Objects
An object is a container of information that you can use in one or more security policies. Objects make it easy to maintain policy consistency. You can create a single object, use it different policies, modify the object, and that change is propagated to every policy that uses the object. Without objects, you would need to modify all the policies, individually, that require the same change.
When you onboard a device, Security Cloud Control recognizes all the objects used by that device, saves them, and lists them on the Objects page. From the Objects page, you can edit existing objects and create new ones to use in your security policies.
Security Cloud Control calls an object used on multiple devices a shared object and identifies them in the Objects page with this badge  .
.
Sometimes a shared object develops some "issue" and is no longer perfectly shared across multiple policies or devices:
-
Duplicate objects are two or more objects on the same device with different names but the same values. These objects usually serve similar purposes and are used by different policies. Duplicate objects are identified by this issue icon:

-
Inconsistent objects are objects on two or more devices with the same name but different values. Sometimes users create objects in different configurations with same name and content but over time the values of these objects diverge which creates the inconsistency. Inconsistent objects are identified by this issue icon:

-
Unused objects are objects that exist in a device configuration but are not referenced by another object, an access-list, or a NAT rule. Unused objects are identified by this issue icon:

You can also create objects for immediate use in rules or policies. You can create an object that is unassociated with any rule or policy. When you use that unassociated object in a rule or policy, Security Cloud Control creates a copy of it and uses the copy.
You can view the objects managed by Security Cloud Control by navigating to the Objects menu or by viewing them in the details of a network policy.
Security Cloud Control allows you to manage network and service objects across supported devices from one location. With Security Cloud Control, you can manage objects in these ways:
-
Search for and filter all your objects based on a variety of criteria.
-
Find duplicate, unused, and inconsistent objects on your devices and consolidate, delete, or resolve those object issues.
-
Find unassociated objects and delete them if they are unused.
-
Discover shared objects that are common across devices.
-
Evaluate the impact of changes to an object on a set of policies and devices before committing the change.
-
Compare a set of objects and their relationships with different policies and devices.
-
Capture objects in use by a device after it has been on-boarded to Security Cloud Control.
If you have issues with creating, editing, or reading objects from an onboarded device, see Troubleshoot Security Cloud Control for more information.
Shared Objects

When looking at a shared object, Security Cloud Control shows you the contents of the object in the object table. Shared objects have exactly the same contents. Security Cloud Control shows you a combined or "flattened" view of the elements of the object in the details pane. Notice that in the details pane, the network elements are flattened into a simple list and not directly associated with a named object.
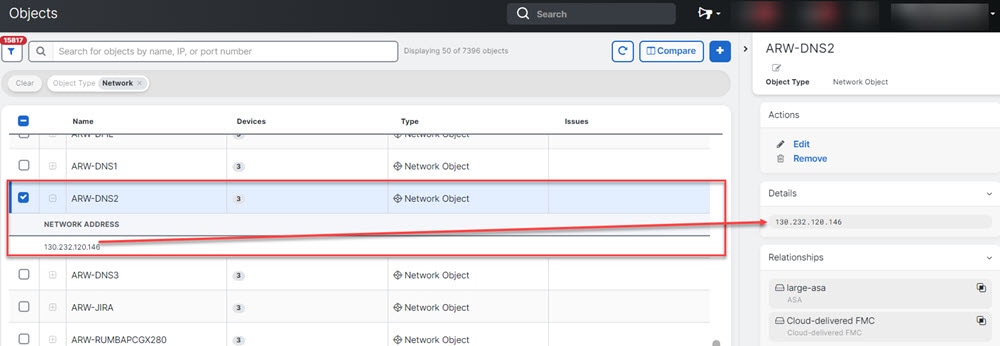
Object Overrides
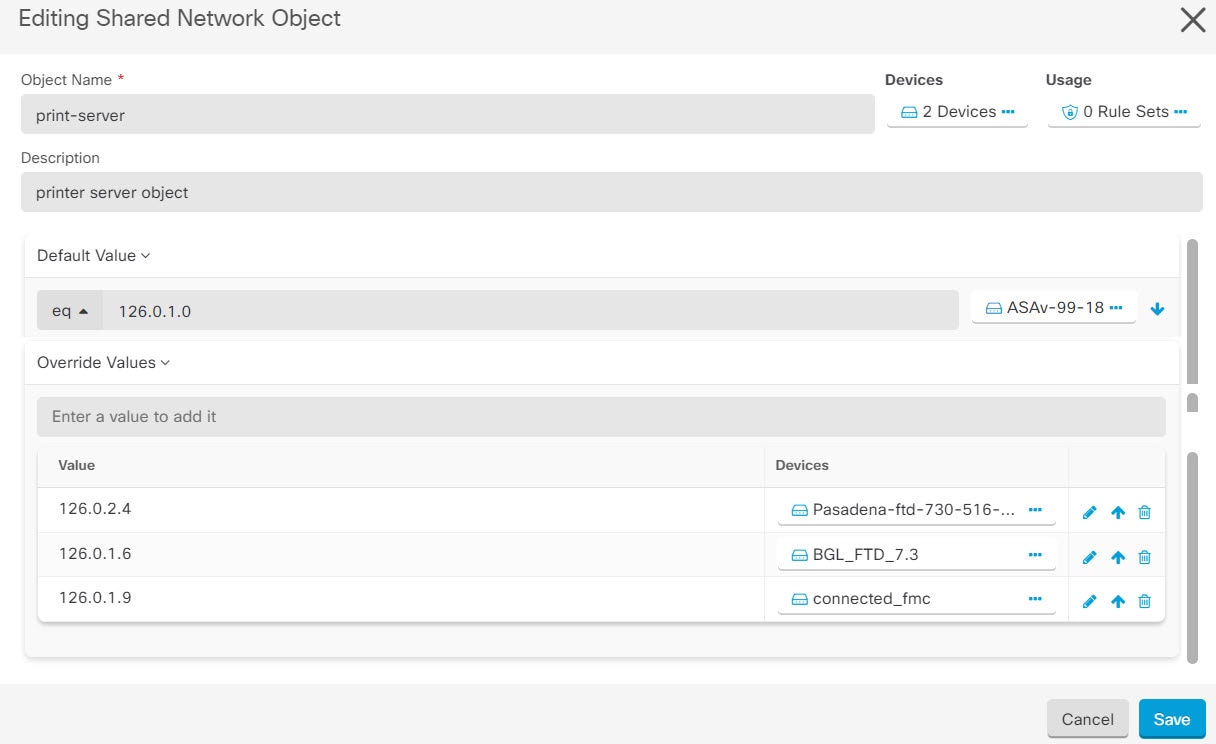
An object override allows you to override the value of a shared network object on specific devices. Security Cloud Control uses the corresponding value for the devices that you specify when configuring the override. Although the objects are on two or more devices with the same name but different values, Security Cloud Control doesn't identify them as Inconsistent objects only because these values are added as overrides.
You can create an object whose definition works for most devices, and then use overrides to specify modifications to the object for the few devices that need different definitions. You can also create an object that needs to be overridden for all devices, but its use allows you to create a single policy for all devices. Object overrides allow you to create a smaller set of shared policies for use across devices without giving up the ability to alter policies when needed for individual devices.
For example, consider a scenario where you have a printer server in each of your offices, and you have created a printer server
object print-server. You have a rule in your ACL to deny printer servers from accessing the internet. The printer server object has a default
value that you want to change from one office to another. You can do this by using object overrides and maintain rule and
"printer-server" object consistent across all locations, although their values may be different.
 Note |
If there are inconsistent objects, you can combine them into a single shared object with overrides. For more information, see Resolve Inconsistent Object Issues. |
Unassociated Objects
You can create objects for immediate use in rules or policies. You can also create an object that is unassociated with any rule or policy. When you use that unassociated object in a rule or policy, Security Cloud Control creates a copy of it and uses the copy. The original unassociated object remains among the list of available objects until it is either deleted by a nightly maintenance job, or you delete it.
Unassociated objects remain in Security Cloud Control as a copy to ensure that not all configurations are lost if the rule or policy associated with the object is deleted accidentally.
In the left pane, click Objects >  and check the Unassociated checkbox.
and check the Unassociated checkbox.
Compare Objects
Procedure
|
Step 1 |
In the left pane, click Objects and choose an option. |
|
Step 2 |
Filter the objects on the page to find the objects you want to compare. |
|
Step 3 |
Click the Compare button |
|
Step 4 |
Select up to three objects to compare. |
|
Step 5 |
View the objects, side-by-side, at the bottom of the screen.
|
|
Step 6 |
(Optional) The Relationships box shows how an object is used. It may be associated with a device or a policy. If the object is associated with a device, you can click the device name and then click View Configuration to see the configuration of the device. Security Cloud Control shows you the device's configuration file and highlights the entry for that object. |
Filters
You can use many different filters on the Security Devices and Objects pages to find the devices and objects you are looking for.
To filter, click  in the left-hand pane of the Security Devices, Policies, and Objects tabs:
in the left-hand pane of the Security Devices, Policies, and Objects tabs:
The Security Devices filter allows you to filter by device type, hardware and software versions, snort version, configuration status, connection states, conflict detection, and secure device connectors, and labels. You can apply filters to find devices within a selected device type tab. You can use filters to find devices within the selected device type tab.
The object filter allows you to filter by device, issue type, shared objects, unassociated objects, and object type. You can include system objects in your results or not. You can also use the search field to search for objects in the filter results that contain a certain name, IP address, or port number.
The object type filter allows you to filter objects by type, such as network object, network group, URL object, URL group, service object, and service group. The shared objects filter allows filtering objects having default values or override values.
When filtering devices and objects, you can combine your search terms to create several potential search strategies to find relevant results.
In the following example, filters are applied to search objects that are "Issues (Used OR Inconsistent) AND Shared Objects with Additional Values.

Object Filters
To filter, click  in the left-hand pane of the Objects tab:
in the left-hand pane of the Objects tab:
-
Filter by Device: Lets you pick a specific device so that you can see objects found on the selected device.
-
Issues: Lets you pick unused, duplicate, and inconsistent objects to view.
-
Ignored Issues: Lets you view all the objects whose inconsistencies you had ignored.
-
Shared Objects: Lets you view all the objects that Security Cloud Control has found to be shared on more than one device. You can choose to see shared objects with only default values or override values, or both.
-
Unassociated Objects: Lets you view all the objects that are not associated with any rule or policy.
-
Object Type: Lets you select an object type to see only those type of objects that you have selected, such as network objects, network groups, URL objects, URL groups, service objects, and service groups.
Sub filters – Within each main filter, there are sub-filters you can apply to further narrow down your selection. These sub-filters are based on Object Type – Network, Service, Protocol, etc.
The selected filters in this filter bar would return objects that match the following criteria:
* Objects that are on one of two devices. (Click Filter by Device to specify the devices.) AND are
* Inconsistent objects AND are
* Network objects OR Service objects AND
* Have the word "group" in their object naming convention
Because Show System Objects is checked, the result would include both system objects and user-defined objects.
Show System-Defined Objects Filter
Some devices come with pre-defined objects for common services. These system objects are convenient because they are already made for you and you can use them in your rules and policies. There can be many system objects in the objects table. System objects cannot be edited or deleted.
Show System-Defined Objects is off by default. To display system objects in the object table, check Show System-Defined Objects in the filter bar. To hide system objects in the object table, leave Show System Objects unchecked in the filter bar.
If you hide system objects, they will not be included in your search and filtering results. If you show system objects, they will be included in your object search and filtering results.
Configure Object Filters
You can filter on as few or as many criteria as you want. The more categories you filter by, the fewer results you should expect.
Procedure
|
Step 1 |
In the left pane, click Objects. |
|
Step 2 |
Open the filter panel by clicking the filter icon |
|
Step 3 |
If you want to restrict your results to those found on particular devices:
|
|
Step 4 |
Check Show System Objects to include system objects in your search results. Uncheck Show System Objects to exclude system objects from your search results. |
|
Step 5 |
Check the object Issues you want to filter by. If you check more than one issue, objects in any of the categories you check are included in your filter results. |
|
Step 6 |
Check Ignored issues if you want to see the object that had issues but was ignored by the administrator. |
|
Step 7 |
Check the required filter in Shared Objects if you are filtering for objects shared between two or more devices.
|
|
Step 8 |
Check Unassociated if you are filtering for objects that are not part of any rule or policy. |
|
Step 9 |
Check the Object Types you want to filter by. |
|
Step 10 |
You can also add an object name, IP address, or port number to the Objects search field to find objects with your search criteria among the filtered results. |
When to Exclude a Device from Filter Criteria
When adding a device to filtering criteria, the results show you the objects on a device but not the relationships of those objects to other devices. For example, assume ObjectA is shared between ASA1 and ASA2. If you were to filter objects to find shared objects on ASA1, you would find ObjectA but the Relationships pane would only show you that the object is on ASA1.
To see all the devices to which an object is related, don't specify a device in your search criteria. Filter by the other criteria and add search criteria if you choose to. Select an object that Security Cloud Control identifies and then look in the Relationships pane. You will see all the devices and policies the object is related to.
Unignore Objects
One way to resolve unused, duplicate, or inconsistent objects is to ignore them. You may decide that though an object is unused, a duplicate, or inconsistent, there are valid reasons for that state and you choose to leave the object issue unresolved. At some point in the future, you may want to resolve those ignored objects. As Security Cloud Control does not display ignored objects when you search for object issues, you will need to filter the object list for ignored objects and then act on the results.
Procedure
|
Step 1 |
In the left pane, click Objects and choose an option. |
|
Step 2 |
|
|
Step 3 |
In the Object table, select the object you want to unignore. You can unignore one object at a time. |
|
Step 4 |
Click Unignore in the details pane. |
|
Step 5 |
Confirm your request. Now, when you filter your objects by issue, you should find the object that was previously ignored. |
Deleting Objects
You can delete a single object or mulitple objects.
Delete a Single Object
 Caution |
If cloud-delivered Firewall Management Center is deployed on your tenant: Changes you make to the ASA, FDM, and FTD network objects and groups are reflected in the corresponding cloud-delivered Firewall Management Center network object or group. In addition, an entry is created in the Devices with Pending Changes page for each on-premises management center with Discover & Manage Network Objects enabled, from which you can choose and deploy the changes to the on-premises management center on which you have these objects. Deleting a network object or group from either page deletes the object or group from both pages. |
Procedure
|
Step 1 |
In the left pane, click Objects. |
|
Step 2 |
Locate the object you want to delete by using object filters and the search field, and select it. |
|
Step 3 |
Review the Relationships pane. If the object is used in a policy or in an object group, you cannot delete the object until you remove it from that policy or group. |
|
Step 4 |
In the Actions pane, click the Remove icon |
|
Step 5 |
Confirm that you want to delete the object by clicking OK. |
|
Step 6 |
Review and deploy the changes you made, or wait and deploy multiple changes at once. |
Delete a Group of Unused Objects
As you onboard devices and start resolving object issues, you find many unused objects. You can delete up to 50 unused objects at a time.
Procedure
|
Step 1 |
Use the Issues filter to find unused objects. You can also use the Device filter to find objects that are not associated with a device by selecting No Device. Once you have filtered the object list, the object checkboxes appear. |
|
Step 2 |
Check the Select all checkbox in the object table header to select all the objects found by the filter that appear in the object table; or, check individual checkboxes for individual objects you want to delete. |
|
Step 3 |
In the Actions pane, click the Remove icon |
|
Step 4 |
Review and deploy now the changes you made, or wait and deploy multiple changes at once. |
Network Objects
A network object can contain a host name, a network IP address, a range of IP addresses, a fully qualified domain name (FQDN), or a subnetwork expressed in CIDR notation. Network groups are collections of network objects and other individual addresses or subnetworks you add to the group. Network objects and network groups are used in access rules, network policies, and NAT rules. You can create, update, and delete network objects and network groups using Security Cloud Control.
Note that not all platforms support network objects, such as Cisco Merkai and Multicloud Defense; when you share dynamic objects, Security Cloud Control automatically translates the appropriate information from the originating platform or device into a set of usable information that Security Cloud Control can use.
|
Device type |
IPv4 / IPv6 |
Single Address |
Range of addresses |
Fully Qualified Domain Name |
Subnet using CIDR Notation |
|---|---|---|---|---|---|
|
Meraki |
IPv4 |
Yes |
Yes |
Yes |
Yes |
|
Multicloud Defense |
IPv4 and IPv6 |
Yes |
Yes |
Yes |
Yes |
|
Device type |
IP Value |
Network Object |
Network Groups |
|---|---|---|---|
|
Meraki |
Yes |
Yes |
Yes |
|
Multicloud Defense |
Yes |
Yes |
Yes |
Reusing Network Objects Across Products
If you have a Security Cloud Control tenant with a cloud-delivered Firewall Management Center and one or more on-premises management centers onboarded to your tenant:
-
When you create a Secure Firewall Threat Defense, FDM-managed threat defense, ASA, or Meraki network object or group, a copy of the object is also added to the objects list on the Objects page used when configuring cloud-delivered Firewall Management Center, and vice versa.
-
When you create a Secure Firewall Threat Defense, FDM-managed threat defense, or ASA network object or group, an entry is created in the Devices with Pending Changes page for each On-Premises Firewall Management Center for which Discover & Manage Network Objects is enabled. From this list, you can choose and deploy the object to the on-premises management center on which you want to use the object and discard the ones that you do not want. Navigate , select the on-premises management center, and click Objects to see your objects in the On-Premises Firewall Management Center user interface and assign them to policies.
Changes you make to network objects or groups on either page apply to the object or group instance on both pages. Deleting an object from one page also deletes the corresponding copy of the object from the other page.
Exceptions:
-
If a network object of the same name already exists for cloud-delivered Firewall Management Center, the new Secure Firewall Threat Defense, FDM-managed threat defense, ASA, or Meraki network object will not be replicated on the Objects page of Security Cloud Control.
-
Network objects and groups in onboarded threat defense devices that are managed by on-premises Secure Firewall Management Center are not replicated and cannot be used in cloud-delivered Firewall Management Center.
Note that for on-premises Secure Firewall Management Center instances that have been migrated to cloud-delivered Firewall Management Center, network objects and groups are replicated to the Security Cloud Control objects page if they are used in policies that were deployed to FTD devices.
-
Sharing Network Objects between Security Cloud Control and cloud-delivered Firewall Management Center is automatically enabled on new tenants but must be requested for existing tenants. If your network objects are not being shared with cloud-delivered Firewall Management Center, contact TAC to have the features enabled on your tenant.
-
Sharing network objects between Security Cloud Control and On-Premises Management Center is not automatically enabled on Security Cloud Control for new on-premises management centers onboarded to Security Cloud Control. If your network objects are not being shared with On-Premises Management Center, ensure Discover & Manage Network Objects toggle button is enabled for the on-premises management center in Settings or contact TAC to have the features enabled on your tenant.
Viewing Network Objects
Network objects you create using Security Cloud Control and those Security Cloud Control recognizes in an onboarded device's configuration are displayed on the Objects page. They are labeled with their object type. This allows you to filter by object type to quickly find the object you are looking for.
When you select a network object on the Objects page, you see the object's values in the Details pane. The Relationships pane shows you if the object is used in a policy and on what device the object is stored.
When you click on a network group you see the contents of that group. The network group is a conglomerate of all the values given to it by the network objects.
Objects Associated with Meraki Devices
About Objects Used with Meraki Devices
The Meraki dashboard utilizes groups of IP addresses, protocols, or port ranges in source and destination fields in outbound access control rules. Once onboarded, Security Cloud Control translates IP address into network objects, and application layer protocol values into either service objects or protocol objects.
A single rule in Security Cloud Control can translate into multiple rules in the dashboard. For example, if you add an ASA protocol group that includes both TCP and UDP protocols to a single access control rule in Security Cloud Control, Security Cloud Control translates the one Security Cloud Control rule into multiple rules in the dashboard: one rule containing a TCP protocol and one rule containing a UDP protocol.
Note that the Meraki dashboard and Security Cloud Control both support CIDR subnet notation. For more information on layer 3 switch interfaces and MX device layout, see the Meraki Knowledge Base.
Which Objects Can You Use With a Meraki Device in Security Cloud Control?
There are no objects in Security Cloud Control that are exclusive to MX devices. Instead, you can create or share FTD, FDM, and ASA objects and associate these objects in rules that are deployed to the device. Because Meraki is not fully compatible with FTD and ASA objects, there may be a few limitations that affect how the MX device uses objects.
Note that if you associate an FTD, FDM, and ASA objects with a MX device, that object becomes shared. Any changes to that object will affect all the devices it is shared with and the devices' configuration status will appear as Not Synced. See Shared Objects for more information. For additional object states that could affect your objects, see the Related Articles section listed at the bottom of this page.
Meraki does not support objects containing IPv6 addresses or FQDNs.
|
Object in Security Cloud Control |
Compatible with Meraki |
|---|---|
|
Protocol Objects |
TCP, UDP, ICMP |
|
Network Objects |
yes |
|
Network Groups |
yes |
|
Service Objects |
yes |
|
ASA Service Groups |
no |
|
FTD Service Groups |
no |
Local Network Objects and Object Groups From the Meraki Cloud
Network objects and object groups provide easier management of firewall rules for Meraki devices. They serve as labels to IP Subnets and FQDN that can be used on access policies such as firewall rules. If there are needs to modify multiple access policies that use the same IP Subnets or FQDN, you only need to modify the network object to have it reflect on all policies.At this time, you must use the Meraki dashboard to create and modify these objects. For more information about what these objects can do for your environment, see Meraki's Network Objects Highlights.
 Note |
Once a device configuration referencing a Meraki network object or network object group is onboarded or synchronized to the Security Cloud Control UI, these objects are displayed as FTD Network objects. These objects and object groups are read-only in Security Cloud Control. |
What Do Meraki Rules Look Like in Security Cloud Control
You can view the objects from the device's policy page, or you can filter the objects page based on device. From the policy page you can view, edit, and reorder the access control rules. Because Security Cloud Control translates the outbound rules from the Meraki dashboard into access control rules with objects, rules and protocols from the Meraki dashboard may look different. The following table addresses the new names for protocols once the device is onboarded to Security Cloud Control:
|
Rule or Protocol Header in the Meraki dashboard |
Rule or Object Header in Security Cloud Control |
|---|---|
|
Policy |
Action |
|
Source IP |
Network Object or Network Group |
|
Destination IP |
Network Object or Network Group |
|
Source Port |
Network Object or Network Group |
|
Destination Port |
Network Object or Network Group |
|
Layer 3 Application Protocol |
Ports (Protocol Groups, Port Groups, or Service Objects) |
The following is an example of what the outbound rules from the Meraki dashboard look in Security Cloud Control:
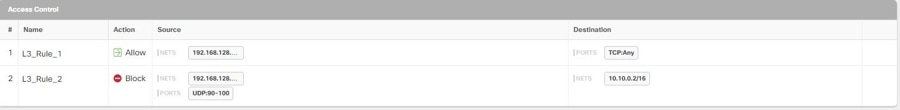
Create a Local Meraki Network Object
A local Meraki network object must be made in the Merkai dashboard. If you have a Meraki device that has not been onboarded to Security Cloud Control yet, any pre-existing local objects are onboarded with the device; if you have a Meraki device that has been onboarded, sychronize the device in Security Cloud Control to read the new configuration and local objects.
 Note |
Once a device configuration referencing a Meraki network object or network object group is onboarded or synchronized with the Security Cloud Control UI, these objects are displayed as FTD Network objects or object groups. These objects and object groups are read-only in Security Cloud Control. |
Before you begin
Procedure
|
Step 1 |
Log into the Meraki dashboard and create a local object or a local object group. See the Meraki Network Objects Configuration Guide for more information. |
|
Step 2 |
Log into Security Cloud Control. Note: If you have not yet onboarded your Meraki device to Security Cloud Control, see Onboard an MX Device to Security Cloud Control for more information. Onboarding a device also onboards all the pre-existing objects. |
|
Step 3 |
In the left pane, click . |
|
Step 4 |
Locate the Merkai device and select it so the device row is highlighted. The device status is Conflict detected. In the pane located to the right, select either Review Conflict to review the changes made to the device's configuration or Accept without Review to accept all configuration changes. |
Create or Edit a Meraki Network Object or Network Group
MX devices use the same format as Firepower and ASA network objects and can contain a host name, an IP address or a subnet address expressed in CIDR notation. Network groups are a collection of network objects and other individual addresses or subnets you add to the group. Network objects and network groups are used in access rules. You can create, read, update, and delete network objects and network groups using Security Cloud Control.
IP addresses that can be added to network objects
|
Device type |
IPv4 / IPv6 |
Single Address |
Range of addresses |
Fully Qualified Domain Name |
Subnet using CIDR Notation |
|---|---|---|---|---|---|
|
MX |
IPv4 |
Yes |
Yes |
No |
Yes |
 Note |
If cloud-delivered Firewall Management Center is deployed on your tenant: When you create an FTD, FDM, or ASA network object or group on the Objects page, a copy of the object is automatically added to the cloud-delivered Firewall Management Center and vice-versa. In addition, an entry is created in the Devices with Pending Changes page for each on-premises management center with Discover & Manage Network Objects enabled, from which you can choose and deploy the objects to the on-premises management center on which you want these objects. |
 Caution |
If cloud-delivered Firewall Management Center is deployed on your tenant: Changes you make to the ASA, FDM, and FTD network objects and groups are reflected in the corresponding cloud-delivered Firewall Management Center network object or group. In addition, an entry is created in the Devices with Pending Changes page for each on-premises management center with Discover & Manage Network Objects enabled, from which you can choose and deploy the changes to the on-premises management center on which you have these objects. Deleting a network object or group from either page deletes the object or group from both pages. |
Create a Meraki Network Object
 Note |
If cloud-delivered Firewall Management Center is deployed on your tenant: When you create an FTD, FDM, or ASA network object or group on the Objects page, a copy of the object is automatically added to the cloud-delivered Firewall Management Center and vice-versa. In addition, an entry is created in the Devices with Pending Changes page for each on-premises management center with Discover & Manage Network Objects enabled, from which you can choose and deploy the objects to the on-premises management center on which you want these objects. |
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Click |
|
Step 3 |
Enter an object name. |
|
Step 4 |
Select Create a network object. |
|
Step 5 |
In the Value section, enter a single IP address or a subnet address expressed in CIDR notation. |
|
Step 6 |
Click Add. |
|
Step 7 |
Review and deploy now the changes you made, or wait and deploy multiple changes at once. |
Create a Meraki Network Group
A network group is made up of multiple network objects or IP addresses.
If you want your network group to be made up of network objects, use the "Create a Network Object" procedure above to create individual network objects for your IP addresses.
 Note |
If cloud-delivered Firewall Management Center is deployed on your tenant: When you create an FTD, FDM, or ASA network object or group on the Objects page, a copy of the object is automatically added to the cloud-delivered Firewall Management Center and vice-versa. In addition, an entry is created in the Devices with Pending Changes page for each on-premises management center with Discover & Manage Network Objects enabled, from which you can choose and deploy the objects to the on-premises management center on which you want these objects. |
Procedure
|
Step 1 |
In the Security Cloud Control navigation bar on the left, click Manage > Objects. |
|
Step 2 |
Click |
|
Step 3 |
Enter an object name. |
|
Step 4 |
Select Create a network group. |
|
Step 5 |
Click Add Object, select the network object from the list and click Select. Continue to do this until you have added all the network objects you want. |
|
Step 6 |
Click Add. |
|
Step 7 |
Review and deploy now the changes you made, or wait and deploy multiple changes at once. |
Edit a Firepower Network Object or Network Group
 Caution |
If cloud-delivered Firewall Management Center is deployed on your tenant: Changes you make to the ASA, FDM, and FTD network objects and groups are reflected in the corresponding cloud-delivered Firewall Management Center network object or group. In addition, an entry is created in the Devices with Pending Changes page for each on-premises management center with Discover & Manage Network Objects enabled, from which you can choose and deploy the changes to the on-premises management center on which you have these objects. Deleting a network object or group from either page deletes the object or group from both pages. |
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Locate the object you want to edit by using object filters and search field. |
|
Step 3 |
Select the object you want to edit. |
|
Step 4 |
Click the edit button |
|
Step 5 |
Edit the values in the dialog box in the same fashion that you created them in the procedures above. |
|
Step 6 |
Click Save. |
|
Step 7 |
Security Cloud Control displays the policies that will be affected by the change. Click Confirm to finalize the change to the object and any policy affected by it. |
|
Step 8 |
Review and deploy now the changes you made, or wait and deploy multiple changes at once. |
Deleting Network Objects and Groups in Security Cloud Control
If Cloud-delivered Firewall Management Center is deployed on your tenant:
Deleting a network object or group from the Manage > Objects page deletes the replicated network object or group from the Manage > Objects page on the cloud-delivered Firewall Management Center and vice-versa.
Service Objects
Protocol Objects
Protocol objects are a type of service object that contain less-commonly used or legacy protocols. Protocol objects are identified by a name and protocol number. Security Cloud Control recognizes these objects in ASA and Firepower (FDM-managed device) configurations and gives them their own filter of "Protocols" so you can find them easily.
ICMP Objects
An Internet Control Message Protocol (ICMP) object is a service object specifically for ICMP and IPv6-ICMP messages. Security Cloud Control recognizes these objects in ASA and Firepower configurations when those devices are onboarded and Security Cloud Control gives them their own filter of "ICMP" so you can find the objects easily.
Using Security Cloud Control, you can rename or remove ICMP objects from an ASA configuration. You can use Security Cloud Control to create, update, and delete ICMP and ICMPv6 objects in a Firepower configuration.
 Note |
For the ICMPv6 protocol, AWS does not support choosing specific arguments. Only rules that allow all ICMPv6 messages are supported. |
Create or Edit a Meraki Service Object
About Service Objects
Service objects are reusable components that specify a TCP/IP protocol and a port. Security Cloud Control categorizes these objects as service objects. When you deploy to the MX device, Security Cloud Control translates the objects into protocols or port ranges. See Objects Associated with Meraki Devices for more information about how Security Cloud Control handles Meraki protocols as objects.
Create a Service Object
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Click |
|
Step 3 |
Enter an object name and description. |
|
Step 4 |
Select Create a service object. |
|
Step 5 |
Click the Service Type button and select the protocol for which you want to create an object. |
|
Step 6 |
Enter the information to identify the protocol by taking one of these actions:
|
|
Step 7 |
Click Add. |
|
Step 8 |
Review and deploy now the changes you made, or wait and deploy multiple changes at once. |
Create a Service Group
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
||
|
Step 2 |
Click
|
||
|
Step 3 |
Enter an object name and description. |
||
|
Step 4 |
Select Create a service group. |
||
|
Step 5 |
Add an existing object by clicking Add Object, selecting an object, and clicking Select. Repeat this step to add more objects. |
||
|
Step 6 |
Click Add when you are done adding service objects and service values to the service group. |
||
|
Step 7 |
Review and deploy now the changes you made, or wait and deploy multiple changes at once. |
Edit a Service Object or a Service Group
Procedure
|
Step 1 |
In the left pane, click Manage > Objects. |
|
Step 2 |
Filter the objects to find the object you want to edit and then select the object in the object table. |
|
Step 3 |
In the details pane, click edit |
|
Step 4 |
Edit the values in the dialog box in the same fashion that you created them in the procedures above. |
|
Step 5 |
Click Save. |
|
Step 6 |
Security Cloud Control displays the policies that will be affected by the change. Click Confirm to finalize the change to the object and any policy affected by it. The object is now ready to be used in the Meraki policy. |
|
Step 7 |
Review and deploy now the changes you made, or wait and deploy multiple changes at once. |
 .
.
 .
.
 , then click
, then click  in the details pane.
in the details pane.

 .
.
 in the Actions pane. (Simple edits may also be performed inline without entering edit mode.)
in the Actions pane. (Simple edits may also be performed inline without entering edit mode.)
 . The devices affected by these changes show the status "Not Synced" in the Devices and
. The devices affected by these changes show the status "Not Synced" in the Devices and  on the details pane. Review any warnings and click
on the details pane. Review any warnings and click  in the navigation bar to view the results of the bulk deploy.
in the navigation bar to view the results of the bulk deploy.


 Feedback
Feedback