System Options
The Configuration > Remote Access VPN > Network (Client) Access > Advanced > IPsec > System Options pane (also reached using Configuration > Site-to-Site VPN > Advanced > System Options) lets you configure features specific to IPsec and VPN sessions on the ASA.
-
Limit the maximum number of active IPsec VPN sessions—Enables or disables limiting the maximum number of active IPsec VPN sessions. The range depends on the hardware platform and the software license.
-
Maximum IPsec Sessions—Specifies the maximum number of active IPsec VPN sessions allowed. This field is active only when you choose the preceding check box to limit the maximum number of active IPsec VPN sessions.
-
-
L2TP Tunnel Keep-alive Timeout—Specifies the frequency, in seconds, of keepalive messages. The range is 10 through 300 seconds. The default is 60 seconds. This is an advanced system option for Network (Client) Access only.
-
Reclassify existing flows when VPN tunnels establish
-
Preserve stateful VPN flows when the tunnel drops—Enables or disables preserving IPsec tunneled flows in Network-Extension Mode (NEM). With the persistent IPsec tunneled flows feature enabled, as long as the tunnel is recreated within the timeout dialog box, data continues flowing successfully because the security appliance still has access to the state information. This option is disabled by default.

Note
Tunneled TCP flows are not dropped, so they rely on the TCP timeout for cleanup. However, if the timeout is disabled for a particular tunneled flow, that flow remains in the system until being cleared manually or by other means (for example, by a TCP RST from the peer).
-
IPsec Security Association Lifetime—Configures the duration of a Security Association (SA). This parameter specifies how to measure the lifetime of the IPsec SA keys, which is how long the IPsec SA lasts until it expires and must be renegotiated with new keys.
-
Time—Specifies the SA lifetime in terms of hours (hh), minutes (mm) and seconds (ss).
-
Traffic Volume—Defines the SA lifetime in terms of kilobytes of traffic. Enter the number of kilobytes of payload data after which the IPsec SA expires, or check unlimited. Minimum is 100 KB, default is 10000 KB, maximum is 2147483647 KB.
-
-
Enable PMTU (Path Maximum Transmission Unit) Aging—Allows an administrator to enable PMTU aging.
-
Interval to Reset PMTU of an SA (Security Association)—Enter the number of seconds at which the PMTU value is reset to its original value.
-
-
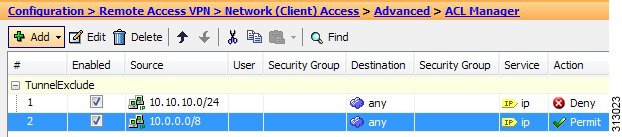
Enable inbound IPsec sessions to bypass interface access-lists. Group policy and per-user authorization ACLs still apply to the traffic—By default, the ASA allows VPN traffic to terminate on an ASA interface; you do not need to allow IKE or ESP (or other types of VPN packets) in an access rule. When this option is checked, you also do not need an access rule for local IP addresses of decrypted VPN packets. Because the VPN tunnel was terminated successfully using VPN security mechanisms, this feature simplifies configuration and maximizes the ASA performance without any security risks. (Group policy and per-user authorization ACLs still apply to the traffic.)
You can require an access rule to apply to the local IP addresses by unchecking this option. The access rule applies to the local IP address, and not to the original client IP address used before the VPN packet was decrypted.
-
Permit communication between VPN peers connected to the same interface—Enables or disables this feature.
You can also redirect incoming client VPN traffic back out through the same interface unencrypted as well as encrypted. If you send VPN traffic back out through the same interface unencrypted, you should enable NAT for the interface so that publicly routable addresses replace your private IP addresses (unless you already use public IP addresses in your local IP address pool).
-
Compression Settings—Specifies the features for which you want to enable compression: WebVPN, and SSL VPN Client. Compression is enabled by default.




 Feedback
Feedback