End-to-End Procedure
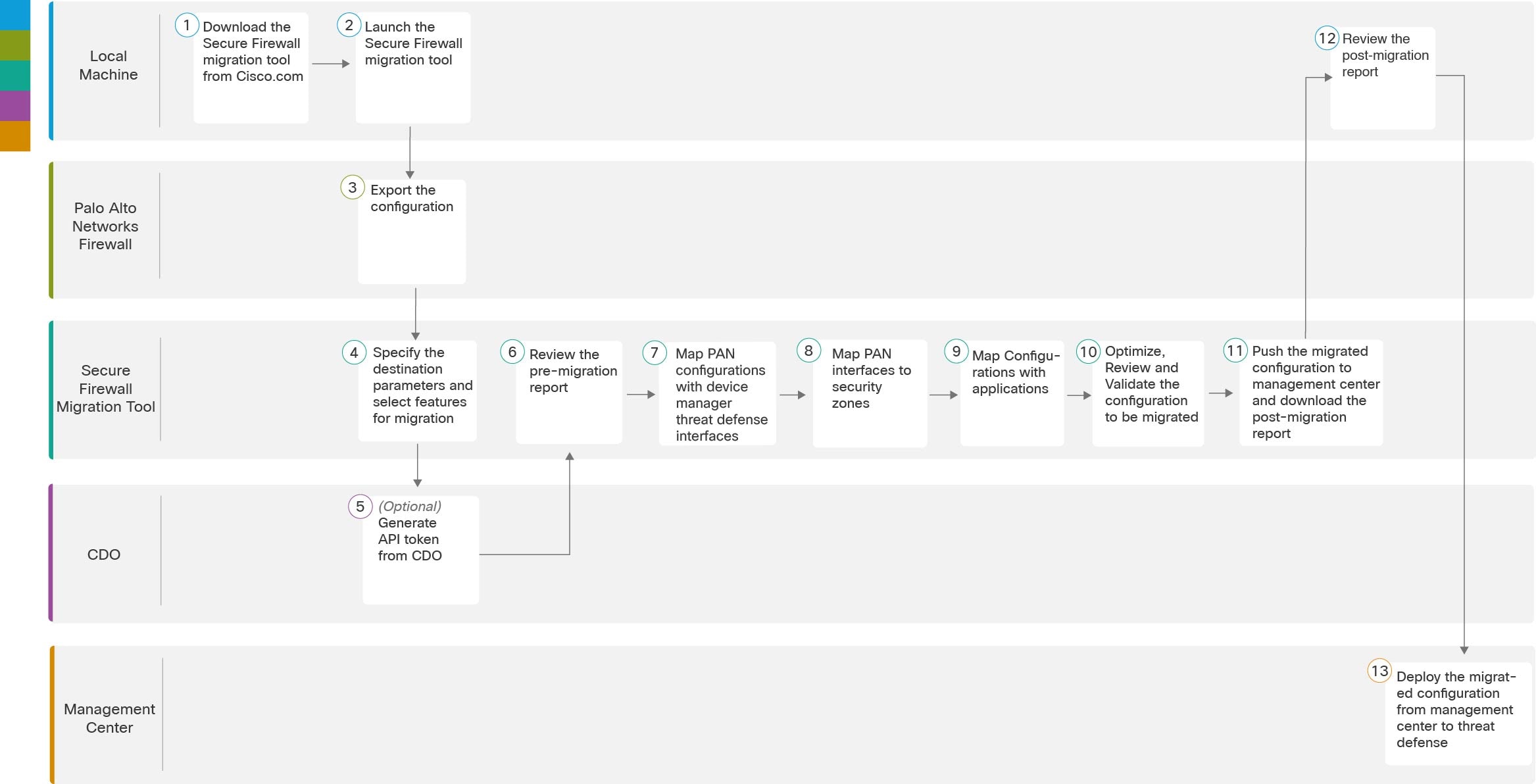
The following flowchart illustrates the workflow for migrating a Palo Alto Networks firewall to threat defense using the Secure Firewall migration tool.
|
Workspace |
Steps |
|
|---|---|---|
|
|
Local Machine |
Download the latest version of Secure Firewall migration tool from Cisco.com. For detailed steps, see Download the Secure Firewall migration tool from Cisco.com. |
|
|
Local Machine |
Launch the Secure Firewall migration tool on your local machine, see Launch the Secure Firewall Migration Tool. |
|
|
Palo Alto Networks Firewall |
Export the Configuration File: To export the configuration from Palo Alto Networks Firewall, see Export the Configuration from Palo Alto Networks. |
|
|
Secure Firewall Migration Tool |
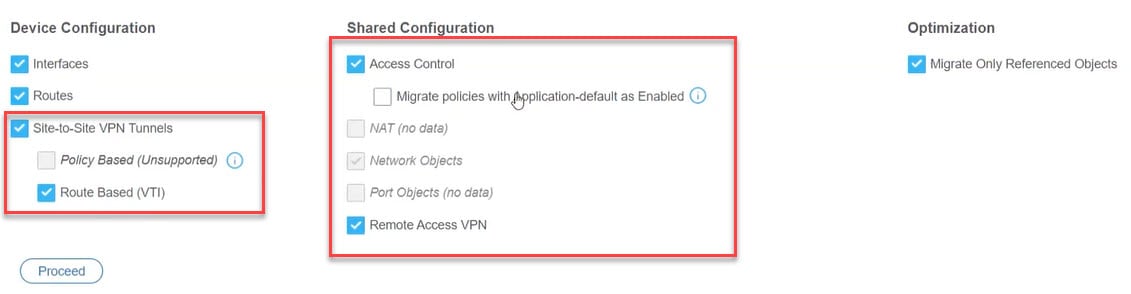
During this step, you can specify the destination parameters for the migration. For detailed steps, see Specify Destination Parameters for the Secure Firewall Migration Tool. |
|
|
Security Cloud Control |
(Optional) This step is optional and only required if you have selected cloud-delivered Firewall Management Center as destination management center. For detailed steps, see Specify Destination Parameters for the Secure Firewall Migration Tool, step 1. |
|
|
Secure Firewall Migration Tool |
Navigate to where you downloaded the pre migration report and review the report. For detailed steps, see Review the Pre-Migration Report. |
|
Secure Firewall Migration Tool |
To ensure that the PAN configuration is migrated correctly, map the PAN interfaces to the appropriate threat defense interface objects, security zones and interface groups. For detailed steps, see Map PAN Firewall Configurations with Secure Firewall Device Manager Threat Defense Interfaces |
|
|
|
Secure Firewall Migration Tool |
Map the PAN interfaces to the appropriate security zones, see Map PAN interfaces to security zones for detailed steps. |
|
|
Secure Firewall Migration Tool |
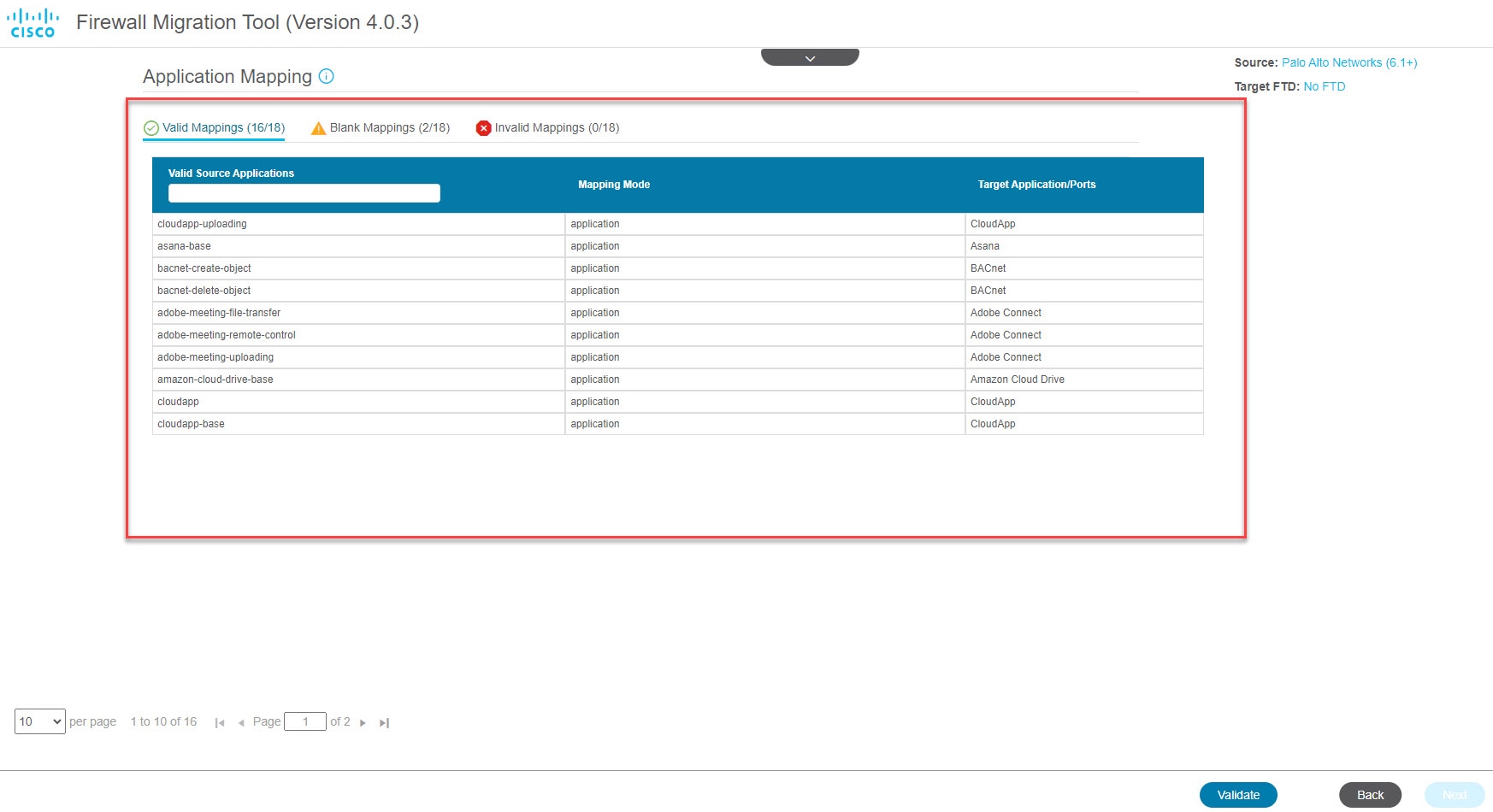
You can map PAN configuration to the corresponding target applications, see Map Configurations with Applications for detailed steps. |
|
|
Secure Firewall Migration Tool |
Optimize and review the configuration carefully and validate that it is correct and matches how you want to configure the threat defense device. For detailed steps, see Optimize, Review and Validate the Configuration to be Migrated. |
|
|
Secure Firewall Migration Tool |
This step in the migration process sends the migrated configuration to management center and allows you to download the post-migration report. For detailed steps, see Push the Migrated Configuration to Management Center. |
|
|
Local Machine |
Navigate to where you downloaded the post migration report and review the report. For detailed steps, see Review the Post-Migration Report and Complete the Migration. |
|
|
Management Center |
Deploy the migrated configuration from the management center to threat defense. For detailed steps, see Review the Post-Migration Report and Complete the Migration. |


 ) to export the table to an editable Excel sheet.
) to export the table to an editable Excel sheet.
 ). The migration tool reads the entries in the Excel and automatically adds them to the corresponding preshared key columns
of the VPN configurations.
). The migration tool reads the entries in the Excel and automatically adds them to the corresponding preshared key columns
of the VPN configurations.
 Feedback
Feedback