About Smart CLI and FlexConfig
FTD uses ASA configuration commands to implement some features, but not all features. There is no unique set of the FTD configuration commands.
You can configure features using the CLI using the following methods:
-
Smart CLI—(Preferred method.) A Smart CLI template is a pre-defined template for a particular feature. All of the commands needed for the feature are provided, and you simply need to select values for variables. The system validates your selection, so that you are more likely to configure a feature correctly. If a Smart CLI template exists for the feature you want, you must use this method.
-
FlexConfig—The FlexConfig policy is a collection of FlexConfig objects. The FlexConfig objects are more free-form than Smart CLI templates, and the system does no CLI, variable, or data validation. You must know ASA configuration commands and follow the ASA configuration guides to create a valid sequence of commands.
The point of Smart CLI and FlexConfig is to allow you to configure features that are not directly supported through FDM policies and settings.
 Caution |
Cisco strongly recommends using Smart CLI and FlexConfig only if you are an advanced user with a strong ASA background and at your own risk. You may configure any commands that are not prohibited. Enabling features through Smart CLI and FlexConfig may cause unintended results with other configured features. You may contact the Cisco Technical Assistance Center for support concerning Smart CLI and FlexConfig objects that you have configured. The Cisco Technical Assistance Center does not design or write custom configurations on any customer's behalf. Cisco expresses no guarantees for correct operation or interoperability with other FTD features. Smart CLI and FlexConfig features may become deprecated at any time. For fully guaranteed feature support, you must wait for the FDM support. When in doubt, do not use Smart CLI or FlexConfig. |
The following topics explain these features in more detail.
Recommended Usage for Smart CLI and FlexConfig
There are two main recommended uses for FlexConfig:
-
You are migrating from ASA to FTD, and there are compatible features you are using (and need to continue using) that the FDM does not directly support. In this case, use the show running-config command on the ASA to see the configuration for the feature and create your FlexConfig objects to implement it. Verify by comparing show running-config output on the two devices.
-
You are using the FTD but there is a setting or feature that you need to configure, e.g. the Cisco Technical Assistance Center tells you that a particular setting should resolve a specific problem you are encountering. For complicated features, use a lab device to test the FlexConfig and verify that you are getting the expected behavior.
Before trying to recreate an ASA configuration, first determine if you can configure an equivalent feature in standard policies. For example, the access control policy includes intrusion detection and prevention, HTTP and other types of protocol inspection, URL filtering, application filtering, and access control, which the ASA implements using separate features. Because many features are not configured using CLI commands, you will not see every policy represented within the output of show running-config .
 Note |
At all times, keep in mind that there is not a one-to-one overlap between ASA and FTD. Do not attempt to completely recreate an ASA configuration on the FTD device. You must carefully test any feature that you configure using FlexConfig. |
CLI Commands in Smart CLI and FlexConfig Objects
The FTD uses ASA configuration commands to configure some features. Although not all ASA features are compatible with FTD, there are some features that can work on the FTD but that you cannot configure in the FDM policies. You can use Smart CLI and FlexConfig objects to specify the CLI required to configure these features.
If you decide to use Smart CLI or FlexConfig to manually configure a feature, you are responsible for knowing and implementing the commands according to the proper syntax. FlexConfig does not validate CLI command syntax. For more information about proper syntax and configuring CLI commands, use the ASA documentation as a reference:
-
ASA CLI configuration guides explain how to configure a feature. Find the guides at http://www.cisco.com/c/en/us/support/security/asa-5500-series-next-generation-firewalls/products-installation-and-configuration-guides-list.html
-
ASA command references provide additional information sorted by command name. Find the references at http://www.cisco.com/c/en/us/support/security/asa-5500-series-next-generation-firewalls/products-command-reference-list.html
The following topics explain more about configuration commands.
How Software Upgrades Affect the FlexConfig Policy
Each new version of the FTD software adds support for configuring features in the FDM. Sometimes, these new features can overlap with features you have previously configured using FlexConfig.
After upgrade, you need to examine the FlexConfig policy and objects. If any contain commands that have become prohibited due to added support within FDM or Smart CLI, icons in the objects list and messages indicate the problem. Please take the time to redo your configuration. Use the list of prohibited commands for help in determining where the commands should now be configured.
The system will not prevent you from deploying changes while the FlexConfig objects that are attached to the FlexConfig policy contain newly-prohibited commands. However, you will be prevented from creating new Smart CLI objects until you resolve all issues noted in the FlexConfig policy.
You can simply remove the problematic objects from the FlexConfig policy, as the restriction applies only to those objects you are actively deploying to the device configuration. Thus, you can remove the objects, then use them as a reference as you create the corresponding Smart CLI or integrated the FDM configuration. Once you are satisfied with the new configuration, you can simply delete the objects. If the removed objects contain some non-prohibited elements, you can edit them to remove the unsupported commands, and then reattach the objects to the FlexConfig policy.
Determine the ASA Software Version and Current CLI Configuration
Because the system uses ASA software commands to configure some features, you need to determine the current ASA version used in software running on the FTD device. This version number indicates which ASA CLI configuration guides to use for instructions on configuring a feature. You also should examine the current CLI-based configuration and compare it to the ASA configuration you want to implement.
Keep in mind that any ASA configuration will be very different from the FTD configuration. Many FTD policies are configured outside of the CLI, so you cannot see the configuration by looking at the commands. Do not try to create a one-to-one correspondence between an ASA and FTD configuration.
To view this information, either open the CLI Console in the FDM or make an SSH connection to the device's management interface and issue the following commands:
-
show version system and look for the Cisco Adaptive Security Appliance Software Version number.
-
show running-config to view the current CLI configuration.
-
show running-config all to include all the default commands in the current CLI configuration.
Prohibited CLI Commands
The purpose of Smart CLI and FlexConfig is to configure features that are available on ASA devices that you cannot configure on the FTD devices using the FDM.
Thus, you are prevented from configuring ASA features that have equivalents in the FDM. The following table lists some of these prohibited command areas. This list contains many parent commands that enter configuration modes. The prohibition of the parent includes the prohibition of the children commands. It also includes the no version of the commands and their associated clear commands.
The FlexConfig object editor prevents you from including these commands in the object. This list does not apply to Smart CLI templates, as they include only those commands you can validly configure.
|
Prohibited CLI Command |
Comments |
|---|---|
|
aaa |
Use . |
|
aaa-server |
Use . |
|
access-group |
Use to configure access rules. |
|
access-list |
Partially blocked.
|
|
anyconnect-custom-data |
Use to configure AnyConnect Client. |
|
asdm |
This feature does not apply to a FTD system. |
|
as-path |
Create Smart CLI AS Path objects and use them in a Smart CLI BGP object to configure an autonomous system path filter. |
|
attribute |
— |
|
auth-prompt |
This feature does not apply to a FTD system. |
|
boot |
— |
|
call-home |
— |
|
captive-portal |
Use to configure the captive portal used for active authentication. |
|
clear |
— |
|
client-update |
— |
|
clock |
Use to configure system time. |
|
cluster |
— |
|
command-alias |
— |
|
community-list |
Create Smart CLI Expanded Community List or Standard Community List objects and use them in a Smart CLI BGP object to configure a community list filter. |
|
compression |
— |
|
configure |
— |
|
crypto |
On the Objects page, use Certificates, IKE Policies, and IPSec Proposals. |
|
dhcp-client |
— |
|
dhcpd |
Use . |
|
dns |
Configure DNS groups using , and assign the groups using . |
|
dns-group |
Configure DNS groups using , and assign the groups using . |
|
domain-name |
Configure DNS groups using , and assign the groups using . |
|
dynamic-access-policy-config dynamic-access-policy-record |
— |
|
enable |
— |
|
event |
— |
|
failover |
— |
|
fips |
— |
|
firewall |
FDM supports routed firewall mode only. |
|
hostname |
Use . |
|
hpm |
This feature does not apply to a FTD system. |
|
http |
Use the Data Interfaces tab on . |
|
inline-set |
— |
|
interface for BVI, Management, Ethernet, GigabitEthernet, and subinterfaces. |
Partially blocked. Configure physical interfaces, subinterfaces, and Bridge Virtual Interfaces on the page. You can then configure additional options using FlexConfig. However, the following interface mode commands are prohibited for these types of interface.
|
|
interface for vni , redundant , tunnel , portchannel |
Configure interfaces on the page. FDM does not support these types of interface. |
|
ip audit |
This feature does not apply to a FTD system. Instead, apply intrusion policies using access control rules. |
|
ip-client |
To configure the system to use data interfaces as the management gateway, use . |
|
ip local pool |
Use to configure address pools. |
|
ipsec |
— |
|
ipv6 |
Create Smart CLI IPv6 Prefix List objects and use them in a Smart CLI BGP object to configure prefix list filtering for IPv6. |
|
ipv6-vpn-addr-assign |
Use to configure address pools. |
|
isakmp |
Use . |
|
jumbo-frame |
The system automatically enables jumbo frame support if you increase the MTU of any interface over the default 1500. |
|
ldap |
— |
|
license-server |
Use . |
|
logging |
Use and . However, you can configure the logging history command in FlexConfig. |
|
management-access |
— |
|
migrate |
Use and to enable IKEv2 support. |
|
mode |
FDM supports single context mode only. |
|
mount |
— |
|
mtu |
Configure MTU per interface on . |
|
nat |
Use . |
|
ngips |
— |
|
ntp |
Use |
|
object-group network object network |
Use . You cannot create network objects or groups in FlexConfig, but you can use network objects and groups defined in the object manager inside the template as variables. |
|
object service |natorigsvc object service |natmappedsvc |
The object service command is allowed in general, but you cannot edit the internal objects named |natorigsvc or |natmappedsvc. In these names, the vertical bar is intentional and it is the first character of the restricted object names. |
|
passwd password |
— |
|
password-policy |
— |
|
policy-list |
Create Smart CLI Policy List objects and use them in a Smart CLI BGP object to configure a policy list. |
|
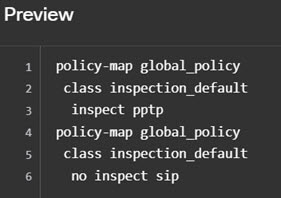
policy-map sub-commands |
You cannot configure the following commands in a policy map.
|
|
prefix-list |
Create Smart CLI IPv4 Prefix List objects and use them in a Smart CLI OSPF or BGP object to configure prefix list filtering for IPv4. |
|
priority-queue |
— |
|
privilege |
— |
|
reload |
You cannot schedule reloads. The system does not use the reload command to restart the system, it uses the reboot command. |
|
rest-api |
This feature does not apply to a FTD system. The REST API is always installed and enabled. |
|
route |
Use to configure static routes. |
|
route-map |
Create Smart CLI Route Map objects and use them in a Smart CLI OSPF or BGP object to configure route maps. |
|
router bgp |
Use the Smart CLI templates for BGP. |
|
router ospf |
Use the Smart CLI templates for OSPF. |
|
scansafe |
This feature does not apply to a FTD system. Instead, configure URL filtering in access control rules. |
|
setup |
This feature does not apply to a FTD system. |
|
sla |
— |
|
ssh |
Use the Data Interfaces tab on . |
|
ssl |
— |
|
telnet |
FTD does not support Telnet connections. Use SSH instead of Telnet to access the device CLI. |
|
time-range |
— |
|
tunnel-group |
Use and . |
|
tunnel-group-map |
Use and . |
|
user-identity |
Use . |
|
username |
To create CLI users, open an SSH or console session to the device and use the configure user commands. |
|
vpdn |
— |
|
vpn |
— |
|
vpn-addr-assign |
— |
|
vpnclient |
— |
|
vpn-sessiondb |
— |
|
vpnsetup |
— |
|
webvpn |
— |
|
zone |
— |
|
zonelabs-integrity |
This feature does not apply to a FTD system. |
Smart CLI Templates
The following table explains the Smart CLI templates based on the feature.
|
Feature |
Templates |
Description |
|---|---|---|
|
Objects: AS Path |
ASPath |
Create ASPath objects for use with routing protocol objects. |
|
Objects: Access List |
Extended Access List Standard Access List |
Create extended or standard ACLs for use with routing objects. You can also refer to these objects by name from FlexConfig objects that configure permitted commands that use ACLs. |
|
Objects: Community List |
Expanded Community List Standard Community List |
Create expanded or standard community lists for use with routing objects. |
|
Objects: Prefix List |
IPV4 Prefix List IPV6 Prefix List |
Create IPv4 or IPv6 prefix lists for use with routing objects. |
|
Objects: Policy List |
Policy List |
Create policy lists for use with routing objects. |
|
Objects: Route Map |
Route Map |
Create route maps for use with routing objects. |
|
Routing: BGP |
BGP |
Use the BGP template to configure the routing process. |
|
Routing: OSPFv2 |
OSPF OSPF Interface Settings |
Use the OSPF template to configure the routing process, and the Interface template to configure per-interface OSPF behavior. Tips:
|






 Feedback
Feedback