FMC administration page permits to configure a link between Cisco Cyber Vision with your Firepower Management Center. This
connection will permit to send regularly (every 10 seconds) the components discovered by Cisco Cyber Vision. Every 10 seconds
a list of new discovered components will be sent with the following properties in Cisco Cyber Vision:
The configuration of this connection consists of adding the IP address of FMC, then importing a certificate in Cisco Cyber
Vision.

In FMC, to download the necessary certificate, please navigate to "System" then to "Integration" and open the "Host Input
Client" tab. In the tab create a new Client with the button "Create Client". Add the Cisco Cyber Vision Center IP address
as host name, then download the pkcs12 certificate.
Then, in FMC, menu "Policies", "Application Detectors" add a new Product Map with the button "Create Product Map Set". Please
create the new product Map with the exact name and case as presented below:

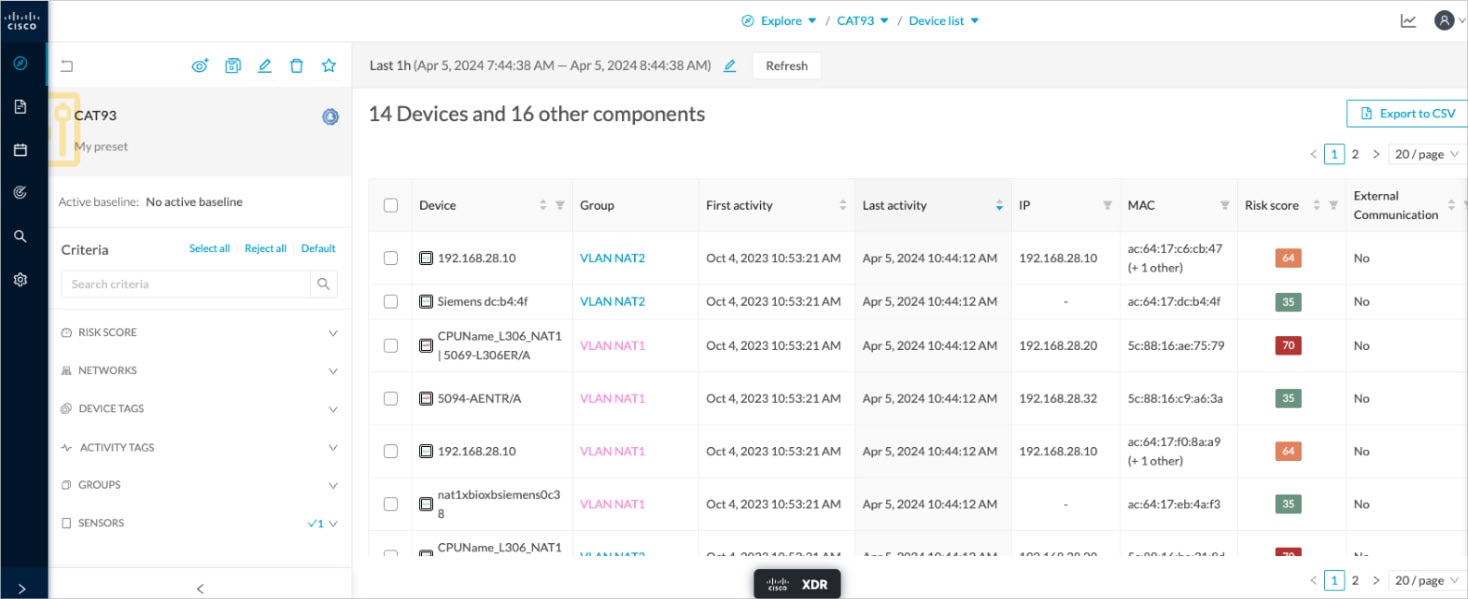
The created hosts could be consulted in FMC, menu "Analysis", tab "Hosts – Network Map":







 Feedback
Feedback