About the Identity Firewall
In an enterprise, users often need access to one or more server resources. Typically, a firewall is not aware of the users’ identities and, therefore, cannot apply security policies based on identity. To configure per-user access policies, you must configure a user authentication proxy, which requires user interaction (a username/password query).
The Identity Firewall in the ASA provides more granular access control based on users’ identities. You can configure access rules and security policies based on user names and user group names rather than through source IP addresses. The ASA applies the security policies based on an association of IP addresses to Windows Active Directory login information and reports events based on the mapped usernames instead of network IP addresses.
The Identity Firewall integrates with Microsoft Active Directory in conjunction with an external Active Directory (AD) Agent that provides the actual identity mapping. The ASA uses Windows Active Directory as the source to retrieve the current user identity information for specific IP addresses and allows transparent authentication for Active Directory users.
Identity-based firewall services enhance the existing access control and security policy mechanisms by allowing users or groups to be specified in place of source IP addresses. Identity-based security policies can be interleaved without restriction between traditional IP address-based rules.
The key benefits of the Identity Firewall include:
-
Decoupling network topology from security policies
-
Simplifying the creation of security policies
-
Providing the ability to easily identify user activities on network resources
-
Simplifying user activity monitoring
Architecture for Identity Firewall Deployments
The Identity Firewall integrates with Window Active Directory in conjunction with an external Active Directory (AD) Agent that provides the actual identity mapping.
The identity firewall consists of three components:
-
ASA
-
Microsoft Active Directory
Although Active Directory is part of the Identity Firewall on the ASA, Active Directory administrators manage it. The reliability and accuracy of the data depends on data in Active Directory.
Supported versions include Windows Server 2003, Windows Server 2008, and Windows Server 2008 R2 servers.
-
Active Directory (AD) Agent
The AD Agent runs on a Windows server. Supported Windows servers include Windows 2003, Windows 2008, and Windows 2008 R2.

Note
Windows 2003 R2 is not supported for the AD Agent server.
The following figure show the components of the Identity Firewall. The succeeding table describes the roles of these components and how they communicate with one another.
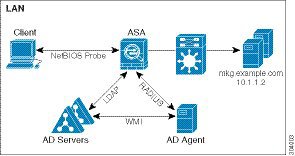
|
1 |
On the ASA: Administrators configure local user groups and Identity Firewall policies. |
4 |
Client <-> ASA: The client logs into the network through Microsoft Active Directory. The AD Server authenticates users and generates user login security logs. Alternatively, the client can log into the network through a cut-through proxy or VPN. |
|
2 |
ASA <-> AD Server: The ASA sends an LDAP query for the Active Directory groups configured on the AD Server. The ASA consolidates local and Active Directory groups and applies access rules and Modular Policy Framework security policies based on user identity. |
5 |
ASA <-> Client: Based on the policies configured on the ASA, it grants or denies access to the client. If configured, the ASA probes the NetBIOS of the client to pass inactive and no-response users. |
|
3 |
ASA <-> AD Agent: Depending on the Identity Firewall configuration, the ASA downloads the IP-user database or sends a RADIUS request to the AD Agent that asks for the user’s IP address. The ASA forwards the new mapped entries that have been learned from web authentication and VPN sessions to the AD Agent. |
6 |
AD Agent <-> AD Server: The AD Agent maintains a cache of user ID and IP address mapped entries. and notifies the ASA of changes. The AD Agent sends logs to a syslog server. |
Features of the Identity Firewall
The Identity Firewall includes the following key features.
Flexibility
-
The ASA can retrieve user identity and IP address mapping from the AD Agent by querying the AD Agent for each new IP address or by maintaining a local copy of the entire user identity and IP address database.
-
Supports host group, subnet, or IP address for the destination of a user identity policy.
-
Supports a fully qualified domain name (FQDN) for the source and destination of a user identity policy.
-
Supports the combination of 5-tuple policies with ID-based policies. The identity-based feature works in tandem with the existing 5-tuple solution.
-
Supports use with application inspection policies.
-
Retrieves user identity information from remote access VPN, AnyConnect VPN, L2TP VPN and cut-through proxy. All retrieved users are populated to all ASAs that are connected to the AD Agent.
Scalability
-
Each AD Agent supports 100 ASAs. Multiple ASAs are able to communicate with a single AD Agent to provide scalability in larger network deployments.
-
Supports 30 Active Directory servers provided the IP address is unique among all domains.
-
Each user identity in a domain can have up to 8 IP addresses.
-
Supports up to 64,000 user identity-IP address mapped entries in active policies for the ASA 5500 Series models. This limit controls the maximum number of users who have policies applied. The total number of users are the aggregate of all users configured in all different contexts.
-
Supports up to 512 user groups in active ASA policies.
-
A single access rule can contain one or more user groups or users.
-
Supports multiple domains.
Availability
-
The ASA retrieves group information from the Active Directory and falls back to web authentication for IP addresses when the AD Agent cannot map a source IP address to a user identity.
-
The AD Agent continues to function when any of the Active Directory servers or the ASA are not responding.
-
Supports configuring a primary AD Agent and a secondary AD Agent on the ASA. If the primary AD Agent stops responding, the ASA can switch to the secondary AD Agent.
-
If the AD Agent is unavailable, the ASA can fall back to existing identity sources such as cut-through proxy and VPN authentication.
-
The AD Agent runs a watchdog process that automatically restarts its services when they are down.
-
Allows a distributed IP address/user mapping database for use among ASAs.
Deployment Scenarios
You can deploy the components of the Identity Firewall in the following ways, depending on your environmental requirements.
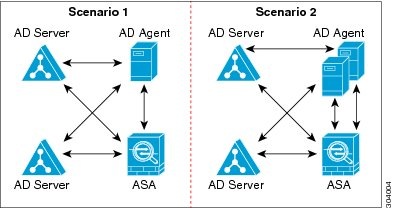
The following figure shows how you can deploy the components of the Identity Firewall to allow for redundancy. Scenario 1 shows a simple installation without component redundancy. Scenario 2 also shows a simple installation without redundancy. However, in this deployment scenario, the Active Directory server and AD Agent are co-located on the same Windows server.

The following figure shows how you can deploy the Identity Firewall components to support redundancy. Scenario 1 shows a deployment with multiple Active Directory servers and a single AD Agent installed on a separate Windows server. Scenario 2 shows a deployment with multiple Active Directory servers and multiple AD Agents installed on separate Windows servers.
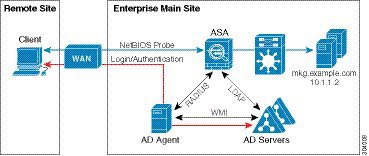
The following figure shows how all Identity Firewall components—Active Directory server, the AD Agent, and the clients—are installed and communicate on the LAN.

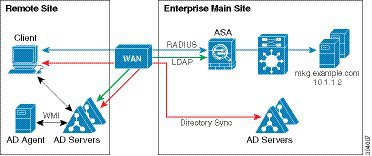
The following figure shows a WAN-based deployment to support a remote site. The Active Directory server and the AD Agent are installed on the main site LAN. The clients are located at a remote site and connect to the Identity Firewall components over a WAN.
The following figure also shows a WAN-based deployment to support a remote site. The Active Directory server is installed on the main site LAN. However, the AD Agent is installed and accessed by the clients at the remote site. The remote clients connect to the Active Directory servers at the main site over a WAN.
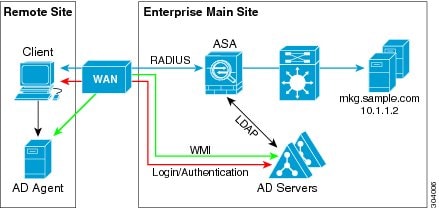
The following figure shows an expanded remote site installation. An AD Agent and Active Directory servers are installed at the remote site. The clients access these components locally when logging into network resources located at the main site. The remote Active Directory server must synchronize its data with the central Active Directory servers located at the main site.
 Feedback
Feedback