback