Overview
The Layer3 Network Address Translation (L3NAT) for IOx applications is supported starting with IOS-XE release 17.14.1. This
feature uses the management IP of the switch as a proxy for all applications within the routed network. The complexity and
overhead associated with managing multiple public IP addresses are reduced. The IE3x00 platform supports the L3NAT feature
with the Cisco Cyber Vision (CCV) IOx application. However, it cannot be used to NAT other Ethernet traffic from hosts connected
to its physical Ethernet ports.
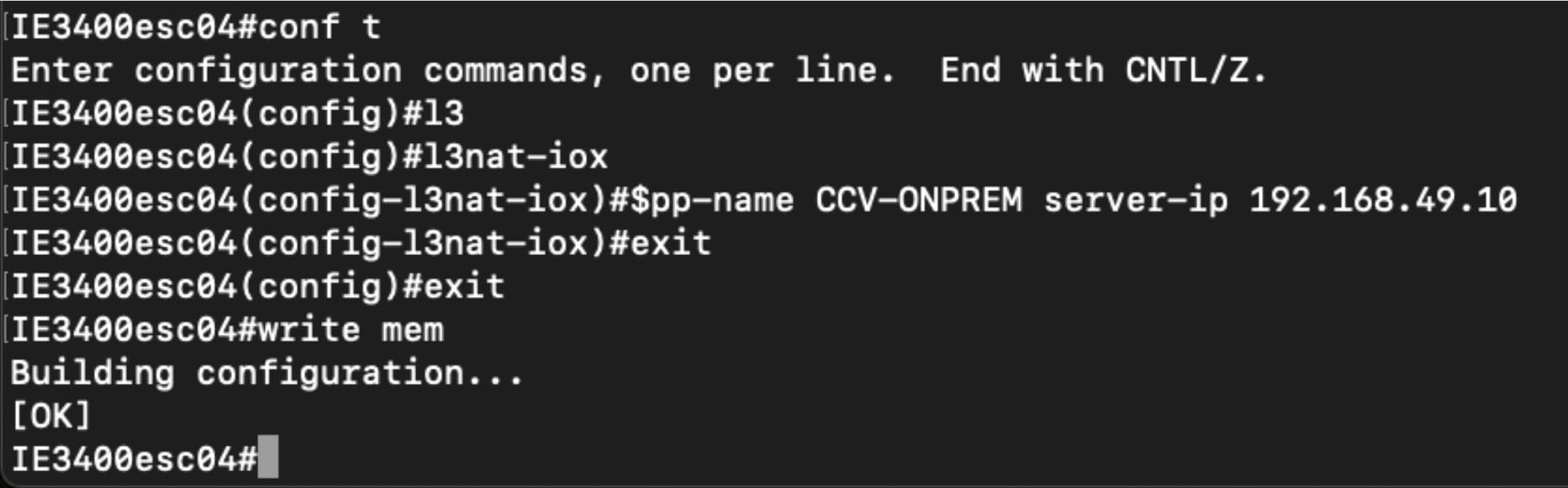
L3NAT-IOx
L3NAT is a networking technique used to translate private IP addresses in an internal network to a public IP address before
packets are sent to an external network at the network layer of the OSI model. The L3NAT-IOx feature utilizes hardware components
such as Application-Specific Integrated Circuits (ASICs) and Field-Programmable Gate Arrays (FPGAs) for implementation.
When a Cyber Sensor application communicates with the external CCV server, the NAT protocol translates the source private
IP address of the Cyber Sensor Application to the public IP address of the Management Switched Virtual Interface (SVI) of
the switch. This translation allows the packets to navigate through the external network, gives the impression that they originate
from the switch management SVI IP address.
When the external CCV server communicates with the Cyber Sensor Application, the NAT protocol reverses the translation. Incoming
packets addressed to the public IP address of the switch management SVI are translated to the private IP address of the destination
Cyber Sensor Application. This ensures seamless communication between the application and external servers.
Guidelines and Restrictions
The guidelines and restrictions for L3NAT-IOx are as follows:
-
This feature only works with the CCV application and doesn't support any other IOx applications.
-
Only static translation is supported.
-
Translation is restricted to TCP and UDP packets exclusively.
-
Users need to set up an extra SVI on IE for the private network used by the application. The IP assigned to this SVI will
act as the default gateway for the application.
-
This feature requires a Network Advantage license.
-
You can not retrieve L3NAT-IOx statistics using YANG with Network Configuration Protocol (NETCONF).
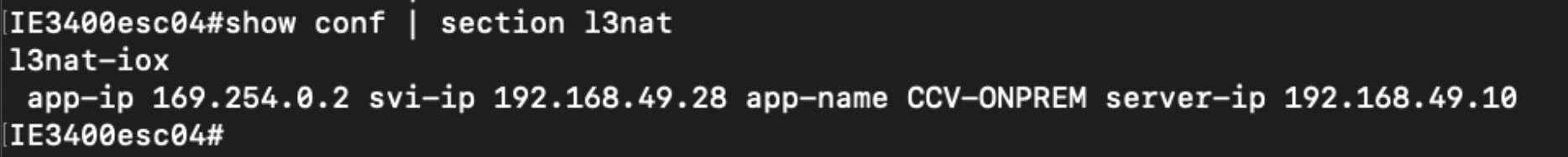
Configuring L3NAT-IOx
The configuration example is based on the following topology:

The above diagram shows application hosting on the switch using a Private IP address. The CCV sensor application is installed
on the access devices connected to hosts. Devices located in the 192.168.49.0/24 network are assigned management IP addresses.
The CCV sensor is installed using the private IP network 169.254.0.1/30.
Once you are done with the initial configuration, proceed with the application installation and deployment following one of
the procedures below with in mind the IP used in the system with the l3nat_iox feature enabled:



 Feedback
Feedback