Information about AWS Integration
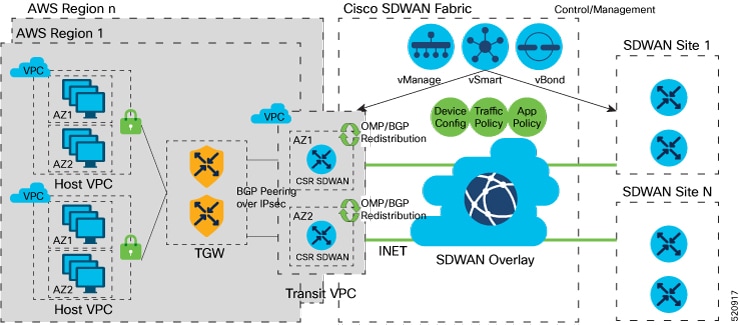
A transit gateway is a network transit hub that you can use to interconnect your VPC and on-premises networks. You can attach a VPC, or a VPN connection to a transit gateway. It acts as a virtual router for traffic flowing between your VPC and VPN connections.
You can configure and manage Cloud OnRamp for Multicloud environments through the Cisco SD-WAN Manager controller. A configuration wizard in Cisco SD-WAN Manager automates the bring-up of the transit gateway to your public cloud account, the creation of cloud gateways that includes transit gateways and Cisco Catalyst 8000V Edge, and the connections between public-cloud applications and the users of those applications at branches in the overlay network. This feature works with AWS virtual private clouds (VPCs) on Cisco cloud routers.
Cloud OnRamp for Multicloud supports integration with multiple AWS accounts. See Limitations for AWS Integration for details.
Supported Platforms
Cloud OnRamp for Multicloud on AWS supports the following platforms:
-
Cisco Cloud Services Router 1000V Series (Cisco CSR1000V)

Note
This platform is supported by Cisco SD-WAN Manager Release 20.3.x.
-
Cisco Catalyst 8000V Edge Software

Note
This platform is supported by Cisco SD-WAN Manager Release 20.4.x and later.
Architecture
Multicloud Dashboard
Multicloud dashboard in Cisco SD-WAN Manager consists of the following workflows:
-
Setup
-
Discover
-
Manage
-
Intent Management
Setup
You can create and manage cloud accounts and configure global settings in Cisco SD-WAN Manager for AWS automation. You can create multiple accounts, pick a specific account for transit gateway, mark one or more accounts for transit VPC automation and use other accounts for host VPC discovery and connectivity.
The multicloud dashboard supports AWS key and IAM role models for authentication. IAM roles only work for AWS cloud deployed Cisco SD-WAN Manager, as this requires special AWS AssumeRole functions. AssumeRole is used for cross-account access.
Global Settings
Global settings enables you to set a configuration one time and repeat across regions and handle resource management globally (per cloud). The software image and instance size specified are used for instantiation of CSRs in the cloud as part of the cloud gateway.
Global settings include:
-
Software image: CSR software image used for creating cloud gateway.
-
AWS Instance Size: CSR instance size used depending upon bandwidth requirements.
-
Cloud Gateway Solution: The gateway solution used for AWS cloud. For example, transit gateway with transit VPC.
-
IP subnet pool: IP subnet pool used for transit VPC creation across regions. Subnet pool can be customized per cloud gateway using custom settings option, if desired.
-
Intra-Tag Communication: Allows or denies communication between the VPCs under the same tag.
-
Default Route in Host VPCs: Default routes are automatically added to the main route table of the VPC that points to the transit gateway.
-
Full Mesh of Transit VPCs: Setup a full mesh connectivity between TVPCs of cloud gateways in different regions so as to carry site to site traffic (through CSRs) over public cloud backbone.

Note
When full mesh of transit VPCs is enabled in the global setting for Cisco Catalyst 8000V in an AWS deployment, the GigabitEthernet3 interface is automatically used for the configurations. This interface cannot be used for anything else, nor can the configuration of the interface be modified.
 Note |
The image and the instance size selected once for global settings are not applicable to all the regions. The accounts used for the image discovery can be different and the selected image or the instance size may not be supported in all the regions. AWS instance size and the software image parameters can be changed only for the new cloud gateways that are created after the settings are updated. For site-to-site communication, an additional interface is configured. The required configuration gets pushed or removed automatically when the site-to-site communication is enabled or disabled respectively in the global settings. |
Discover VPCs
You can discover all the VPCs in all the accounts provided across regions. You can tag and untag these VPCs and use it for future connectivity. Cisco SD-WAN Manager creates tag with the key Cisco-SDWAN-key and you can customize the tag value for all VPCs within the same tag. The same tag can be used to map VPCs (that is, establish connectivity between VPCs) if the Intra-Tag communication in global settings is enabled. You can edit tags and change the membership of a tag associated with a VPC.
 Note |
If you add a tag that is associated with an interconnect gateway, you cannot map it to an AWS cloud gateway in Intent Management. |
Cloud Gateway
Cloud gateway comprises of a transit VPC, two CSR devices, and a transit gateway. Cisco SD-WAN Manager creates all the components when you pick the account and region to instantiate the cloud gateway. You can attach the appropriate device template to any free, available CSR universally unique identifiers (UUIDs) that are synced from PnP Smart Account.
You can override the global settings with custom settings to pick a different image, instance size, and subnet pool for a specific deployment. Only one cloud gateway instance per region is supported.
 Note |
Ensure that you are subscribed to the image desired for the cloud gateway in the AWS marketplace. If you are not subscribed, then the cloud gateway creation fails. |
AWS Branch Connect Overview
The edge devices connect to the host VPCs in the cloud over secure point-to-point tunnels. IPSec tunnels are set up between edge devices and the AWS Transit Gateway. These tunnels carry the branch VPNs traffic and BGP routing traffic. Using BGP, the devices and the transit gateway exchange the routing information and build routing tables.
A branch device can have any number of VPNs that require connectivity to the host VPCs. Each of these VPNs is represented as a VPN attachment to the transit gateway. As part of the VPN attachment, AWS customer gateway and VPN gateway cloud objects are created, which allow VPN connectivity from the branch device to the transit gateway. The transit gateway and the branch devices of a given site are in different BGP ASNs. The mapping information of VPNs to the tags (host VPCs) is derived from the global mapping. This mapping is realized in the cloud.
When you configure a new service VPN in a branch device template, an update event is generated, which triggers mapping based on the connectivity matrix. Similarly, when you remove a service VPN from the device template, another update event is generated, which triggers unmapping.
 Note |
The number of branch edge WAN interfaces need to be proportional to the number of regions that the branch edge device needs to connect to. For example, if a branch needs to connect to hosts in two AWS regions, you need one WAN interface attached to each of the cloud gateway in that region. The WAN interfaces within a branch cannot have the same color. |
AWS Cloud WAN
Minimum supported releases: Cisco IOS XE Catalyst SD-WAN Release 17.12.1a and Cisco Catalyst SD-WAN Manager Release 20.12.1
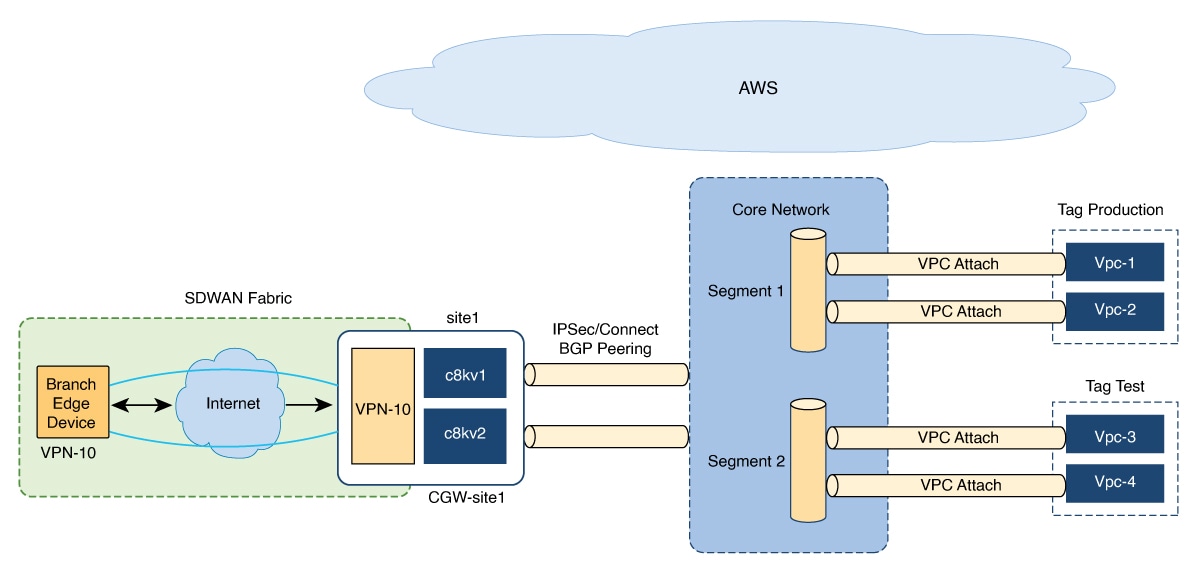
AWS Cloud WAN is a managed WAN service that you can use to build, manage, and monitor a unified global network. You can easily connect and route traffic from different sites and regions over the AWS global network.
AWS Cloud WAN enables you to use simple network policies to configure and secure your network. The network policy is defined and populated in the backend, as you configure AWS integration using Cisco SD-WAN Manager workflows.
Using AWS integration workflows you can create global AWS Cloud WAN network, define different segments and attach different VPCs in different regions to these segments.
(Minimum supported releases: Cisco IOS XE Catalyst SD-WAN Release 17.13.1a and Cisco Catalyst SD-WAN Manager Release 20.13.1) AWS Cloud WAN integration uses BGP-based dymanic routing to route traffic from different sites and regions instead of using static routes. In the AWS integration workflows, the cloud gateways have BGP peering with segments which allow IPSec based connectivity. This adds flexibility and redundancy to the workflows.
Upgrade Considerations from Cisco Catalyst SD-WAN Manager Release 20.12.1 to Cisco Catalyst SD-WAN Manager Release 20.13.1
-
Disable the site-to-site communications (in global settings) for AWS in Cisco SD-WAN Manager before you upgrade to Cisco Catalyst SD-WAN Manager Release 20.13.1. After the upgrade is complete you can enable the site-to-site communications in global settings.
Information About Configuring Devices for AWS Integration Using Configuration Groups
Minimum supported release: Cisco IOS XE Catalyst SD-WAN Release 17.14.1a and Cisco Catalyst SD-WAN Manager Release 20.14.1
You can use configuration groups in Cisco SD-WAN Manager to configure devices in AWS integration workflows. The use of same configuration groups between two cloud gateways is not supported.
You can enable configuration of devices using configuration groups in the global settings. When you create a cloud gateway, if you have enabled configuration using configuration groups in the global settings, you can choose an existing configuration group or create a new one. For more information about configuration groups, see Cisco Catalyst SD-WAN Configuration Groups.
 Note |
After you enable configuration of devices using configuration groups in the global settings, you can configure devices using both templates and configuration groups. |
Software-Defined Cloud Interconnect Cloud Gateway Extension
From Cisco Catalyst SD-WAN Manager Release 20.15.1, in the Software-Defined Cloud Interconnect (SDCI) workflow, while creating a cloud gateway, you cannot configure devices using configuration groups.
 Feedback
Feedback