|
Network Object NAT
|
8.3(1)
|
Configures NAT for a network object IP address(es).
We introduced or modified the
following commands:
nat
(object network configuration mode), show
nat, show xlate, show nat pool.
|
|
Twice NAT
|
8.3(1)
|
Twice NAT lets you identify both the source and destination
address in a single rule.
We modified or introduced the
following commands:
nat,
show nat, show xlate, show
nat pool.
|
|
Identity NAT configurable proxy ARP and route lookup
|
8.4(2)/8.5(1)
|
In earlier releases for identity NAT, proxy ARP was disabled,
and a route lookup was always used to determine the egress interface. You could
not configure these settings. In 8.4(2) and later, the default behavior for
identity NAT was changed to match the behavior of other static NAT
configurations: proxy ARP is enabled, and the NAT configuration determines the
egress interface (if specified) by default. You can leave these settings as is,
or you can enable or disable them discretely. Note that you can now also
disable proxy ARP for regular static NAT.
For pre-8.3 configurations, the migration of NAT exempt rules
(the
nat 0 access-list command) to 8.4(2) and later now includes
the following keywords to disable proxy ARP and to use a route lookup:
no-proxy-arp and
route-lookup. The
unidirectional keyword that was used for migrating to 8.3(2)
and 8.4(1) is no longer used for migration. When upgrading to 8.4(2) from
8.3(1), 8.3(2), and 8.4(1), all identity NAT configurations will now include
the
no-proxy-arp and
route-lookup keywords, to maintain existing functionality.
The
unidirectional keyword is removed.
We modified the following
command:
nat static [no-proxy-arp] [route-lookup].
|
|
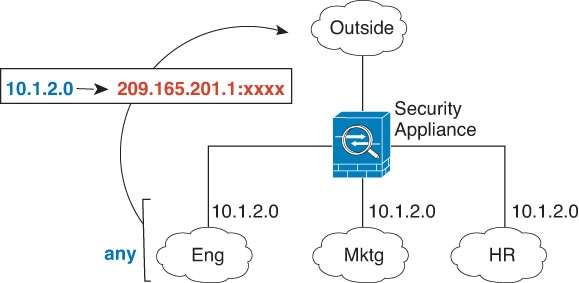
PAT pool and round robin address assignment
|
8.4(2)/8.5(1)
|
You can now specify a pool of PAT addresses instead of a single
address. You can also optionally enable round-robin assignment of PAT addresses
instead of first using all ports on a PAT address before using the next address
in the pool. These features help prevent a large number of connections from a
single PAT address from appearing to be part of a DoS attack and makes
configuration of large numbers of PAT addresses easy.
We modifed the following
commands:
nat dynamic [pat-pool
mapped_object [round-robin]] and
nat source dynamic [pat-pool
mapped_object [round-robin]].
|
|
Round robin PAT pool allocation uses the same IP address for
existing hosts
|
8.4(3)
|
When using a PAT pool with round robin allocation, if a host has
an existing connection, then subsequent connections from that host will use the
same PAT IP address if ports are available.
We did not modify any
commands.
This feature is not available
in 8.5(1) or 8.6(1).
|
|
Flat range of PAT ports for a PAT pool
|
8.4(3)
|
If available, the real source port number is used for the mapped
port. However, if the real port is
not available, by default the mapped ports are chosen from
the same range of ports as the real port number: 0 to 511, 512 to 1023, and
1024 to 65535. Therefore, ports below 1024 have only a small PAT pool.
If you have a lot of traffic that uses the lower port ranges,
when using a PAT pool, you can now specify a flat range of ports to be used
instead of the three unequal-sized tiers: either 1024 to 65535, or 1 to 65535.
We modifed the following
commands:
nat dynamic [pat-pool
mapped_object [flat [include-reserve]]] and
nat source dynamic [pat-pool
mapped_object [flat [include-reserve]]].
This
feature is not available in 8.5(1) or 8.6(1).
|
|
Extended PAT for a PAT pool
|
8.4(3)
|
Each PAT IP address allows up to 65535 ports. If 65535 ports do
not provide enough translations, you can now enable extended PAT for a PAT
pool. Extended PAT uses 65535 ports per
service, as opposed to per IP address, by including the
destination address and port in the translation information.
We modifed the following
command:
nat dynamic [pat-pool
mapped_object [extended]] and
nat source dynamic [pat-pool
mapped_object
[extended]].
This
feature is not available in 8.5(1) or 8.6(1).
|
|
Automatic NAT rules to translate a VPN peer’s local IP address
back to the peer’s real IP address
|
8.4(3)
|
In rare situations, you might want to use a VPN peer’s real IP
address on the inside network instead of an assigned local IP address. Normally
with VPN, the peer is given an assigned local IP address to access the inside
network. However, you might want to translate the local IP address back to the
peer’s real public IP address if, for example, your inside servers and network
security is based on the peer’s real IP address.
You can enable this feature on one interface per tunnel group.
Object NAT rules are dynamically added and deleted when the VPN session is
established or disconnected. You can view the rules using the
show nat
command.
Because of routing issues, we do not recommend using this
feature unless you know you need it; contact Cisco TAC to confirm feature
compatibility with your network. See the following limitations:
-
Only supports Cisco IPsec and AnyConnect Client.
-
Return traffic to the public IP addresses must be routed back to
the ASA so the NAT policy and VPN policy can be applied.
-
Does not support load-balancing (because of routing issues).
-
Does not support roaming (public IP changing).
We introduced the following
command:
nat-assigned-to-public-ip
interface (tunnel-group general-attributes configuration
mode).
|
|
NAT support for IPv6
|
9.0(1)
|
NAT now supports IPv6 traffic, as well as translating between
IPv4 and IPv6. Translating between IPv4 and IPv6 is not supported in
transparent mode.
We modified the following
commands:
nat (global and object network configuration modes),
show nat, show nat pool,
show xlate.
|
|
NAT support for reverse DNS lookups
|
9.0(1)
|
NAT now supports translation of the DNS PTR record for reverse
DNS lookups when using IPv4 NAT, IPv6 NAT, and NAT64 with DNS inspection
enabled for the NAT rule.
|
|
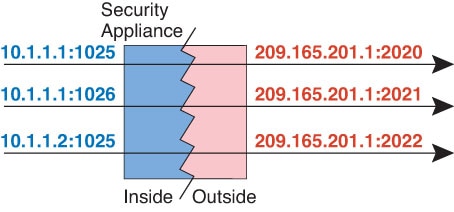
Per-session PAT
|
9.0(1)
|
The per-session PAT feature improves the scalability of PAT and, for
clustering, allows each member unit to own PAT connections;
multi-session PAT connections have to be forwarded to and owned by
the control unit. At the end of a per-session PAT session, the ASA
sends a reset and immediately removes the xlate. This reset causes
the end node to immediately release the connection, avoiding the
TIME_WAIT state. Multi-session PAT, on the other hand, uses the PAT
timeout, by default 30 seconds. For “hit-and-run” traffic, such as
HTTP or HTTPS, the per-session feature can dramatically increase the
connection rate supported by one address. Without the per-session
feature, the maximum connection rate for one address for an IP
protocol is approximately 2000 per second. With the per-session
feature, the connection rate for one address for an IP protocol is
65535/average-lifetime.
By default, all TCP traffic and UDP DNS traffic use a
per-session PAT xlate. For traffic that requires multi-session PAT, such as
H.323, SIP, or Skinny, you can disable per-session PAT by creating a
per-session deny rule.
We introduced the following
commands:
xlate per-session,
show nat pool.
|
|
Transactional Commit Model on NAT Rule Engine
|
9.3(1)
|
When enabled, a NAT rule update is applied after the rule
compilation is completed; without affecting the rule matching performance.
We added the
nat keyword to the following commands:
asp rule-engine transactional-commit,
show running-config asp rule-engine transactional-commit,
clear configure asp rule-engine transactional-commit.
We added NAT to the following screen: Configuration > Device
Management > Advanced > Rule Engine.
|
|
Carrier
Grade NAT enhancements
|
9.5(1)
|
For
carrier-grade or large-scale PAT, you can allocate a block of ports for each
host, rather than have NAT allocate one port translation at a time (see RFC
6888).
We added the following commands:
xlate block-allocation
size ,
xlate block-allocation
maximum-per-host . We added the
block-allocation keyword to the
nat command.
|
|
NAT support for SCTP
|
9.5(2)
|
You can now specify SCTP ports in static network object NAT
rules. Using SCTP in static twice NAT is not recommended. Dynamic NAT/PAT does
not support SCTP.
We modified the following commands:
nat static (object).
|
|
Interim logging for NAT port block allocation.
|
9.12(1)
|
When you enable port block allocation for NAT, the system generates
syslog messages during port block creation and deletion. If you
enable interim logging, the system generates message 305017 at the
interval you specify. The messages report all active port blocks
allocated at that time, including the protocol (ICMP, TCP, UDP) and
source and destination interface and IP address, and the port block.
We added the following command: xlate
block-allocation pba-interim-logging seconds .
|
|
Changes to PAT address allocation in clustering. The PAT pool
flat option is now enabled by
default and it is not configurable.
|
9.15(1)
|
The way PAT addresses are distributed to the members of a cluster is
changed. Previously, addresses were distributed to the members of
the cluster, so your PAT pool would need a minimum of one address
per cluster member. Now, the control unit instead divides each PAT
pool address into equal-sized port blocks and distributes them
across cluster members. Each member has port blocks for the same PAT
addresses. Thus, you can reduce the size of the PAT pool, even to as
few as one IP address, depending on the amount of connections you
typically need to PAT. Port blocks are allocated in 512-port blocks
from the 1024-65535 range. You can optionally included the reserved
ports, 1-1023, in this block allocation when you configure PAT pool
rules. For example, in a 4-node cluster, each node gets 32 blocks
with which it will be able to handle 16384 connections per PAT pool
IP address compared to a single node handling all 65535 connections
per PAT pool IP address.
As part of this change, PAT pools for all systems, whether standalone
or operating in a cluster, now use a flat port range of 1023 -
65535. Previously, you could optionally use a flat range by
including the flat keyword in a PAT pool
rule. The flat keyword is no longer
supported: the PAT pool is now always flat. The
include-reserve keyword, which was
previously a sub-keyword to flat , is now
an independent keyword within the PAT pool configuration. With this
option, you can include the 1 - 1023 port range within the PAT
pool.
Note that if you configure port block allocation (the
block-allocation PAT pool option),
your block allocation size is used rather than the default 512-port
block. In addition, you cannot configure extended PAT for a PAT pool
for systems in a cluster.
New/Modified commands: nat ,
show nat pool
|
|
New Section 0 for system-defined NAT rules.
|
9.16(1)
|
A new Section 0 has been added to the NAT rule table. This section is
exclusively for the use of the system. Any NAT rules that the system
needs for normal functioning are added to this section, and these
rules take priority over any rules you create. Previously,
system-defined rules were added to Section 1, and user-defined rules
could interfere with proper system functioning. You cannot add,
edit, or delete Section 0 rules, but you will see them in
show nat detail command output.
|
|
Twice NAT support for fully-qualified domain name (FQDN) objects as
the translated (mapped) destination.
|
9.17(1)
|
You can use an FQDN network object, such as one specifying
www.example.com, as the translated (mapped) destination address in
twice NAT rules. The system configures the rule based on the IP
address returned from the DNS server.
|






 Feedback
Feedback