System Logging
System logging operations use a mechanism similar to the UNIX syslog command to record system-wide, high-level operations that occur on Cisco SD-WAN devices in the overlay network. The log levels (priorities) of the messages are the same as standard UNIX commands, and you can configure the priority of syslog messages. Cisco SD-WAN devices can send log messages to a UNIX-style syslog service.
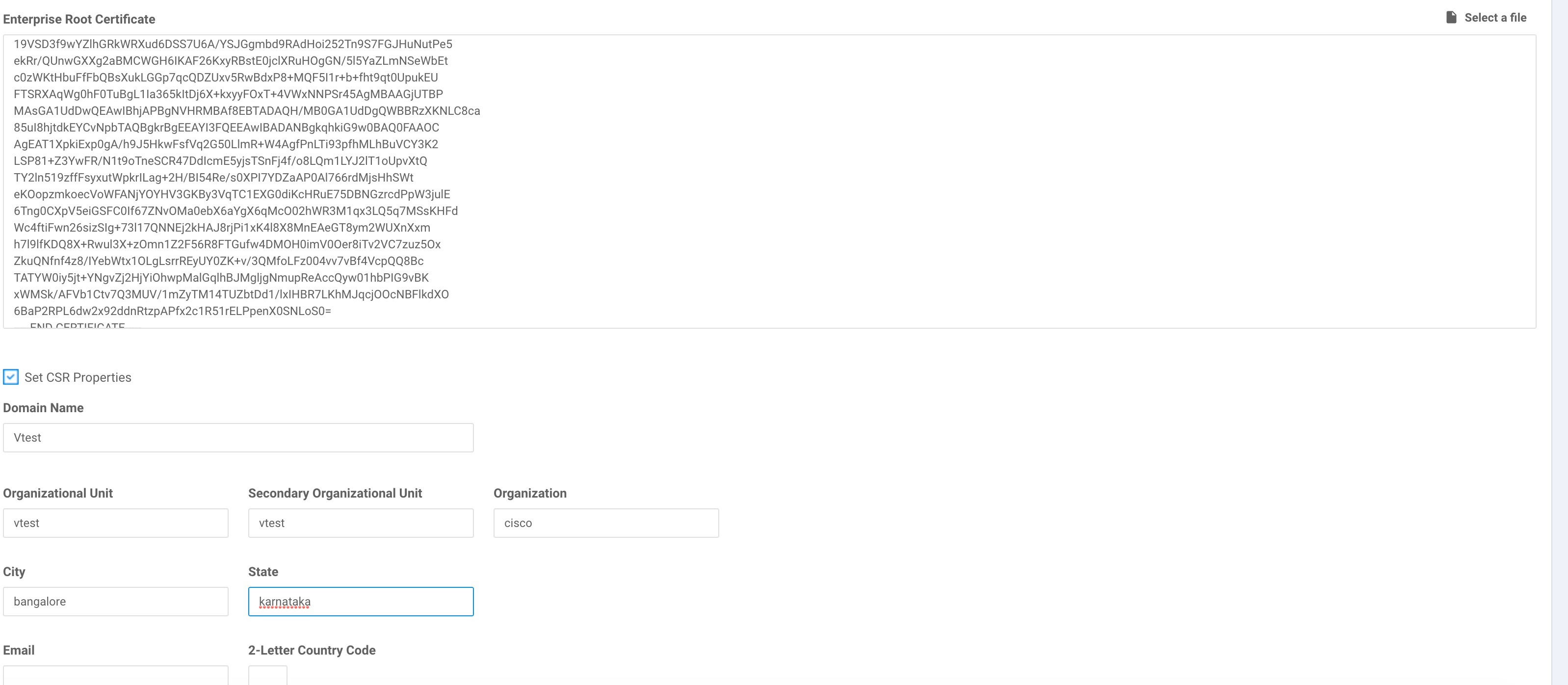
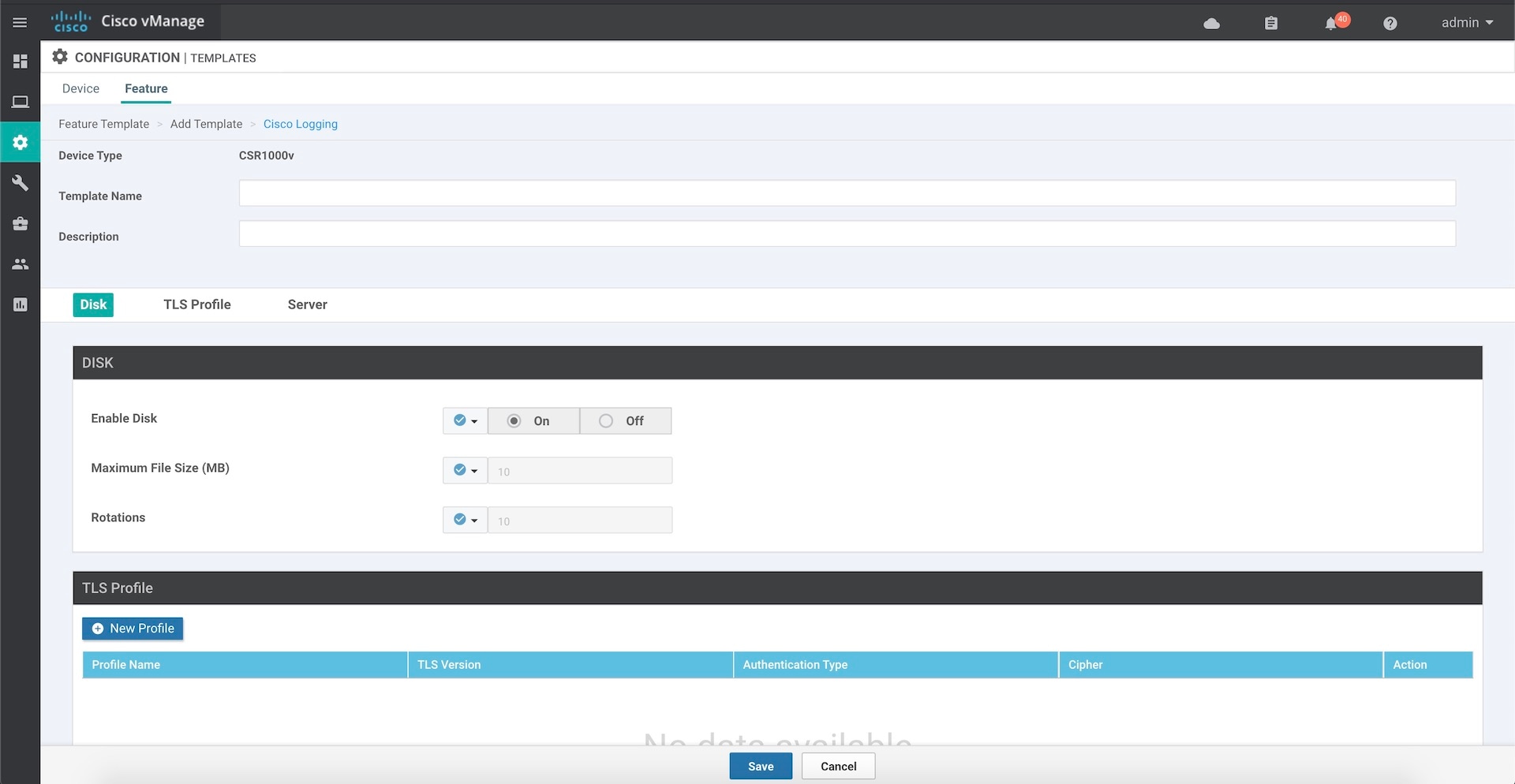
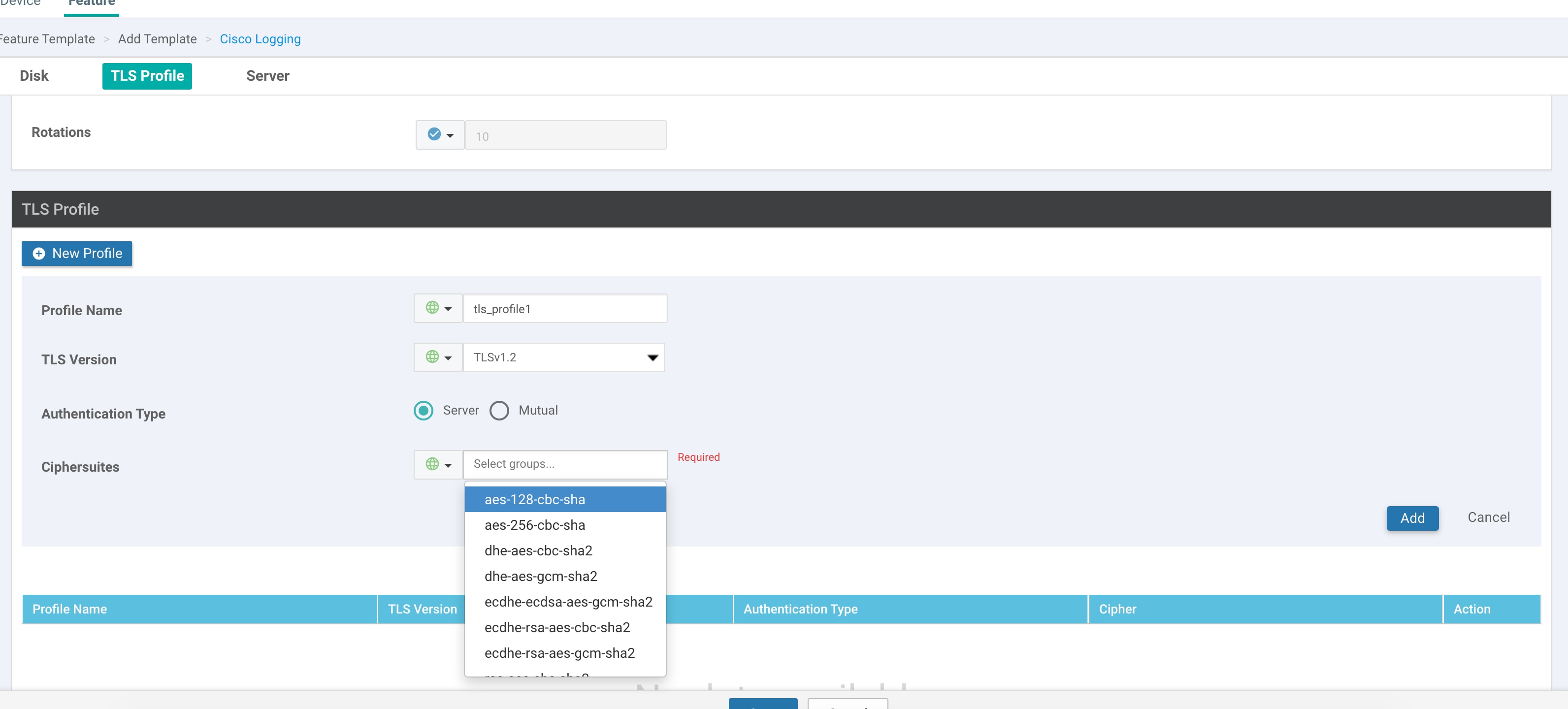
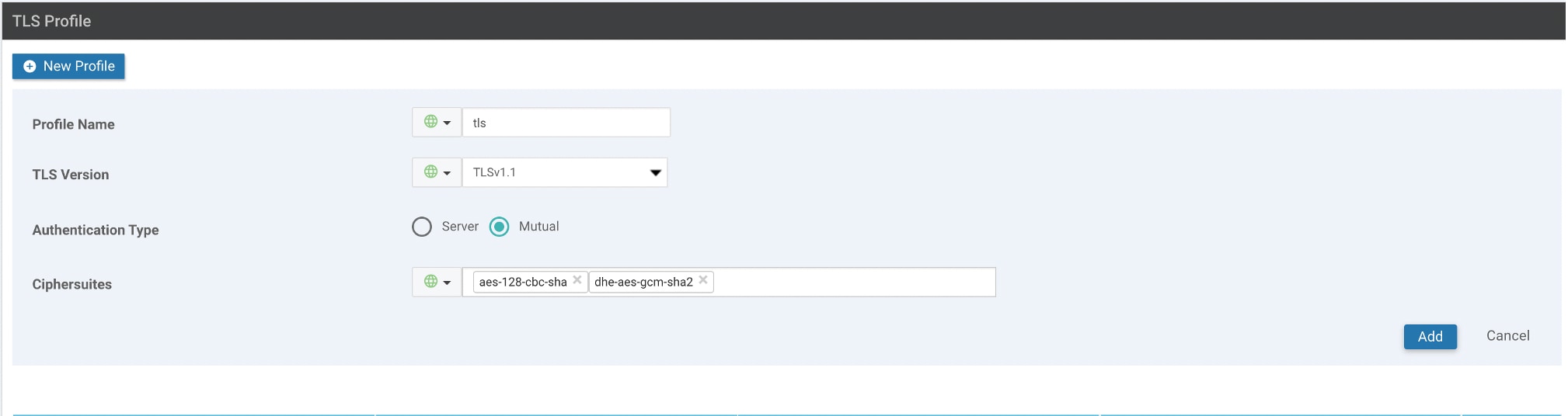
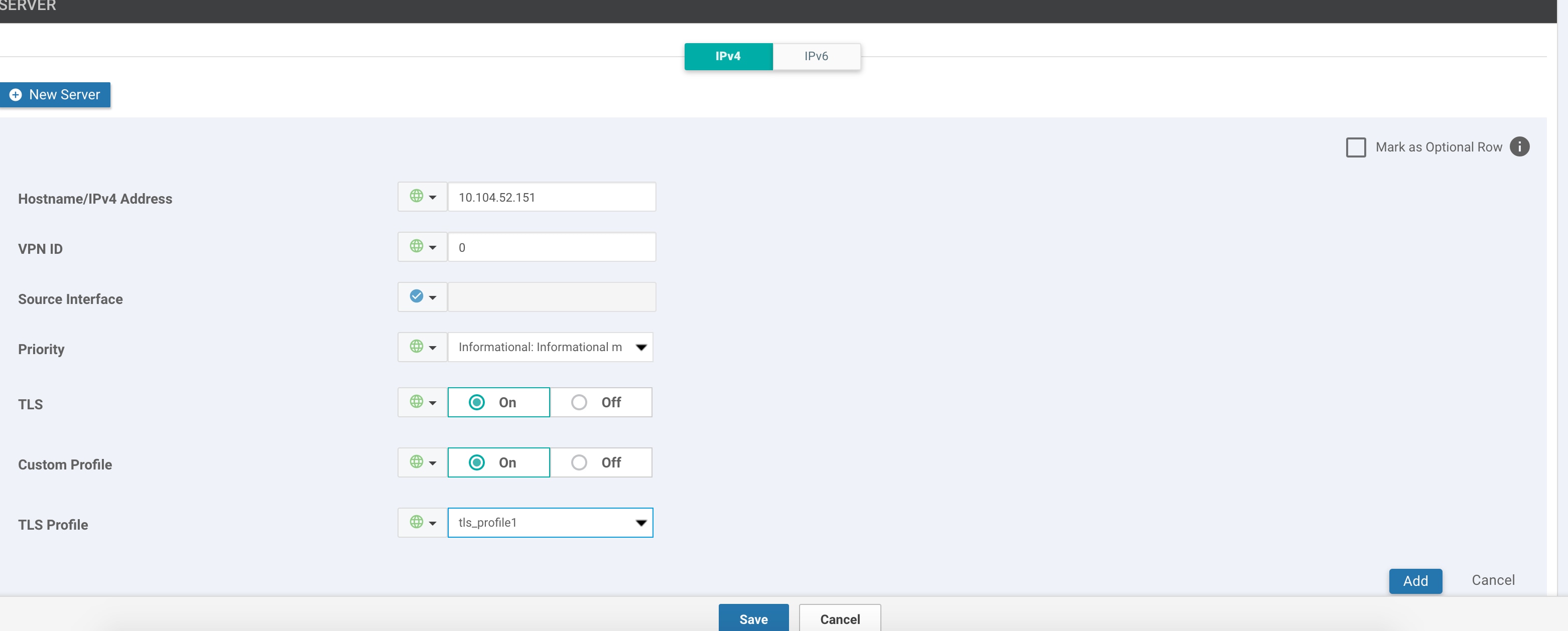
Cisco IOS XE SD-WAN devices and Cisco vEdge devices send syslog messages to syslog servers on configured external hosts using TCP and UDP. When these devices are sending the syslog messages, the messages might transit several hops to reach the output destination. The intermediate networks during the hops might not be trustworthy, be in a different domain, or have a different security level. Therefore, Cisco IOS XE SD-WAN devices now support sending secure syslog messages over the Transport Layer Security (TLS) as per RFC5425. To secure the syslog message content from potential tampering, the TLS protocol is used for certificate exchange, mutual authentication, and ciphers negotiation.
Cisco IOS XE SD-WAN devices supports both mutual and server authentication for sending syslog messages over TLS.

 Feedback
Feedback