|
Platform Features
|
|
ASA for the Firepower 4150
|
We introduced the ASA for the Firepower 4150.
Requires FXOS 2.0.1.
We did not add or modify any screens.
|
|
Hot Plug Interfaces on the ASAv
|
You can add and remove Virtio virtual interfaces on the ASAv while the system is active. When you add a new interface to the
ASAv, the virtual machine detects and provisions the interface. When you remove an existing interface, the virtual machine
releases any resource associated with the interface. Hot plug interfaces are limited to Virtio virtual interfaces on the Kernel-based
Virtual Machine (KVM) hypervisor.
|
|
Microsoft Azure support on the ASAv10
|
Microsoft Azure is a public cloud environment that uses a private Microsoft Hyper V Hypervisor. The ASAv runs as a guest in
the Microsoft Azure environment of the Hyper V Hypervisor. The ASAv on Microsoft Azure supports one instance type, the Standard
D3, which supports four vCPUs, 14 GB, and four interfaces.
Also in 9.5(2.200).
|
|
Through traffic support on the Management 0/0 interface for the ASAv
|
You can now allow through traffic on the Management 0/0 interface on the ASAv. Previously, only the ASAv on Microsoft Azure
supported through traffic; now all ASAvs support through traffic. You can optionally configure this interface to be management-only,
but it is not configured by default.
|
|
Common Criteria Certification
|
The ASA was updated to comply with the Common Criteria requirements. See the rows in this table for the following features
that were added for this certification:
-
ASA SSL Server mode matching for ASDM
-
SSL client RFC 6125 support:
-
Reference Identities for Secure Syslog Server connections and Smart Licensing connections
-
ASA client checks Extended Key Usage in server certificates
-
Mutual authentication when ASA acts as a TLS client for TLS1.1 and 1.2
-
PKI debug messages
-
Crypto Key Zeroization verification
-
IPsec/ESP Transport Mode Support for IKEv2
-
New syslog messages
|
|
Firewall Features
|
|
DNS over TCP inspection
|
You can now inspect DNS over TCP traffic (TCP/53).
We modified the following page: Add/Edit dialog box
|
|
MTP3 User Adaptation (M3UA) inspection
|
You can now inspect M3UA traffic and also apply actions based on point code, service indicator, and message class and type.
We added or modified the following pages: ; the tab for service policy rules
|
|
Session Traversal Utilities for NAT (STUN) inspection
|
You can now inspect STUN traffic for WebRTC applications including Cisco Spark. Inspection opens pinholes required for return
traffic.
We added an option to the Rule Actions > Protocol Inspection tab of the Add/Edit Service Policy dialog box
|
|
Application layer health checking for Cisco Cloud Web Security
|
You can now configure Cisco Cloud Web Security to check the health of the Cloud Web Security application when determining
if the server is healthy. By checking application health, the system can fail over to the backup server when the primary server
responds to the TCP three-way handshake but cannot process requests. This ensures a more reliable system.
We modified the following screen:
|
|
Connection holddown timeout for route convergence.
|
You can now configure how long the system should maintain a connection when the route used by the connection no longer exists
or is inactive. If the route does not become active within this holddown period, the connection is freed. You can reduce the
holddown timer to make route convergence happen more quickly. However, the 15 second default is appropriate for most networks
to prevent route flapping.
We modified the following screen:
Also in 9.4(3).
|
|
Changes in TCP option handling
|
You can now specify actions for the TCP MSS and MD5 options in a packet’s TCP header when configuring a TCP map. In addition,
the default handling of the MSS, timestamp, window-size, and selective-ack options has changed. Previously, these options
were allowed, even if there were more than one option of a given type in the header. Now, packets are dropped by default if
they contain more than one option of a given type. For example, previously a packet with 2 timestamp options would be allowed,
now it will be dropped.
You can configure a TCP map to allow multiple options of the same type for MD5, MSS, selective-ack, timestamp, and window-size.
For the MD5 option, the previous default was to clear the option, whereas the default now is to allow it. You can also drop
packets that contain the MD5 option. For the MSS option, you can set the maximum segment size in the TCP map (per traffic
class). The default for all other TCP options remains the same: they are cleared.
We modified the following screen: Add/Edit dialog box
|
|
Transparent mode maximum interfaces per bridge group increased to 64
|
The maximum interfaces per bridge group was increased from 4 to 64.
We did not modify any screens.
|
|
Flow offload support for multicast connections in transparent mode.
|
You can now offload multicast connections to be switched directly in the NIC on transparent mode Firepower 4100 and 9300 series
devices. Multicast offload is available for bridge groups that contain two and only two interfaces.
There are no new commands or ASDM screens for this feature.
|
|
Customizable ARP rate limiting
|
You can set the maximum number of ARP packets allowed per second. The default value depends on your ASA model. You can customize
this value to prevent an ARP storm attack.
We modified the following screen:
|
|
Ethertype rule support for the IEEE 802.2 Logical Link Control packet's Destination Service Access Point address.
|
You can now write Ethertype access control rules for the IEEE 802.2 Logical Link Control packet's Destination Service Access
Point address. Because of this addition, the bpdu keyword no longer matches the intended traffic. Rewrite bpdu rules for dsap 0x42 .
We modified the following screen: .
|
|
Remote Access Features
|
|
Pre-fill/Username-from-cert feature for multiple context mode
|
AnyConnect SSL support is extended, allowing pre-fill/username-from-certificate feature CLIs, previously available only in
single mode, to be enabled in multiple context mode as well.
We did not modify any screens.
|
|
Flash Virtualization for Remote Access VPN
|
Remote access VPN in multiple context mode now supports flash virtualization. Each context can have a private storage space
and a shared storage place based on the total flash that is available:
-
Private storage—Store files associated only with that user and specific to the content that you want for that user.
-
Shared storage—Upload files to this space and have it accessible to any user context for read/write access once you enable
it.
We modified the following screens:
|
|
AnyConnect client profiles supported in multiple context mode
|
AnyConnect client profiles are supported in multiple context mode. To add a new profile using ASDM, you must have the AnyConnect
Secure Mobility Client release 4.2.00748 or 4.3.03013 and later.
|
|
Stateful failover for AnyConnect connections in multiple context mode
|
Stateful failover is now supported for AnyConnect connections in multiple context mode.
We did not modify any screens.
|
|
Remote Access VPN Dynamic Access Policy (DAP) is supported in multiple context mode
|
You can now configure DAP per context in multiple context mode.
We did not modify any screens.
|
|
Remote Access VPN CoA (Change of Authorization) is supported in multiple context mode
|
You can now configure CoA per context in multiple context mode.
We did not modify any screens.
|
|
Remote Access VPN localization is supported in multiple context mode
|
Localization is supported globally. There is only one set of localization files that are shared across different contexts.
We did not modify any screens.
|
|
Umbrella Roaming Security module support
|
You can choose to configure the AnyConnect Secure Mobility Client's Umbrella Roaming Security module for additional DNS-layer
security when no VPN is active.
We modified the following screen: .
|
|
IPsec/ESP Transport Mode Support for IKEv2
|
Transport mode is now supported for ASA IKEv2 negotiation. It can be used in place of tunnel (default) mode. Tunnel mode encapsulates
the entire IP packet. Transport mode encapsulates only the upper-layer protocols of an IP packet. Transport mode requires
that both the source and destination hosts support IPSec, and can only be used when the destination peer of the tunnel is
the final destination of the IP packet.
We modified the following screen:
|
|
Per-packet routing lookups for IPsec inner packets
|
By default, per-packet adjacency lookups are done for outer ESP packets; lookups are not done for packets sent through the
IPsec tunnel. In some network topologies, when a routing update has altered the inner packet’s path, but the local IPsec tunnel
is still up, packets through the tunnel may not be routed correctly and fail to reach their destination. To prevent this,
use the new option to enable per-packet routing lookups for the IPsec inner packets.
We modified the following screen: adding the Enable IPsec Inner Routing Lookup checkbox.
|
|
Certificate and Secure Connection Features
|
|
ASA client checks Extended Key Usage in server certificates
|
Syslog and Smart licensing Server Certificates must contain “ServerAuth” in the Extended Key Usage field. If not, the connection
fails.
|
|
Mutual authentication when ASA acts as a TLS client for TLS1.1 and 1.2
|
If the server requests a client certificate from the ASA for authentication, the ASA will send the client identity certificate
configured for that interface. The certificate is configured by the ssl trust-point command.
|
|
PKI debug messages
|
The ASA PKI module makes connections to CA servers such as SCEP enrollment, revocation checking using HTTP, etc. All of these
ASA PKI exchanges will be logged as debug traces under debug crypto ca message 5.
|
|
ASA SSL Server mode matching for ASDM
|
For an ASDM user who authenticates with a certificate, you can now require the certificate to match a certificate map.
We modified the following screen:
|
|
Reference Identities for Secure Syslog Server connections and Smart Licensing connections
|
TLS client processing now supports rules for verification of a server identity defined in RFC 6125, Section 6. Identity verification
will be done during PKI validation for TLS connections to the Syslog Server and the Smart Licensing server only. If the presented
identity cannot be matched against the configured reference identity, the connection is not established.
We modifed the following screens:
|
|
Crypto Key Zeroization verification
|
The ASA crypto system has been updated to comply with new key zeroization requirements. Keys must be overwritten with all
zeros and then the data must be read to verify that the write was successful.
|
|
SSH public key authentication improvements
|
In earlier releases, you could enable SSH public key authentication without also enabling AAA SSH authentication with the
Local user database . The configuration is now fixed so that you must explicitly enable AAA SSH authentication. To disallow
users from using a password instead of the private key, you can now create a username without any password defined.
We modifed the following screens:
|
|
Interface Features
|
|
Increased MTU size for the ASA on the Firepower 4100/9300 chassis
|
You can set the maximum MTU to 9188 bytes on the Firepower 4100 and 9300; formerly, the maximum was 9000 bytes. This MTU is
supported with FXOS 2.0.1.68 and later.
We modified the following screen:
|
|
Routing Features
|
|
Bidirectional Forwarding Detection (BFD) Support
|
The ASA now supports the BFD routing protocol. Support was added for configuring BFD templates, interfaces, and maps. Support
for BGP routing protocol to use BFD was also added.
We added or modified the following screens:
|
|
IPv6 DHCP
|
The ASA now supports the following features for IPv6 addressing:
-
DHCPv6 Address client—The ASA obtains an IPv6 global address and optional default route from the DHCPv6 server.
-
DHCPv6 Prefix Delegation client—The ASA obtains delegated prefix(es) from a DHCPv6 server. The ASA can then use these prefixes
to configure other ASA interface addresess so that StateLess Address Auto Configuration (SLAAC) clients can autoconfigure
IPv6 addresses on the same network.
-
BGP router advertisement for delegated prefixes
-
DHCPv6 stateless server—The ASA provides other information such as the domain name to SLAAC clients when they send Information
Request (IR) packets to the ASA. The ASA only accepts IR packets, and does not assign addresses to the clients.
We added or modified the following screens:
|
|
High Availability and Scalability Features
|
|
Improved sync time for dynamic ACLs from AnyConnect when using Active/Standby failover
|
When you use AnyConnect on a failover pair, then the sync time for the associated dynamic ACLs (dACLs) to the standby unit
is now improved. Previously, with large dACLs, the sync time could take hours during which time the standby unit is busy syncing
instead of providing high availability backup.
We did not modify any screens.
|
|
Licensing Features
|
|
|
Permanent License Reservation for the ASAv
|
For highly secure environments where communication with the Cisco Smart Software Manager is not allowed, you can request a
permanent license for the ASAv. In 9.6(2), we also added support for this feature for the ASAv on Amazon Web Services. This
feature is not supported for Microsoft Azure.
| Note
|
Not all accounts are approved for permanent license reservation. Make sure you have approval from Cisco for this feature before
you attempt to configure it.
|
We introduced the following commands: license smart reservation, license smart reservation cancel, license smart reservation install, license smart reservation
request universal, license smart reservation return
No ASDM support.
Also in 9.5(2.200).
|
|
Satellite Server support for the ASAv
|
If your devices cannot access the internet for security reasons, you can optionally install a local Smart Software Manager
satellite server as a virtual machine (VM).
We did not modify any screens.
|
|
Permanent License Reservation for the ASAv Short String enhancement
|
Due to an update to the Smart Agent (to 1.6.4), the request and authorization codes now use shorter strings.
We did not modify any screens.
|
|
Permanent License Reservation for the ASA on the Firepower 4100/9300 chassis
|
For highly secure environments where communication with the Cisco Smart Software Manager is not allowed, you can request a
permanent license for the ASA on the Firepower 9300 and Firepower 4100. All available license entitlements are included in
the permanent license, including the Standard Tier, Strong Encryption (if qualified), Security Contexts, and Carrier licenses.
Requires FXOS 2.0.1.
All configuration is performed on the Firepower 4100/9300 chassis; no configuration is required on the ASA.
|
|
Smart Agent Upgrade for ASAv to v1.6
|
The smart agent was upgraded from Version 1.1 to Version 1.6. This upgrade supports permanent license reservation and also
supports setting the Strong Encryption (3DES/AES) license entitlement according to the permission set in your license account.
| Note
|
If you downgrade from Version 9.5(2.200), the ASAv does not retain the licensing registration state. You need to re-register
with the Configuration > Device Management > Licensing > Smart Licensing page with the Force registration option; obtain the ID token from the Smart Software Manager.
|
We did not change any screens.
Also in 9.5(2.200).
|
|
Monitoring Features
|
|
Packet capture of type asp-drop supports ACL and match filtering
|
When you create a packet capture of type asp-drop, you can now also specify an ACL or match option to limit the scope of the
capture.
We did not modify any screens.
|
|
Forensic Analysis enhancements
|
You can create a core dump of any process running on the ASA. The ASA also extracts the text section of the main ASA process
that you can copy from the ASA for examination.
We did not modify any screens.
|
|
Tracking Packet Count on a Per-Connection Basis through NetFlow
|
Two counters were added that allow Netflow users to see the number of Layer 4 packets being sent in both directions on a connection.
You can use these counters to determine average packet rates and sizes and to better predict traffic types, anomalies, and
events.
We did not modify any screens.
|
|
SNMP engineID sync for Failover
|
In a failover pair, the SNMP engineIDs of the paired ASAs are synced on both units. Three sets of engineIDs are maintained
per ASA—synced engineID, native engineID and remote engineID.
An SNMPv3 user can also specify the engineID of the ASA when creating a profile to preserve localized snmp-server user authentication and privacy options. If a user does not specify the native engineID, the show running config output will show two engineIDs per user.
We modified the following command: snmp-server user
No ASDM support.
Also in 9.4(3).
|

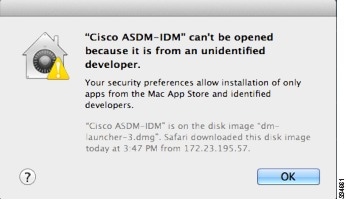
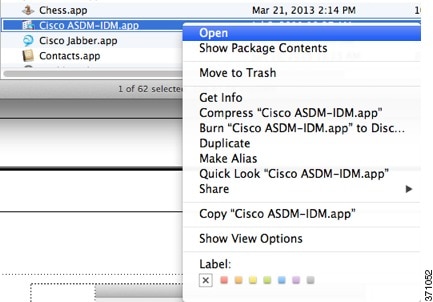
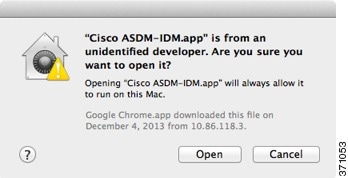
 Feedback
Feedback