About the ASA
The ASA provides advanced stateful firewall and VPN concentrator functionality in one device.
Unsupported Features
The following ASA features are not supported on the Firepower 2100:
-
Integrated Routing and Bridging
-
Redundant interfaces
-
Clustering
-
Clientless SSL VPN with KCD
-
ASA REST API
-
ASA FirePOWER module
-
Botnet Traffic Filter
-
The following inspections:
-
SCTP inspection maps (SCTP stateful inspection using ACLs is supported)
-
Diameter
-
GTP/GPRS
-
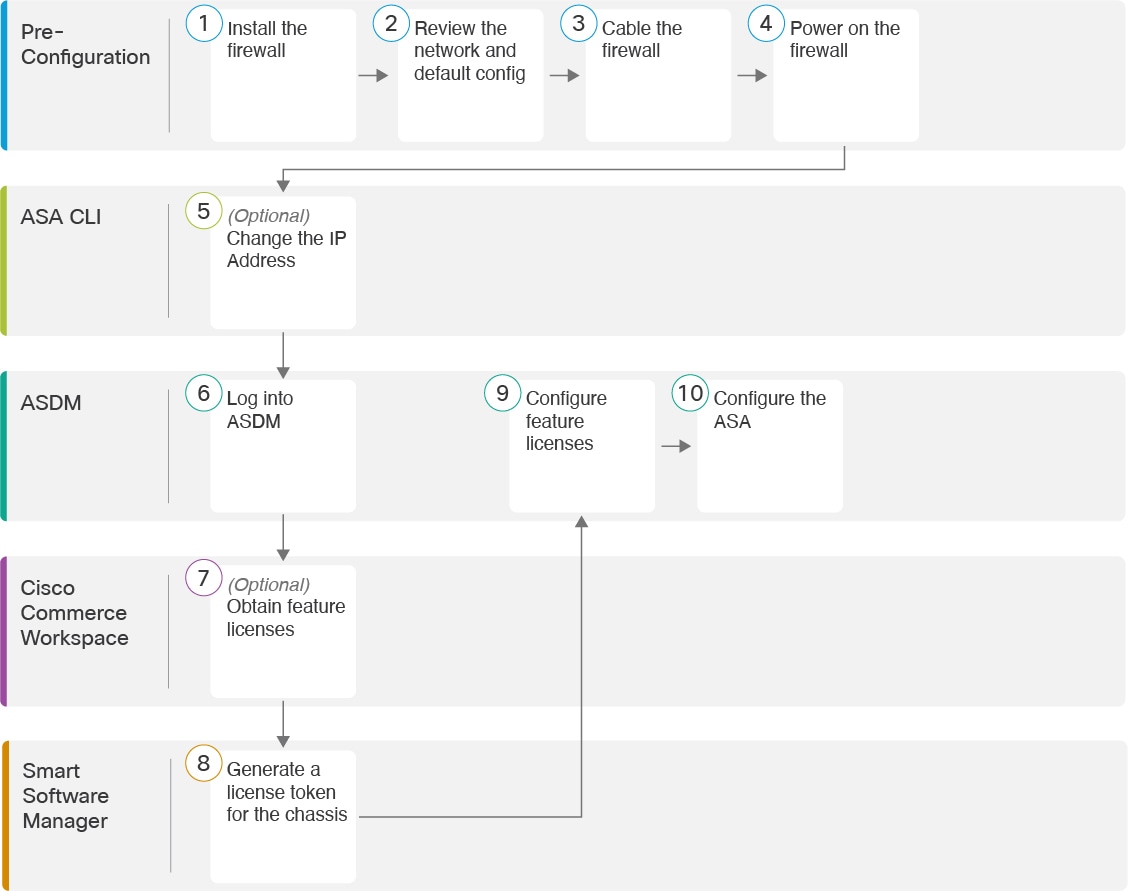
Migrating an ASA 5500-X Configuration
You can copy and paste an ASA 5500-X configuration into the Firepower 2100 in Appliance Mode. However, you will need to modify your configuration. Also note some behavioral differences between the platforms.
-
To copy the configuration, enter the more system:running-config command on the ASA 5500-X.
-
Edit the configuration as necessary (see below).
-
Connect to the console port of the Firepower 2100 in Appliance Mode, and enter global configuration mode:
ciscoasa> enable Password: The enable password is not set. Please set it now. Enter Password: ****** Repeat Password: ****** ciscoasa# configure terminal ciscoasa(config)# -
Clear the current configuration using the clear configure all command.
-
Paste the modified configuration at the ASA CLI.
This guide assumes a factory default configuration, so if you paste in an existing configuration, some of the procedures in this guide will not apply to your ASA.
|
ASA 5500-X Configuration |
Firepower 2100 in Appliance Mode Configuration |
|---|---|
|
PAK License |
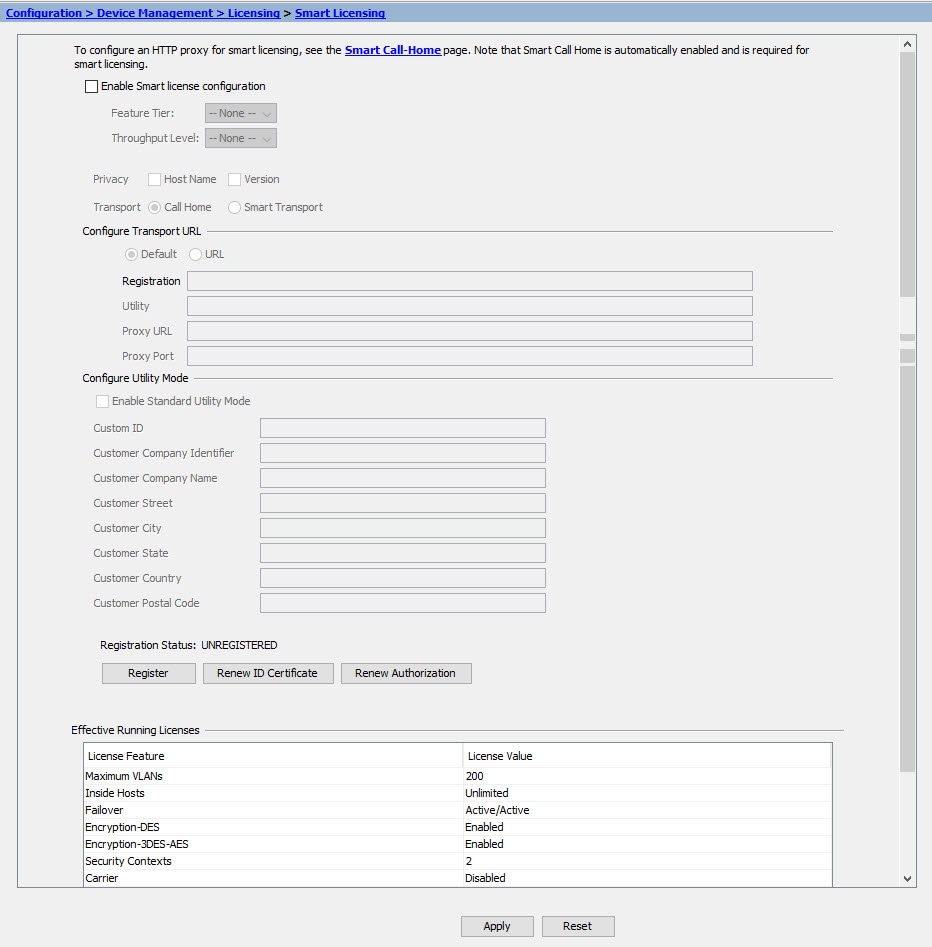
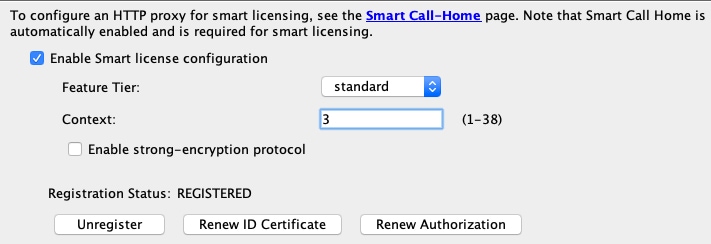
Smart License PAK licensing is not applied when you copy and paste your configuration. There are no licenses installed by default. Smart Licensing requires that you connect to the Smart Licensing server to obtain your licenses. Smart Licensing also affects ASDM or SSH access (see below). |
|
Initial ASDM access |
Remove any VPN or other strong encryption feature configuration—even if you only configured weak encryption—if you cannot connect to ASDM or register with the Smart Licensing server. You can reenable these features after you obtain the Strong Encryption (3DES) license. The reason for this issue is that the ASA includes 3DES capability by default for management access only. If you enable a strong encryption feature, then ASDM and HTTPS traffic (like that to and from the Smart Licensing server) are blocked. The exception to this rule is if you are connected to a management-only interface, such as Management 1/1. SSH is not affected. |
|
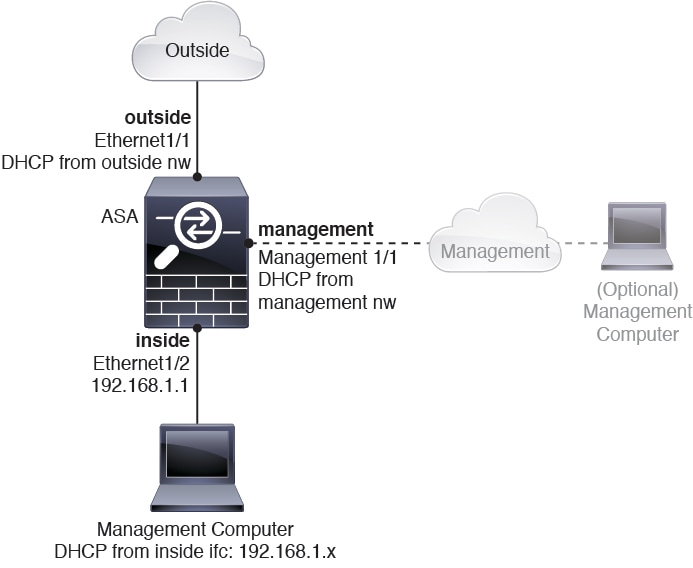
Interface IDs |
Make sure you change the interface IDs to match the new hardware IDs. For example, the ASA 5525-X includes Management 0/0, and GigabitEthernet 0/0 through 0/5. The Firepower 1120 includes Management 1/1 and Ethernet 1/1 through 1/8. |
|
boot system commands The ASA 5500-X allows up to four boot system commands to specify the booting image to use. |
The Firepower 2100 in Appliance Mode only allows a single boot system command, so you should remove all but one command before you paste. You actually do not need to have any boot system commands present in your configuration, as it is not read at startup to determine the booting image. The last-loaded boot image will always run upon reload. The boot system command performs an action when you enter it: the system validates and unpacks the image and copies it to the boot location (an internal location on disk0 managed by FXOS). The new image will load when you reload the ASA. |



 Feedback
Feedback