About Policy Analyzer and Optimizer
Secure Firewall Threat Defense devices with extensive access control policies, especially those generated through the firewall migration process, may have numerous duplicate or shadowed rules. Such bloated policies with unoptimized rulesets can lead to excessive consumption of device memory, delayed loading of rules, long search times, resulting in inefficient security policy enforcement, reduced network speeds, and extended deployment durations.
To deal with such situations, Security Cloud Control provides Policy Analyzer and Optimizer. It is an intelligent cloud service that can analyze security policies, detect anomalies, and provide recommendations on remediations that can be performed to optimize the policies, thereby improving the firewall performance. The Policy Analyzer and Optimizer can analyze policies both in the cloud-delivered Firewall Management Center and On-Premises Firewall Management Centers that are onboarded to Security Cloud Control. In addition, this feature can:
-
provide comprehensive visualization of policy health information, including an analysis overview and policy insights based on aggregate hit counts.
-
analyze policies regularly on scheduled intervals or whenever preferred.
-
detect rule anomalies, such as duplicate rules, object overlap in rules, and expired rules.

Note that the Policy Analyzer and Optimizer can get launched from Security Cloud Control's Services page, on the left pane, and on-premises management center's Access Control policies page for the administrator's convenience.
Analysis, Remediation, and Reporting
The Policy Analyzer and Optimizer performs these services: analysis, remediation, and reporting.
Analysis
The Policy Analyzer and Optimizer polls cloud-delivered Firewall Management Center and on-premises management center for policies and displays them on the Policy Analyzer and Optimizer page. To open the Policy Analyzer and Optimizer page, in the left pane, click , select Cloud-delivered FMC or any on-premises management center, and choose Policy Analyzer and Optimizer from the right pane. Alternatively, on the Security Cloud Control left pane, choose . Choose Cloud-delivered FMC or any on-premises management center from the Data Source tab on the top-left corner.
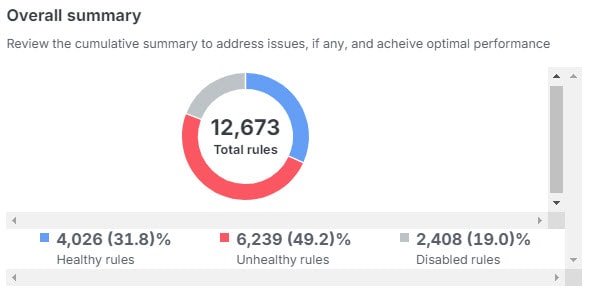
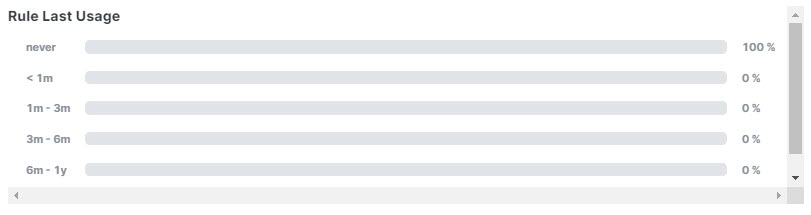
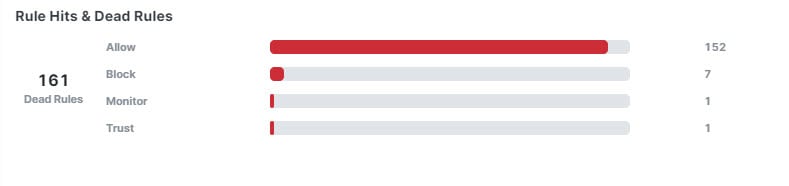
When you have created a new access control policy or imported a policy, it will take a while for the Policy Analyzer and Optimizer to identify it, after which you can manaually trigger the policy analysis. You can also wait for the auto-analysis that occurs every 24 hours. When the analysis is done, Policy Analyzer and Optimizer provides insights on the number of rules in the policy, the percentage of the policy that can be optimized, and a detailed summary that contains information such as Rule Health Summary, Rule Last Usage, Rule Hits & Dead Rules, and so on.

 Note |
The Optimizable percentage under Observations column is an approximation of how many rules in the policies can be optimized if the suggested remediations are applied. |
Remediation
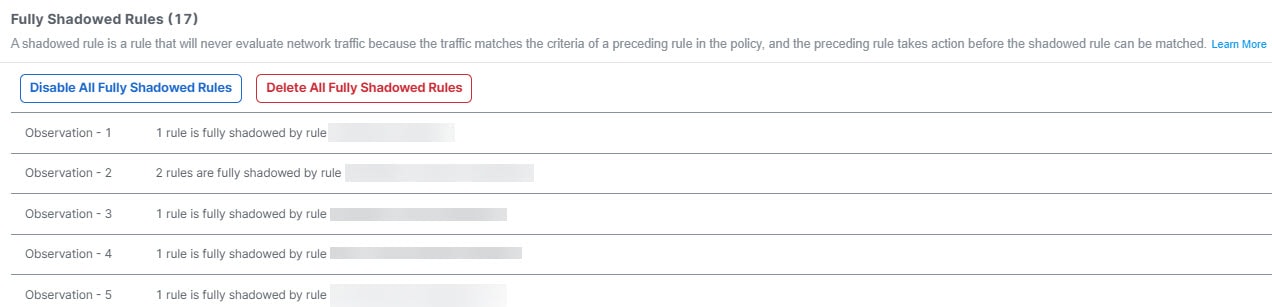
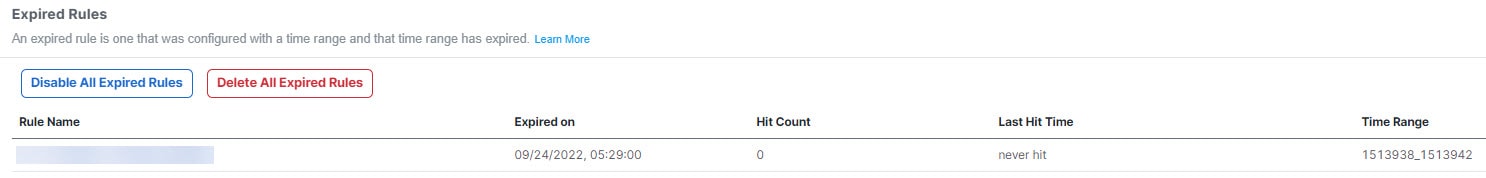
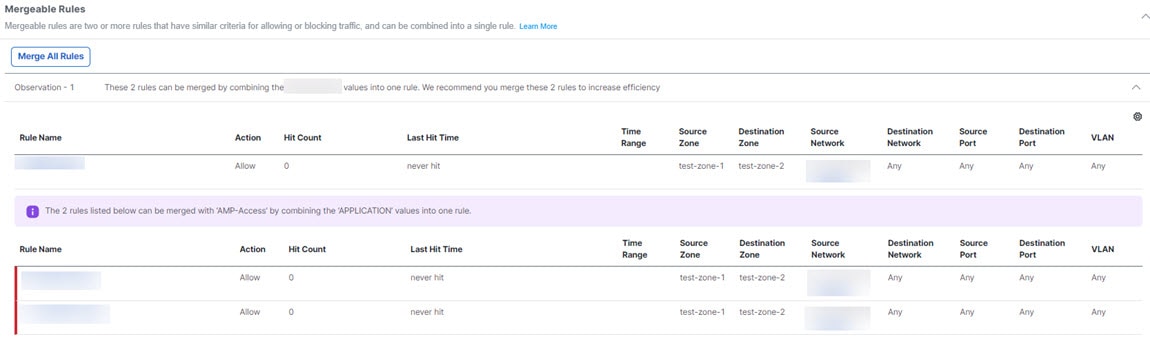
The policy analysis summary describes the health of your security policy and lets you choose which remediations suggested by the Policy Analyzer and Optimizer you want to apply to your policies. Using the suggested remediations, you could either disable or delete Duplicate Rules, Overlapping Objects, Expired Rules and merge rules that have similar allow and block settings, which can be merged into a single rule. The hit count data is listed under the Policy Insights tab. You can Apply Remediation to make the chosen remediations get applied to your policies.
Reporting
A detailed report is available for an analyzed policy. After remediation is applied on a policy, a remediation report becomes available. This report contains a consolidated list of the policy anomalies that existed and the remediations that were applied and can be downloaded as a PDF.
 ) button on the top-right corner to manually refresh the page to see new policies.
) button on the top-right corner to manually refresh the page to see new policies.






 Feedback
Feedback